 Common Problem
Common Problem
 Zerodium announces $400,000 payout for Microsoft Outlook Zero-Click RCE security vulnerability
Zerodium announces $400,000 payout for Microsoft Outlook Zero-Click RCE security vulnerability
Zerodium announces $400,000 payout for Microsoft Outlook Zero-Click RCE security vulnerability
- Click to enter:ChatGPT tool plug-in navigation

Zerodium is a security vulnerability exploitation supplier. Earlier today Time announced that it is increasing bounty payouts for Microsoft Outlook Zero-Click Remote Code Execution (RCE) by 60% to $400,000 from the previous $250,000.
Zero-click attacks are particularly dangerous because they require no user interaction at all to deliver the malicious payload to a potential victim’s device. Zerodium noted, however, that the increase in payout was "temporary," meaning the decision could be revised later.
Here is the full announcement:
We are temporarily increasing payouts for Microsoft Outlook RCE from $250,000 to $400,000. We are looking for zero-click vulnerabilities that lead to remote code execution when receiving/downloading emails in Outlook without any user interaction, such as reading the malicious email or opening an attachment. Exploits that rely on opening/reading emails may receive lower rewards.
In related Outlook news, Microsoft's One Outlook Project Monarch has apparently been delayed, but it's reportedly still making progress.
Alongside Microsoft’s Outlook payments announcement, Zerodium also announced Mozilla’s Thunderbird platform with a $200,000 bounty.
We are looking for zero-click vulnerabilities that affect Thunderbird and lead to remote code execution when receiving/downloading an email, without any user interaction such as reading the malicious email or opening an attachment. Exploits that rely on opening/reading emails may receive lower rewards.
The above is the detailed content of Zerodium announces $400,000 payout for Microsoft Outlook Zero-Click RCE security vulnerability. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to change the font in Outlook on Apple mobile phone
Mar 08, 2024 pm 04:46 PM
How to change the font in Outlook on Apple mobile phone
Mar 08, 2024 pm 04:46 PM
How to change the font in Outlook on Apple mobile phone? First open the Outlook software and click on the file in the upper left corner of the interface. You can set the font according to your own preferences. After the settings are completed, click the OK button. Let’s take a look! How to change the font in Outlook on Apple mobile phone 1. Open the Outlook software and click the "File" option in the upper left corner of the interface. 2. In the list that appears, find "Options" and click to enter. 3. On the left side of the option list, click "Mail". 4. Next, select “Letter and Fonts”. 5. If you want to set the font for new emails, reply emails, or composing, click the corresponding option to enter the settings. 6. Set the font according to personal preference. After the setting is completed, click OK
 Outlook emails lost from control panel in Windows 11
Feb 29, 2024 pm 03:16 PM
Outlook emails lost from control panel in Windows 11
Feb 29, 2024 pm 03:16 PM
Is the Outlook mail icon missing from Windows 11's Control Panel? This unexpected situation has caused confusion and concern among some individuals who rely on OutlookMail for their communication needs. Why don't my Outlook emails show up in Control Panel? There may be several possible reasons why there are no Outlook mail icons in Control Panel: Outlook is not installed correctly. Installing Office applications from the Microsoft Store does not add the Mail applet to Control Panel. The location of the mlcfg32.cpl file in Control Panel is missing. The path to the mlcfg32.cpl file in the registry is incorrect. The operating system is not currently configured to run this application
 How to sort emails by sender, subject, date, category, size in Outlook
Feb 19, 2024 am 10:48 AM
How to sort emails by sender, subject, date, category, size in Outlook
Feb 19, 2024 am 10:48 AM
Outlook offers many settings and features to help you manage your work more efficiently. One of them is the sorting option that allows you to categorize your emails according to your needs. In this tutorial, we will learn how to use Outlook's sorting feature to organize emails based on criteria such as sender, subject, date, category, or size. This will make it easier for you to process and find important information, making you more productive. Microsoft Outlook is a powerful application that makes it easy to centrally manage your email and calendar schedules. You can easily send, receive, and organize email, while built-in calendar functionality makes it easy to keep track of your upcoming events and appointments. How to be in Outloo
