Why does online behavior management ban teamviewer?
A few days ago, the Shenzhen Network and Information Security Information Notification Center issued an emergency notice, stating that TeamViewer, a well-known remote office tool, has been breached by the overseas hacker organization APT41, and reminded corporate organizations to take protective measures. In other words, APT41 has broken through all the protection systems of TeamViewer and obtained relevant data permissions. The risk level is very high. Before teamviewer officially provides solutions and releases relevant patches, we recommend that users suspend the use of teamviewer software to avoid unnecessary losses.
The following is an introduction to teamviewer communication methods and how to use WSG Internet Behavior Management to ban teamviewer.
1. teamviewer communication method
When teamviewer starts, it will first connect to the teamviewer official website (both http and https) to obtain the ID and routing information. If the direct connection cannot be made, teamviewer will also obtain the local proxy configuration and try to connect through the proxy server.
For teamviewer’s subsequent point-to-point remote control, most of the ports passed are tcp 5938. Communication data for other dynamic ports also exists.
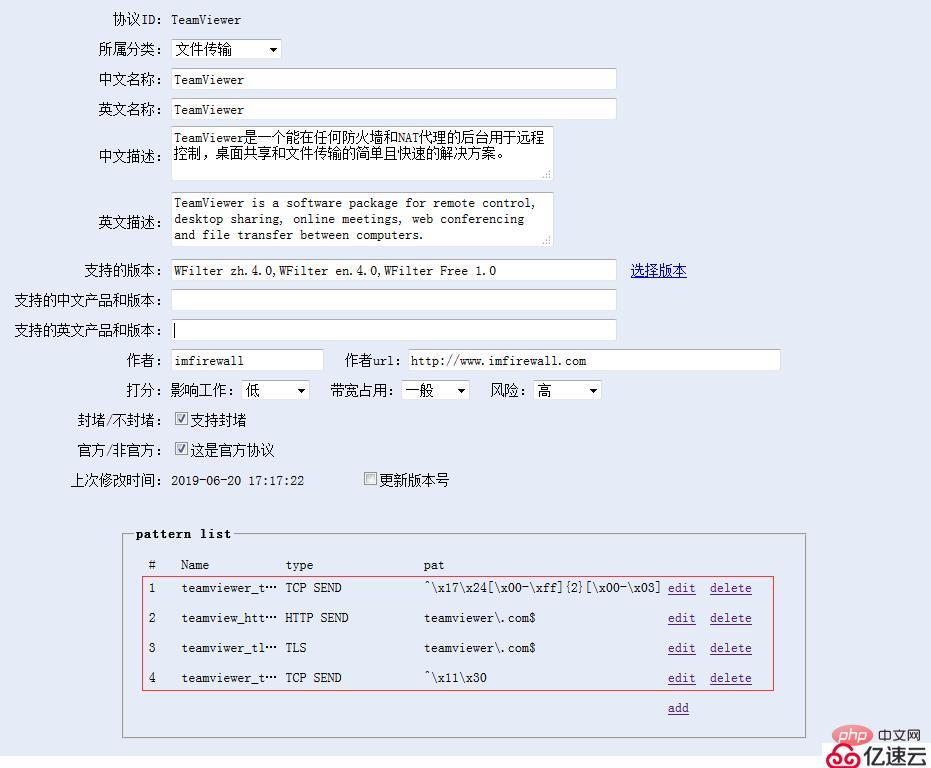
2. Specific steps to ban teamviewer
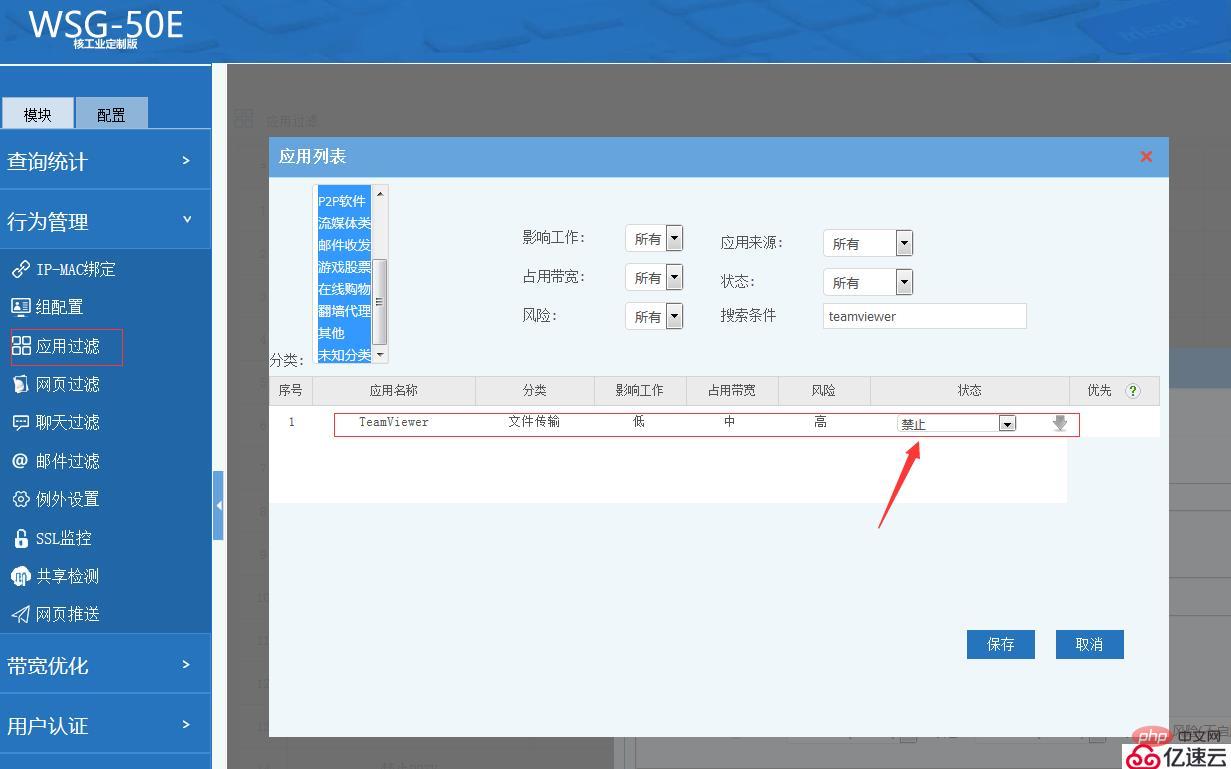
