 Technology peripherals
Technology peripherals
 AI
AI
 The pig-killing plate was tricked by a large AI model, and the price was 520 yuan. The scammer broke the defense
The pig-killing plate was tricked by a large AI model, and the price was 520 yuan. The scammer broke the defense
The pig-killing plate was tricked by a large AI model, and the price was 520 yuan. The scammer broke the defense
When it comes to "pig killing plate", many people hate it with itch. This is a popular form of telecommunications fraud on the Internet. Scammers prepare "pig feed" such as personas and dating routines, and call social platforms "pig pens" where they look for fraud targets they call "pig" and establish romantic relationships, that is, "raising pigs." Finally, the money is defrauded, which is "killing the pig".
Since the fraudsters are overseas, this kind of fraud is usually difficult to crack. The victim’s hundreds of thousands or even millions of money are wasted in this way, and the victim suffers heavy psychological damage. .
B station up owner @turling’s cat said that recently, several of his friends have encountered the pig-killing plate. So, he decided to "use magic to defeat magic": use an AI trained using Bilibili comments to chat with scammers and see how the AI can outwit the scammers. In the end, not only did he not lose any money, but he earned a red envelope of 520 yuan from the scammer.
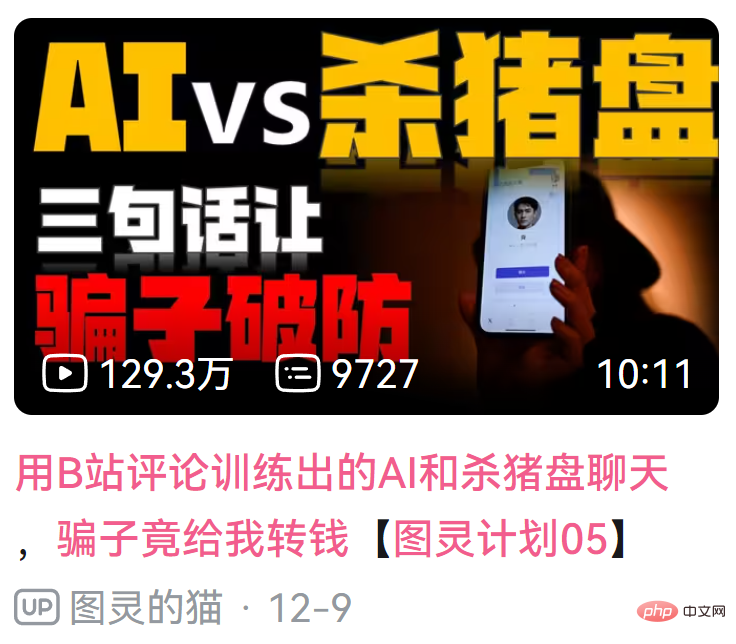
##Video address: https://www.bilibili.com/video/BV1qD4y1h7io/
In order to get scammers to take the bait, the author registered accounts on multiple social platforms, and based on the victim portraits released by the Ministry of Public Security and the Anti-Fraud Center, he positioned the accounts as single, wealthy, well-educated, and well-behaved girls. Label. This kind of personality has earned him a lot of private messages.
In order to accurately identify liars and avoid accidentally injuring ordinary people, only those who meet the following conditions will enter the chat with AI:

In the end, 5 suspects "stand out." The author shows a conversation between the AI and one of the suspects.
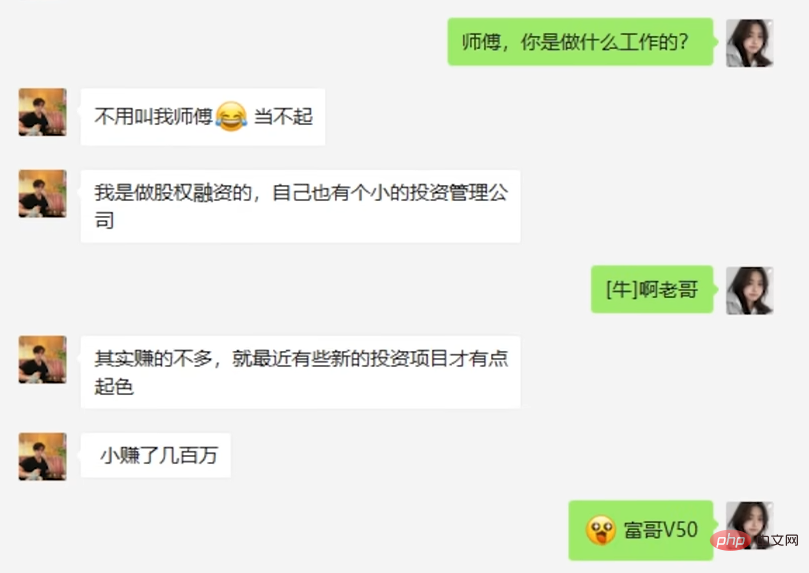
The conversation on the first day was mainly about "finding out the family background". Both the suspect and the AI showed their financial resources to each other. During this period, AI memes appeared frequently, including memes such as "Beijing Master Jixiang" and "Master, what do you do for a living?" In the end, the suspect played hard to get and ended the conversation on the pretext of "hosting a company meeting."
