
Experimental configuration steps:
The first stage: iaskmp SA (the object to be protected by IKE SA is related to the key)
IKE does not directly care about user data, and IKE SA serves for secure negotiation of IPSec SA
1, shared key or digital certificate
IKE adopts Diffie-Hellman algorithm, the key is derived from the peer through the peer
group1 The key length is 768bit
group2 The key length is 1024bit
group5 The key length is 1536bit
is used for data The value of the encrypted key is calculated by the algorithm and cannot be defined or modified by the administrator
2. Verify neighbor (establish neighbor)
Second phase: IPsec SA (user The data traffic is actually transmitted on the IPSec SA)
IPSec SA directly serves user data flow. All security policies in IPSec SA are for the security of user data flow
1. Data encapsulation protocol (ESP\AH is a security protocol)
2. Working mode (transmission\transparent)
3. Encryption algorithm (DES\3DES\AES)
4 , Authentication method (MD5\SHA)
The third phase: Define the flow of interest (communication network segment, based on extended ACL)
The fourth phase: Security Association (SA)
1. Verify neighbor
2, Data encryption method
3, Interested flow
Phase 5: Interface call
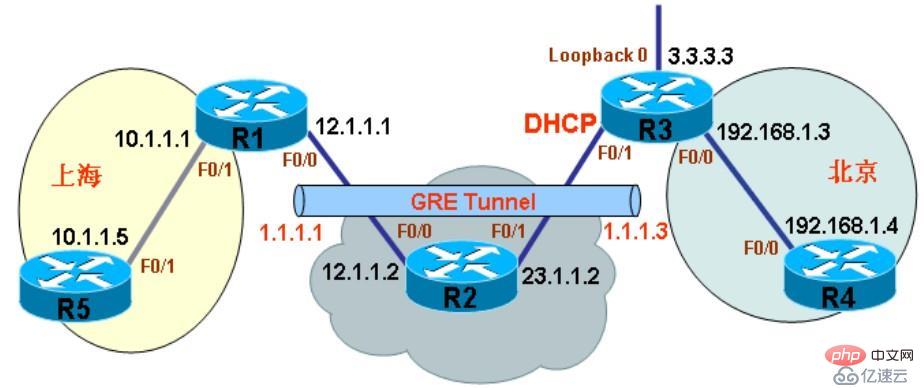
R1
Router>enable because
R1(config)#service timestamps debug datetime localtime
R1(config)#service timestamps log datetime localtime
R1(config)#interface f0/1 #no shutdown .1 255.255.255.0
R1(config -if)#no shutdown
R1(config-if)#exit
R1(config)#interface loop0 config-if)#no shutdown
R1(config-if)#exit
R1(config)#ip route 0.0.0.0 0.0.0.0 12.1.1.2
R1(config)#interface tunnel10
R1(config-if)#tunnel source 12.1.1.1
R1(config-if)#tunnel destination 23.1.1.3
R1(config-if)# ip address 172.16.1.1 255.255.255.0
R1(config-if)#tunnel mode gre ip
R1(config-if)#no shutdown
R1(config)#ip route 192.168.1.0 255.255.255.0 tunnel10
R1(config)#crypto isakmp policy 10 IKE first-stage authentication policy (ensure key security)
R1(config-isakmp)#authentication pre-share Authentication method
R1(config- isakmp)#encryption des IKE stage 1.5 encryption (data encryption, encryption method, default is DES)
R1(config-isakmp)#group 2 key algorithm (Diffie-Hellman)
group1(768bit), group2 (1024bit), group5 (1536bit), the default is group1
R1(config-isakmp)#hash md5 authentication method
R1(config-isakmp)#exit
R1(config)#crypto isakmp key 6 cisco address 23.1.1.3 255.255.255.0 Authentication
R1(config)#crypto isakmp keepalive 10 3 Send DPD every 10s to detect ××× establishment, if there is no reply within 3s, send it again 3 times
R1(config)#crypto ipsec transform-set cisco esp-des esp-md5-hmac isakmp policy, data encapsulation mode
R1(cfg-crypto-trans)#exit
R1(config)#ip access-list extended interested Define flow of interest
R1(config-ext-nacl )#permit gre host 12.1.1.1 host 23.1.1.3 The host for local communication and the host for peer communication
R1(config-ext-nacl)#permit ip 10.1.1.0 0.0.0.255 192.168.1.0 0.0.0.255 tunnel mode defines the flow of interest
R1(config-ext-nacl)#exit
R1(config)#crypto map IPSec*** 10 ipsec-isakmp security association (above association Data encapsulation method, stream of interest)
R1(config-crypto-map)# set peer 23.1.1.3
R1(config-crypto-map)#set transform-set cisco
R1(config-crypto-map)#match address interested
R1(config-crypto-map)#exit
R1(config)#interface f0/0 -if)#crypto map IPSec***
R1(config)#ip access-list extended nat
R1(config-ext-nacl)#10 permit ip 1.1.1.0 0.0.0.255 any
R1(config-ext-nacl)#exit
R1(config)#int loop0
R1(config-if)#ip nat inside
R1(config-if)#int s0/0
R1(config-if)#ip nat outside
R1(config-if)#exit
R1(config)#ip nat inside source list nat int f0/0 overload
R1(config)# ip nat inside source static udp 192.168.2.2 4500 interface f0/0 4500
R1(config)#ip nat inside source static udp 192.168.2.2 500 interface f0/0 500
R3
Router>enable because
R3(config)#service timestamps debug datetime localtime
R3(config)#service timestamps log datetime localtime
R3(config)#interface f0/0 no shutdown 255.255.255.0
R3(config- if)#no shutdown
R3(config-if)#exit
R3(config)#ip route 0.0.0.0 0.0.0.0 23.1.1.2
R3(config)#interface tunnel11 #R3(config-if)#tunnel source 23.1.1.3
R3(config-if)#tunnel destination 12.1.1.1
R3(config-if)# ip address 172.16.1.3 255.255.255.0
R3 (config-if)#tunnel mode gre ip
R3(config-if)#no shutdown
R3(config-if)#exit
R3(config)#ip route 10.1.1.0 255.255.255.0 tunnel11
R3(config)#crypto isakmp policy 10
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#encryption des
R3(config-isakmp) #group 2
R3(config-isakmp)#hash md5
R3(config-isakmp)#exit
R3(config)#crypto isakmp key 6 cisco address 12.1.1.1 255.255.255.0
R3(config)#crypto ipsec transform-set cisco esp-des esp-md5-hmac
R3(cfg-crypto-trans)#mode tunnel
R3(cfg-crypto-trans)#exit