In the WFilter series of online behavior management, we have added teamviewer extraction features to In our application feature library, you only need to set "teamviewer" to "forbidden" in application filtering to block the teamviewer official website and prohibit the teamviewer software's own communication. The configuration is as shown below:
3. Effect test
After the above configuration, the use of teamviewer software can be prohibited and the teamviewer website can be blocked.
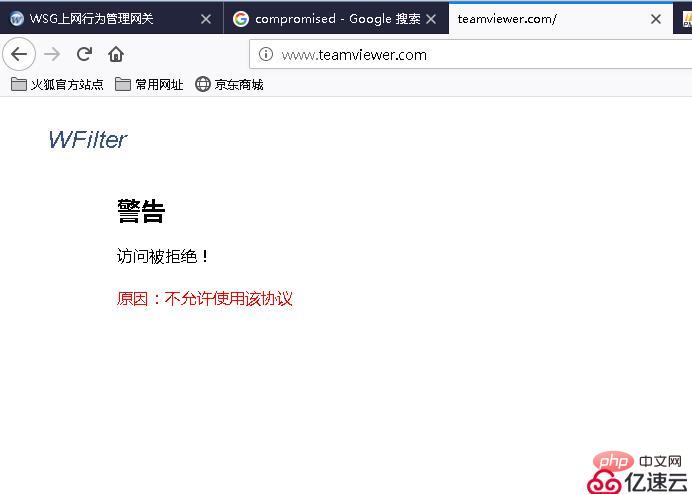
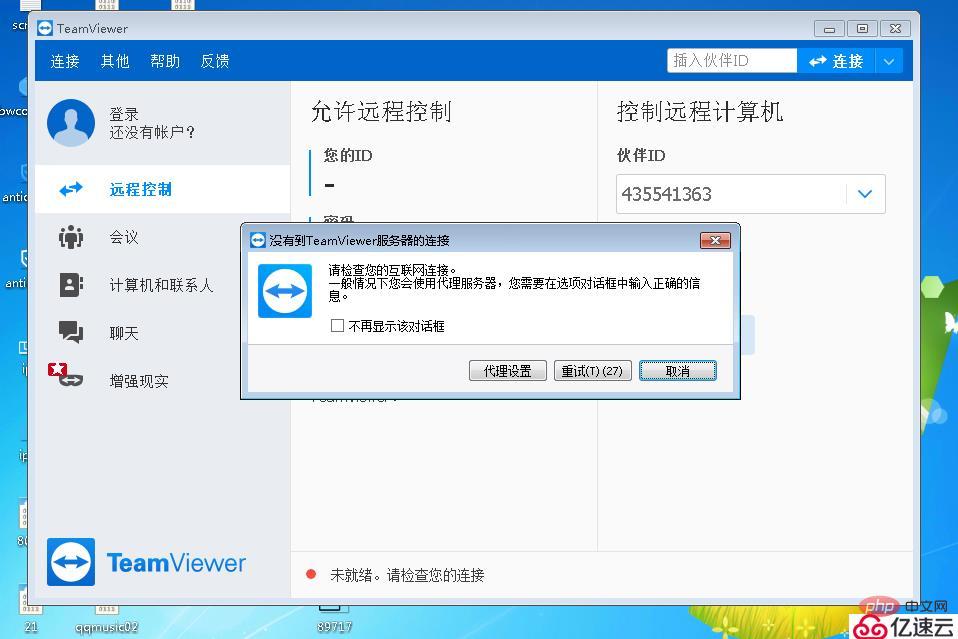
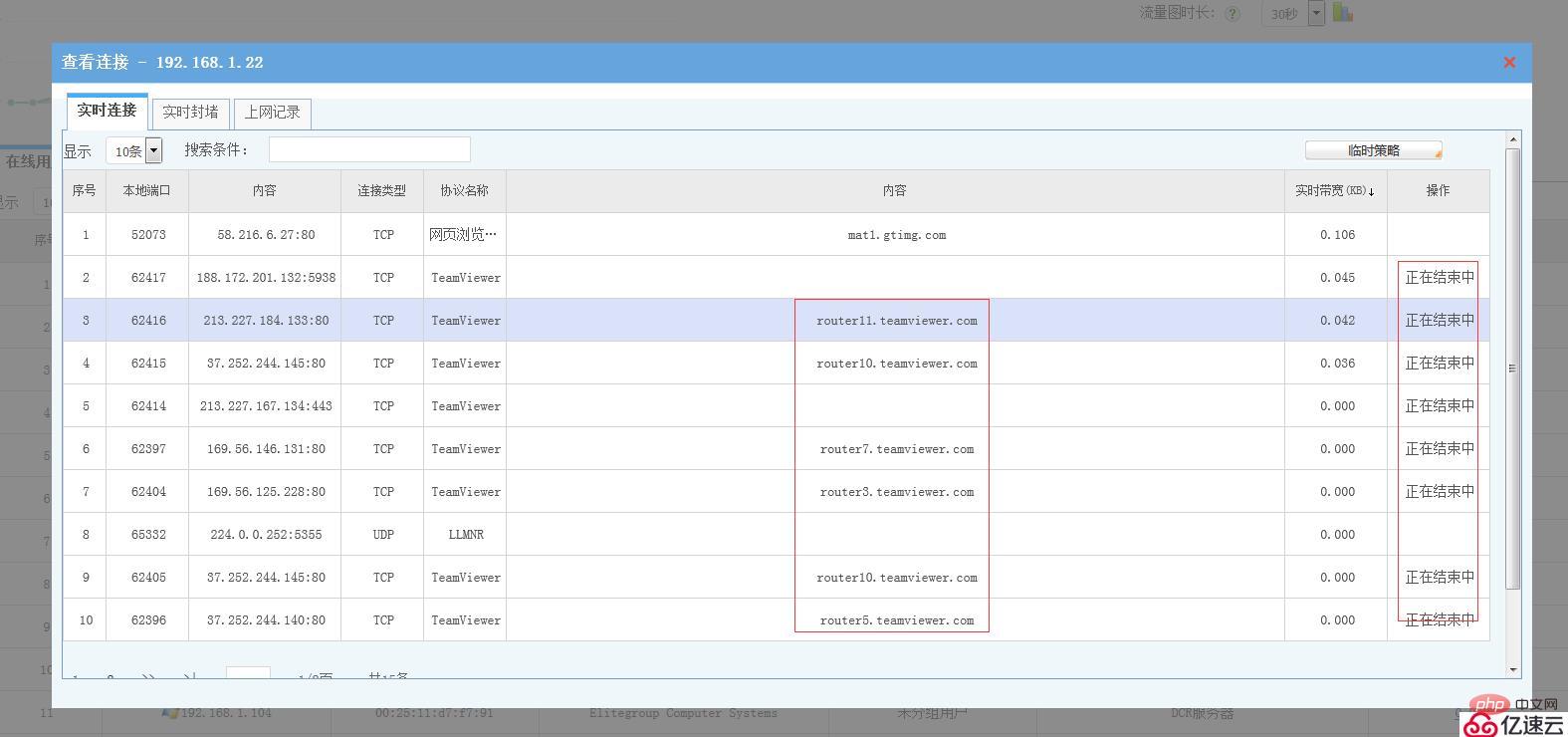
In WSG, you can see that the teamviewer software is trying to access the teamviewer official website and is banned.
The above is the detailed content of Why does online behavior management ban teamviewer?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52


