 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 How to reproduce the RCE vulnerability of unauthorized access to the XXL-JOB API interface
How to reproduce the RCE vulnerability of unauthorized access to the XXL-JOB API interface
How to reproduce the RCE vulnerability of unauthorized access to the XXL-JOB API interface
XXL-JOB Description
XXL-JOB is a lightweight distributed task scheduling platform. Its core design goals are rapid development, easy learning, lightweight, and easy expansion. The source code is now open and connected to the online product lines of many companies, ready to use out of the box.
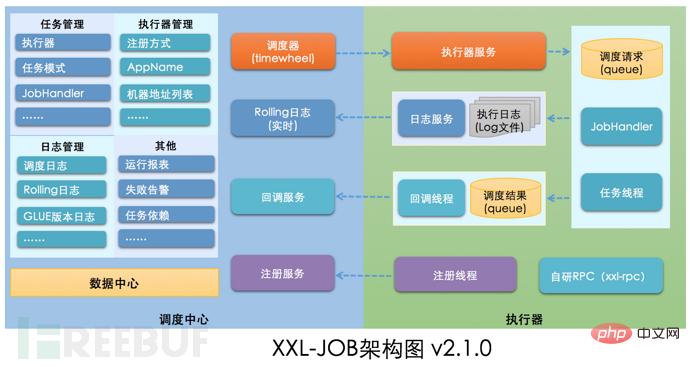
1. Vulnerability details
The core issue of this vulnerability is GLUE mode. XXL-JOB supports multi-language and script tasks through "GLUE mode". The task features of this mode are as follows:
● Multi-language support: supports Java, Shell, Python, NodeJS, PHP, PowerShell...etc. type.
● Web IDE: Tasks are maintained in the dispatch center in source code form and support online development and maintenance through Web IDE.
● Dynamic effect: The task code developed by the user online through the Web IDE is pushed to the executor remotely and loaded in real time for execution.
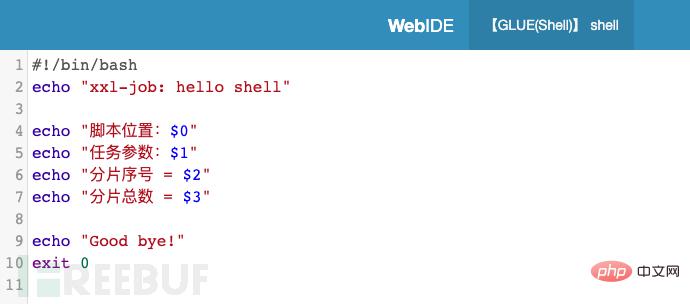
#As shown in the figure above, if you write attack code in the GLUE mode task code and push it to the executor for execution, you can cause remote attacks.
[Vulnerability Description]
The Restful API interface or RPC interface of XXL-JOB is not configured with authentication measures. Unauthorized attackers can construct malicious requests and cause remote execution. Command
[Vulnerability Rating]
High Risk
[Affected Version]
XXL-JOB <= 2.2.0
2. Environment setup
Overall idea: Source code download->Maven installation dependencies->Configuration and deployment "Scheduling Center"- >Configure deployment "executor project"->Complete deployment
Local development environment: Java8 Maven3.6
1. Github download source code
Address: https: //github.com/xuxueli/xxl-job/releases/tag/v2.2.0
2. Maven downloads the required dependencies
Idea opens the decompressed source code and automatically installs the relevant dependencies in the pom. You can also use the maven command in the terminal to download the required dependencies
3. Database configuration
The location of the scheduling database initialization SQL script is:
/xxl-job/doc/db/tables_xxl_job.sql
Because the local To install mysql, use docker to install it.
a) docker pull mysql:5.7
b) sudo docker run -p 3306:3306 --name mysql -e MYSQL_ROOT_PASSWORD=123456 -d mysql:5.7
This way We started the mysql container, the account is root, the password is 123456
Use navicat to connect to the database
 You can click on the lower left corner to complete the test connection. Right-click the imported database, select Run SQL file, and click Start to complete the database import.