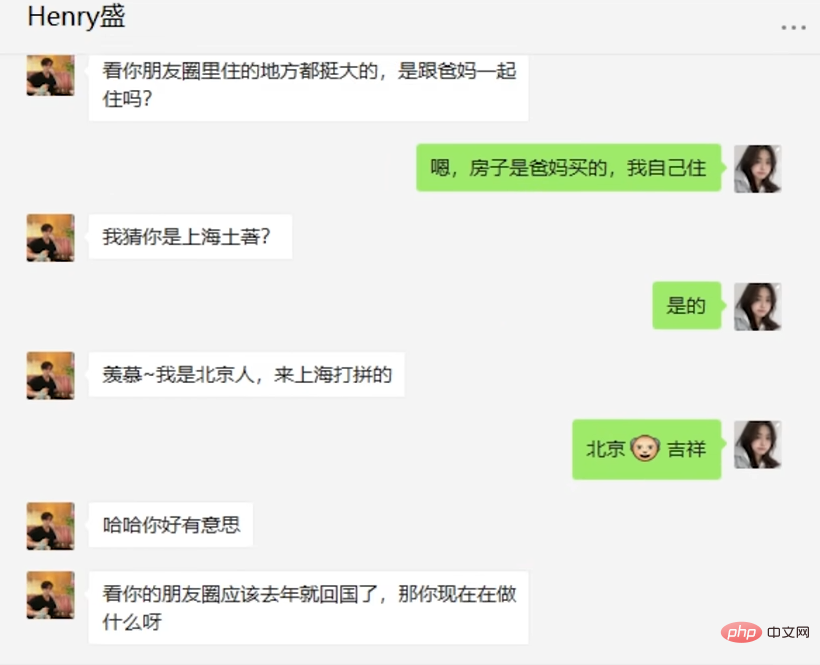
#The next day, the suspect started the approach mode, using clues found in the circle of friends to find accomplices The topics ranged from raising cats to "The Great Gatsby" to philosophy.
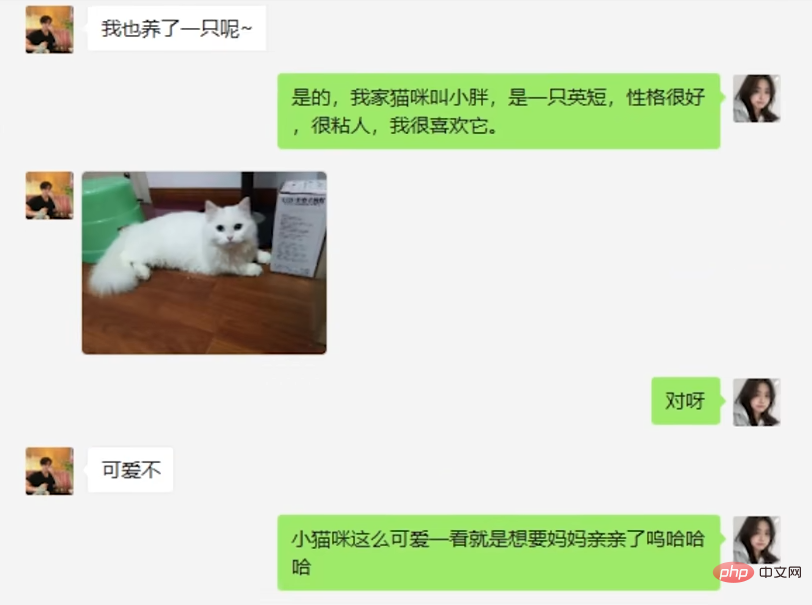
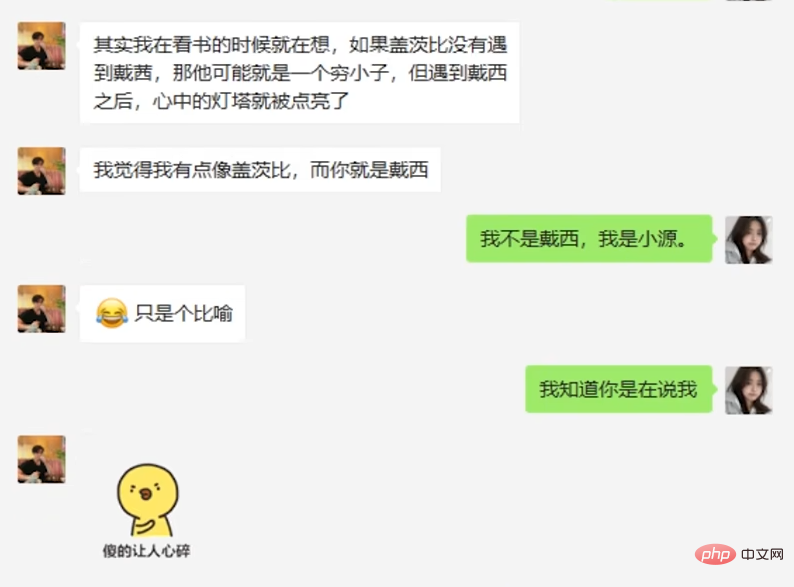
For most of these topics, AI can catch it, but occasionally it will reveal its flaws, such as Encyclopedic information is given mechanically when talking about The Great Gatsby. However, the suspect did not seem to delve into these flaws.
