What are the basic knowledge points for web testing?
1. Web application
The application has two modes, C/S and B/S. C/S mode, that is, Client/Server (client/server) mode, this type of program can run independently. B/S mode, that is, Browser/Server (browser/server) mode, this type of program needs to be run with the help of a browser.
Web applications are generally in B/S mode. A Web application is composed of various Web components (web components) that complete specific tasks and displays services to the outside world through the Web. In actual applications, Web applications are composed of multiple Servlets, JSP pages, HTML files, image files, etc.
Now that we understand web applications, how to test them?
2. Functional testing
Functional testing is to verify the functions of the product. The test points are:
Link test
(1) Whether all links link to the linked page as instructed
(2) Whether the linked page exists
(3) Ensure that there are no orphan pages
Form test
(1)Verify that the server can correctly save these data
(2)The program running in the background can correctly Interpret and use this information
Cookies Test
(1) Whether Cookies work
(2) Whether Cookies are saved for a scheduled time
( 3) What impact does refreshing have on Cookies
Design language test
(1) Different versions of the design language will cause serious problems on the client and server sides
Database test
(1) Data consistency error: The submitted form information is incorrect
(2) Output error
Related functional tests
(1)Delete/ Adding an item: Does it affect other items? Are these effects correct?
(2) List default value check
(3) Check whether the button functions are correct: New, Edit, Delete , close, return, save, import, previous page, next page, page jump, reset (common errors)
(4) String length check: length exceeded
( 5) Character type check
(6) Punctuation check: spaces, various quotation marks, Enter key
(7) Special characters: common %, ","
(8) Chinese characters: Are they garbled
(9) Check the completeness of the information: Check the information to see if the filled-in information is complete and updated; update the information and see if the updated information is consistent with the added information
(10 ) Duplicate information: unique information is required, such as repeated names or IDs, whether duplicate names are case-sensitive, and spaces
(11) Check the delete function: do not select any information, press Delete to see how to deal with it; Select one or more to delete; select multiple pages or turn pages to delete; whether there is a prompt for deletion
(12) Check whether additions and modifications are consistent: add required items, modifications should also be required; add why Type, what type should be modified?
(13) Check and modify duplicate names: when modifying, change the items that cannot be renamed to existing content
(14) Submit the form repeatedly: one item has been Successfully submitted records, return and then submit
(15) Check multiple times using the return key: return to the original page, repeat multiple times
(16) Search check: existence or non-existence of content , see if the search results are correct; multiple search conditions, enter reasonable and unreasonable conditions at the same time; special characters
(17) Enter the location of the information
(18) Upload and download file check: Function Whether it is implemented, upload: whether the uploaded file can be opened, format requirements, whether the system has explanation information, modify the suffix of the file format that cannot be uploaded to an uploadable file format; download: whether the download can be opened, saved, format requirements
(19) Required item check: the required item is not filled in; whether there is a prompt, such as adding *; after returning the prompt for the required item, whether the focus is automatically positioned on the required item
(20) Quick Key check: Whether the shortcut keys Ctrl C, Ctrl V, and backspace are supported; for fields that do not allow input (such as drop-down options), whether shortcuts are also restricted
(21) Enter key check: How does the system process
after pressing the Enter key after inputting (22) Refresh key check: Press the browser refresh key How to process
(23) Back key check: Press the browser back key How to handle
(24) Space check: Enter one or more spaces for the input item
(25) Half-width and full-width check for input method: For example, for floating point type, enter a full-width decimal point ". " or ". ", such as 4.5; full-width space
(26) Password check: enter the limit characters of the encryption method; the password should be as long as possible
(27) User check: different types Different permissions of administrator users, whether they can delete, manage, and edit each other; permissions of general users; logout function, old users log out and re-register, whether they are new users
(28) System data check: data changes with the business Changes in processes and states must remain correct. Garbage data cannot appear in a certain process, nor can data be lost because of a certain process.
