
Hello everyone, the writeup shared below was created by the author who discovered during the Tumblr user registration process that Tumblr’s “human-machine authentication” mechanism (reCAPTCHA) is flawed and can be easily bypassed. . The security risk caused by this bypass is that malicious attackers can create a large number of fake social accounts and enumerate usernames and emails for the accounts, which indirectly leads to abnormal traffic in the Tumblr website application and even leaks of user information.
On June 16 last year, HackerOne was held in London In the hackathon competition, the bounty paid for discovering vulnerabilities exceeded more than 80,000 US dollars. Vulnerability public testing is indeed an industry with a promising future. For public testing platforms, organized testing activities with bounties can not only motivate security researchers to discover vulnerabilities, but also improve the quality of reported vulnerabilities, and can also provide detailed vulnerability information. Forward it to the manufacturer for prompt repair.
Security is a complex subject, and even large companies will inevitably make mistakes. Enterprises often face uncertain security risks between internal resources and external attackers, and vulnerability public testing can make up for the existing security gaps. If your organization is unable to train or select high-quality and diverse security testers from within, you can use external public testing projects or consulting services to test security products or related systems and discover vulnerabilities.
Personally, I also encountered some bad experiences during the public testing process. I once reported a high-risk vulnerability to Myspace that allowed access to any account, but during lengthy negotiations with Myspace, they were simply indifferent and I ultimately chose to disclose the vulnerability (click here to read). This vulnerability affects nearly 360 million user accounts. I hope that public pressure can be used to prompt the vulnerability to be fixed. This behavior is also forced.
On the contrary, I once discovered a reCaptcha verification code bypass vulnerability of Tumblr company. After reporting it to them through Twitter, they directly messaged me to communicate. It only took two days to get the vulnerability. repair. The following is my sharing of the vulnerability discovery process.