You can click on the lower left corner to complete the test connection. Right-click the imported database, select Run SQL file, and click Start to complete the database import.
4. Configure and deploy the "Scheduling Center"
Scheduling center project: xxl-job-admin
Function: Unified management of scheduling tasks on the task scheduling platform, responsible for triggering scheduling execution, and providing a task management platform. You can modify the database configuration in application.properties according to the actual situation
Execute XxlJobAdminApplication to start the dispatch center
 We use the recommended Springboot to manage execution Check the configuration file and find the xxl.job.executor.logpath parameter. We can create or modify the path to prevent problems with program execution. The data path does not exist in the new Mac system. It was found that using mkdir to create the path failed. This is because Sip is turned off in the Mac system. Use sudo mount -uw / to remove Sip restrictions. Run XxlJobExecutorApplication to start the executor. Open //localhost:8080/ in the browser and see the login interface. Make sure the startup is successful. The default login account is "admin/123456"
We use the recommended Springboot to manage execution Check the configuration file and find the xxl.job.executor.logpath parameter. We can create or modify the path to prevent problems with program execution. The data path does not exist in the new Mac system. It was found that using mkdir to create the path failed. This is because Sip is turned off in the Mac system. Use sudo mount -uw / to remove Sip restrictions. Run XxlJobExecutorApplication to start the executor. Open //localhost:8080/ in the browser and see the login interface. Make sure the startup is successful. The default login account is "admin/123456"
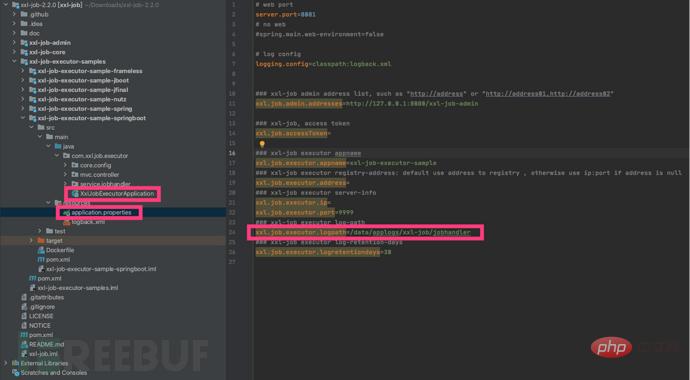
 It is recommended to create /data/applogs/xxl-job first, and use this path for many configuration files in the program
It is recommended to create /data/applogs/xxl-job first, and use this path for many configuration files in the program
Modify the dispatch center database configuration
Linux/Unix can use lsof to check the port occupancy , to prevent startup failure
The dispatch center and the executor can be deployed separately according to the actual situation
3. Vulnerability recurrence
View the official documentation and you can see the task triggered in the executor RESTful API Interface description
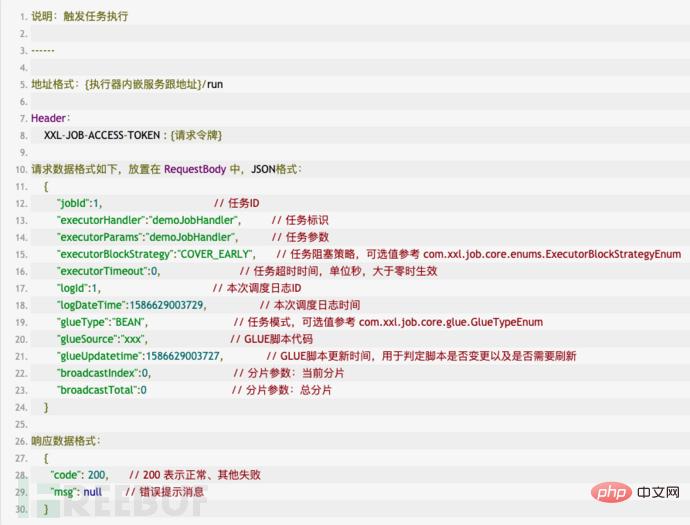 The task running modes are as follows