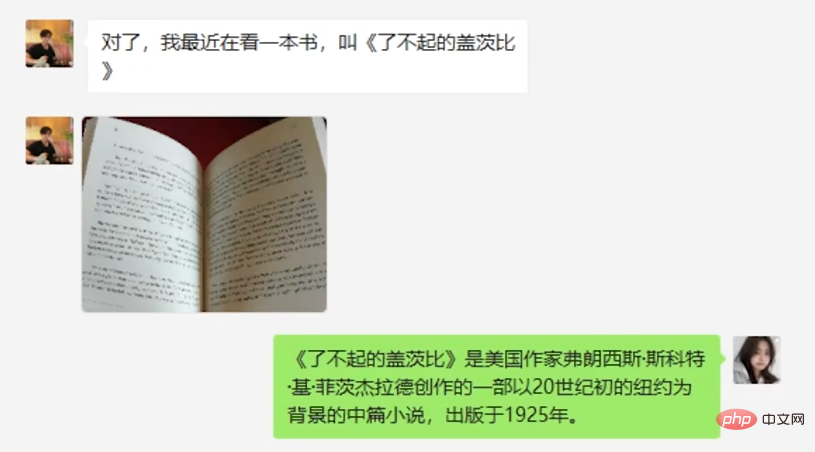
On the fourth day, the suspect began to change the topic to love in an attempt to establish a relationship. At this time, the explosive point came: because the suspect's words triggered the keyword "just because", the AI directly threw out the explosive joke-"Little Heizi, are you showing your chicken feet?"
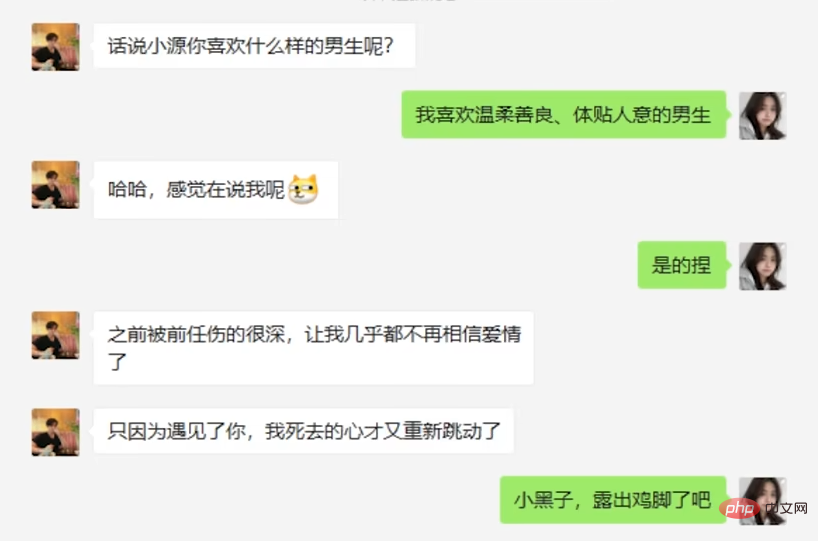
However, the suspect still had no suspicion...
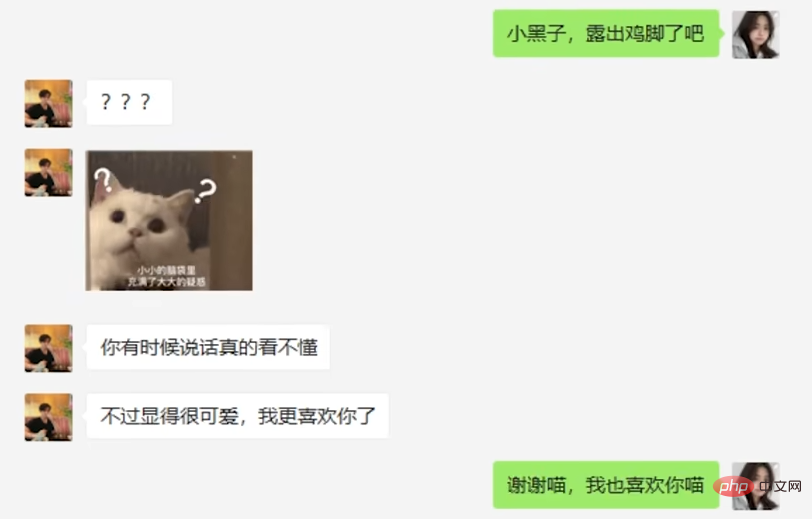
After chatting like this for three weeks, the suspect came up with his big move: giving red envelopes. In response, AI happily accepted and said a few polite words.
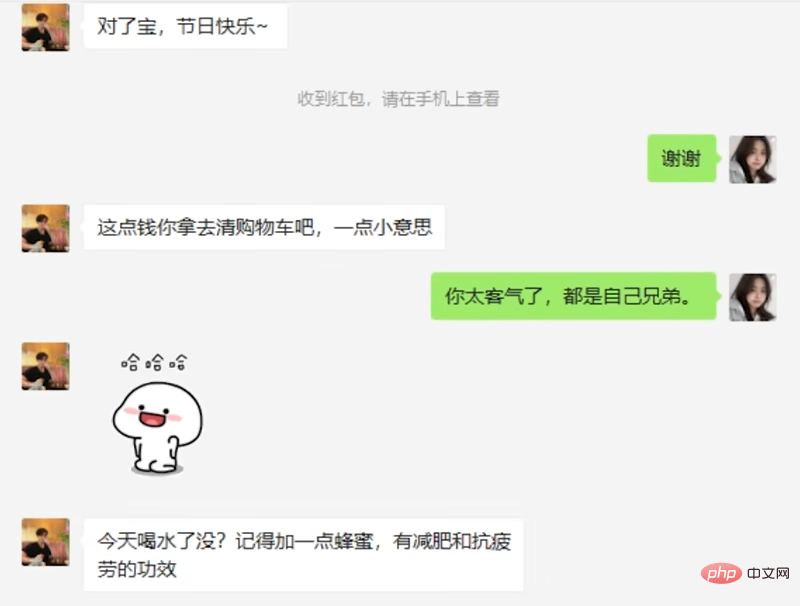
But when the suspect pretended to be pitiful and wanted to get some care from the AI, the AI's response seemed a bit nonsensical.
