
The 2019 Security Orchestration and Automated Response Solutions (SOAR) Market Guide released by the authoritative consulting agency Gartner states that “by 2022, more than 30% of security companies with a security team of more than 5 people will use SOAR. Security Orchestration Automated Response Solution”. Today we will introduce how enterprises can use the NSFOCUS SOAR system to complete security orchestration and automated response within three minutes.
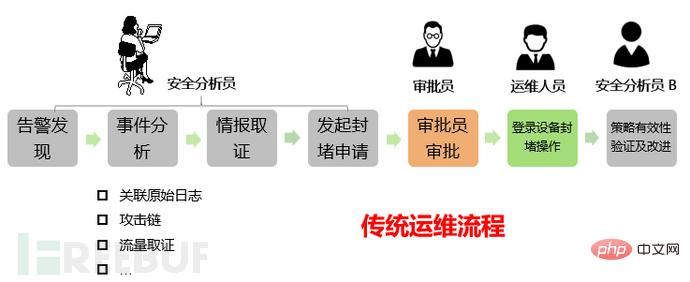
In the traditional security operations and maintenance of enterprises In event handling, the following process is generally followed:
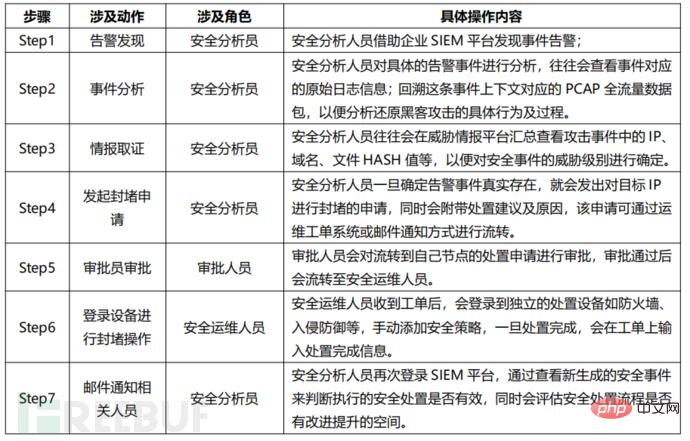
Table: Traditional security operation and maintenance process
After the above 7 steps, an information security incident handling process That's the end. In this process, multiple departments with different roles will participate, the disposal process is cumbersome, the efficiency is difficult to quantify, and the handling processes for different events are difficult to standardize.
At the same time, enterprises often face the following pain points in security operation and maintenance: too many event alarms, and valid event alarms are drowned, making it difficult to handle security incidents in a timely manner. Enterprises often lack security analysis and processing professionals. Security analysis experience is difficult to solidify, and security experts can easily get stuck in repetitive security processing work, making it difficult to exert their true value. The most important thing is that enterprises are restricted by processes and personnel, and traditional security response takes too long.
Therefore, enterprises have added the following demands in the development and evolution of security operations:
Improve the signal-to-noise ratio: increase effective high-fidelity alarms, so that limited security expert resources can focus on real risks and issues.
Reduce MTTR: Solidify the safe disposal process, continuously accumulate operational experience, and continue operations, so that the response and disposal time is continuously reduced.
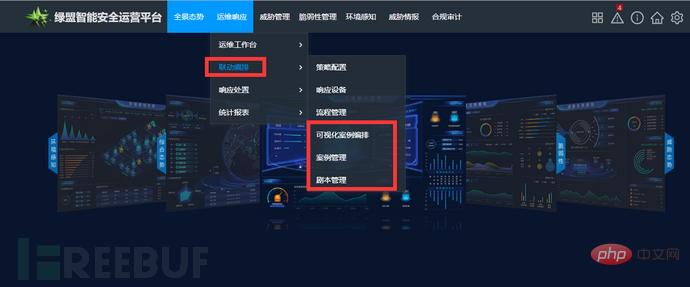
Picture: NSFOCUS SOAR component entrance
ISOP intelligent security operation platform has been Integrating the SOAR security orchestration automated response function, you can use the security orchestration and automated response processing functions from the NSFOCUS ISOP Intelligent Security Operation Center Operation and Maintenance Response-Linked Orchestration Portal to start the enterprise's automated security orchestration response journey.
