 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 How to conduct APT organization tracking and governance based on knowledge graph
How to conduct APT organization tracking and governance based on knowledge graph
How to conduct APT organization tracking and governance based on knowledge graph
Advanced persistent threats (APT) are increasingly becoming a major cyberspace threat that cannot be ignored against important assets of governments and enterprises. Since APT attacks often have clear attack intentions, and their attack methods are extremely concealed and latent, traditional network detection methods are usually unable to effectively detect them. In recent years, APT attack detection and defense technologies have gradually attracted the attention of governments and network security researchers from various countries.
1. Research on the governance of APT organizations in developed countries
1.1 At the strategic level, the United States emphasizes "America First" and "Promoting Peace through Strength"
The Trump administration has successively released the "National Security Strategy Report", "DoD Cyber Strategy" and "National Cyber Strategy", interpreting Trump's "America First" strategy and emphasizing "cyber deterrence" and "promoting peace through strength," highlighting the importance of cyber warfare, placing the role of "military and force" before diplomacy and state affairs, and emphasizing the protection of U.S. infrastructure to ensure the continued prosperity of the United States. At the same time, the importance of artificial intelligence (AI) to economic growth was emphasized.
1.2 At the regulatory level, the United States legislates to track APT organizations
On September 5, 2018, the U.S. House of Representatives voted to pass the "Cyber Deterrence and Response Act of 2018", which aims to Deter and sanction future state-sponsored cyberattacks against the United States to protect U.S. political, economic, and critical infrastructure from compromise. The bill requires the President of the United States to identify a list of advanced persistent threat (APT) organizations, publish it in the Federal Register, and update it regularly.
1.3 At the attack level, the U.S. military develops advanced cyber warfare tools based on knowledge graphs
In September 2010, "****" disclosed that the Pentagon strives to control the network Preemptively strike in war and achieve the "5D" effects of deception, denial, separation, degradation, and destruction. Research on the attack level of cyber warfare has always been a focus of the U.S. government and its affiliated research institutions. According to the models built by the United States around cyber warfare in recent years, it is important to map the battlefield network with a multi-level knowledge graph and conduct model verification combined with shooting range exercises. Direction of the research.
1.3.1 DARPA’s Plan X uses knowledge graphs to depict battlefield maps to support VR operations
PLAN Revolutionary technology to understand, plan and manage cyber warfare in real-time, large-scale and dynamic cyber environments. Based on a well-established universal map, it helps military network operators use a visual method to perform network intrusion tasks on the battlefield. PLAN The optimal invasion path and invasion plan are provided to combatants.
1.3.2 MITER's CyGraph prototype supports network operations
CyGraph is MITER's prototype system for graph model research. CyGraph uses a hierarchical graph structure, including four levels of graph data: Network Infrastructure, Security Posture, Cyber Threats, and Mission Dependencies, to support the protection of key assets. tasks such as attack surface identification and attack situation understanding.
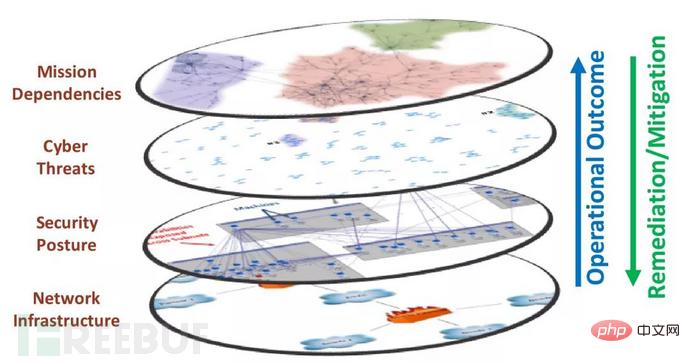
Figure 1.1 CyGraph’s multi-layer graph structure
1.4 At the defense level, develop a new generation APT description language model based on ATT&CK
ATT&CK is a model and knowledge base that reflects the attack behavior of each attack life cycle. ATT&CK uses a knowledge base to analyze opponent attack methods and evaluate existing protection systems. It can also be combined with the shooting range to conduct attack simulation testing and automated verification. At the same time, many foreign security manufacturers use it to detect and track the actual effects of APT organizations.
