EVE-NG Mirror Example Analysis
1. Download and unzip the compressed package ikuai-8.rar
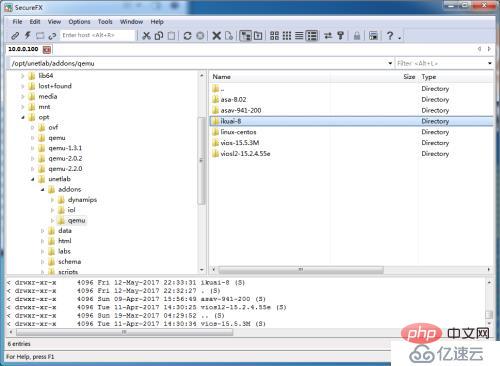
2. Upload to the /opt/unetlab/addons/qemu directory
3. Log in to EVE via SSH and execute the script
root@eve-ng:~# cd /opt/unetlab/addons/qemu/ikuai-8
root@eve-ng:/opt/unetlab/addons/qemu/ikuai-8#source ikuai.sh
Great!!! "iKuai Device" import successfully!!!
root@eve-ng:/opt/unetlab/addons/qemu/ikuai-8
#4. Test
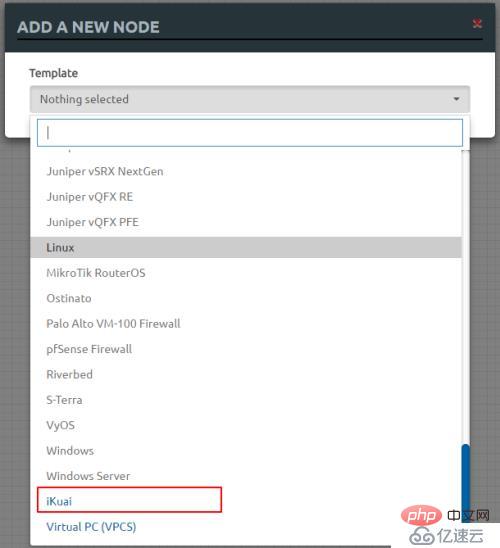
Device icon

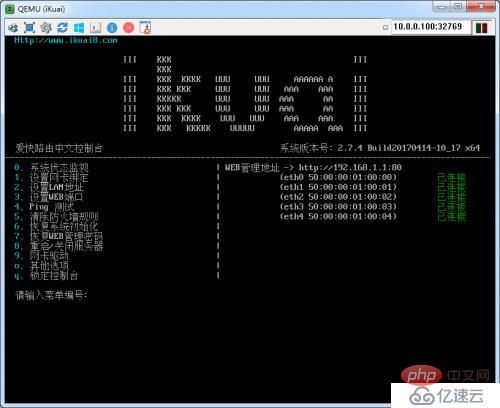
The device started successfully! ! !
【Panabit】
1. Download and unzip the compressed package panabit-v17.rar
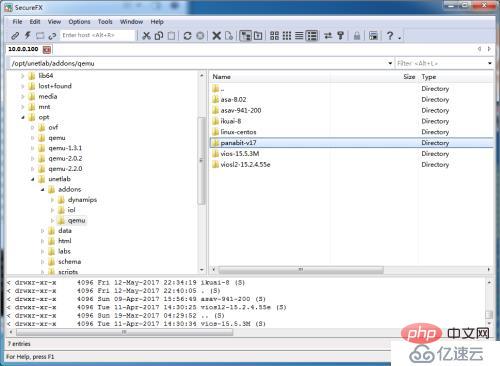 ##3. Log in to EVE via SSH and execute the script
##3. Log in to EVE via SSH and execute the script
root@eve-ng:/opt/unetlab/addons/qemu/panabit-v17#source panabit.sh
Great!!! " Panabit Device" import successfully!!!
root@eve-ng:/opt/unetlab/addons/qemu/panabit-v17
#4. Test
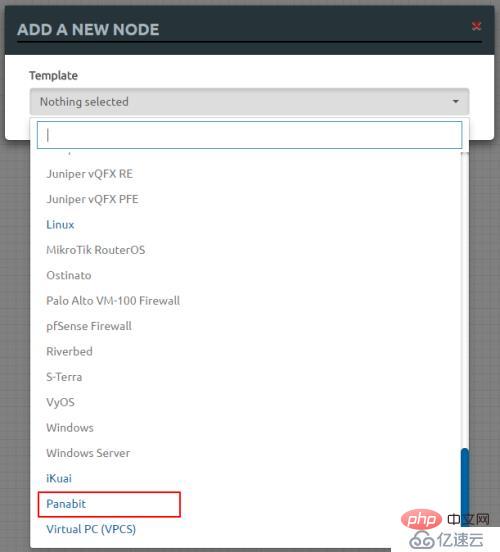 Device icon
Device icon