When I visited www.tumblr.com for user registration, I found that the Google reCAPTCHA verification code service embedded in it had a misconfiguration vulnerability, that is In reCAPTCHA verification code requests sent by clients and applications, the parameter value named 'g-recaptcha-response' can be left blank. This vulnerability will affect all newly registered users and does not require any special tools to exploit. You only need to manually click the button that appears on the website or initiate modifications through a packet capture agent.
Generally speaking, if the Captcha mechanism is properly run and deployed, it has a rate limiting effect (Rate Limiting), which can be used to prevent spam users from creating fake social accounts and reduce specific Application request volume. The Tumblr page reCAPTCHA verification code bypass vulnerability I discovered can be used by attackers to create fake accounts. In addition, since Tumblr's user registration mechanism only allows the registered email address to be bound to a user name, this vulnerability can also be used to target users. Brute force enumeration attacks on email addresses and usernames. Repeated large-scale enumerations can lead to the leakage of Tumblr user registration information.
Let’s first look at the normal account creation process on the www.tumblr.com page. First, go to the login page https://www.tumblr.com/login and click The registration button "Sign up" in the upper right corner:
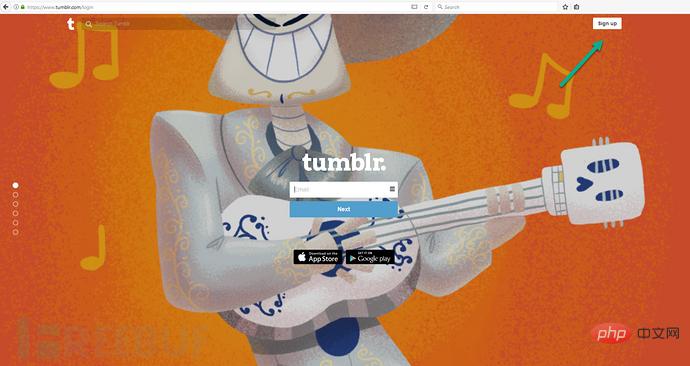
#Then it jumps to the account registration page https://www.tumblr.com/register:

Next, click the start button 'Get Started', and then some required options will appear, including username, password and email address:

After completing the above required fields, you also need to enter your age and check the terms of service:
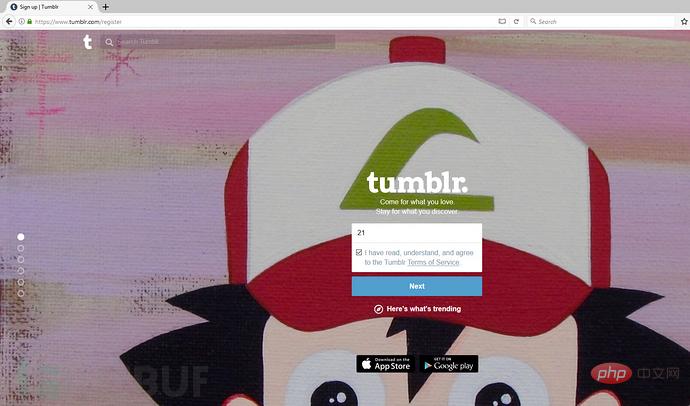
Next, a "human-machine authentication" (reCAPTCHA) will pop up )page:
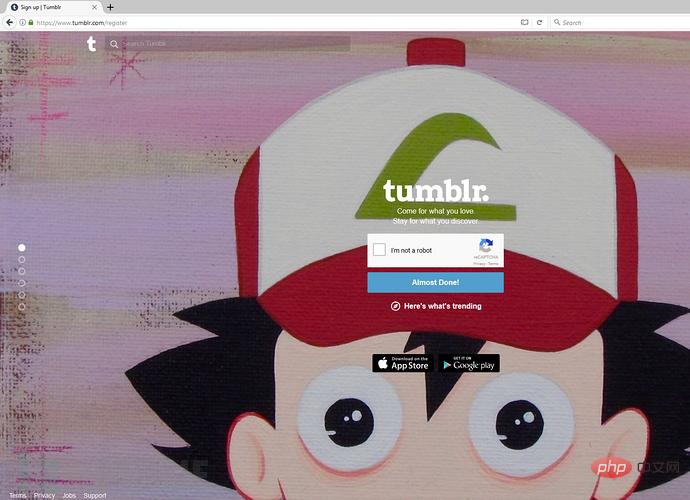
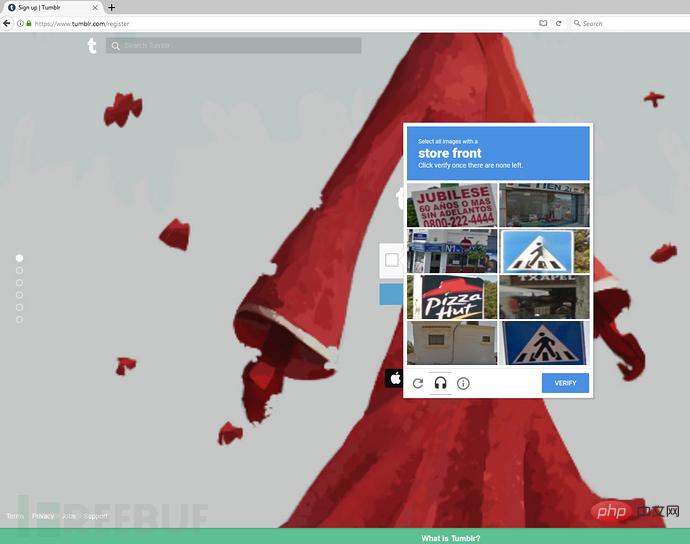
In addition to such a "human-machine authentication" (reCAPTCHA) option deployed here, there is also an option "Almost Done!" below it. The funny thing is that although generally you need to complete "Human-Machine Authentication" before proceeding to the next step, my test found that you can just ignore "I'm not a robot" in "Human-Machine Authentication". Simply click "Almost Done!" below to complete the so-called "human-machine authentication" here, and then go directly to the next step to the user's Tumblr homepage. Is this "human-computer authentication" (reCAPTCHA) deployment here just for show?