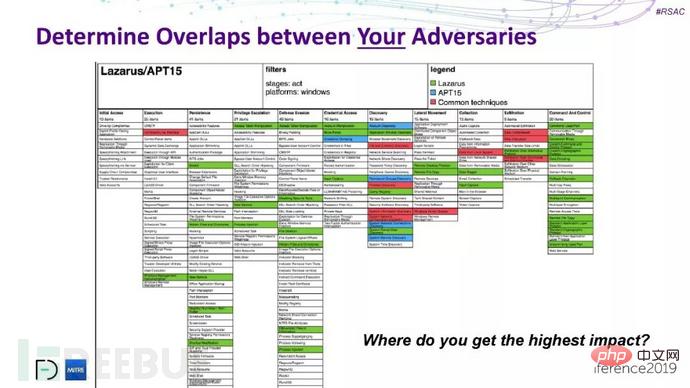
Figure 1.2 ATT&CK Comparative analysis of TTP capabilities for lazarus and APT15
2. APT organization tracking practice based on knowledge graph
The APT tracking practice based on the knowledge graph takes the threat primitive model as the core and uses a top-down approach to build the APT knowledge graph.
2.1 Entity class construction based on threat primitive model
The definition of APT knowledge type refers to various current security standards and specifications, such as the common attack mode enumeration of attack mechanisms and classification (CAPEC), Malware Attribute Enumeration and Characteristics (MAEC) and Common Vulnerabilities and Exposures (CVE), etc. Twelve knowledge types are designed: attack mode, campaign, defense measures, identity, threat indicator, intrusion set ,Malicious Code, Observable Entities, Reports, Attackers,Tools, Vulnerabilities.
2.2 APT knowledge graph ontology structure
The knowledge type definition only forms isolated knowledge nodes with relevant information describing the characteristics of the APT organization. There is no semantic relationship between knowledge nodes. On the one hand, the semantic design extracts expert knowledge related to vulnerabilities, vulnerabilities, assets, and attack mechanisms contained in the U.S. National Vulnerability Database (NVD). Secondly, it refers to the seven types of relationships defined by STIX. An overview of STIX2.0 object relationships is shown in Figure 2.1 below.
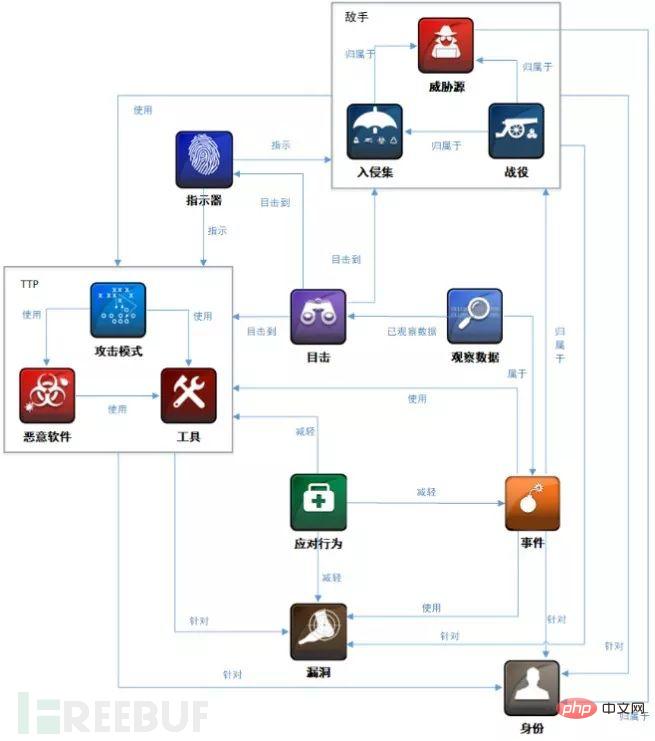
Figure 2.1 STIX2.0 structure diagram
Summarizes and summarizes the multiple types of semantic relationships involved in the APT report, including "instruction", "exploitation", " Belongs to" and other semantic relations, construct the ontology structure as shown in Figure 2.2.