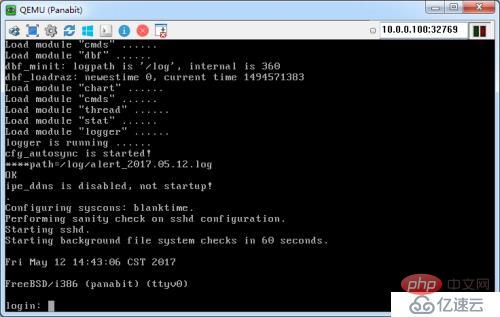 The device started successfully! ! !
The device started successfully! ! !
【FreeNAS】
1. Download and decompress the compressed package freenas-9.10.rar
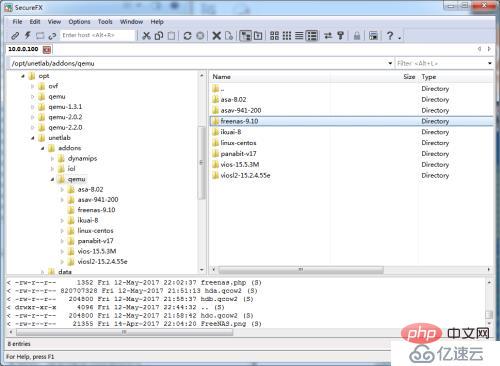
##2. Upload to /opt/unetlab /addons/qemu directory
Device iconGreat!!! "FreeNAS Device" import successfully!!!
root@eve-ng:/opt/unetlab/addons/qemu/freenas-9.10
#4. Test
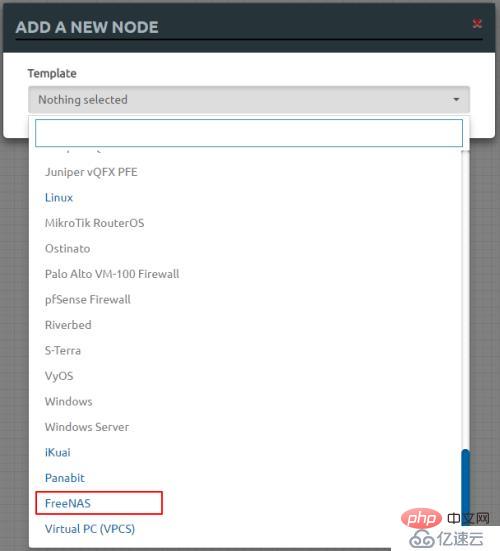

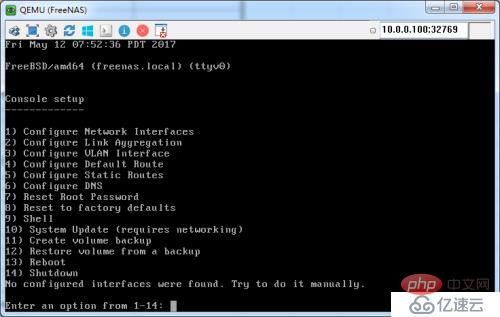
The above is the detailed content of EVE-NG Mirror Example Analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)





