How to conduct web penetration skills analysis
Currently, with the continuous development of information networks, people's awareness of information security is increasing day by day, and the security protection measures of information systems are also gradually improving. Firewalls are usually deployed at the Internet boundary of the server to isolate internal and external networks, only external needs are The server port is exposed. Adopting this measure can greatly improve the security level of the information system. For external attackers, it is like closing all irrelevant channels, leaving only a necessary entrance.
But in this state, there is still a type of security problem that cannot be avoided, and that is web vulnerability. The reason is that the user's input characters are not strictly filtered when the program is written, allowing hackers to carefully construct a malicious string to achieve their own goals.
So, how can we find out whether there are such security issues? Below we will list a few relatively simple penetration techniques.
XSS Vulnerability
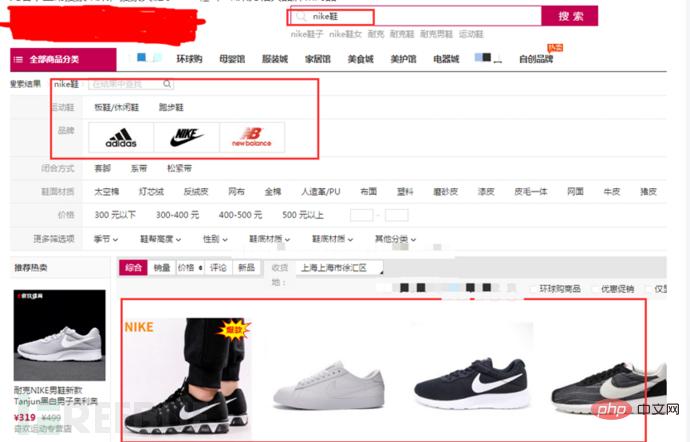
Try to find all the places that are user-controllable and can be output in the page code, such as the following: each parameter of the URL, the URL itself, Common scenarios for forms and search boxes (including comment areas, message areas, personal information, order information, search boxes, current directories, image attributes, etc.), then enter the code <script>alert(hello)</script> . If it is as shown in the picture below, then please be aware that your system is likely to be subject to a cross-site scripting attack.

Cross-site scripting attack XSS malicious attackers will insert malicious Script code into the Web page. When the user browses the page, the Script code embedded in the Web will be executed to achieve the purpose of maliciously attacking users.
XSS attacks are aimed at user-level attacks! Stored XSS, persistence, code is stored in the server, such as inserting code in personal information or published articles, etc. If there is no filtering or the filtering is not strict, then these codes will be stored in the server, and when the user accesses the page Trigger code execution. This kind of XSS is more dangerous and can easily cause worms, cookie theft, etc.
SQL injection
[SQL statement targeted: $sql="select*from admin where id=".$id;]
Normal Visit: www.linuxtest.com/test2.php?id=1
Find the injection point:
1. Abnormal access to www.linuxtest/test2.php?id=1', the result Returning to an abnormal page indicates that there may be an injection node. Continue with the verification below.
2. Continue to access www.linuxtest/test2.php?id=1 and 1=1 abnormally, and the result is returned to the normal page.
3. Continue to access www.linuxtest/test2.php?id=1 and 1=2 abnormally. The result is an abnormal page returned with an injection node. You can add attack SQL statements directly after id=1.
[Other SQL1 statements: $sql="select*from admin where id=$id";]
Same as above
[Other SQL2 statements: $sql= "select*from admin where id='{$id}'";】
There is an injection point at this time, but we must eliminate the single quotes to insert the corresponding attack SQL. The methods are:
Add (and '=) to eliminate; for example: test2.php?id=1' union select 1,2,3 and '=; the resulting SQL is: select*from admin where id='1' union select 1 ,2,3 and '='
Increase (and "='), (union select 1,2,'3), etc.
Due to different system environments, attackers may cause The damage is different, which is mainly determined by the security permissions of the application to access the database. If the user's account has administrator or other higher-level permissions, the attacker may perform various operations he wants to do on the database tables, including adding , delete or update data, or even delete the table directly.
The above is a direct manual operation, and the following will lead you to witness the penetration of the burp_suite tool.
When you need to initiate a request, the system will be intercepted It is in the startup state as shown below (taking a certain website as an example):
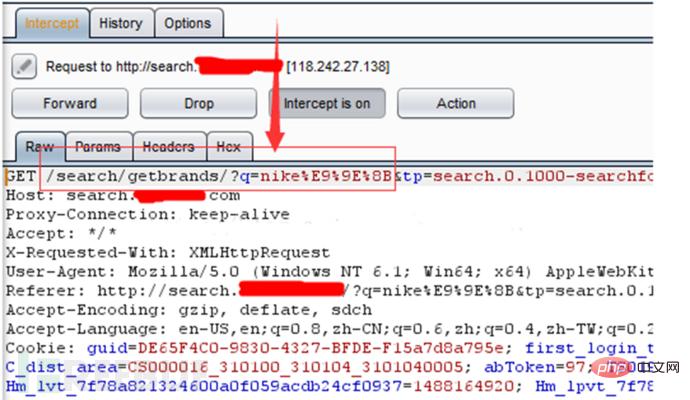
When you enter the page you want to modify and tamper with the parameters Click Close. If successful, the page will return the parameters you modified. This is the interception tampering vulnerability.