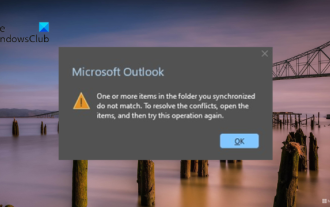 One or more items in the folder you synced do not match Outlook error
Mar 18, 2024 am 09:46 AM
One or more items in the folder you synced do not match Outlook error
Mar 18, 2024 am 09:46 AM
When you find that one or more items in your sync folder do not match the error message in Outlook, it may be because you updated or canceled meeting items. In this case, you will see an error message saying that your local version of the data conflicts with the remote copy. This situation usually happens in Outlook desktop application. One or more items in the folder you synced do not match. To resolve the conflict, open the projects and try the operation again. Fix One or more items in synced folders do not match Outlook error In Outlook desktop version, you may encounter issues when local calendar items conflict with the server copy. Fortunately, though, there are some simple ways to help
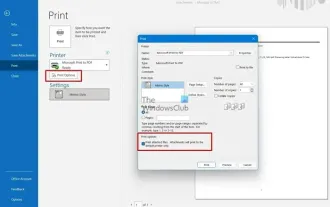 How to print all attachments in Outlook
Feb 20, 2024 am 10:30 AM
How to print all attachments in Outlook
Feb 20, 2024 am 10:30 AM
Outlook is one of the most feature-rich email clients and has become an indispensable tool for professional communication. One of the challenges is printing all attachments at the same time in Outlook. Usually you need to download attachments one by one before you can print them, but if you want to print everything at once, this is the problem most people encounter. How to Print All Attachments in Outlook Although most of the information is maintained online in the Outlook application, there are times when you need to print out the information for backup. Must sign documents in person to satisfy legal requirements such as contracts, government forms, or homework assignments. There are several methods that allow you to print all attachments in Outlook with one click instead of printing them one by one. Let's look at each one in detail. Outloo
 Outlook calendar not syncing;
Mar 26, 2024 am 09:36 AM
Outlook calendar not syncing;
Mar 26, 2024 am 09:36 AM
If your Outlook calendar cannot sync with Google Calendar, Teams, iPhone, Android, Zoom, Office account, etc., please follow the steps below to resolve the issue. The calendar app can be connected to other calendar services such as Google Calendar, iPhone, Android, Microsoft Office 365, etc. This is very useful because it can sync automatically. But what if OutlookCalendar fails to sync with third-party calendars? Possible reasons could be selecting the wrong calendar for synchronization, calendar not visible, background application interference, outdated Outlook application or calendar application, etc. Preliminary fix for Outlook calendar not syncing
 Outlook signature disappears every day after restart
Feb 19, 2024 pm 05:24 PM
Outlook signature disappears every day after restart
Feb 19, 2024 pm 05:24 PM
An email signature is important to demonstrate legitimacy and professionalism and includes contact information and company logo. Outlook users often complain that signatures disappear after restarting, which can be frustrating for those looking to increase their company's visibility. In this article, we will explore different fixes to resolve this issue. Why do my Microsoft Outlook signatures keep disappearing? If this is your first time using Microsoft Outlook, make sure your version is not a trial version. Trial versions may cause signatures to disappear. Additionally, the version architecture should also match the version architecture of the operating system. If you find that your email signature disappears from time to time in Outlook Web App, it may be due to
 Office 365 says Outlook PST cannot be found
Feb 19, 2024 am 11:15 AM
Office 365 says Outlook PST cannot be found
Feb 19, 2024 am 11:15 AM
If Outlook cannot locate your PST file, you may be interested in the following information. PST files are key files in Microsoft applications, including Outlook, that store emails, calendar events, and other data. These files are crucial when managing Outlook projects. However, some users encounter the "OutlookPST file not found" problem when starting Outlook. Why can't Outlook find my PST file? The PST not found error that Outlook keeps throwing may be due to the PST file being damaged, causing the inbox file to be too large or the data to be cluttered. Another possible cause is a damaged Outlook application. Office365