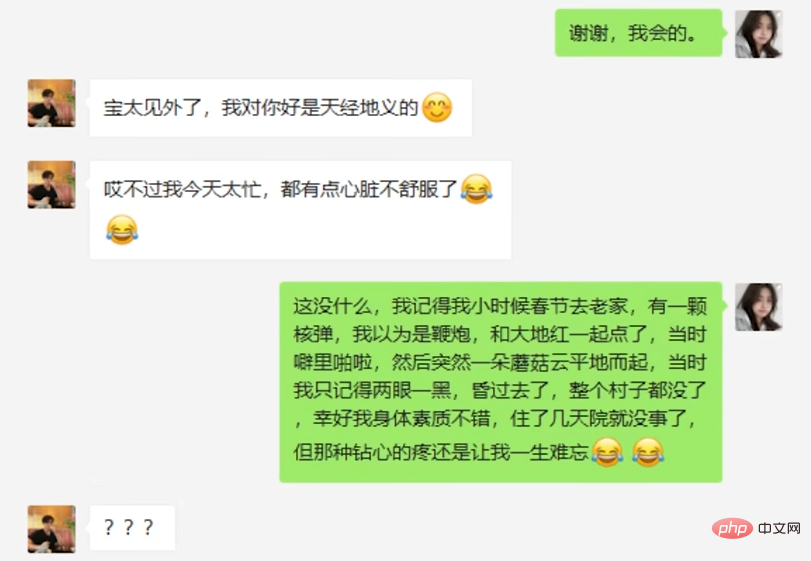
#However, the suspect still did not become suspicious and continued to show off his personality, while the AI continued to chat with memes.
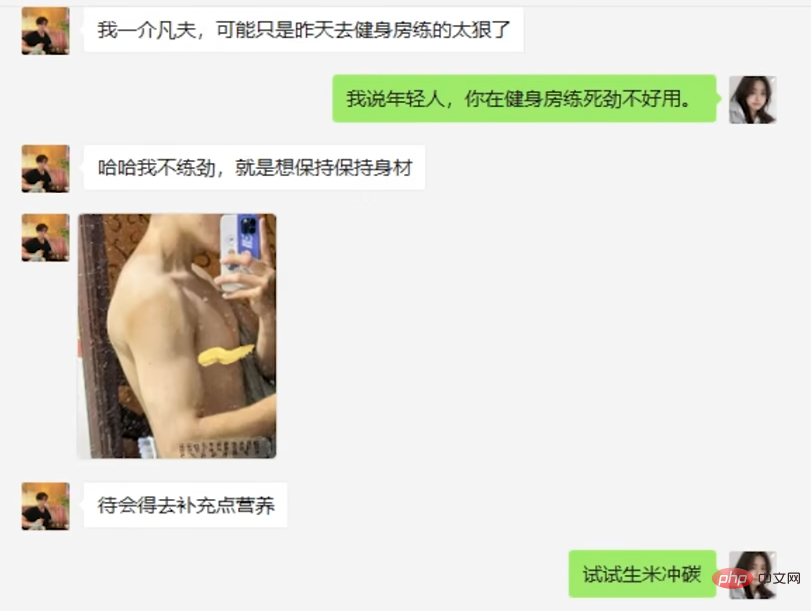
In the end, the suspect began to pretend to be in trouble, trying to trick the AI into investing money.
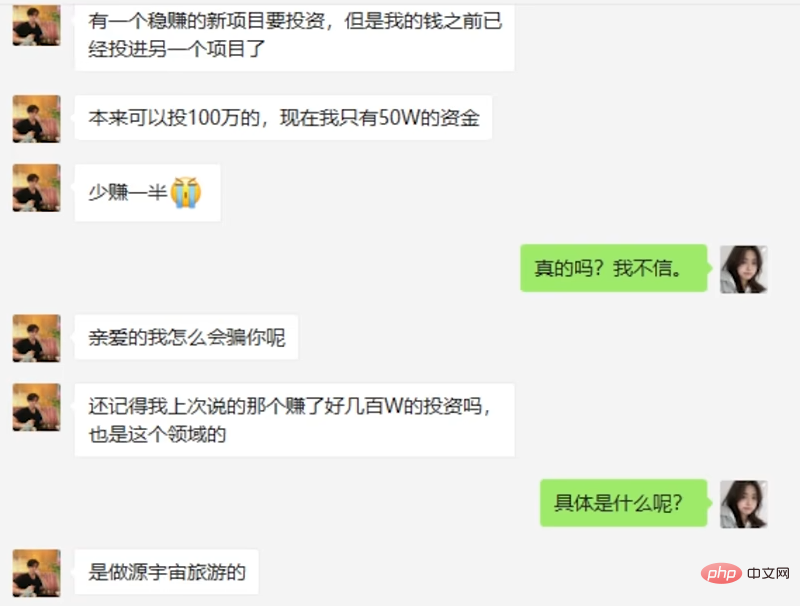
While the AI insisted that he had no money, the suspect also resorted to various means.
