How to use APT framework TajMahal
Overview
‘TajMahal’ is a previously unknown and technically complex APT framework discovered by Kaspersky Lab in the fall of 2018. This complete spy framework consists of two packages named "Tokyo" and "Yokohama". It includes backdoors, loaders, orchestrators, C2 communicators, voice recorders, keyloggers, screen and webcam grabbers, document and encryption key stealers, and even the victim machine's own file indexer. We found up to 80 malicious modules stored in its encrypted virtual file system, which is one of the highest number of plugins we have seen in an APT tool set.
To highlight its capabilities, TajMahal is able to steal data from victims as well as from burned CDs in the printer queue. It can also request to steal specific files from a previously seen USB stick; the next time the USB is connected to the computer, the files will be stolen.
TajMahal has been developed and used for at least the past five years. The first known "legitimate" sample timestamp is from August 2013, and the last is from April 2018. The first confirmed date of seeing a TajMahal sample on a victim's machine is August 2014.
Technical Details
Kaspersky discovered two different types of TajMahal packages, claiming to be Tokyo and Yokohama. Kaspersky Lab discovered that victim systems were infected by two software packages. This suggests that Tokyo was used as a first-stage infection, with Tokyo deploying a fully functional Yokohama on the victim's system, with the framework shown below:
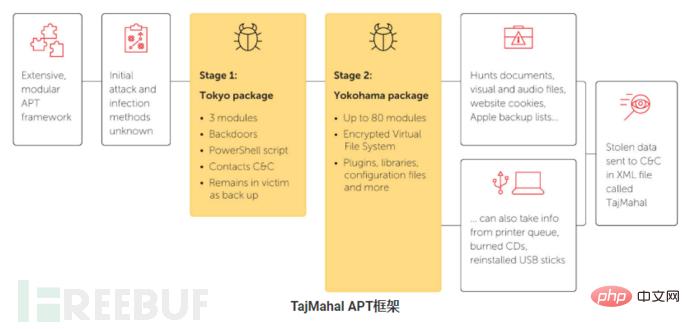
According to these victims The module on the attacker's machine identified the following interesting capabilities:
The ability to steal documents sent to the printer queue.
The data collected for victim reconnaissance includes backup lists of Apple mobile devices.
Take screenshots while recording VoiceIP application audio.
Steal and write the CD image.
Ability to steal files previously seen on removable drives when they become available again.
Steal Internet Explorer, Netscape Navigator, FireFox and RealNetworks cookies.
If removed from the frontend file or related registry value, it will reappear after a reboot with a new name and launch type.
Affiliation:
Conjecture 1: Russia
Kaspersky has only disclosed one victim so far, a diplomatic department in Central Asia , in previous reports, APT28 also began to carry out attacks against Central Asia.
Conjecture 2: United States:
As can be seen from the map, Central Asia is adjacent to Russia and China. This region has always been the target of the United States’ efforts to win over
And the framework Kabba is called a complex modular framework. According to the timestamp, it was compiled as early as 13 years ago. Kabba was first discovered in 18 years, and the American APT Attacks are usually stealthy and modular, making them difficult to detect. Flame was the first complex modular Trojan to be discovered
The above is the detailed content of How to use APT framework TajMahal. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 Example analysis of using ZoomEye to find APT attacks
May 27, 2023 pm 07:19 PM
Example analysis of using ZoomEye to find APT attacks
May 27, 2023 pm 07:19 PM
The data online on ZoomEye is in overwrite and update mode, which means that if the data is not scanned in the second scan, the updated data will not be overwritten. The data on ZoomEye will retain the banner data obtained in the first scan. This mechanism is here In fact, there is a good scene fit in the traceability of this kind of malicious attack: the download servers used by malicious attacks such as Botnet, APT and other attacks are usually directly deactivated and discarded after being discovered. Of course, some are hacked targets, and they are also very violent. Go offline directly! Therefore, many attack sites are likely to be cached online by ZoomEye. Of course, with the data provided in the ZoomEye history api, you can query the number of banners obtained by each scan regardless of whether you cover it or not.
 What is the difference between Linux package management tools yum and apt?
May 30, 2023 am 09:53 AM
What is the difference between Linux package management tools yum and apt?