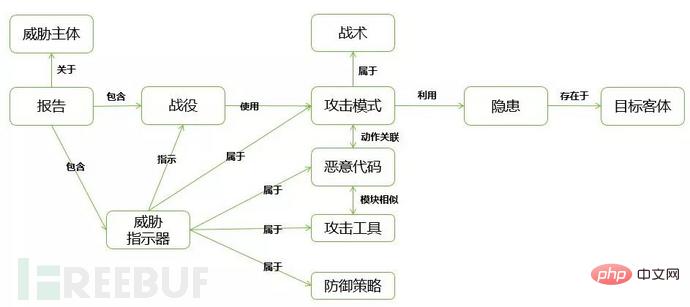
Figure 2.2 APT knowledge graph ontology structure
2.3 APT attack organization knowledge base construction
This article is based on APT knowledge base is established in a top-down manner. First, the information extraction and alignment operation is performed. Based on the APT knowledge graph ontology, knowledge entities, attributes and knowledge relationships related to the APT organization are extracted from massive data. Then, attribute disambiguation and fusion are performed based on the knowledge attributes defined in the APT knowledge ontology, and the APT knowledge base is output.
The sources of information related to the APT organization include structured data (structured intelligence database, STIX intelligence), semi-structured data (open source intelligence community websites such as Alienvault, IBM x-force intelligence community website, MISP, ATT&CK ), unstructured data (Talos security blog, Github APT report).
2.4 Experiments and Applications
The APT theme knowledge graph constructed in this article currently includes 257 APT organizations, as shown in Figure 2.3.
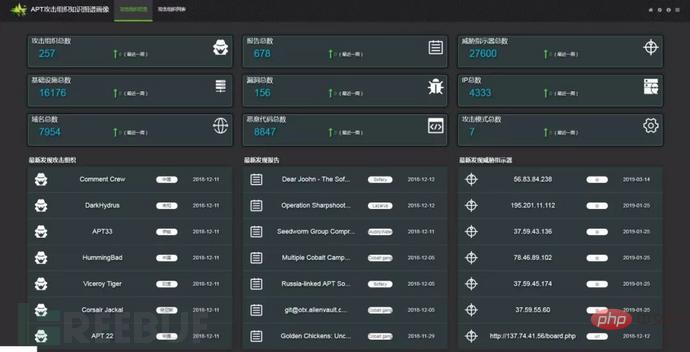
Figure 2.3 Overview of APT organizations
Combined with the constructed knowledge graph ontology structure, a portrait of the APT32 attack organization was made through semantic search, as shown in Figure 2.4 , shown in 2.5.
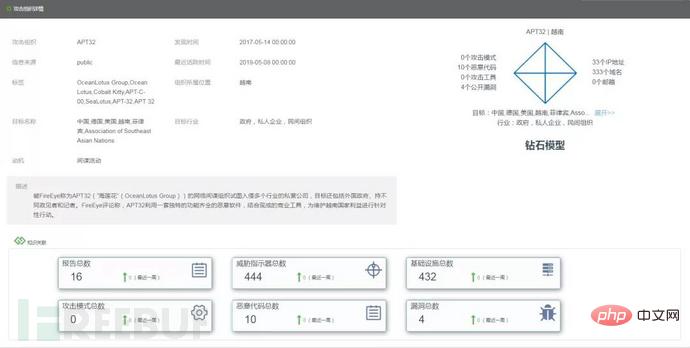
Figure 2.4 APT32 diamond model
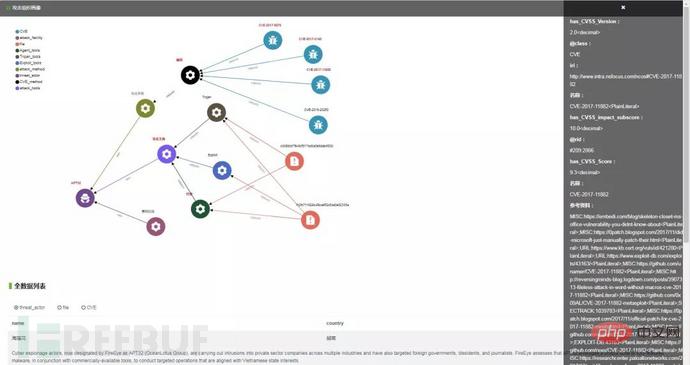
Figure 2.5 APT 32 portrait
The portrait information includes APT32 The infrastructure, technical means, and attack tools controlled by the organization. Combined with the knowledge of APT portraits, through real-time monitoring and comparison of APT organizational characteristics, the organizational relevance of events is marked, and real-time monitoring and statistics of the activity of APT organizations are achieved.