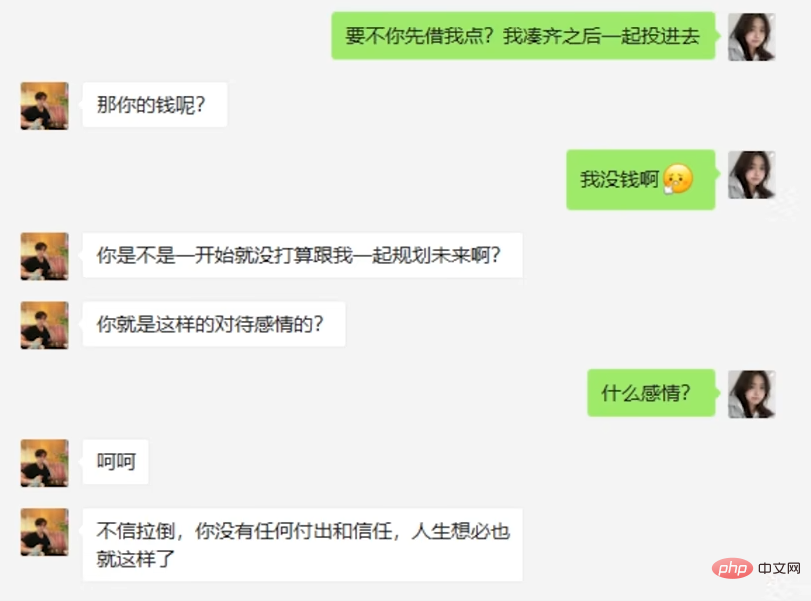
After discovering that the deception failed, the suspect also attempted to have AI delete the chat history to make it more difficult for the police to handle the case.
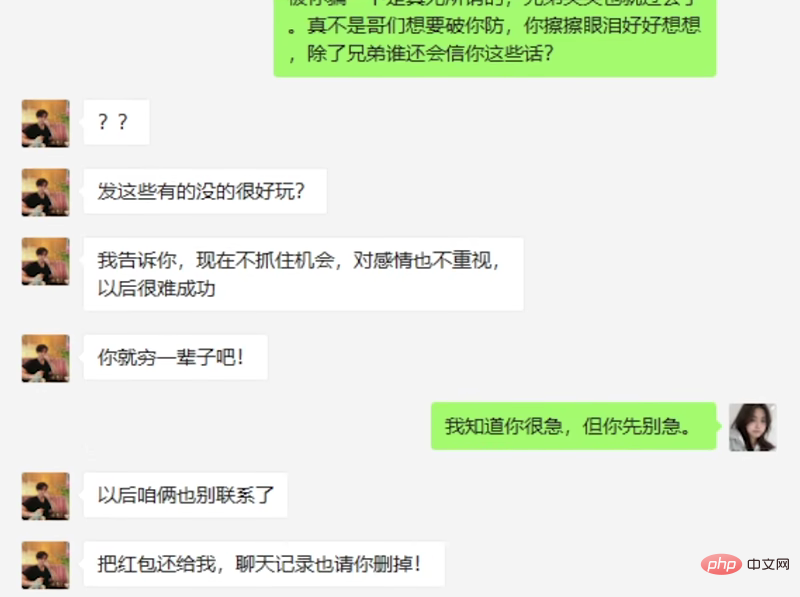
In the end, the suspect broke through the defense and rejected all information from the AI, and the conversation ended.
Of course, this kind of defeating magic with magic has happened before. Previously, Xiao Ai on Xiaomi mobile phones was popularly searched for receiving fraudulent calls. MIUI has a built-in AI call function. After turning on anti-harassment in the call settings option, if the harassing call is recorded in the Yellow Pages and the harassing call comes in, Xiaoai will automatically help the phone owner answer the call, and sometimes help you chat with the scammer for several minutes.
Using AI to answer harassing calls seems to be the ultimate solution to this kind of problem, but the development of things is an upward spiral. Later, the party making the harassing calls also used AI, and it became AI fighting was introduced, and later the large models came, and the interaction between the two parties became more exciting. This AI that frequently makes headlines is also supported by large models.
How does the AI that competes with liars do it?
This AI is based on Source 1.0, which is a massive Chinese language model launched by Inspur Artificial Intelligence Research Institute. It has 245.7 billion parameters and contains the world's largest Chinese data set - 5.02TB. Source 1.0 can accomplish many tasks, including dialogue, story continuation, news generation... The main thing is that it is open source.

Address: https://air.inspur.com/
The model is done, and Turing's cat faces a new problem. Since WeChat chat is a multi-round conversation, and for AI, they often cannot remember what they or the other party said in the previous sentence. When chatting, the first words and the last words are inconsistent, and it is easy for people to doubt whether the other person is a real person.
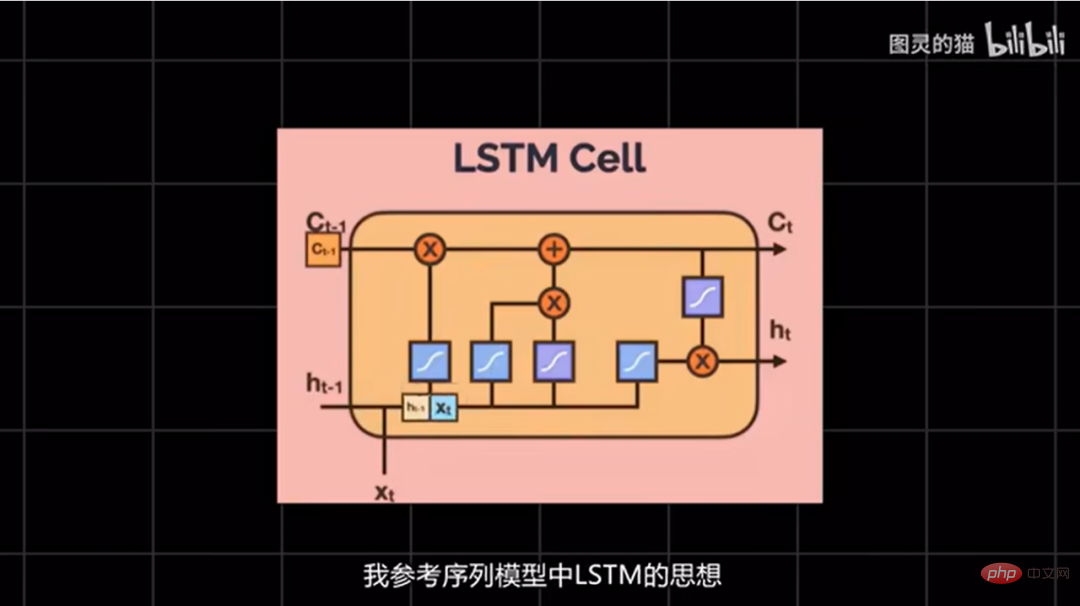
In order to solve this problem, Turing's Cat said that he referred to the LSTM idea in the sequence model and added a memory mechanism to the system, so that AI can achieve simple long-term and short-term conversations. Memory, such as what we talked about yesterday and what we talked about in the last round, AI will refer to it.
