What are the basic knowledge points of computer network
Ⅰ. Division of network levels
In order to establish computer networks on a larger scale, the International Organization for Standardization (ISO) In 1978, the "Open System Internet Reference Model" was proposed, the famous OSI (Open System Interconnection) model.
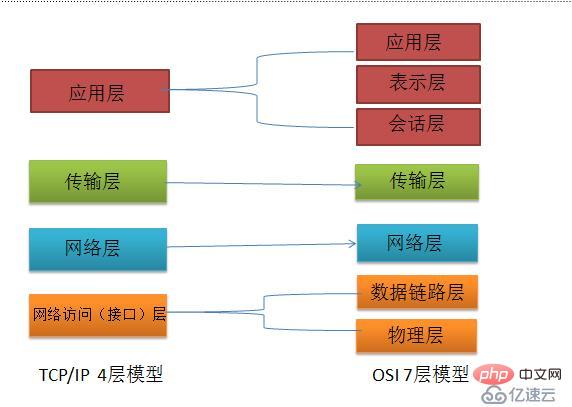
Ⅱ.OSI seven-layer network model
Whether it is the OSI seven-layer model or the TCP/IP four-layer model, each Each layer must have its own exclusive protocol to complete its corresponding work and communicate between the upper and lower layers. Let’s start with the detailed description of OSI’s seven-layer model:⑴Physical layer
The physical layer is the most basic network structure, which is composed of various devices. This layer provides a reliable physical medium for transmitting data to the upper layer protocol. Simply put, the physical layer ensures that the original data is transmitted on various physical media.⑵Data link layer
The data link layer provides services to the network layer on the basis of the physical layer. Its most basic service is to Data originating from the network is reliably transmitted to the target machine network layer of adjacent nodes.Main protocol : Ethernet protocol;
Important equipment: bridges, switches;
⑶Network layer
The purpose of the network layer is to realize data transmission between two end systems;Important equipment: router
⑷Transport layer
The first end-to-end , host-to-host level; the transport layer is responsible for segmenting upper-layer data and providing end-to-end, reliable or unreliable transmission. In addition, the transport layer must also deal with end-to-end error control and flow control issues;Mainly included protocols: TCP protocol, UDP protocol;
Important equipment: Gateway
⑸ Session layer
The session layer manages the session process between hosts, that is, it is responsible for establishing, Manage and terminate sessions between processes. The session layer also uses checkpoints inserted into the data to achieve data synchronization.⑹Presentation layer
The presentation layer transforms the upper layer data or information to ensure that the application layer information of one host can be understood by the application program of another host. Data conversion at the presentation layer includes data encryption, compression, format conversion, etc.⑺Application layer
Provides an interface for the operating system or network application to access network services.Ⅲ.IP address
⑴IP address classification: (This refers to the IPv4 address defined by the IPv4 protocol. The entire address is composed of 32-bit binary)
Class A: The first binary bit is 0, the network bit is 8 bits; 0.0.0.0~127.255.255.255
⑵A, B, C Class private address
In order to solve the problem of IP address exhaustion, increase the number of times the IP address is taken; it can be reused, and the Internet cannot route it Class A: 10.0.0.0/8, the range is: 10.0.0.0~10.255.255.255
Class B: 172.16.0.0/12, the range is: 172.16.0.0~172.31.255.255
Class C: 192.168.0.0/16, the range is 192.168.0.0~192.168.255.255
⑶ Reserved address (loopback address), cannot be Select the IP address used for configuration of other hosts,
0.0.0.0~0.255.255.255
127.0.0.0~127.255.255.255
⑷Automatically assign address segment:
169.254.0.0~169.254.255.255
⑸Network address: an address where the host bits are all 0 (All binary bits are 0)
For example: 1.0.0.0 represents the name of a range
⑹Broadcast address: An address with all host bits set to 1
For example: 1.255.255.255: As the destination address, it represents all IP addresses in the entire network segment
⑺Directed broadcast address :
255.255.255.255: As the destination address, it represents all IP addresses in the entire IP address stack
IV. Division of subnet masks
With the continuous expansion of Internet applications, the disadvantages of IPv4 are gradually exposed, that is, too many network bits are occupied, and too few host bits are used, so the host addresses it can provide are becoming increasingly scarce. Currently, in addition to In addition to using NAT to allocate reserved addresses within the enterprise, a high-class IP address is usually subdivided to form multiple subnets for use by user groups of different sizes.
Subnetting is actually to increase the number of network bits in the IP address and reduce the number of host bits; in this way, the scope of the broadcast domain can be reduced, the number of hosts in the logical network segment can be reduced, and management can be facilitated and precise application of security policies;
Ⅴ.TCP/IP protocol
The TCP/IP protocol is the most basic protocol of the Internet, which is composed of the network layer The IP protocol is composed of the TCP protocol at the transport layer;
TCP is a connection-oriented communication protocol. A connection is established through a three-way handshake. When the communication is completed, the connection must be dismantled. Since TCP is connection-oriented, it can only be used for end-to-end communication. TCP provides a reliable data flow service. TCP uses a method called "sliding window" for flow control. The so-called window actually represents the receiving capability and is used to limit the sending speed of the sender.