May 30, 2023 am 09:53 AM
Generally speaking, famous Linux systems are basically divided into two categories: RedHat series: Redhat, Centos, Fedora, etc.; Debian series: Debian, Ubuntu, etc. yum (YellowdogUpdater, Modified) is a Shell front-end package manager in Fedora, RedHat and SUSE. apt (AdvancedPackagingTool) is a shell front-end package manager in Debian and Ubuntu. Overview Generally speaking, the famous Linux systems are basically divided into two categories: RedHat series: Redhat, Cento
 How to analyze APT Trojans based on the threat intelligence cycle model
May 14, 2023 pm 10:01 PM
How to analyze APT Trojans based on the threat intelligence cycle model
May 14, 2023 pm 10:01 PM
About the Threat Intelligence Processing Cycle Model The term "Threat Intelligence Processing Cycle" (F3EAD) originates from the military. It is a method for organizing resources and deploying troops designed by the US Army's commanders at all levels of the main combat arms. The Network Emergency Response Center draws on this method and processes threat intelligence information in the following six stages: Threat Intelligence Processing Cycle Application of the F3EAD Threat Intelligence Processing Cycle Model Step 1: Find a date on a certain month and deploy it on the partner's public cloud server The "Onion" system alarm found a suspected Trojan horse program, so the emergency response team quickly started the emergency response process: stakeholders and others gathered the group with one click and called in. The victim system is isolated for investigation. The security system and audit logs are exported for traceability analysis. Preparation of business system architecture and code-related information to analyze intrusion breaches and victims
 Tutorial on installing php8 on deepin system.
Feb 19, 2024 am 10:50 AM
Tutorial on installing php8 on deepin system.
Feb 19, 2024 am 10:50 AM
To install PHP8 on Deepin system, you can follow the steps below: Update the system: Open a terminal and execute the following command to update the system packages: sudoaptupdatesudoaptupgrade Add Ondřej SurýPPA source: PHP8 can be installed through Ondřej SurýPPA source. Execute the following command to add the source: sudoaptinstallsoftware-properties-commonsudoadd-apt-repositoryppa:ondrej/php Update the package list: Execute the following command to update the package list to get PHP in the PPA source
 How to change Ubuntu's apt-get update source?
Jan 05, 2024 pm 03:40 PM
How to change Ubuntu's apt-get update source?
Jan 05, 2024 pm 03:40 PM
Manually modify Ubuntu's apt-get source 1. Use the ssh tool to connect to Ubuntu (I use xshell) 2. Type cd/etc/apt/3 on the command line and back up the source.list file in this directory (you must have sudo permissions) ), then there is a source.list.bak file. 4. Clear the source.list file content (note: it cannot be restored after clearing, so you need to perform the previous step to back up the file in advance). At this time, use sudo to prompt that the permissions are insufficient. Switch directly to the root user and execute this command. 5. Use vim to open source.list, press the i key to enter the editing mode, paste the source address to be modified, and then press
 Tutorial on compiling and installing MySQL5.7 on Ubuntu 20.04 system.
Feb 19, 2024 pm 04:57 PM
Tutorial on compiling and installing MySQL5.7 on Ubuntu 20.04 system.
Feb 19, 2024 pm 04:57 PM
MySQL 5.7 can be installed by using the official MySQL APT repository. The following are the steps to install MySQL5.7 through the official APT repository on Ubuntu20.04 system: Add the MySQLAPT repository: wgethttps://dev.mysql.com/get/mysql-apt-config_0.8.17-1_all.debsudodpkg-imysql -apt-config_0.8.17-1_all.deb During the installation process, you will see a configuration interface. Select the MySQLServer version as 5.7, and then complete the configuration. Update package list: sud
 Tutorial on compiling and installing Docker on Ubuntu 18.04 system.
Feb 19, 2024 pm 02:03 PM
Tutorial on compiling and installing Docker on Ubuntu 18.04 system.
Feb 19, 2024 pm 02:03 PM
The following is a tutorial for compiling and installing Docker on Ubuntu18.04 system: Uninstall the old version of Docker (if installed): sudoaptremovedockerdocker-enginedocker.iocontainerdrunc Update system packages: sudoaptupdatesudoaptupgrade Install Docker dependencies: sudoaptinstallapt-transport-httpsca-certificatescurlsoftware-properties-commonAdd Docker Official GPG key: curl-
 Can't find yum and installation method in Ubuntu system!
Mar 02, 2024 pm 01:07 PM
Can't find yum and installation method in Ubuntu system!
Mar 02, 2024 pm 01:07 PM
yum is the package manager in the RedHat series distributions (such as RHEL and CentOS), while Ubuntu uses another package manager called apt (AdvancedPackageTool). In Ubuntu systems, you can use the apt command to manage software packages. Following are the basic steps to install packages in Ubuntu system: Update package index Before performing any installation operation, first execute the following command to update the package index: sudoaptupdate Installing a package Use the following command to install a specific package: sudoaptinstallpackage_name will "package_name̶