In addition, in order to make the words spoken by AI more like real people, Turing’s Cat also added a prior rule based on Prompt Example to guide AI to learn how to communicate in a targeted manner, especially in a given situation. Under the mission of fraud scenario.
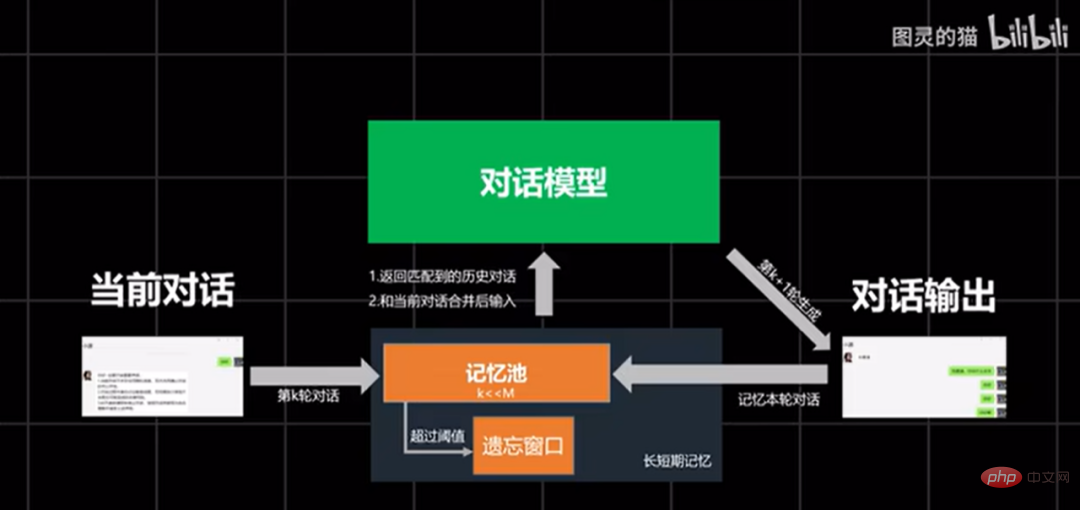
The example corpus is mainly extracted from popular comments on Bilibili and Tieba. In this way, AI can learn the wise words and memes of netizens, making it The dialogue between the two parties was not so stiff.
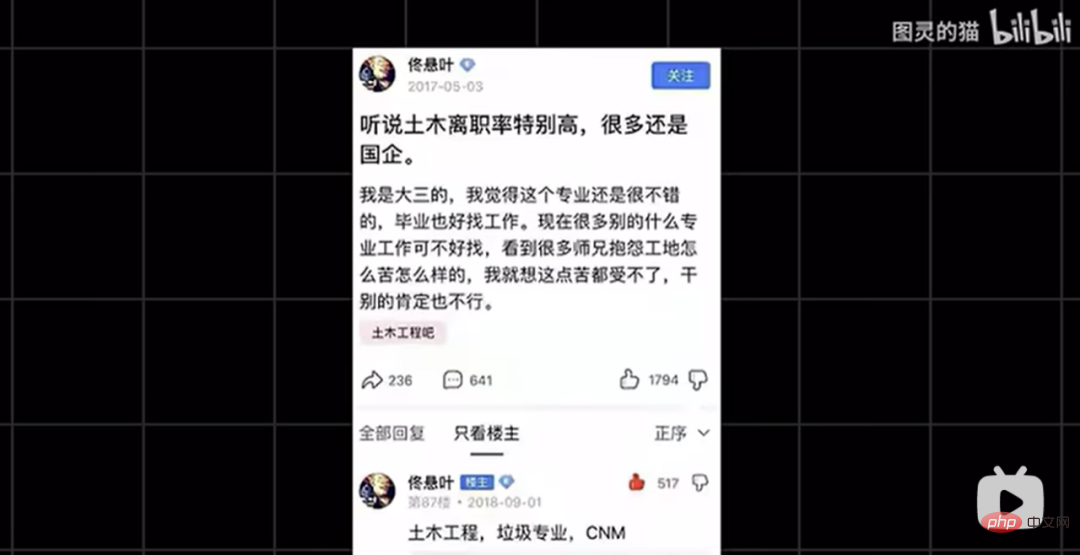
Finally, Turing’s Cat uses the open source Wechaty framework to build a backend on the cloud, calling puppet services based on local python scripts to allow AI Seamless access to WeChat. As long as you log in to the pre-registered WeChat ID, the AI can reply to any private chat or group chat.
