How to conduct range practice with bee-box LDAP injection
If the essence of sql injection is splicing strings, then the essence of everything that can be injected is splicing strings. LDAP injection is no exception as a kind of injection. What is more interesting is that it is splicing parentheses ( SQL injection also concatenates parentheses, but it is more conventional to say that it concatenates strings).
In the environment configuration chapter, the configuration of the ldap environment in bee-box has been discussed in detail. The shooting range practice chapter is more about the connection process between php and ldap, and the introduction of the special functions used in the middle. Some tips for splicing parentheses.
Let’s first talk about the login process of the ldap shooting range in bwapp:
First of all, this is an LDAP login interface, the URL is http:/ /192.168.3.184/bWAPP/ldap_connect.php, take a look at what is written in this php file.
Detailed explanation of php connection LDAP function
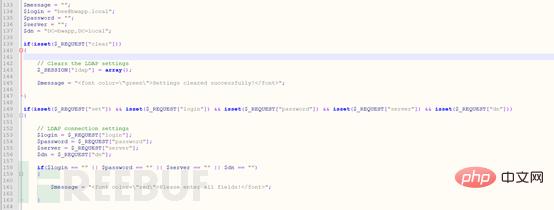
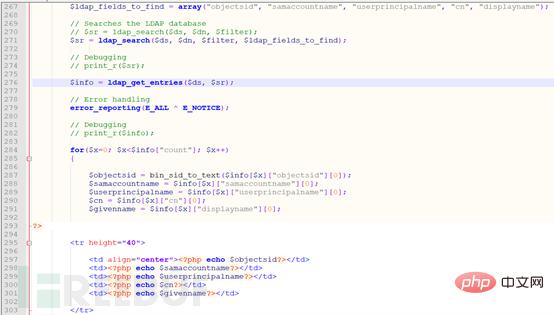
#Starting from the code of 133 of the ldap_connect.php file, the five variables are $message, $login, $ password, $server, $dn.
What is the first of these five variables used for? The second is the username to log in to the ldap server, the third is the password, the fourth is the server address, and the fifth is the distinguished name (describe one full LDAP path).
The first if statement is to clear the login LDAP form, and the second if statement is to determine whether the five variables are null values. These are all trivial matters. The key point is the following else. From this else At the beginning, there are multiple if and else statements. Let’s go one by one.
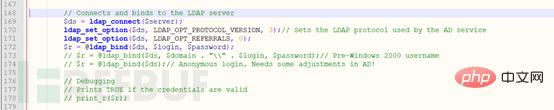
First look at the three functions ldap_connect, ldap_set_option, and ldap_bind before the first if, and explain the functions of these three functions in turn.
ldap_connect: used to connect to the ldap database, the format is as follows
$server = “localhost”
$LDAPCONN=LDAP_Connect($server)
If $ The return value of LDAPCONN is a numeric type. When the return result is 0, the connection fails, and when the return result is other values, the connection succeeds.
ldap_set_option($link_identifier,$option, &$retval): Receives three parameters
$link_identifier
The LDAP connection identifier returned by the ldap_connect() function (determines LDAP Whether the connection is successful)
$option can receive the following values:
LDAP_OPT_DEREF(int): How to handle aliases when searching, the value range is as follows: LDAP_DEREF_NEVER(0, default value), LDAP_DEREF_SEARCHING (1), LDAP_DEREF_FINDING(2), LDAP_DEREF_ALWAYS(3)
LDAP_OPT_NETWORK_TIMEOUT(int): Network timeout seconds, LDAP_NO_LIMIT(0, default value) means never timeout.
LDAP_OPT_PROTOCOL_VERSION(int): Specifies the LDAP protocol version used, the value range is as follows: LDAP_VERSION2 (2, default value), LDAP_VERSION3 (3).
LDAP_OPT_REFERRALS(bool): Whether the LDAP library automatically follows the references returned by the LDAP server. The value range is as follows: TRUE (1, default value), FALSE (0).
&$retval A variable that accepts option values
For example, the code in bwapp:
ldap_set_option($ds,LDAP_OPT_PROTOCOL_VERSION, 3);
This sentence The meaning of the code is that if the ldap connection is successful, then specify the protocol used by LDAP as version 3. (No need to go into detail here, all are applicable formats)
ldap_bind($link_identifier,$bind_rdn,$bind_password)
$link_identifier: LDAP connection identifier returned by the ldap_connect() function (determine LDAP Whether the connection is successful)
$bind_rdn: Use the specified rdn, that is, the login path, such as cn=admin,dc=bwapp,dc=local
$bind_password: Specify the login password.
ldap_search($link_identifier, $dn,$filter): LDAP directory search function, successfully returns the resource descriptor of a result set, which is usually referenced by other functions as $result_identifier, and returns FALSE on failure.
$link_identifier: LDAP connection identifier returned by the ldap_connect() function (to determine whether the connection is successful)
$dn: DN of the directory to be searched
$filter: Search filters. For example, "(objectClass=*)" means to search all entries (for the read function, it means all attributes).
