Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 Example analysis of XML external entity injection vulnerability
Example analysis of XML external entity injection vulnerability
Example analysis of XML external entity injection vulnerability
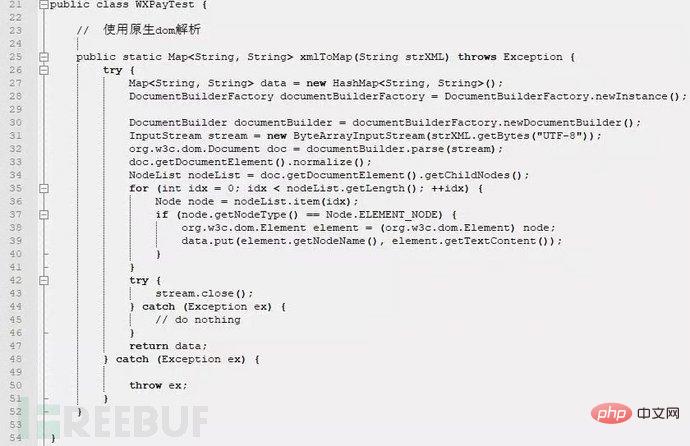
1. XML external entity injection
XML external entity injection vulnerability is what we often call XXE vulnerability. XML is a widely used data transmission format, and many applications contain code for processing XML data. By default, many outdated or improperly configured XML processors will reference external entities.
If an attacker can upload an XML document or add malicious content to an XML document, through vulnerable code, dependencies, or integrations, they can attack a flawed XML processor. The occurrence of XXE vulnerabilities has nothing to do with the development language. As long as the xml data is parsed in the application and the data is controlled by the user, the application may be vulnerable to XXE attacks. This article takes a java program as an example to introduce the causes and repairs of XXE vulnerabilities. For details on the XXE vulnerability, please see CWE-611: Improper Restriction of XML External Entity Reference ('XXE')(http://cwe.mitre.org/data/definitions/611.html).
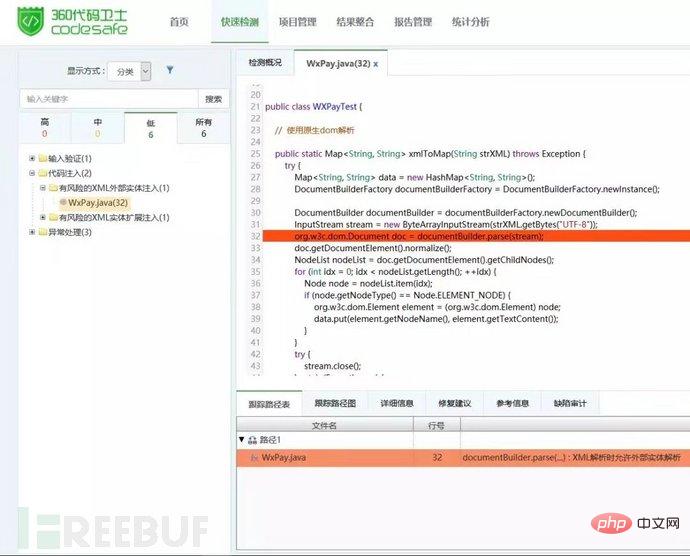
2. XML external entity injection
XXE vulnerabilities may be used to extract data, perform remote server requests, scan internal systems, perform denial of service attacks and other attacks. The business impact depends primarily on the affected referrers and data protection needs.