Based on IDS and sandbox probe equipment in a certain environment, a big data analysis cluster experimental environment composed of 4 servers, combined with the APT organizational portrait characteristics provided by the knowledge graph, from June 2 to June 2019 A total of 5 APT organizations were found to be active during the 9-day period, and the results are shown in Figure 2.6.
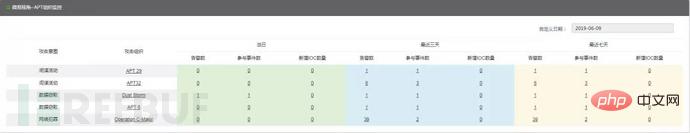
Figure 2.6 APT Organization Tracking
3. Countermeasures and Suggestions
1. Improve information related to APT attacks Formulation of policies and regulations. At present, the Chinese government has not yet issued specific policies and regulations to respond to APT attacks, which is very detrimental to promoting, standardizing, and guiding the analysis and detection of domestic APT attacks.
2. Recommend a research ecosystem of co-construction, co-research and sharing. The cooperation between the Chinese government and enterprises needs to be further deepened to build technical solutions and model standards that can be adopted at the industry and national levels.
3. Build a unified intelligence sharing format and strengthen intelligence sharing. Since its implementation, GB/T 36643-2018 "Information Security Technology - Network Security Threat Information Format Specification" has not been widely used in domestic governments and enterprises.
4. Strengthen the construction of universal threat primitive models. my country has not yet fully constructed a set of common threat primitives to support a unified threat intelligence expression format and the sharing of APT-related threat intelligence and knowledge.
The above is the detailed content of How to conduct APT organization tracking and governance based on knowledge graph. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Example analysis of using ZoomEye to find APT attacks
May 27, 2023 pm 07:19 PM
Example analysis of using ZoomEye to find APT attacks
May 27, 2023 pm 07:19 PM
The data online on ZoomEye is in overwrite and update mode, which means that if the data is not scanned in the second scan, the updated data will not be overwritten. The data on ZoomEye will retain the banner data obtained in the first scan. This mechanism is here In fact, there is a good scene fit in the traceability of this kind of malicious attack: the download servers used by malicious attacks such as Botnet, APT and other attacks are usually directly deactivated and discarded after being discovered. Of course, some are hacked targets, and they are also very violent. Go offline directly! Therefore, many attack sites are likely to be cached online by ZoomEye. Of course, with the data provided in the ZoomEye history api, you can query the number of banners obtained by each scan regardless of whether you cover it or not.
 What is the difference between Linux package management tools yum and apt?
May 30, 2023 am 09:53 AM
What is the difference between Linux package management tools yum and apt?
May 30, 2023 am 09:53 AM
Generally speaking, famous Linux systems are basically divided into two categories: RedHat series: Redhat, Centos, Fedora, etc.; Debian series: Debian, Ubuntu, etc. yum (YellowdogUpdater, Modified) is a Shell front-end package manager in Fedora, RedHat and SUSE. apt (AdvancedPackagingTool) is a shell front-end package manager in Debian and Ubuntu. Overview Generally speaking, the famous Linux systems are basically divided into two categories: RedHat series: Redhat, Cento
 How to analyze APT Trojans based on the threat intelligence cycle model
May 14, 2023 pm 10:01 PM
How to analyze APT Trojans based on the threat intelligence cycle model
May 14, 2023 pm 10:01 PM
About the Threat Intelligence Processing Cycle Model The term "Threat Intelligence Processing Cycle" (F3EAD) originates from the military. It is a method for organizing resources and deploying troops designed by the US Army's commanders at all levels of the main combat arms. The Network Emergency Response Center draws on this method and processes threat intelligence information in the following six stages: Threat Intelligence Processing Cycle Application of the F3EAD Threat Intelligence Processing Cycle Model Step 1: Find a date on a certain month and deploy it on the partner's public cloud server The "Onion" system alarm found a suspected Trojan horse program, so the emergency response team quickly started the emergency response process: stakeholders and others gathered the group with one click and called in. The victim system is isolated for investigation. The security system and audit logs are exported for traceability analysis. Preparation of business system architecture and code-related information to analyze intrusion breaches and victims
 Tutorial on installing php8 on deepin system.
