
At present, the SpringBoot framework is becoming more and more widespread, and most small and medium-sized enterprises are developing new projects. When the back-end language uses java, SpringBoot is the first choice.
In many open source frameworks, such as: ruoyi, these.
I don’t know why? We will all find the dependencies of SpringBoot Actuator in the pom files in these frameworks.
Hey, this Actuator is estimated to have not been used by many people, but it will appear in the pom file; as a result, when doing some security vulnerability testing, it will appear Vulnerability issues.
For example:
We are starting to fix these vulnerabilities! ! !
Actuator is a functional module provided by Springboot for introspection and monitoring of application systems. With the help of Actuator developers can easily Use certain monitoring indicators of the system to view and make statistics.
The core of Actuator is the endpoint, which is used to monitor applications and interactions. There are many Endpoints built into spring-boot-actuator (health, info, beans, metrics, httptrace, shutdown, etc.) , and also allows us to extend our own Endpoints.
Each Endpoint can be enabled and disabled. To access Endpoint remotely, it must also be exposed through JMX or HTTP. Most applications choose HTTP.
Okay, Actuator looks pretty good and can be used for monitoring. However, most companies have probably never used it, so they will not be able to enjoy the benefits of Actuator.
Actuator While bringing convenience, if it is not managed well, it will lead to the leakage of some sensitive information; it may cause our server to be exposed to the external network, and the server may collapse . So let’s take a look, what security issues will arise?
For example, we can visit:
http://localhost:7200/actuator/env
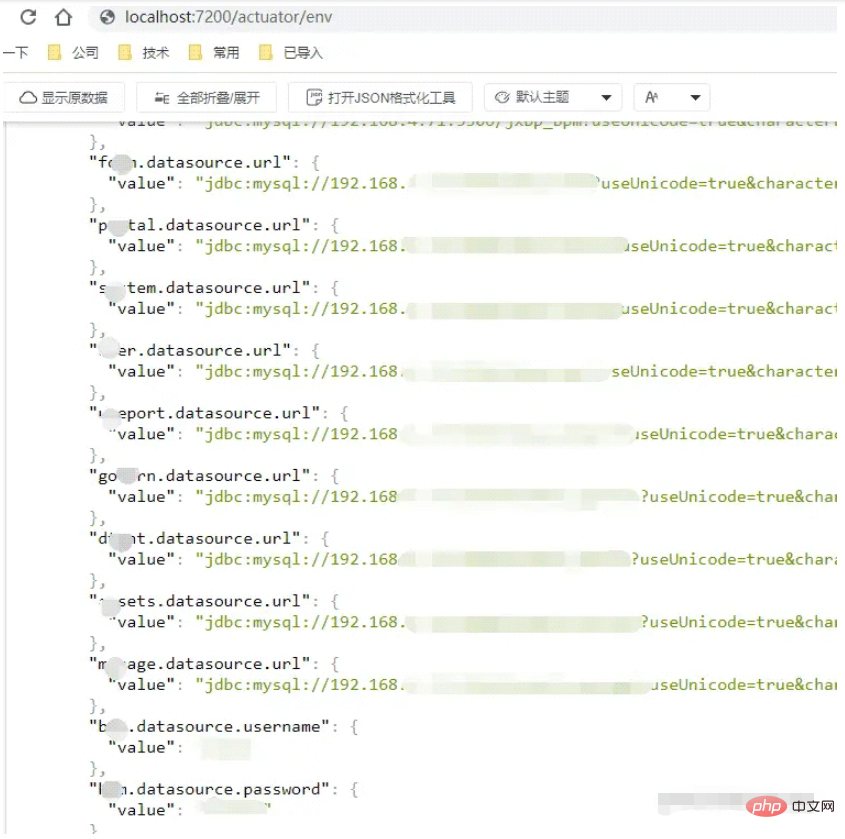
Did you see the above message? Wow, we can actually see the database connection address, account password and other information.
If these addresses are not controlled, wouldn't this be a serious vulnerability for some people with technical foundation? It is estimated to be a T0 level vulnerability.
How do we control these?
Add the following configuration in llsydn-dev.properties
management.endpoints.web.exposure.exclude=env,heapdump,threaddump,mappings
In this way, access to env will be prohibited.
Then let’s visit again, for example:
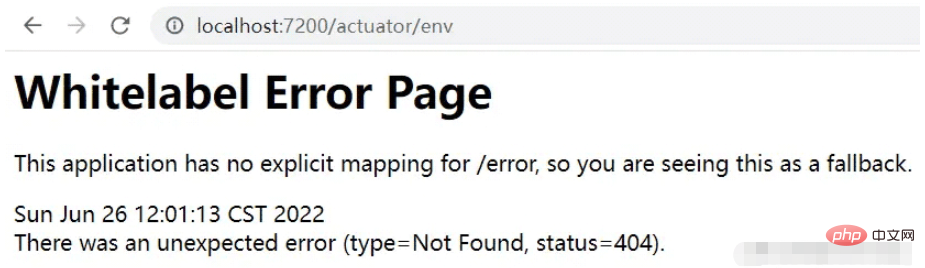
Okay, you can see that 404 appears when accessing, indicating that it has been banned.
For the above modification, it is actually possible to implement the method of disabling env, so that the corresponding interface information can basically be controlled, and basically it can be done Arrived safely.
However, when doing security vulnerability scanning, the corresponding vulnerability will still be scanned out. In fact, this vulnerability has not been solved. So can we ban Actuator completely?
The answer is definitely yes! ! !
For example, the following configuration:
# 完全禁用actuator management.server.port=-1
With this configuration, the vulnerability will not be scanned out after the security vulnerability scan is performed!
The above is the detailed content of How to fix SpringBoot Actuator unauthorized access vulnerability. For more information, please follow other related articles on the PHP Chinese website!
 SpringBoot project building steps
SpringBoot project building steps
 What is the difference between j2ee and springboot
What is the difference between j2ee and springboot
 Detailed explanation of nginx configuration
Detailed explanation of nginx configuration
 How to restart the service in swoole framework
How to restart the service in swoole framework
 Can Microsoft Visual C++ be uninstalled?
Can Microsoft Visual C++ be uninstalled?
 The Metaverse recognizes the top ten potential coins
The Metaverse recognizes the top ten potential coins
 What are the differences between weblogic and tomcat
What are the differences between weblogic and tomcat
 Usage of source command in linux
Usage of source command in linux