Since 2018, a total of 92 vulnerability information related to it have been released in CVE. Some of the CVEs are as follows:
| Apache Camel 2.20.0 to 2.20. 3 and 2.21.0 Core have an XXE vulnerability in the XSD validation processor. | |
|---|---|
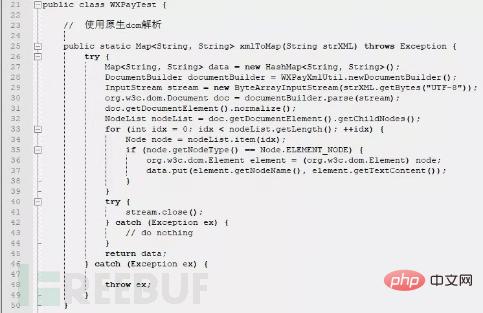
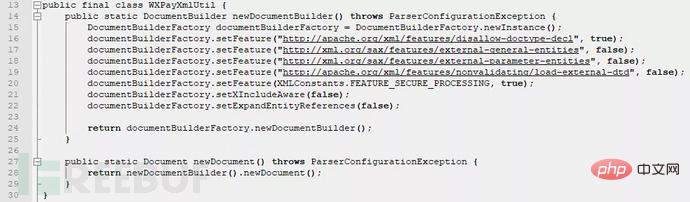
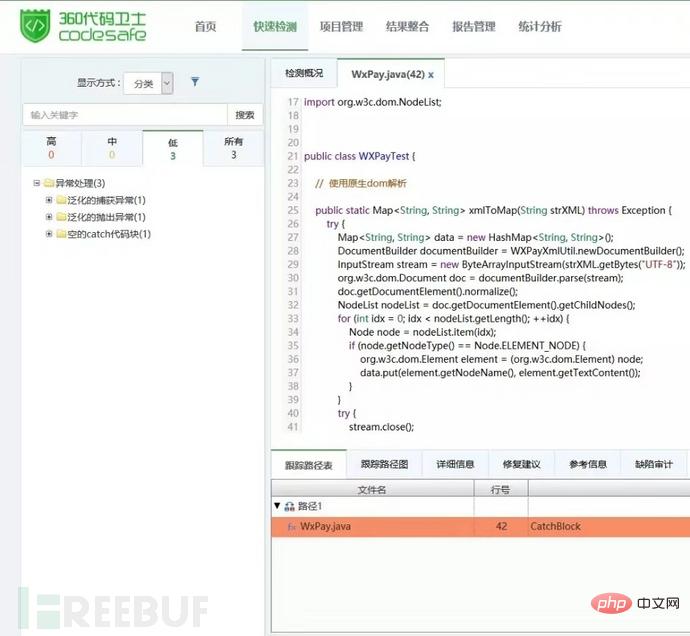
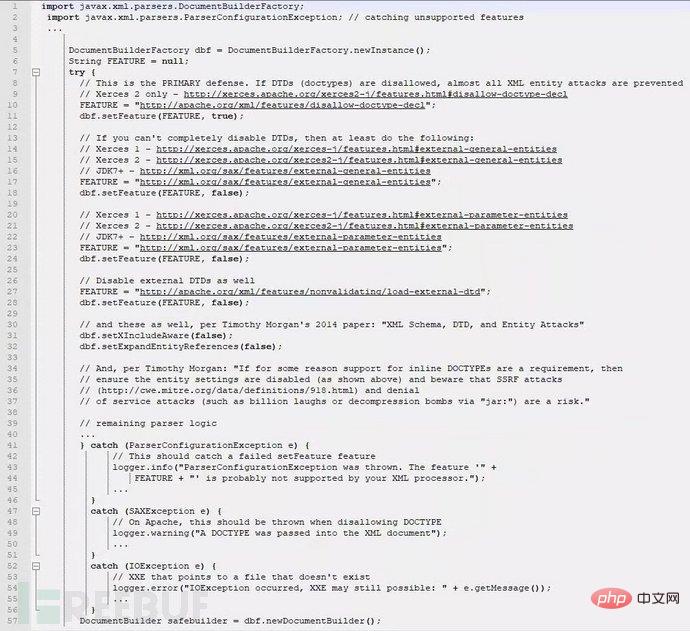
| There is an XXE vulnerability in the WXPayUtil class in the WeChat Payment Java SDK. | |
| In Umlet with version number less than 14.3, there is an XML external entity injection vulnerability in file parsing, which may lead to confidential data leakage and rejection Service, server-side request forgery. This attack can be carried out via a specially crafted UXF file. | |
The above is the detailed content of Example analysis of XML external entity injection vulnerability. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1389
1389
 52
52
 Can I open an XML file using PowerPoint?
Feb 19, 2024 pm 09:06 PM
Can I open an XML file using PowerPoint?