TCP message header format:
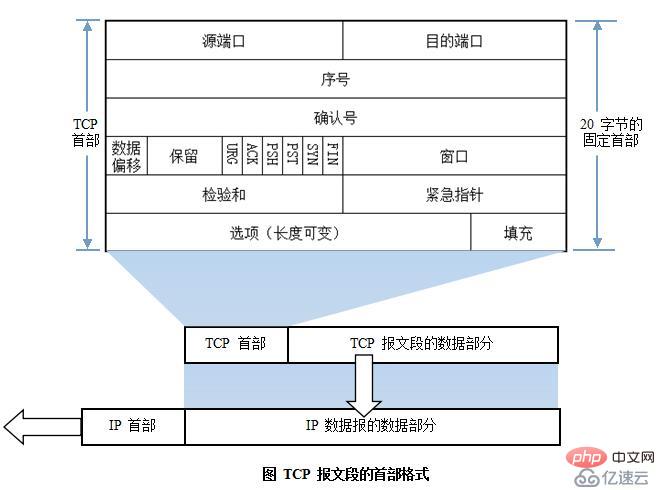
16-bit source port
16-bit destination port number
32-bit sequence number: range (1 ~ 2^32-2) SEQ
The first data The sequence number of the segment is randomly selected;
The sequence number of the second data segment: The sequence number of the previous data segment The data part size of the previous data segment 1
3 2 confirmation number: range (2 ~ 2^32-1)
This receiver used to confirm the data that has been received , and requires the sender to continue transmitting the identification of subsequent data segments; Generally speaking, the confirmation number is the sequence number of the next data segment to be sent by the sender;4 digits The header length is 24 bytes to 60 bytes
3-digit reserved flag
3 Certification encryption logo seat
# 6 -bit TCP Features Bit:
URG: Emergency Poor Labeling Bit; if this logo position 1, the repost of the data The priority will be increased so that such data is forwarded first; if the URG flag bits of multiple data are set to 1 at the same time, the larger the 16-bit emergency pointer is, the higher the priority will be; ACK: Confirmation flag bit related to connection management; used to respond to the party that actively initiates a connection establishment request or teardown request; PSH: push bit, if the flag is set to 1, the receiving party can The data is not added to the cache queue and is directly handed over to the application process for processing; RST: Reset the connection flag; when the TCP connection is exhausted or fails, the flag of the TCP connection is rebuilt; SYN: Synchronization flag bit, used to signal the party that initiates a connection establishment request to initiate a connection during the process of establishing a TCP connection;FIN: End the connection logo position. If the logo position 1, the other party will guide the TCP connection will be dismantled and confirm it; Implement traffic negotiation and control to prevent network congestion;
Sliding window:
Congestion window: Emergency window: Window size , meaning the number of data segments we can transmit at one time;16-bit data segment checksum: verification information to ensure the integrity of the data;
16-bit emergency pointer: used to distinguish its priority when the URG flag bits are all set to 1;
Option: timestamp of data segment segmentation
Connection-oriented features of TCP protocol:
1. Connection establishment; three-way handshake
1) Generated by the sender A TCP header data. In the header, the source and destination ports are given by the application layer protocol; the sequence number is randomly selected, the confirmation number is 0, and the flag SYN is set to 1;
2) The receiver receives the After sending the SYN request data from the sender, it determines whether it can complete the data communication required by the other party; if it can, it returns a TCP header data generated by it; the source and destination ports are exactly the opposite of the previous data; the sequence number is random , the confirmation number is the sequence number of the other party's next data, and the SYN and ACK flags are set to 1 at the same time; 3) After the sender accepts the other party's response data, it checks whether its ACK flag is set to 1 ;If it is 1, check whether the SYN flag is set to 1. If it is also 1, confirm it; then generate the second TCP header data; the sequence number is the sequence number 1 of the previous data, and the confirmation number is the next data of the receiver. Serial number; ACK flag position 1;2. Dismantle the connection and wave four times
1) When all data transmission is completed, one party will take the initiative to send the signal to the other party Send a TCP header data with the FIN flag set to 1;
2) After the other party receives such data with the FIN set to 1, it responds with a confirmation data with ACK set to 1 3) The other party Actively send a data with FIN set to 1, requesting to tear down the connection 4) The active end party confirms and sends TCP header data with ACK set to 1;VI.UDP Protocol
UDP user data protocol is a connectionless communication protocol. UDP data includes destination port number and source port number information. Since communication does not require a connection, broadcast transmission can be achieved. UDP communication does not require confirmation from the receiver, it is an unreliable transmission, and packet loss may occur;
UDP and TCP are on the same layer;
UDP header:
16-bit source port
1
6-digit destination port: The receiver of this data communication must transmit data from the transport layer to the application layer The port number used; generally speaking, the destination port number of the data is fixed; 16-bit UDP length
: The length of the entire datagram, including the header;1
6-digit UDP checksum: The checksum of the entire UDP datagram, ensuring data integrity to a certain extent.