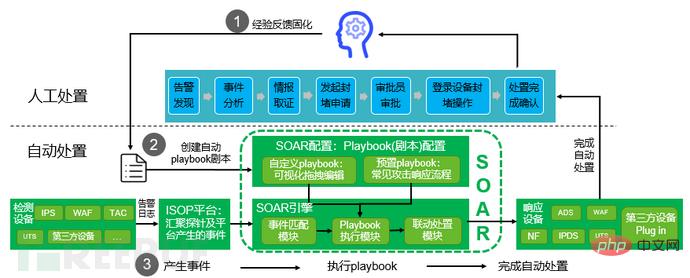 Picture: NSFOCUS SOAR security orchestration and automated response solution
Picture: NSFOCUS SOAR security orchestration and automated response solution
The SOAR component in ISOP deeply integrates people, security technology, and processes through visual orchestration; it solidifies through manual operation and maintenance experience The Playbook scripts are connected in series and parallel to build a workflow for security incident handling, automatically triggering different security devices to perform response actions. Case management is based on a more comprehensive and end-to-end understanding of the security event context, helping enterprises to integrate complex incident response processes and tasks. Transform flows into consistent, repeatable, measurable and effective workflows, and transform passive emergency response into automated continuous response.
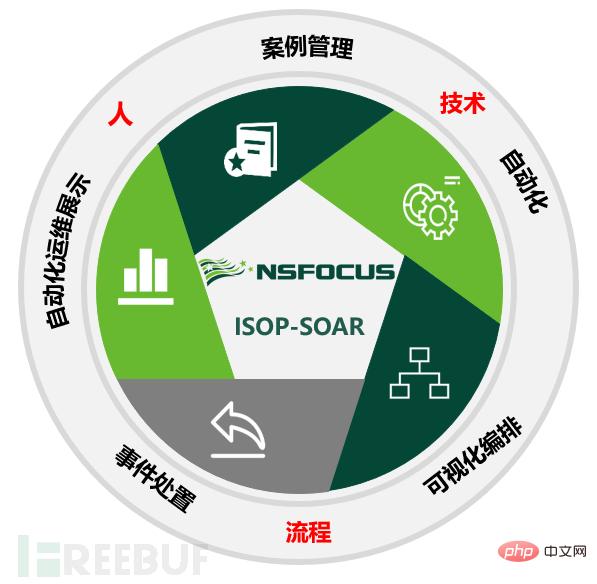
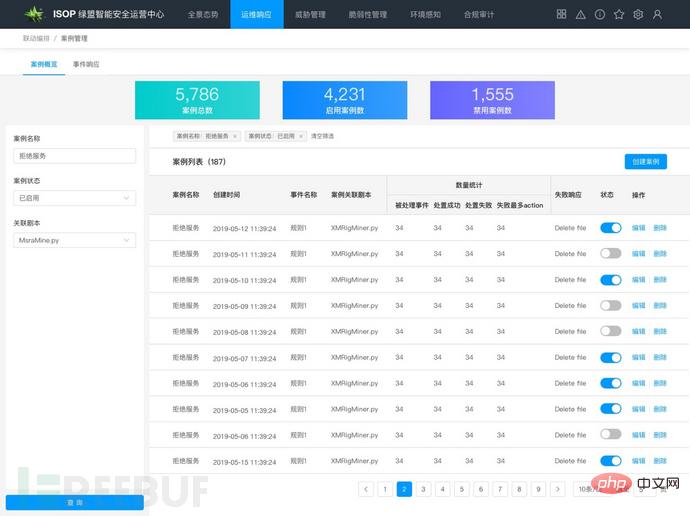 Figure: Case management
Figure: Case management
Case is the most basic function in the SOAR component, which runs through the entire security incident handling life cycle, including the selection and execution of log sources, security rules, intelligence forensics and incident handling Playbook scripts required for information security incident analysis and judgment. As long as the alarm security events in the enterprise can be matched to cases, automated response processing can be completed. Cases have a more comprehensive and end-to-end understanding of the security event context, which helps to convert complex incident response processes and tasks into consistent and repeatable , measurable and effective workflow.