Feb 19, 2024 pm 09:06 PM
Can XML files be opened with PPT? XML, Extensible Markup Language (Extensible Markup Language), is a universal markup language that is widely used in data exchange and data storage. Compared with HTML, XML is more flexible and can define its own tags and data structures, making the storage and exchange of data more convenient and unified. PPT, or PowerPoint, is a software developed by Microsoft for creating presentations. It provides a comprehensive way of
 Using Python to merge and deduplicate XML data
Aug 07, 2023 am 11:33 AM
Using Python to merge and deduplicate XML data
Aug 07, 2023 am 11:33 AM
Using Python to merge and deduplicate XML data XML (eXtensibleMarkupLanguage) is a markup language used to store and transmit data. When processing XML data, sometimes we need to merge multiple XML files into one, or remove duplicate data. This article will introduce how to use Python to implement XML data merging and deduplication, and give corresponding code examples. 1. XML data merging When we have multiple XML files, we need to merge them
 Convert XML data to CSV format in Python
Aug 11, 2023 pm 07:41 PM
Convert XML data to CSV format in Python
Aug 11, 2023 pm 07:41 PM
Convert XML data in Python to CSV format XML (ExtensibleMarkupLanguage) is an extensible markup language commonly used for data storage and transmission. CSV (CommaSeparatedValues) is a comma-delimited text file format commonly used for data import and export. When processing data, sometimes it is necessary to convert XML data to CSV format for easy analysis and processing. Python is a powerful
 Filtering and sorting XML data using Python
Aug 07, 2023 pm 04:17 PM
Filtering and sorting XML data using Python
Aug 07, 2023 pm 04:17 PM
Implementing filtering and sorting of XML data using Python Introduction: XML is a commonly used data exchange format that stores data in the form of tags and attributes. When processing XML data, we often need to filter and sort the data. Python provides many useful tools and libraries to process XML data. This article will introduce how to use Python to filter and sort XML data. Reading the XML file Before we begin, we need to read the XML file. Python has many XML processing libraries,
 Import XML data into database using PHP
Aug 07, 2023 am 09:58 AM
Import XML data into database using PHP
Aug 07, 2023 am 09:58 AM
Importing XML data into the database using PHP Introduction: During development, we often need to import external data into the database for further processing and analysis. As a commonly used data exchange format, XML is often used to store and transmit structured data. This article will introduce how to use PHP to import XML data into a database. Step 1: Parse the XML file First, we need to parse the XML file and extract the required data. PHP provides several ways to parse XML, the most commonly used of which is using Simple
 Python implements conversion between XML and JSON
Aug 07, 2023 pm 07:10 PM
Python implements conversion between XML and JSON
Aug 07, 2023 pm 07:10 PM
Python implements conversion between XML and JSON Introduction: In the daily development process, we often need to convert data between different formats. XML and JSON are common data exchange formats. In Python, we can use various libraries to convert between XML and JSON. This article will introduce several commonly used methods, with code examples. 1. To convert XML to JSON in Python, we can use the xml.etree.ElementTree module
 Handling errors and exceptions in XML using Python
Aug 08, 2023 pm 12:25 PM
Handling errors and exceptions in XML using Python
Aug 08, 2023 pm 12:25 PM
Handling Errors and Exceptions in XML Using Python XML is a commonly used data format used to store and represent structured data. When we use Python to process XML, sometimes we may encounter some errors and exceptions. In this article, I will introduce how to use Python to handle errors and exceptions in XML, and provide some sample code for reference. Use try-except statement to catch XML parsing errors When we use Python to parse XML, sometimes we may encounter some
 Python parsing special characters and escape sequences in XML
Aug 08, 2023 pm 12:46 PM
Python parsing special characters and escape sequences in XML
Aug 08, 2023 pm 12:46 PM
Python parses special characters and escape sequences in XML XML (eXtensibleMarkupLanguage) is a commonly used data exchange format used to transfer and store data between different systems. When processing XML files, you often encounter situations that contain special characters and escape sequences, which may cause parsing errors or misinterpretation of the data. Therefore, when parsing XML files using Python, we need to understand how to handle these special characters and escape sequences. 1. Special characters and