R3(config)#ip access-list extended interested
R3(config-ext-nacl)#permit gre host 23.1.1.3 host 12.1.1.1
R3(config-ext-nacl)#exit
R3(config)#crypto map IPSec*** 10 ipsec-isakmp
R3(config-crypto-map)#set peer 12.1.1.1
R3(config-crypto-map)# set transform-set cisco
R3(config-crypto-map)#match address interested
R3(config-crypto-map)#exit
R3(config)#interface serial 0/1
R3(config-if)#crypto map IPSec***
IPSec also has the disadvantages of complex configuration, consuming more computing resources, increased latency, and not supporting multicast
View strategy :
show crypto isakmp policy Define domain shared key to establish *** connection
show crypto engine connections active View the number of encrypted and decrypted packets
clear crypto isakmp Clear the first phase of IKE
Traffic optimization:
access-list 101 permit esp host 12.1.1.1 host 23.1.1.3
access-list 101 permit udp host 12.1.1.1 host 23.1.1.3 eq isakmp
access-list 101 permit ip 10.1.1.0 0.0.0.255 192.168.1.0 0.0.0.255
First of all, there are MM (main mode) and brutal mode in the first stage, and QM (quick mode) in the second stage.
Secondly, the last two messages in the main mode are encrypted, which can provide identity protection function
The message integration in aggressive mode is too high, so there is no identity protection function
In aggressive mode (in this case, the responder cannot select the corresponding pre-shared key based on the IP address, that is, it does not rely on the IP address to identify the identity, making the aggressive mode The mode has better flexibility)
View the results through display ike sa
1. The first phase of ike sa has been successfully established
3. ike is using version v1
peer The status of this security association
flag displays the status of this security association
RD (ready) indicates that the SA has been established successfully
ST (stayalive) indicates that this end is the initiator of channel negotiation
RL (Replaced) means that this channel has been replaced by a new channel and will be deleted after a period of time
FD (Fading) means that this channel has experienced a soft timeout and is still in use. This channel will be deleted when a hard timeout occurs
TO (timeout) means that this SA has not received a keepalive message after the last keepalive timeout occurred. If the keepalive message is not received when the next keepalive timeout occurs, this SA will be deleted
TD (deleting ) indicates that the SA is about to be deleted
NEG (negotiating) indicates that the IKE SA is being negotiated, which is caused by inconsistencies in certain parameters set at both ends of the tunnel
D (DPD) indicates that the DPD detection function is enabled and is being negotiated Do DPD detection
M (active) indicates that the IKE SA status is primary
S (standby) indicates that the IKE SA status is standby
A(alone) indicates that the IKE SA status is Alone, and there is no backup between IPSec tunnels
The phase this SA belongs to: Phase1: The phase of establishing a secure channel for communication. This phase establishes the ISAKMP SA Phase2: The phase of negotiating security services. IPSec SA is established at this stage
The security association is uniquely identified by three elements (security protocol number (AH or ESP), destination IP address, security parameter index (SPI, Security Parameter Index))
Security The parameter index is a 32-bit value generated to uniquely identify the SA. It is transmitted in the IPsec header
IPSec-IKE aggressive mode
1. The problem of slow negotiation at both ends of the tunnel
2. Uncertainty of the initiator’s source address
(When the initiator’s IP address is dynamically allocated, the initiator’s IP address cannot be known by the responder in advance, and both parties intend to use pre-shared key verification. Method)
In tunnel mode, ESP messages can maintain the confidentiality of the original IP header data
Configuring the pre-shared key must be configured on both ends, and the keys on both sides must be consistent
In tunnel mode in IPSEC, ESP does not verify new IP packet header fields (tunnel mode encapsulates new headers and does not verify them)
IKE uses DH group2 default group by default
AH Features that can be implemented (AH protocol, AH is a message header verification protocol, the main functions provided are data source verification, data integrity verification and message replay prevention functions)
AH does not encrypt the protected data. All cannot complete confidentiality
IKE Internet Password Exchange Protocol: The IKE protocol is used to automatically negotiate the cryptographic algorithms used by AH and ESP
The above is the detailed content of How to configure IPsec instructions. For more information, please follow other related articles on the PHP Chinese website!