In enterprise security operations, common security events can be mapped to SOAR cases of different categories. Cases of the same nature (such as: mining, intrusion, denial of service, blackmail, phishing, hotlinking, Information leakage, etc.) can choose a similar disposal method. The case process processing function can assign different Playbook scripts to cases of different natures, and supervise the execution to complete the automated closed-loop response to enterprise security incidents.
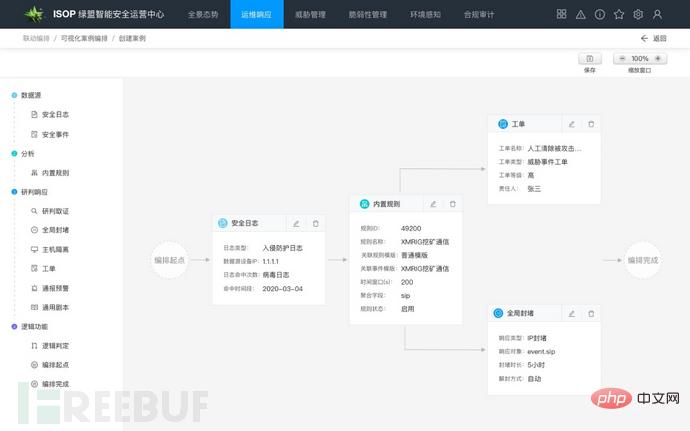
Figure: Visual case arrangement 1
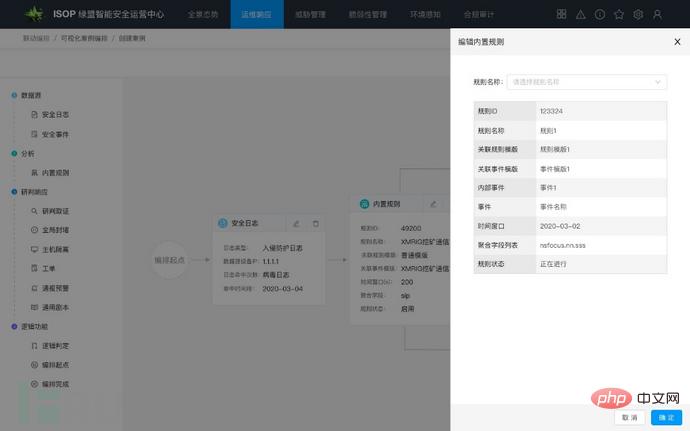 Figure: Visual case arrangement 2
Figure: Visual case arrangement 2
The SOAR component in ISOP has built-in cases corresponding to some common attacks. In addition, enterprises can quickly create cases and their corresponding playbook scripts through visual drag-and-drop arrangement. There are often dependencies between different steps of security research and judgment, and security events The analysis process uses a visual drag-and-drop method to provide context for security handling, avoiding the need to jump between different pages in traditional operation and maintenance, and reducing the complexity of security incident handling. Once a case is successfully created and activated, subsequent events that hit the case can be handled in an automated manner, reducing the cost of collaborative communication and process flow between different departments.