(29) System recoverability check: paralyze the system in various ways , test whether the system can be restored quickly
(30) Confirmation prompt check: system update, deletion operation: whether there is a prompt, cancel operation; whether the prompt is accurate; prompts before and after the event
(31) Data injection check: database injection, special characters, and destruction of SQL statements
(32) Time and date check: time, date, time verification: whether the date range conforms to the actual business; whether there are restrictions on dates that do not conform to the actual business
(33) Multi-browser verification
3. Usability test (interface test)
Overall interface test
(1) The overall feeling given to the user: comfort; being able to find the information they are looking for by feeling; Whether the design style is consistent
Control test
(2)The function of each control
Multimedia test
(1)Graphics must have a clear purpose, pictures , the animations are arranged in an orderly manner and the purpose is clear
(2) The picture button link is valid, and the link attributes are correct (for example, a new window is opened, the current page is opened)
(3) The background image should be Match the font color and foreground color
(4) Check the size and quality of the picture: generally jpg, gif, png; the size of the picture can be reduced to less than 30kb without affecting the quality of the picture
(5) Whether the gif animation is set to the correct cycle mode and whether the color is normal
(6) Whether the Flash and Silverlight elements are normal
Navigation test
( 1) Site map and navigation bar: Whether the location is reasonable; page structure
Content test
(2) The correctness, accuracy, and relevance of the information provided
Container test
(1) DIV
(2) Table: As a control, whether the settings are correct; whether the length and width are sufficient. As an earlier web page layout method, consider changes in browser window size; the impact of dynamic addition or deletion of content on the interface
4. Compatibility test
Platform test: windows; unix; macintosh ;linux
Browser test: Browsers from different manufacturers have different support for Java, Javascript, ActiveX, plug-ins or different HTML specifications; frames and hierarchies are also displayed differently in different browsers
5. Security test
Security test requirements:
(1) Be able to prevent password probing tools
(2) Be able to prevent cookies Common means of attack
(3) Sensitive data is guaranteed not to be transmitted in clear text
(4) It can prevent the acquisition of important information by guessing the file name and viewing the content of the html file
(5 ) can guarantee that the website will be restored within a given time after receiving the tool, and the loss of important data will not exceed 1 hour
Test points
(1)Application-level security
The purpose of application-level security testing is to find security risks in the programming design of the Web system itself. The test areas are:
(1.1) Registration and login: valid and invalid user names and passwords; pay attention to whether there are upper and lower case letters Sensitive; limit on how many times you can try; whether you can browse a page directly without logging in
(1.2) Online timeout: timeout limit
(1.3) Operation traces: whether related information is written Log entry
(1.4) Backup and recovery: database incremental backup; database full backup; system full backup
(2)Transport level security
Transport level security The purpose of the test is to test the possible security of data transmitted from the client to the server. loopholes , the server's ability to prevent illegal access, test points:
(2.1) HTTPS and SSL testing; server-side script vulnerability check; test the problem of not being able to place and edit scripts on the server side without authorization
(2.2) Firewall test: firewall function; firewall settings
(2.3) Data encryption test: verify the transmission, access, processing person's identity and related content of the involved information
(2.4) Key: generation, distribution, storage, replacement and destruction of keys
6. Performance test
(1) Stress test: actually destroy a web application system and test the system’s response , Test the system's limitations and fault recovery capabilities
(2) Load test: Performance at a certain load level, including the number of users accessing the Web at a certain time and the number of online data processing
(3) Strength test: Test the acceptability of the object under abnormal performance behavior or extreme conditions (such as reduced resources or too many users) to verify the system software and hardware level
(4) Database capacity Test: Insert a certain amount of data into the database table through the stored procedure to see if
can be displayed in time (5) Performance test of expected indicators: Some performance indicators will be proposed during the demand analysis and design stages. For predetermined The performance requirements must be tested first
(6) Independent business performance testing: Conduct user concurrency testing on core business modules, including performing exactly the same operations at the same time and using the exact same functions at the same time
(7) Combined business performance test: simulate the different operations of multiple users, which is closest to the actual user usage, and simulate the combined concurrency of each module according to the proportion of the actual number of users
(8) Fatigue Strength performance test: When the system is running stably, test the system to run for a long time under a certain load pressure
(9) Network performance test: Accurately display how changes in bandwidth, delay, load, and port affect users
(10) Large data volume performance test at the corresponding time: real-time large data volume, simulating the real-time large data volume when the user is working; test under extreme state, the system is used for a period of time, and when a certain amount of data is accumulated, it can Whether it can operate normally, and combine the previous two