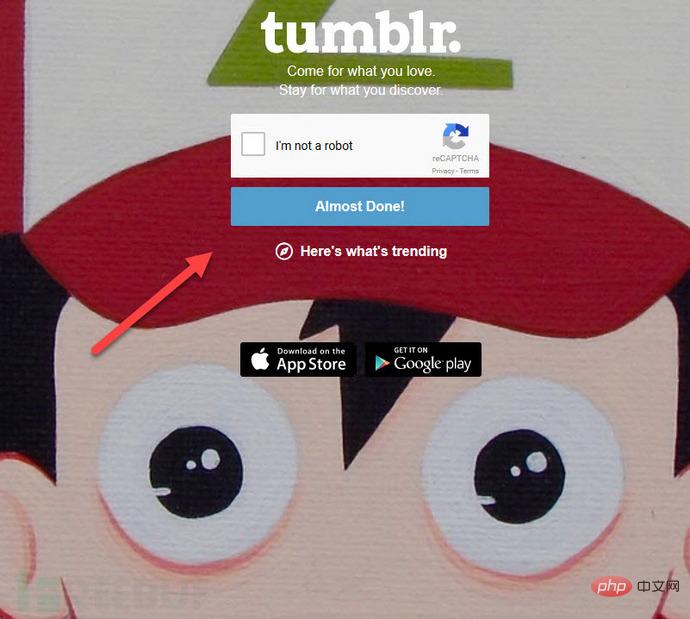
For in-depth analysis, we use Burp to take a look at the user's "human-machine authentication" (reCAPTCHA) step Initiate specific requests and responses.
The POST request when initiating "human-machine authentication" is as follows:
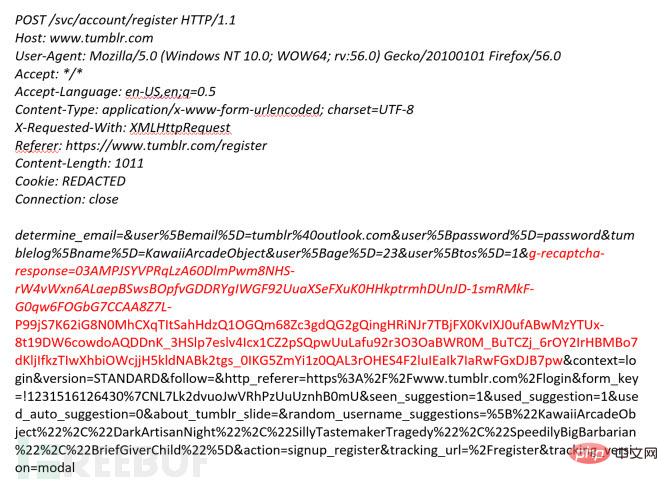
If you look closely at the above POST request, you can find that the recaptcha challenge is a The parameter value of 'g-recaptcha-response' is the red part in the picture above. But if we leave this parameter value blank, it is equivalent to not checking it. What will happen? The POST request constructed in this way is as follows:
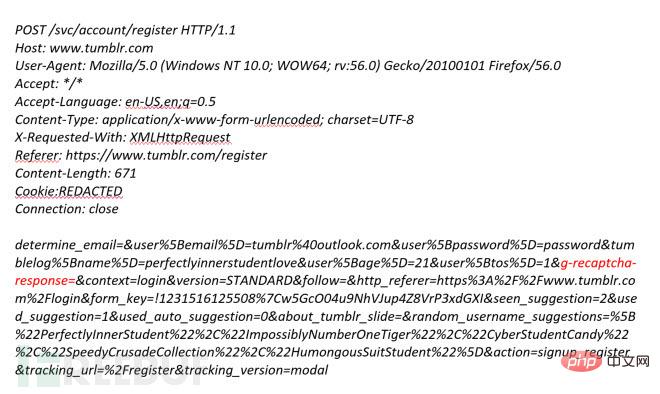
After testing, it was found that the Tumblr server returned the same and valid response to the above two POST requests:
 Of course, that is to say, the Tumblr server simply forgot to check the value of the 'g-recaptcha-response' parameter, which resulted in the above-mentioned "human-machine authentication" (reCAPTCHA) mechanism being bypassed.
Of course, that is to say, the Tumblr server simply forgot to check the value of the 'g-recaptcha-response' parameter, which resulted in the above-mentioned "human-machine authentication" (reCAPTCHA) mechanism being bypassed.
Although many website applications require a high degree of trust from the user base, authentication bypass vulnerabilities like this are also common in these websites. No, not long ago Google just fixed a vulnerability that completely bypasses reCAPTCHA.
The above is the detailed content of How to analyze and bypass reCAPTCHA verification during Tumblr user registration process. For more information, please follow other related articles on the PHP Chinese website!