Source code in bwapp: ldap_search($ds, $dn,$filter), where $ds=ldap_connect(),
$dn=”DC=bwapp,DC=local”, $filter=(cn=*) (that is, all ranges of cn). These three parameters indicate that the ldap_search function indicates that all directories of the current server are queried (relative to bwapp).
ldap_count_entries($link_identifier,$search): Returns the number of query results
$link_identifier: The LDAP connection identifier returned by the dap_connect() function (to determine whether the connection is successful)
$search:= ldap_search($link_identifier, $dn, $filter) returns the result set of the query.
At this point, the function has almost been analyzed. Let us outline the general idea of this connection file.
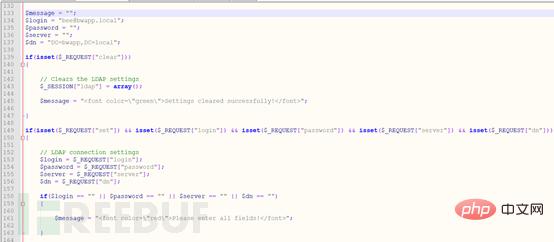
From lines 149 to 163, the code determines whether the various values obtained are empty. If they are empty, a prompt message is thrown.
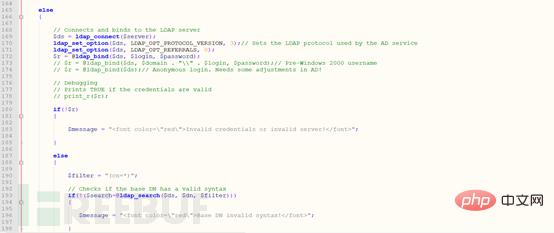
Lines 165 to 198 are used to determine whether the login is successful. Lines 165 to 184 are used to determine whether the ldap service exists. Lines 187 to 198 are used to determine whether there is a distinction. name (equivalent to database name).
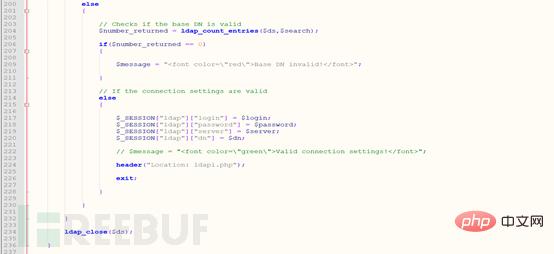
From line 200 to line 236 is to determine whether the corresponding dn exists, that is, whether the corresponding ldap path exists. If it does not exist, the corresponding prompt message will be thrown. If it exists Call ldapi.php, which is the ldap query. After getting the query results in ldapi, the results are output as a table.
Introduction to the php file of LDAP query results
The place where the table is output is in the ldapi.php file. Next, look at the code in ldapi.php.
Start directly from line 231. From line 231 to line 240 are all mentioned above. Bind the LDAP directory. The code is as follows. If you don’t understand, you can take a look at the LDAP binding above. Part
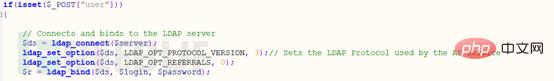
If the LDAP directory is successfully bound, the query will start. The query code starts from line 242
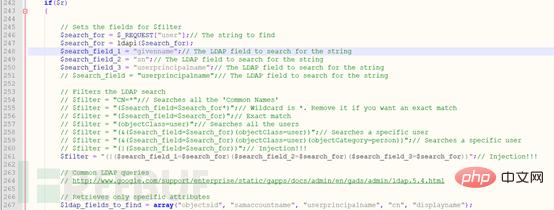
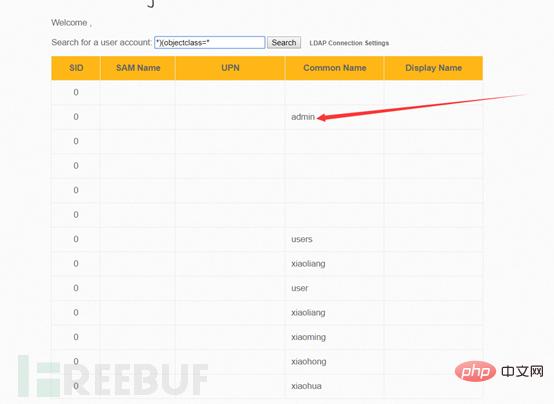
From receiving the value of the POST parameter user to establishing an alias ($search_field_1, $search_field_2, $search_field_3), specifying the filter ($filter) (the filter is a query statement, similar to a sql statement), the syntax rules are as follows:
| #Operator | Character | Use |
|---|---|---|
| = | Create a request for a certain The field must have a filter for the given value. | |
| * | represents a field that can be equal to any value except NULL. | ##Brackets |
| Separate filters to allow other logical operators to work. | ## Combine filters with | |
| . All conditions of the corresponding series must be true. | ## or | | |
| ##Non | ! | |
| ## |
The above is the detailed content of How to conduct range practice with bee-box LDAP injection. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to understand LDAP injection
May 22, 2023 pm 09:47 PM
How to understand LDAP injection
May 22, 2023 pm 09:47 PM
1. LDAP injection LDAP (Light Directory Access Portocol) is a lightweight directory access protocol based on the X.500 standard. It provides services and protocols for accessing directory databases. It is often used to form directory services with directory databases. The directory is a professional distributed database optimized for query, browsing and search. It organizes data in a tree structure, similar to the file directory in Linux/Unix systems. Data that is not modified frequently, such as public certificates, security keys, and company physical device information, is suitable for storage in the directory. LDAP can be understood as a search protocol, which is similar to SQL and has query syntax, but also has the risk of injection attacks. LDAP injection refers to the client
 How to conduct range practice with bee-box LDAP injection
May 13, 2023 am 09:49 AM
How to conduct range practice with bee-box LDAP injection
May 13, 2023 am 09:49 AM
If the essence of sql injection is to splice strings, then the essence of everything that can be injected is to splice strings. LDAP injection is no exception as a kind of injection. What is more interesting is that it is splicing parentheses (sql injection is also concatenates parentheses, but it is more conventional to say that it concatenates strings). In the environment configuration chapter, the configuration of the ldap environment in bee-box has been discussed in great detail. The shooting range practice chapter is more about the connection process between php and ldap, the introduction of the special functions used in the middle, and some techniques for splicing parentheses. Let’s first talk about the login process of the ldap shooting range in bwapp: First, this is an LDAP login interface, the URL is http://192.168.3.184/bW