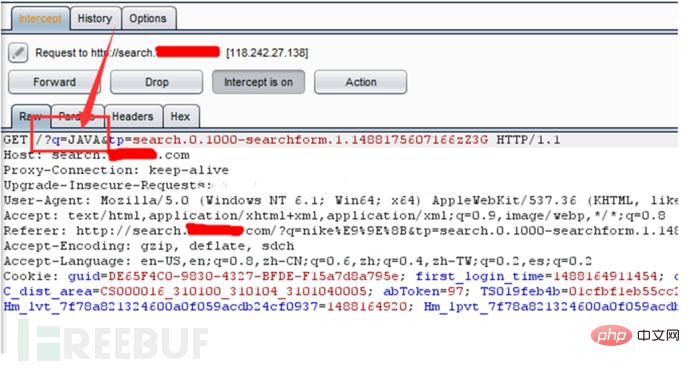
Result:
In most cases, burpsuite completes vulnerability attacks by tampering with parameters. You can see that the web page is directly tampered with. This situation not only reduces the customer experience, but also faces operational risks. , or even legal risks, resulting in a series of risks such as public relations crises.
The above is the detailed content of How to conduct web penetration skills analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
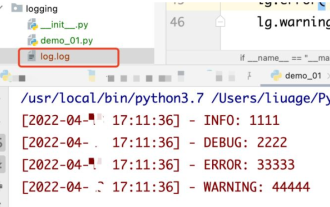 How to use python+Flask to realize real-time update and display of logs on web pages
May 17, 2023 am 11:07 AM
How to use python+Flask to realize real-time update and display of logs on web pages
May 17, 2023 am 11:07 AM
1. Log output to file using module: logging can generate a custom level log, and can output the log to a specified path. Log level: debug (debug log) = 5) {clearTimeout (time) // If all results obtained 10 consecutive times are empty Log clearing scheduled task}return}if(data.log_type==2){//If a new log is obtained for(i=0;i
 How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
Introduction to Caddy Caddy is a powerful and highly scalable web server that currently has 38K+ stars on Github. Caddy is written in Go language and can be used for static resource hosting and reverse proxy. Caddy has the following main features: Compared with the complex configuration of Nginx, its original Caddyfile configuration is very simple; it can dynamically modify the configuration through the AdminAPI it provides; it supports automated HTTPS configuration by default, and can automatically apply for HTTPS certificates and configure it; it can be expanded to data Tens of thousands of sites; can be executed anywhere with no additional dependencies; written in Go language, memory safety is more guaranteed. First of all, we install it directly in CentO
 Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Face-blocking barrage means that a large number of barrages float by without blocking the person in the video, making it look like they are floating from behind the person. Machine learning has been popular for several years, but many people don’t know that these capabilities can also be run in browsers. This article introduces the practical optimization process in video barrages. At the end of the article, it lists some applicable scenarios for this solution, hoping to open it up. Some ideas. mediapipeDemo (https://google.github.io/mediapipe/) demonstrates the mainstream implementation principle of face-blocking barrage on-demand up upload. The server background calculation extracts the portrait area in the video screen, and converts it into svg storage while the client plays the video. Download svg from the server and combine it with barrage, portrait
 Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web Server Processing in JavaAPI Development With the development of the Internet, the Web server has become the core part of application development and is also the focus of many enterprises. In order to meet the growing business needs, many developers choose to use Jetty for web server development, and its flexibility and scalability are widely recognized. This article will introduce how to use Jetty7 in JavaAPI development for We
 How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
Form validation is a very important link in web application development. It can check the validity of the data before submitting the form data to avoid security vulnerabilities and data errors in the application. Form validation for web applications can be easily implemented using Golang. This article will introduce how to use Golang to implement form validation for web applications. 1. Basic elements of form validation Before introducing how to implement form validation, we need to know what the basic elements of form validation are. Form elements: form elements are
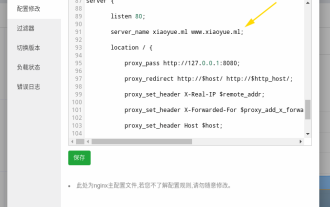 How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
First of all, you will have a doubt, what is frp? Simply put, frp is an intranet penetration tool. After configuring the client, you can access the intranet through the server. Now my server has used nginx as the website, and there is only one port 80. So what should I do if the FRP server also wants to use port 80? After querying, this can be achieved by using nginx's reverse proxy. To add: frps is the server, frpc is the client. Step 1: Modify the nginx.conf configuration file in the server and add the following parameters to http{} in nginx.conf, server{listen80
 What are web standards?
Oct 18, 2023 pm 05:24 PM
What are web standards?
Oct 18, 2023 pm 05:24 PM
Web standards are a set of specifications and guidelines developed by W3C and other related organizations. It includes standardization of HTML, CSS, JavaScript, DOM, Web accessibility and performance optimization. By following these standards, the compatibility of pages can be improved. , accessibility, maintainability and performance. The goal of web standards is to enable web content to be displayed and interacted consistently on different platforms, browsers and devices, providing better user experience and development efficiency.
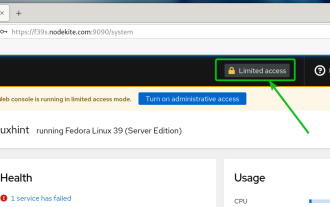 How to enable administrative access from the cockpit web UI
Mar 20, 2024 pm 06:56 PM
How to enable administrative access from the cockpit web UI
Mar 20, 2024 pm 06:56 PM
Cockpit is a web-based graphical interface for Linux servers. It is mainly intended to make managing Linux servers easier for new/expert users. In this article, we will discuss Cockpit access modes and how to switch administrative access to Cockpit from CockpitWebUI. Content Topics: Cockpit Entry Modes Finding the Current Cockpit Access Mode Enable Administrative Access for Cockpit from CockpitWebUI Disabling Administrative Access for Cockpit from CockpitWebUI Conclusion Cockpit Entry Modes The cockpit has two access modes: Restricted Access: This is the default for the cockpit access mode. In this access mode you cannot access the web user from the cockpit