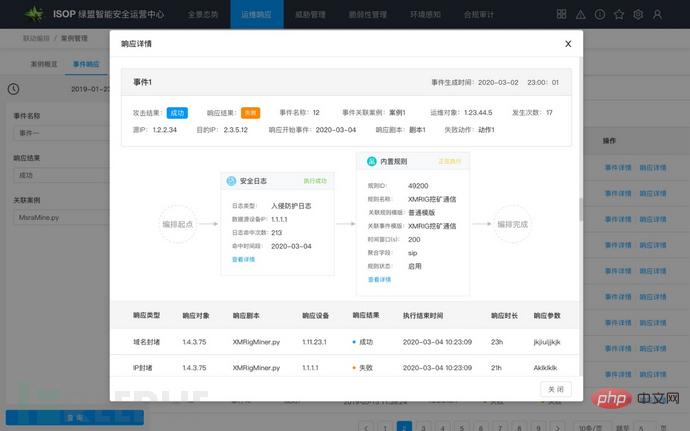 Figure: Case Disposal Process Tracking
Figure: Case Disposal Process Tracking
Case can help enterprises conduct streamlined and continuous investigation, analysis and response handling tracking records for a set of related events. During the case execution process , the execution status of each intermediate process of security events (successful, executing, failed) can be displayed in the visual orchestration process, thereby realizing the visualization of the end-to-end operation and maintenance process.
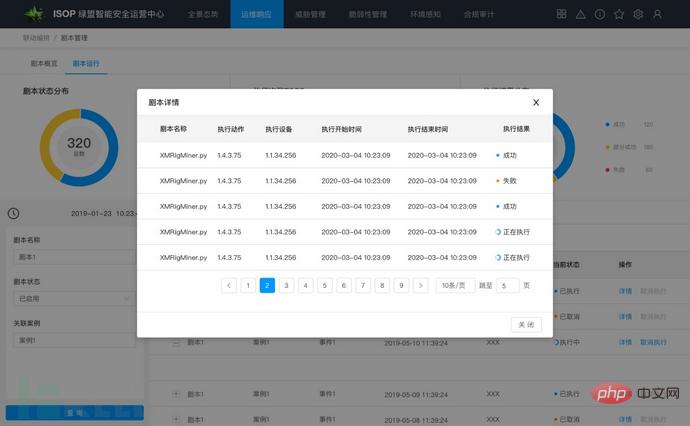
Figure: Script Playbook running status
Playbook script is equivalent to the work flow of a security engineer. Drives automated closed-loop security processing of case matching events. The ISOP SOAR module may involve the concurrent execution of multiple scripts. The running status of different scripts can be globally overviewed through the interface (execution, successful execution, failure).
The experience of the security incident handling process in the enterprise can be solidified into Playbook scripts and applied to automated response handling. The handling actions can include equipment blocking, work order sending, email notification, etc., so that security experts can start from Released from tedious and repetitive security operations and maintenance.
Automated security orchestration response "last mile" blocking response is generally executed by security equipment. NSFOCUS ISOP one-click blocking module has accumulated experience in the early stage A large number of response processing devices, such as firewalls, ADS, UTS, IDS, WAF, etc., the response actions include: session blocking, IP banning, domain name blacklist, traffic traction cleaning, etc. These devices can be directly passed through without secondary development. The SOAR module is plug-and-play. You only need to develop a plug-in based on the northbound management and control interface provided by the third-party device to complete the automated linkage orchestration response of the third-party device.
Security devices connected to the SOAR system can complete automated response processing through Playbook script calls, without the need for security operation and maintenance personnel to log in to independent security devices to configure blocking policies.