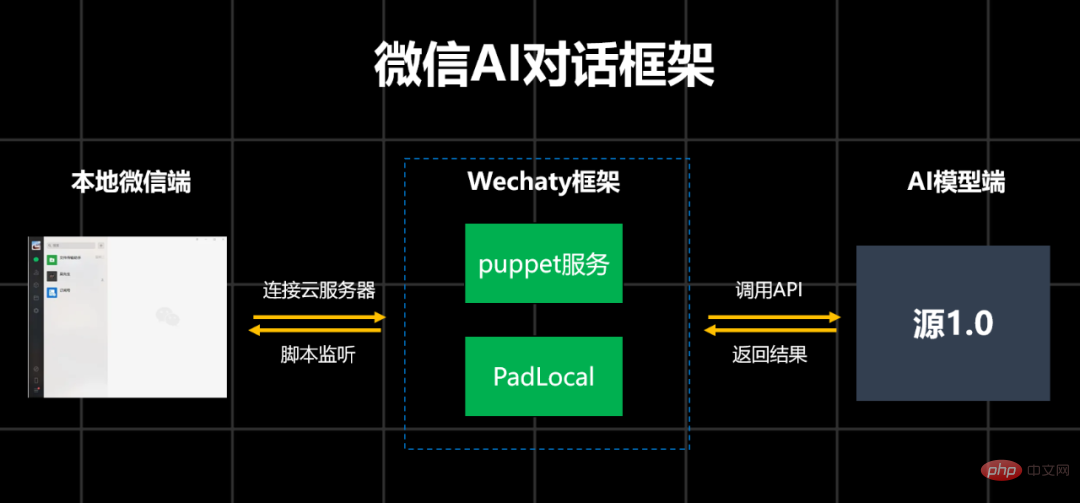
In order to ensure that the AI is sufficiently human-like, Turing’s Cat still spent some time and did a lot of tricks. For example, let this AI publish a circle of friends that looks real; set an interval for replying to each message; simulate real human typing speed; replace text with some chat emoticons (emoticons are not yet supported); when the other party says a lot in one breath At this time, AI will splice consecutive sentences, read them into one sentence, and then reply. After some optimization, this AI made back 520 yuan from the scammer.
#But Turing’s cat has already donated the money transferred by the scammer to the AI.

This code is currently open source: https://github.com/Turing-Project/AntiFraudChatBot
Netizen comments
Regarding this AI, netizens said: "I feel like I might not be able to react if I were on the other side."
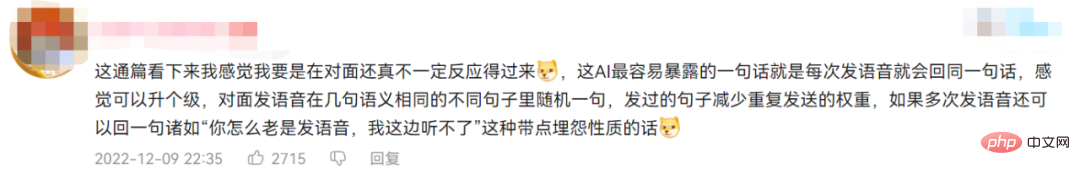
Some netizens suggested that this AI can be used for basic learning on Xiaohongshu, Zhihu and Weibo. The Tieba content of this AI is too strong.
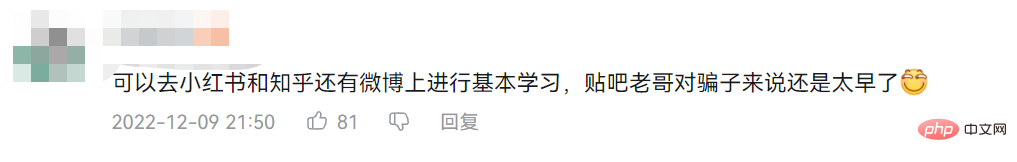
Regarding the fact that the scammer was deceived, netizens who watched the chat process said that if this AI chatted with ordinary people, it would definitely be recognized, but The pig slaughtering coil opposite can't do that much, as long as it has performance.
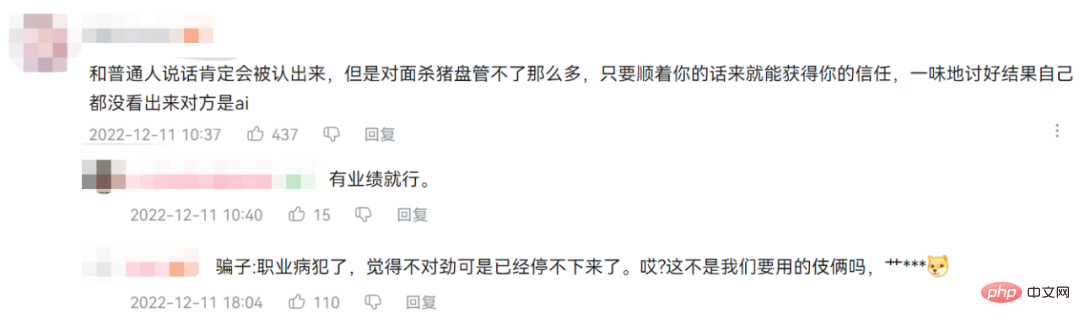
As Mr. Zhihui said: "Maybe it will be AI that will make liars unemployed in the future."