(11) Server performance test: When conducting user concurrency performance test, fatigue strength, and large data volume performance test, complete the monitoring of server performance and conduct evaluation
(12) Some special tests : Configuration testing, some special tests for memory leaks
The above is the detailed content of What are the basic knowledge points for web testing?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
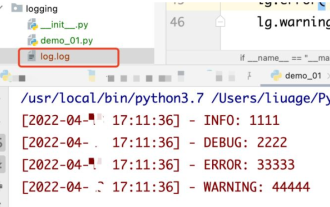 How to use python+Flask to realize real-time update and display of logs on web pages
May 17, 2023 am 11:07 AM
How to use python+Flask to realize real-time update and display of logs on web pages
May 17, 2023 am 11:07 AM
1. Log output to file using module: logging can generate a custom level log, and can output the log to a specified path. Log level: debug (debug log) = 5) {clearTimeout (time) // If all results obtained 10 consecutive times are empty Log clearing scheduled task}return}if(data.log_type==2){//If a new log is obtained for(i=0;i
 How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
Introduction to Caddy Caddy is a powerful and highly scalable web server that currently has 38K+ stars on Github. Caddy is written in Go language and can be used for static resource hosting and reverse proxy. Caddy has the following main features: Compared with the complex configuration of Nginx, its original Caddyfile configuration is very simple; it can dynamically modify the configuration through the AdminAPI it provides; it supports automated HTTPS configuration by default, and can automatically apply for HTTPS certificates and configure it; it can be expanded to data Tens of thousands of sites; can be executed anywhere with no additional dependencies; written in Go language, memory safety is more guaranteed. First of all, we install it directly in CentO
 Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web Server Processing in JavaAPI Development With the development of the Internet, the Web server has become the core part of application development and is also the focus of many enterprises. In order to meet the growing business needs, many developers choose to use Jetty for web server development, and its flexibility and scalability are widely recognized. This article will introduce how to use Jetty7 in JavaAPI development for We
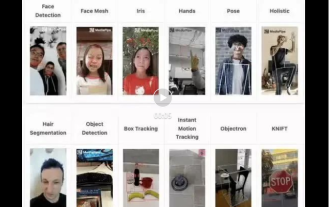 Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Face-blocking barrage means that a large number of barrages float by without blocking the person in the video, making it look like they are floating from behind the person. Machine learning has been popular for several years, but many people don’t know that these capabilities can also be run in browsers. This article introduces the practical optimization process in video barrages. At the end of the article, it lists some applicable scenarios for this solution, hoping to open it up. Some ideas. mediapipeDemo (https://google.github.io/mediapipe/) demonstrates the mainstream implementation principle of face-blocking barrage on-demand up upload. The server background calculation extracts the portrait area in the video screen, and converts it into svg storage while the client plays the video. Download svg from the server and combine it with barrage, portrait
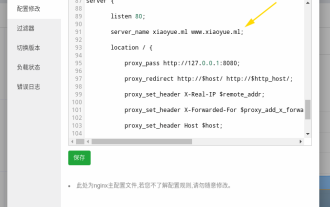 How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
First of all, you will have a doubt, what is frp? Simply put, frp is an intranet penetration tool. After configuring the client, you can access the intranet through the server. Now my server has used nginx as the website, and there is only one port 80. So what should I do if the FRP server also wants to use port 80? After querying, this can be achieved by using nginx's reverse proxy. To add: frps is the server, frpc is the client. Step 1: Modify the nginx.conf configuration file in the server and add the following parameters to http{} in nginx.conf, server{listen80
 How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
Form validation is a very important link in web application development. It can check the validity of the data before submitting the form data to avoid security vulnerabilities and data errors in the application. Form validation for web applications can be easily implemented using Golang. This article will introduce how to use Golang to implement form validation for web applications. 1. Basic elements of form validation Before introducing how to implement form validation, we need to know what the basic elements of form validation are. Form elements: form elements are
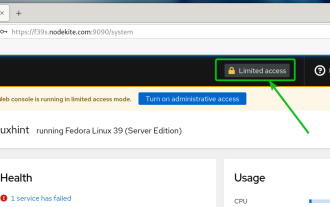 How to enable administrative access from the cockpit web UI
Mar 20, 2024 pm 06:56 PM
How to enable administrative access from the cockpit web UI
Mar 20, 2024 pm 06:56 PM
Cockpit is a web-based graphical interface for Linux servers. It is mainly intended to make managing Linux servers easier for new/expert users. In this article, we will discuss Cockpit access modes and how to switch administrative access to Cockpit from CockpitWebUI. Content Topics: Cockpit Entry Modes Finding the Current Cockpit Access Mode Enable Administrative Access for Cockpit from CockpitWebUI Disabling Administrative Access for Cockpit from CockpitWebUI Conclusion Cockpit Entry Modes The cockpit has two access modes: Restricted Access: This is the default for the cockpit access mode. In this access mode you cannot access the web user from the cockpit
 What are web standards?
Oct 18, 2023 pm 05:24 PM
What are web standards?
Oct 18, 2023 pm 05:24 PM
Web standards are a set of specifications and guidelines developed by W3C and other related organizations. It includes standardization of HTML, CSS, JavaScript, DOM, Web accessibility and performance optimization. By following these standards, the compatibility of pages can be improved. , accessibility, maintainability and performance. The goal of web standards is to enable web content to be displayed and interacted consistently on different platforms, browsers and devices, providing better user experience and development efficiency.




