How SpringBoot Security implements single sign-out and clears all tokens
Requirements
Systems A, B, and C implement login through the sso service
Systems A, B, and C obtain Atoken and Btoken respectively , Ctoken three tokens
After one of the systems actively logs out, the other two systems also log out
So far all Atoken and Btoken , Ctoken invalid
Record token
pom file introduces dependency
Redis database dependency
hutool: used to parse token
<dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-data-redis</artifactId> </dependency> <dependency> <groupId>cn.hutool</groupId> <artifactId>hutool-all</artifactId> <version>5.7.13</version> </dependency>
token storage class implements AuthJdbcTokenStore
TokenStore inherits JdbcTokenStore
Use the username of the logged-in user username as the Redis key
Because there will be multiple systems where the user logs in, the value uses the Redis list type to store the token
Set the validity time to ensure that it is no less than the maximum validity time of the token in the list
@Component
public class AuthJdbcTokenStore extends JdbcTokenStore {
public static final String USER_HAVE_TOKEN = "user-tokens:";
@Resource
RedisTemplate redisTemplate;
public AuthJdbcTokenStore(DataSource connectionFactory) {
super(connectionFactory);
}
@Override
public void storeAccessToken(OAuth3AccessToken token, OAuth3Authentication authentication) {
super.storeAccessToken(token, authentication);
if (Optional.ofNullable(authentication.getUserAuthentication()).isPresent()) {
User user = (User) authentication.getUserAuthentication().getPrincipal();
String userTokensKey = USER_HAVE_TOKEN + user.getUsername();
String tokenValue = token.getValue();
redisTemplate.opsForList().leftPush(userTokensKey, tokenValue);
Long seconds = redisTemplate.opsForValue().getOperations().getExpire(userTokensKey);
Long tokenExpTime = getExpTime(tokenValue);
Long expTime = seconds < tokenExpTime ? tokenExpTime : seconds;
redisTemplate.expire(userTokensKey, expTime, TimeUnit.SECONDS);
}
}
private long getExpTime(String accessToken) {
JWT jwt = JWTUtil.parseToken(accessToken);
cn.hutool.json.JSONObject jsonObject = jwt.getPayload().getClaimsJson();
long nowTime = Instant.now().getEpochSecond();
long expEndTime = jsonObject.getLong("exp");
long expTime = (expEndTime - nowTime);
return expTime;
}
}oauth_access_token Using JdbcTokenStore to store tokens requires a new table
CREATE TABLE `oauth_access_token` ( `create_time` timestamp NULL DEFAULT CURRENT_TIMESTAMP, `token_id` varchar(255) DEFAULT NULL, `token` blob, `authentication_id` varchar(255) DEFAULT NULL, `user_name` varchar(255) DEFAULT NULL, `client_id` varchar(255) DEFAULT NULL, `authentication` blob, `refresh_token` varchar(255) DEFAULT NULL, UNIQUE KEY `authentication_id` (`authentication_id`) ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb3;
AuthorizationServerConfigurerAdapter uses AuthJdbcTokenStore for token storage
Introducing DataSource, because the construction method of JdbcTokenStore must pass in DataSource
Create according to TokenStore, Use AuthJdbcTokenStore to implement
- ##tokenServices Add TokenStore
- endpoints Add tokenServices
@Configuration
@EnableAuthorizationServer
public class AuthorizationServerConfig extends AuthorizationServerConfigurerAdapter {
@Autowired
private DataSource dataSource;
...
@Bean
public TokenStore tokenStore() {
JdbcTokenStore tokenStore = new AuthJdbcTokenStore(dataSource);
return tokenStore;
}
@Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) {
DefaultTokenServices tokenServices = new DefaultTokenServices();
tokenServices.setTokenStore(tokenStore());
endpoints
.authenticationManager(authenticationManager)
.tokenServices(tokenServices)
.accessTokenConverter(converter)
;
}
...
}- Inherit SimpleUrlLogoutSuccessHandler
- Get the username userName
- Get the token list stored in Redis during login
- Token string is converted into OAuth3AccessToken
- Use tokenStore to delete token
@Component
public class AuthLogoutSuccessHandler1 extends SimpleUrlLogoutSuccessHandler {
String USER_HAVE_TOKEN = AuthJdbcTokenStore.USER_HAVE_TOKEN;
@Resource
RedisTemplate redisTemplate;
@Resource
TokenStore tokenStore;
@Override
public void onLogoutSuccess(HttpServletRequest request, HttpServletResponse response, Authentication authentication) throws IOException, ServletException {
if (!Objects.isNull(authentication)) {
String userName = authentication.getName();
String userTokensKey = USER_HAVE_TOKEN + userName;
Long size = redisTemplate.opsForList().size(userTokensKey);
List<String> list = redisTemplate.opsForList().range(userTokensKey, 0, size);
for (String tokenValue : list) {
OAuth3AccessToken token = tokenStore.readAccessToken(tokenValue);
if (Objects.nonNull(token)) {
tokenStore.removeAccessToken(token);
}
}
redisTemplate.delete(userTokensKey);
super.handle(request, response, authentication);
}
}
}tokenStore.removeAccessToken(token);
The above is the detailed content of How SpringBoot Security implements single sign-out and clears all tokens. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1382
1382
 52
52
 17 ways to solve the kernel_security_check_failure blue screen
Feb 12, 2024 pm 08:51 PM
17 ways to solve the kernel_security_check_failure blue screen
Feb 12, 2024 pm 08:51 PM
Kernelsecuritycheckfailure (kernel check failure) is a relatively common type of stop code. However, no matter what the reason is, the blue screen error causes many users to be very distressed. Let this site carefully introduce 17 types to users. Solution. 17 solutions to kernel_security_check_failure blue screen Method 1: Remove all external devices When any external device you are using is incompatible with your version of Windows, the Kernelsecuritycheckfailure blue screen error may occur. To do this, you need to unplug all external devices before trying to restart your computer.