Feb 19, 2024 am 10:50 AM
Tutorial on installing php8 on deepin system.
Feb 19, 2024 am 10:50 AM
To install PHP8 on Deepin system, you can follow the steps below: Update the system: Open a terminal and execute the following command to update the system packages: sudoaptupdatesudoaptupgrade Add Ondřej SurýPPA source: PHP8 can be installed through Ondřej SurýPPA source. Execute the following command to add the source: sudoaptinstallsoftware-properties-commonsudoadd-apt-repositoryppa:ondrej/php Update the package list: Execute the following command to update the package list to get PHP in the PPA source
 How to change Ubuntu's apt-get update source?
Jan 05, 2024 pm 03:40 PM
How to change Ubuntu's apt-get update source?
Jan 05, 2024 pm 03:40 PM
Manually modify Ubuntu's apt-get source 1. Use the ssh tool to connect to Ubuntu (I use xshell) 2. Type cd/etc/apt/3 on the command line and back up the source.list file in this directory (you must have sudo permissions) ), then there is a source.list.bak file. 4. Clear the source.list file content (note: it cannot be restored after clearing, so you need to perform the previous step to back up the file in advance). At this time, use sudo to prompt that the permissions are insufficient. Switch directly to the root user and execute this command. 5. Use vim to open source.list, press the i key to enter the editing mode, paste the source address to be modified, and then press
 Tutorial on compiling and installing Docker on Ubuntu 18.04 system.
Feb 19, 2024 pm 02:03 PM
Tutorial on compiling and installing Docker on Ubuntu 18.04 system.
Feb 19, 2024 pm 02:03 PM
The following is a tutorial for compiling and installing Docker on Ubuntu18.04 system: Uninstall the old version of Docker (if installed): sudoaptremovedockerdocker-enginedocker.iocontainerdrunc Update system packages: sudoaptupdatesudoaptupgrade Install Docker dependencies: sudoaptinstallapt-transport-httpsca-certificatescurlsoftware-properties-commonAdd Docker Official GPG key: curl-
 Tutorial on compiling and installing MySQL5.7 on Ubuntu 20.04 system.
Feb 19, 2024 pm 04:57 PM
Tutorial on compiling and installing MySQL5.7 on Ubuntu 20.04 system.
Feb 19, 2024 pm 04:57 PM
MySQL 5.7 can be installed by using the official MySQL APT repository. The following are the steps to install MySQL5.7 through the official APT repository on Ubuntu20.04 system: Add the MySQLAPT repository: wgethttps://dev.mysql.com/get/mysql-apt-config_0.8.17-1_all.debsudodpkg-imysql -apt-config_0.8.17-1_all.deb During the installation process, you will see a configuration interface. Select the MySQLServer version as 5.7, and then complete the configuration. Update package list: sud
 Can't find yum and installation method in Ubuntu system!
Mar 02, 2024 pm 01:07 PM
Can't find yum and installation method in Ubuntu system!
Mar 02, 2024 pm 01:07 PM
yum is the package manager in the RedHat series distributions (such as RHEL and CentOS), while Ubuntu uses another package manager called apt (AdvancedPackageTool). In Ubuntu systems, you can use the apt command to manage software packages. Following are the basic steps to install packages in Ubuntu system: Update package index Before performing any installation operation, first execute the following command to update the package index: sudoaptupdate Installing a package Use the following command to install a specific package: sudoaptinstallpackage_name will "package_name̶