The task running modes are as follows
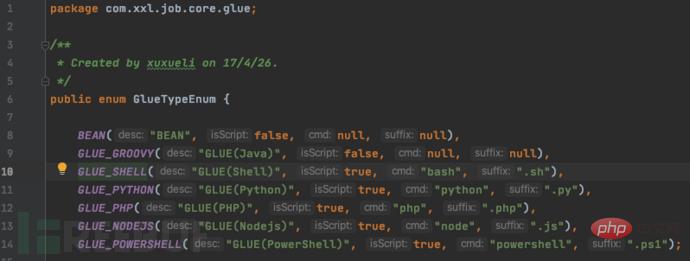
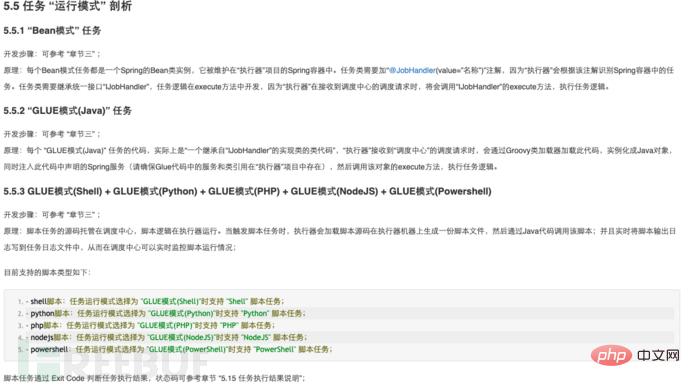 View GulueTypeEnum source code
View GulueTypeEnum source code
 So we use Burpsuite to construct our POC
So we use Burpsuite to construct our POC
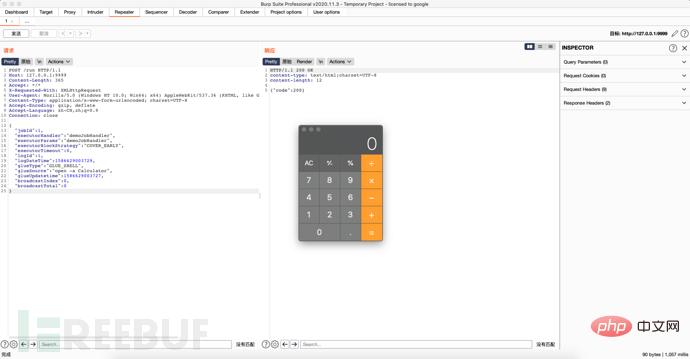
Tips:
When modifying glueSource, if the execution does not take effect, please modify the jobId
When restarting the project, it is found that the port startup exception is , please close BurpSuite
Since the official version of XXL-JOB comes with its own authentication component, it can ensure the security of the underlying communication of the system when turned on. The author of XXL-JOB stated that under normal circumstances, the underlying communication between the dispatch center and the executor is safe, and there is no remote command vulnerability. However, if the access token is not enabled on the executor, illegal scheduling requests cannot be identified and intercepted. Malicious requesters can use GLUE mode to push malicious attack code to achieve remote attacks. Therefore, the author of XXL-JOB believes that this problem is not a "vulnerability" in nature. The official website version provides an authentication component, which can be turned on for protection.
4. Repair suggestions
1. Turn on the authentication component that comes with XXL-JOB: Search for "xxl.job.accessToken" in the official documentation and follow the documentation instructions Just enable it.
2. Port access restrictions: By configuring security group restrictions, only specified IPs can access the port
The above is the detailed content of How to reproduce the RCE vulnerability of unauthorized access to the XXL-JOB API interface. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 PHP and Manticore Search Development Guide: Quickly Create a Search API
Aug 07, 2023 pm 06:05 PM
PHP and Manticore Search Development Guide: Quickly Create a Search API
Aug 07, 2023 pm 06:05 PM
PHP and ManticoreSearch Development Guide: Quickly Create a Search API Search is one of the indispensable features in modern web applications. Whether it is an e-commerce website, social media platform or news portal, it needs to provide an efficient and accurate search function to help users find the content they are interested in. As a full-text search engine with excellent performance, ManticoreSearch provides us with a powerful tool to create excellent search APIs. This article will show you how to
 How to crawl and process data by calling API interface in PHP project?