 How Springboot integrates Jasypt to implement configuration file encryption
Jun 01, 2023 am 08:55 AM
How Springboot integrates Jasypt to implement configuration file encryption
Jun 01, 2023 am 08:55 AM
Introduction to Jasypt Jasypt is a java library that allows a developer to add basic encryption functionality to his/her project with minimal effort and does not require a deep understanding of how encryption works. High security for one-way and two-way encryption. , standards-based encryption technology. Encrypt passwords, text, numbers, binaries... Suitable for integration into Spring-based applications, open API, for use with any JCE provider... Add the following dependency: com.github.ulisesbocchiojasypt-spring-boot-starter2. 1.1Jasypt benefits protect our system security. Even if the code is leaked, the data source can be guaranteed.
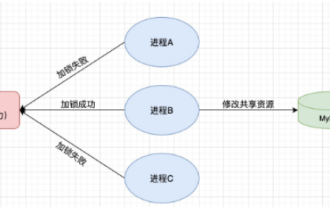 How to use Redis to implement distributed locks in SpringBoot
Jun 03, 2023 am 08:16 AM
How to use Redis to implement distributed locks in SpringBoot
Jun 03, 2023 am 08:16 AM
1. Redis implements distributed lock principle and why distributed locks are needed. Before talking about distributed locks, it is necessary to explain why distributed locks are needed. The opposite of distributed locks is stand-alone locks. When we write multi-threaded programs, we avoid data problems caused by operating a shared variable at the same time. We usually use a lock to mutually exclude the shared variables to ensure the correctness of the shared variables. Its scope of use is in the same process. If there are multiple processes that need to operate a shared resource at the same time, how can they be mutually exclusive? Today's business applications are usually microservice architecture, which also means that one application will deploy multiple processes. If multiple processes need to modify the same row of records in MySQL, in order to avoid dirty data caused by out-of-order operations, distribution needs to be introduced at this time. The style is locked. Want to achieve points
 What to do if the login token is invalid
Sep 14, 2023 am 11:33 AM
What to do if the login token is invalid
Sep 14, 2023 am 11:33 AM
Solutions to invalid login token include checking whether the Token has expired, checking whether the Token is correct, checking whether the Token has been tampered with, checking whether the Token matches the user, clearing the cache or cookies, checking the network connection and server status, logging in again or requesting a new Token. Contact technical support or developers, etc. Detailed introduction: 1. Check whether the Token has expired. The login Token usually has a validity period set. Once the validity period exceeds, it will be considered invalid, etc.
 How to solve the problem that springboot cannot access the file after reading it into a jar package
Jun 03, 2023 pm 04:38 PM
How to solve the problem that springboot cannot access the file after reading it into a jar package
Jun 03, 2023 pm 04:38 PM
Springboot reads the file, but cannot access the latest development after packaging it into a jar package. There is a situation where springboot cannot read the file after packaging it into a jar package. The reason is that after packaging, the virtual path of the file is invalid and can only be accessed through the stream. Read. The file is under resources publicvoidtest(){Listnames=newArrayList();InputStreamReaderread=null;try{ClassPathResourceresource=newClassPathResource("name.txt");Input
 How to solve the problem of invalid login token
Sep 14, 2023 am 10:57 AM
How to solve the problem of invalid login token
Sep 14, 2023 am 10:57 AM
The problem of invalid login token can be solved by checking the network connection, checking the token validity period, clearing cache and cookies, checking login status, contacting the application developer and strengthening account security. Detailed introduction: 1. Check the network connection, reconnect to the network or change the network environment; 2. Check the token validity period, obtain a new token, or contact the developer of the application; 3. Clear cache and cookies, clear browser cache and Cookie, and then log in to the application again; 4. Check the login status.
 How to implement Springboot+Mybatis-plus without using SQL statements to add multiple tables
Jun 02, 2023 am 11:07 AM
How to implement Springboot+Mybatis-plus without using SQL statements to add multiple tables
Jun 02, 2023 am 11:07 AM
When Springboot+Mybatis-plus does not use SQL statements to perform multi-table adding operations, the problems I encountered are decomposed by simulating thinking in the test environment: Create a BrandDTO object with parameters to simulate passing parameters to the background. We all know that it is extremely difficult to perform multi-table operations in Mybatis-plus. If you do not use tools such as Mybatis-plus-join, you can only configure the corresponding Mapper.xml file and configure The smelly and long ResultMap, and then write the corresponding sql statement. Although this method seems cumbersome, it is highly flexible and allows us to
 Comparison and difference analysis between SpringBoot and SpringMVC
Dec 29, 2023 am 11:02 AM
Comparison and difference analysis between SpringBoot and SpringMVC
Dec 29, 2023 am 11:02 AM
SpringBoot and SpringMVC are both commonly used frameworks in Java development, but there are some obvious differences between them. This article will explore the features and uses of these two frameworks and compare their differences. First, let's learn about SpringBoot. SpringBoot was developed by the Pivotal team to simplify the creation and deployment of applications based on the Spring framework. It provides a fast, lightweight way to build stand-alone, executable