The above is the detailed content of What are the basic knowledge points of computer network. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Is the metropolitan area network a public network?
Aug 31, 2022 am 10:53 AM
Is the metropolitan area network a public network?
Aug 31, 2022 am 10:53 AM
The metropolitan area network is a public network; the metropolitan area network is a computer communication network established within a city, referred to as MAN, and is a broadband local area network. Due to the use of local area network technology with active switching elements, the transmission delay in the network is small. It can be used as a backbone network to connect hosts, databases, and LANs located in different locations in the same city to each other.
 What is an open network system in a communication network?
Aug 22, 2022 pm 02:17 PM
What is an open network system in a communication network?
Aug 22, 2022 pm 02:17 PM
The open network system is an "all-channel communication network." An all-channel communication network is an all-round open communication network system in which all members can communicate and contact each other without restriction; in this communication network, the degree of centralization is low and the status difference between members is small. With high morale, members can express their opinions directly, freely and fully, which is conducive to brainstorming and improving the accuracy of communication. The disadvantage is that it can easily lead to low work efficiency.
 What are the resource sharing functions of computer networks?
Jul 15, 2022 pm 04:29 PM
What are the resource sharing functions of computer networks?
Jul 15, 2022 pm 04:29 PM
The resource sharing functions of computer networks include: 1. Hardware resource sharing, which can improve equipment utilization and avoid repeated investment in equipment; 2. Software resource sharing and data resource sharing, which can make full use of existing information resources and reduce the software development process. to avoid repeated construction of large databases; 3. Communication channel resource sharing means that the same channel can be used by multiple users at the same time, which can improve the utilization of channel resources.
 What does a computer network system in a school belong to?
Jul 13, 2022 pm 04:43 PM
What does a computer network system in a school belong to?
Jul 13, 2022 pm 04:43 PM
A computer network system within a school is a local area network (LAN). A local area network is a network composed of multiple computers used in a small area. The coverage is usually limited to 10 kilometers. It belongs to a small-scale network established by a unit or department. LAN can be divided into wireless LAN and wired LAN. Wireless LAN can transmit audio, video, and text. Now many companies and campuses are using wireless LAN.
 What are the most prominent features of computer networks?
Jan 13, 2021 pm 03:13 PM
What are the most prominent features of computer networks?
Jan 13, 2021 pm 03:13 PM
The most prominent feature of computer networks is resource sharing. Resource sharing is one of the main purposes for people to establish computer networks. Usually, the resources required by multiple users at the same time always exceed the number of actual physical resources of the system. However, using logical (or virtual) resource allocation to realize resource sharing can better handle this contradiction and improve the efficiency of computer use.
 What are the topologies of computer networks?
Feb 22, 2023 am 11:30 AM
What are the topologies of computer networks?
Feb 22, 2023 am 11:30 AM
The topology of a computer network refers to the physical structure of nodes and lines formed by computers or equipment on the Internet and transmission media. It mainly includes star topology, bus topology, ring topology, tree topology, and hybrid topology. , network topology, switching power supply topology; among them, star network topology is the most widely used network topology.
 Why does a company use an intranet?
Aug 22, 2022 pm 03:57 PM
Why does a company use an intranet?
Aug 22, 2022 pm 03:57 PM
Reasons for using an intranet: 1. Resource sharing, which can provide convenient sharing of software and hardware resources, especially in the direction of hardware resources. Office automation equipment such as printers and scanners are fully utilized. 2. Facilitate teamwork. Most modern LANs provide a platform that allows multiple users to work on the same file and always use the latest version. 3. It is easy to find information, and the intranet can be used as a place to place all trusted information. 4. Reduce management costs. With the help of the intranet, online forms can be easily provided, streamlining the work process from the beginning, and greatly improving work efficiency.
 How to solve computer network connection error 711 in win7 system
Jul 17, 2023 am 08:41 AM
How to solve computer network connection error 711 in win7 system
Jul 17, 2023 am 08:41 AM
Many friends who use win7 system must have encountered the problem of network connection error 711. How to solve the problem of network connection error 711 in win7 system? Today, the editor will bring you a solution to the network connection error 711 on Windows 7 computers. How to solve the computer network connection error 711 in win7 system: 1. Open "Computer", find the "C:\Windows\System32\LogFiles folder, right-click and select Properties"; 2. Click "Security Options, select Advanced"; 3. Click "Owner", select "Edit"; 4. Select the account "aaa" currently in use and click OK; 5.