 How to configure the environment for bee-box LDAP injection
May 12, 2023 pm 08:37 PM
How to configure the environment for bee-box LDAP injection
May 12, 2023 pm 08:37 PM
1. Overview According to my learning process, I must know what the model and vulnerability of my web attack are. Now I have encountered an unexpected situation. The first time I saw LDAP was during a penetration test in a state-owned enterprise. I found an unpopular one (authorized) and piqued my interest in it. The concept of LDAP: Full name: Lightweight Directory Access Protocol (Lightweight Directory Access Protocol), features: I won’t talk about the protocol, it’s too esoteric, it can be understood as a database for storing data, its special feature is that it is a tree A database in the form of a database. First, the name of the database is equivalent to the root of the tree (i.e. DB=dc), and then the process from the root to a leaf node is
 Solution to PHP Fatal error: Call to undefined function ldap_bind()
Jun 22, 2023 pm 11:37 PM
Solution to PHP Fatal error: Call to undefined function ldap_bind()
Jun 22, 2023 pm 11:37 PM
When developing web applications using PHP, we often need to use LDAP authentication to protect application access. However, in some cases, when we try to use PHP's LDAP functionality to implement authentication, we may encounter the following error message: "PHPFatalerror:Calltoundefinedfunctionldap_bind()". This error message usually occurs when an application calls the ldap_bind() function
 How to use Nginx to protect against LDAP injection attacks
Jun 10, 2023 pm 08:19 PM
How to use Nginx to protect against LDAP injection attacks
Jun 10, 2023 pm 08:19 PM
With the increase in network security vulnerabilities, LDAP injection attacks have become a security risk faced by many websites. In order to protect website security and prevent LDAP injection attacks, some security measures need to be used. Among them, Nginx, as a high-performance web server and reverse proxy server, can provide us with a lot of convenience and protection. This article will introduce how to use Nginx to prevent LDAP injection attacks. LDAP injection attack LDAP injection attack is an attack method targeting the LDAP database. The attacker
 Using LDAP for user authentication in PHP
Jun 20, 2023 pm 10:25 PM
Using LDAP for user authentication in PHP
Jun 20, 2023 pm 10:25 PM
LDAP (LightweightDirectoryAccessProtocol) is a protocol for accessing distributed directory services. It can be used for tasks such as user authentication, authorization, account maintenance, and data storage. In PHP applications, LDAP can be used as a powerful authentication mechanism to provide powerful authentication and authorization functions for applications. This article will introduce how to use LDAP for user authentication in PHP. The specific content includes: Installation and configuration L
 How to protect against LDAP injection vulnerabilities using PHP
Jun 24, 2023 am 10:40 AM
How to protect against LDAP injection vulnerabilities using PHP
Jun 24, 2023 am 10:40 AM
As network security issues receive more and more attention, more and more programmers are beginning to pay attention and learn how to prevent code from being attacked. Among them, common attack methods include SQL injection, XSS, CSRF, etc. However, there is another common attack method that is underestimated: LDAP injection vulnerabilities. This article will introduce the principle of this attack method and how to use PHP to prevent LDAP injection vulnerabilities. LDAP introduction LDAP (LightweightDirectoryAccessProtocol)
 How to use PHP and LDAP to implement user group management and authorization
Jun 25, 2023 am 08:22 AM
How to use PHP and LDAP to implement user group management and authorization
Jun 25, 2023 am 08:22 AM
As the scale of enterprises and business needs continue to expand, user group management and authorization have become an essential part. LDAP (Lightweight Directory Access Protocol), as a directory service protocol widely used in enterprise networks, provides an efficient way to achieve user group management and authorization. This article will introduce how to use PHP and LDAP to implement user group management and authorization. 1. What is LDAP LDAP is a lightweight directory access protocol that is widely used as a directory service protocol in enterprise networks. LDAP is client/server based