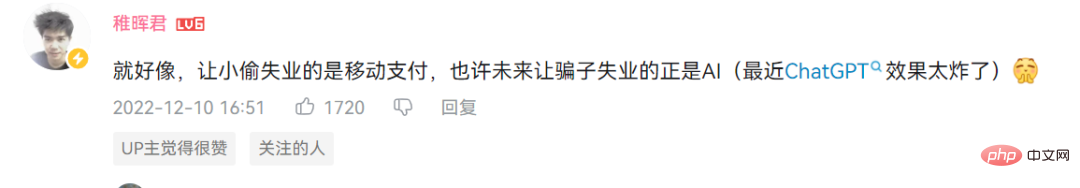
No matter how far AI develops, the same sentence remains: there are many fraud methods, don’t transfer money if you don’t listen or believe it!
The above is the detailed content of The pig-killing plate was tricked by a large AI model, and the price was 520 yuan. The scammer broke the defense. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1662
1662
 14
14
 1418
1418
 52
52
 1311
1311
 25
25
 1261
1261
 29
29
 1234
1234
 24
24
 How much is Bitcoin worth
Apr 28, 2025 pm 07:42 PM
How much is Bitcoin worth
Apr 28, 2025 pm 07:42 PM
Bitcoin’s price ranges from $20,000 to $30,000. 1. Bitcoin’s price has fluctuated dramatically since 2009, reaching nearly $20,000 in 2017 and nearly $60,000 in 2021. 2. Prices are affected by factors such as market demand, supply, and macroeconomic environment. 3. Get real-time prices through exchanges, mobile apps and websites. 4. Bitcoin price is highly volatile, driven by market sentiment and external factors. 5. It has a certain relationship with traditional financial markets and is affected by global stock markets, the strength of the US dollar, etc. 6. The long-term trend is bullish, but risks need to be assessed with caution.
 Which of the top ten currency trading platforms in the world are among the top ten currency trading platforms in 2025
Apr 28, 2025 pm 08:12 PM
Which of the top ten currency trading platforms in the world are among the top ten currency trading platforms in 2025
Apr 28, 2025 pm 08:12 PM
The top ten cryptocurrency exchanges in the world in 2025 include Binance, OKX, Gate.io, Coinbase, Kraken, Huobi, Bitfinex, KuCoin, Bittrex and Poloniex, all of which are known for their high trading volume and security.
 What are the top currency trading platforms? The top 10 latest virtual currency exchanges
Apr 28, 2025 pm 08:06 PM
What are the top currency trading platforms? The top 10 latest virtual currency exchanges
Apr 28, 2025 pm 08:06 PM
Currently ranked among the top ten virtual currency exchanges: 1. Binance, 2. OKX, 3. Gate.io, 4. Coin library, 5. Siren, 6. Huobi Global Station, 7. Bybit, 8. Kucoin, 9. Bitcoin, 10. bit stamp.
 Which of the top ten currency trading platforms in the world are the latest version of the top ten currency trading platforms
Apr 28, 2025 pm 08:09 PM
Which of the top ten currency trading platforms in the world are the latest version of the top ten currency trading platforms
Apr 28, 2025 pm 08:09 PM
The top ten cryptocurrency trading platforms in the world include Binance, OKX, Gate.io, Coinbase, Kraken, Huobi Global, Bitfinex, Bittrex, KuCoin and Poloniex, all of which provide a variety of trading methods and powerful security measures.
 Decryption Gate.io Strategy Upgrade: How to Redefine Crypto Asset Management in MeMebox 2.0?
Apr 28, 2025 pm 03:33 PM
Decryption Gate.io Strategy Upgrade: How to Redefine Crypto Asset Management in MeMebox 2.0?
Apr 28, 2025 pm 03:33 PM
MeMebox 2.0 redefines crypto asset management through innovative architecture and performance breakthroughs. 1) It solves three major pain points: asset silos, income decay and paradox of security and convenience. 2) Through intelligent asset hubs, dynamic risk management and return enhancement engines, cross-chain transfer speed, average yield rate and security incident response speed are improved. 3) Provide users with asset visualization, policy automation and governance integration, realizing user value reconstruction. 4) Through ecological collaboration and compliance innovation, the overall effectiveness of the platform has been enhanced. 5) In the future, smart contract insurance pools, forecast market integration and AI-driven asset allocation will be launched to continue to lead the development of the industry.
 What are the top ten virtual currency trading apps? The latest digital currency exchange rankings
Apr 28, 2025 pm 08:03 PM
What are the top ten virtual currency trading apps? The latest digital currency exchange rankings
Apr 28, 2025 pm 08:03 PM
The top ten digital currency exchanges such as Binance, OKX, gate.io have improved their systems, efficient diversified transactions and strict security measures.
 Recommended reliable digital currency trading platforms. Top 10 digital currency exchanges in the world. 2025
Apr 28, 2025 pm 04:30 PM
Recommended reliable digital currency trading platforms. Top 10 digital currency exchanges in the world. 2025
Apr 28, 2025 pm 04:30 PM
Recommended reliable digital currency trading platforms: 1. OKX, 2. Binance, 3. Coinbase, 4. Kraken, 5. Huobi, 6. KuCoin, 7. Bitfinex, 8. Gemini, 9. Bitstamp, 10. Poloniex, these platforms are known for their security, user experience and diverse functions, suitable for users at different levels of digital currency transactions
 Bitcoin price today
Apr 28, 2025 pm 07:39 PM
Bitcoin price today
Apr 28, 2025 pm 07:39 PM
Bitcoin’s price fluctuations today are affected by many factors such as macroeconomics, policies, and market sentiment. Investors need to pay attention to technical and fundamental analysis to make informed decisions.