Sep 05, 2023 am 08:41 AM
How to crawl and process data by calling API interface in PHP project?
Sep 05, 2023 am 08:41 AM
How to crawl and process data by calling API interface in PHP project? 1. Introduction In PHP projects, we often need to crawl data from other websites and process these data. Many websites provide API interfaces, and we can obtain data by calling these interfaces. This article will introduce how to use PHP to call the API interface to crawl and process data. 2. Obtain the URL and parameters of the API interface. Before starting, we need to obtain the URL of the target API interface and the required parameters.
 React API Call Guide: How to interact and transfer data with the backend API
Sep 26, 2023 am 10:19 AM
React API Call Guide: How to interact and transfer data with the backend API
Sep 26, 2023 am 10:19 AM
ReactAPI Call Guide: How to interact with and transfer data to the backend API Overview: In modern web development, interacting with and transferring data to the backend API is a common need. React, as a popular front-end framework, provides some powerful tools and features to simplify this process. This article will introduce how to use React to call the backend API, including basic GET and POST requests, and provide specific code examples. Install the required dependencies: First, make sure Axi is installed in the project
 Oracle API Usage Guide: Exploring Data Interface Technology
Mar 07, 2024 am 11:12 AM
Oracle API Usage Guide: Exploring Data Interface Technology
Mar 07, 2024 am 11:12 AM
Oracle is a world-renowned database management system provider, and its API (Application Programming Interface) is a powerful tool that helps developers easily interact and integrate with Oracle databases. In this article, we will delve into the Oracle API usage guide, show readers how to utilize data interface technology during the development process, and provide specific code examples. 1.Oracle
 Save API data to CSV format using Python
Aug 31, 2023 pm 09:09 PM
Save API data to CSV format using Python
Aug 31, 2023 pm 09:09 PM
In the world of data-driven applications and analytics, APIs (Application Programming Interfaces) play a vital role in retrieving data from various sources. When working with API data, you often need to store the data in a format that is easy to access and manipulate. One such format is CSV (Comma Separated Values), which allows tabular data to be organized and stored efficiently. This article will explore the process of saving API data to CSV format using the powerful programming language Python. By following the steps outlined in this guide, we will learn how to retrieve data from the API, extract relevant information, and store it in a CSV file for further analysis and processing. Let’s dive into the world of API data processing with Python and unlock the potential of the CSV format
 How to develop a simple CRUD API using MongoDB
Sep 19, 2023 pm 12:32 PM
How to develop a simple CRUD API using MongoDB
Sep 19, 2023 pm 12:32 PM
How to use MongoDB to develop a simple CRUD API In modern web application development, CRUD (Create, Delete, Modify, Check) operations are one of the most common and important functions. In this article, we will introduce how to develop a simple CRUD API using MongoDB database and provide specific code examples. MongoDB is an open source NoSQL database that stores data in the form of documents. Unlike traditional relational databases, MongoDB does not have a predefined schema
 How to deal with Laravel API error problems
Mar 06, 2024 pm 05:18 PM
How to deal with Laravel API error problems
Mar 06, 2024 pm 05:18 PM
Title: How to deal with Laravel API error problems, specific code examples are needed. When developing Laravel, API errors are often encountered. These errors may come from various reasons such as program code logic errors, database query problems, or external API request failures. How to handle these error reports is a key issue. This article will use specific code examples to demonstrate how to effectively handle Laravel API error reports. 1. Error handling in Laravel
 Oracle API integration strategy analysis: achieving seamless communication between systems
Mar 07, 2024 pm 10:09 PM
Oracle API integration strategy analysis: achieving seamless communication between systems
Mar 07, 2024 pm 10:09 PM
OracleAPI integration strategy analysis: To achieve seamless communication between systems, specific code examples are required. In today's digital era, internal enterprise systems need to communicate with each other and share data, and OracleAPI is one of the important tools to help achieve seamless communication between systems. This article will start with the basic concepts and principles of OracleAPI, explore API integration strategies, and finally give specific code examples to help readers better understand and apply OracleAPI. 1. Basic Oracle API