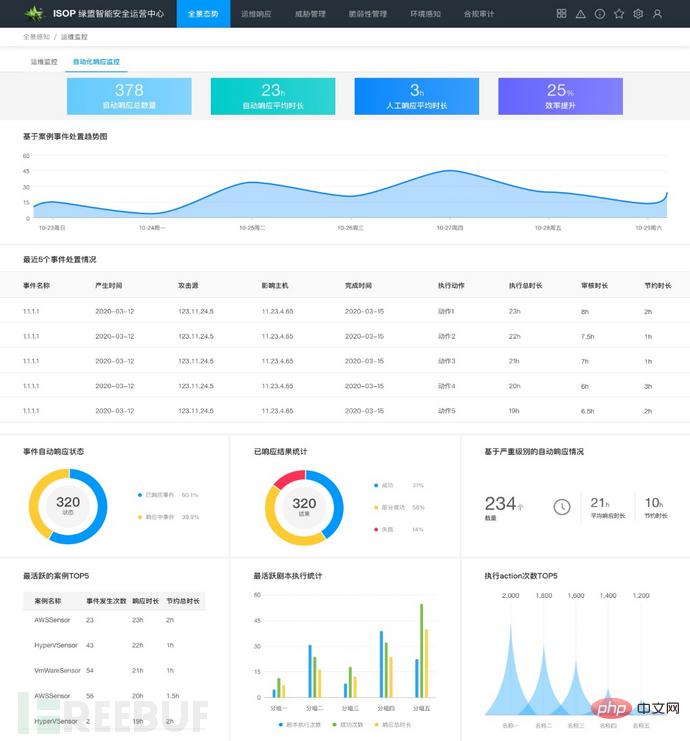 Picture: Large screen display of automated operation and maintenance
Picture: Large screen display of automated operation and maintenance
The large screen of automated operation and maintenance can present enterprise automation responses from a global perspective Disposal overview, such as automatic response operation efficiency, case incident statistical information, case incident disposal trends, script execution information, etc., displays operation and maintenance indicators in a measurable and quantifiable manner.
For known case events, through the case matching trigger mechanism, Enterprises can complete security orchestration and automated closed-loop response processes in three minutes.
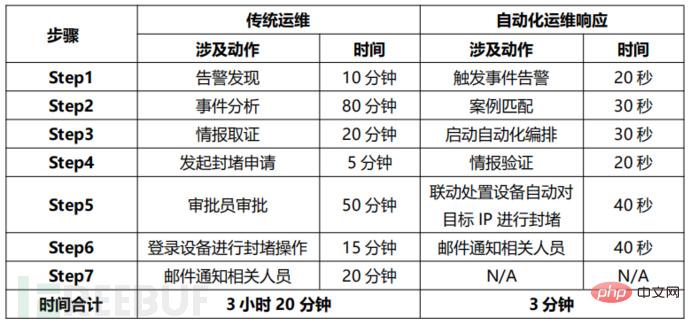
Table: Comparison of traditional operation and maintenance timeliness and automated operation and maintenance response time
Consolidate the experience of security experts into Playbooks to automate the entire process of analysis, judgment, and disposal of known attacks, so that security experts can devote their energy to red-blue confrontation, threat hunting, threat modeling, APT analysis, and vulnerabilities Mining and other work scenarios that require advanced security skills create higher value for enterprise security operation and maintenance work.
The essence of the SOAR system is the selection of research and judgment strategies and disposal strategies corresponding to different threat scenarios. This is also the role of Playbook in enterprises. The core value in the competition between offense and defense is reflected. The standardization of operation and maintenance processes is the prerequisite for the solidification of Playbook scripts. SOAR Playbooks can be used as a starting point to standardize complex and irregular processing processes and consolidate the standardization of enterprise information security operation processes.
The above is the detailed content of How to Easily Complete Enterprise Security Orchestration Response SOAR. For more information, please follow other related articles on the PHP Chinese website!
 unicode to Chinese
unicode to Chinese
 Introduction to xmpp protocol
Introduction to xmpp protocol
 What to do if the CPU temperature is too high
What to do if the CPU temperature is too high
 Usage of sprintf function in php
Usage of sprintf function in php
 How to open mds file
How to open mds file
 The role of the formatfactory tool
The role of the formatfactory tool
 JS array sorting: sort() method
JS array sorting: sort() method
 The latest ranking of the top ten exchanges in the currency circle
The latest ranking of the top ten exchanges in the currency circle
 How to check if port 445 is closed
How to check if port 445 is closed




