 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 What are common web security vulnerabilities and testing methods?
What are common web security vulnerabilities and testing methods?
What are common web security vulnerabilities and testing methods?
1. Six basic principles of security testing:
Authentication: Return of requests for authenticated users
Access control: Permission control and data protection for unauthenticated users
Integrity: The user must accurately receive the information sent by the server
Confidentiality: The information must be accurately delivered to the intended user
Reliability: How often does it fail? How long does it take for the network to recover from a failure? What steps are taken to deal with catastrophic failure? (Personally, I understand that this place should be more biased towards the category of fault-tolerance and disaster-tolerance testing)
Non-repudiation: Users should be able to prove that the data received comes from a specific server
2. Common security test content
Permission Control
SQL Injection
URL Security Test
XSS (Cross-site Scripting Attack)
CSRF (Cross-site Request Forgery) )
URL jump vulnerability
Other security considerations
3. What causes security problems in Web applications? Generally, there are several reasons:
1. Complex application systems have a large amount of code and many developers, so negligence is inevitable.
2. The system has been upgraded many times and personnel have been changed frequently, resulting in code inconsistency.
3. Multiple Web systems such as historical legacy systems and trial operation systems run together on the same server.
4. Developers have not received secure coding training or the company simply does not have unified secure coding standards.
5. The testers are inexperienced or released without professional security assessment testing.
6. There is no verification of user input, here are a few examples:
1) Never trust user input, verify user input
2) Numeric input must be legal numbers
3) Character input requires special processing of encoding symbols
4) Verify all input points, including Get, Post, Cookies and other HTTP headers
4. Common vulnerabilities and solutions in security testing:
1. XSS cross-site scripting attack
SS is similar to SQL injection, XSS is Inserting malicious scripts through web pages mainly uses front-end HTML and JavaScript scripts. When the user browses the web, an attack method is implemented to control the user's browser behavior.
A successful XSS can obtain the user's cookie and use the cookie to steal the user's operating permissions for the website; it can also obtain the user's contact list and use the identity of the attacker to target specific targets. Send a lot of spam to the group, etc.
XSS is divided into three categories: storage type (persistent XSS), reflection type (non-persistent XSS), and DOM type.
Test method:
In the data input interface, enter: <script>alert(/123/)</script>. If a dialog box pops up after successful saving, it indicates that there is An XSS vulnerability.
Or change the parameters in the url request to <script>alert(/123/)</script>. If a dialog box pops up on the page, it indicates that there is an XSS vulnerability.
2. SQL injection
SQL injection is to insert SQL commands into the Web form submission or enter the query character
string of the domain name or page request, and ultimately deceive the server to execute Malicious SQL commands.
The possible harms caused by SQL injection include: web pages and data are tampered with, core data is stolen, and the server where the database is located is attacked and turned into a puppet host.
For example, some websites do not use precompiled sql, and some fields entered by the user on the interface are added to the sql. It is very likely that these fields contain some malicious sql commands. For example: password = "1' OR '1'='1"; even if you don't know the user password, you can log in normally.
Test method:
On the page that needs to be queried, enter the correct query conditions and simple sql statements such as 1=1, and check the response results. If the results returned by entering the correct query conditions are consistent, it means The application does not filter user input, and it can be initially determined that there is a SQL injection vulnerability.
Modification suggestions:
Verify user input, you can use regular expressions, or limit the length ;Convert the following keywords, etc.;
||alert|and|exec|execute|insert|select|delete|update|count|drop|chr|mid|master|truncate|declare|sitename|netuser |xp_cmdshell|or| |,|like'|and|exec|execute|insert|create|drop|table|from|grant|group_concat|column_name|information_schema.columns|table_schema|union|where|select|delete|update|order |by|count|chr|mid|master|truncate|declare|or|--| |,|like|//
Do not use dynamic assembly sql, you can use parameterized sql or directly use stored procedures Perform data query and access;
Do not use database connections with administrator privileges, use separate database connections with limited permissions for each application;
Exception information for applications should be given as little as possible Tip, it is best to wrap the original error message with a custom error message.
3. URL jump vulnerability
URL jump vulnerability, that is, an unverified redirect vulnerability, refers to a web program that jumps directly to the URL in the parameter, or is introduced in the page The URL of any developer is redirected to an unsafe third-party area, thus causing security issues.
Test method:
1. Use the packet capture tool to capture the request.
2. Grab the 302 URL, modify the target address, and check if it can jump.
ps: However, many jumps now have referer verification added, causing the attacker to fail to jump.
4. File upload vulnerability
A file upload attack means that the attacker uploads an executable file to the server and executes it.
This attack method is the most direct and effective. The uploaded files can be viruses, Trojans, malicious scripts, webshells, etc.
Webshell is a command execution environment that exists in the form of web files such as asp, php, jsp or cgi. It can also be said to be a web backdoor. After an attacker prevents or inserts a webshell into the affected system, he can easily enter the system through the webshell and control the website server.
Test method:
Strictly verify the uploaded file type, size, etc., and prohibit the uploading of files with malicious code.
Verify the execution permissions of the relevant directories. You can access all directories on the Web server through the browser and check whether the directory structure is returned. If the directory structure is displayed, there may be a security issue.
5. CSRF cross-site forged request attack
CSRF uses the identity of the logged-in user to send malicious requests in the name of the user to complete illegal operations.
For example: If a user browses and trusts website A that has a CSRF vulnerability, the browser generates a corresponding cookie, and the user visits dangerous website B without exiting the website.
Dangerous website B requires access to website A and makes a request. The browser visits website A with the user's cookie information. Because website A does not know whether the request is from the user itself or from dangerous website B, it will process the request from dangerous website B, thus completing the simulation of user operations. Purpose. This is the basic idea of CSRF attacks.
Test method:
1. Open two pages with the same browser. After the permission of one page expires, can the other page be successfully operated? If it can still be successfully operated, there is a risk.
2. Use tools to send requests, do not add the referer field in the http request header, check the response of the returned message, and redirect to the error interface or login interface.
The above is the detailed content of What are common web security vulnerabilities and testing methods?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1381
1381
 52
52
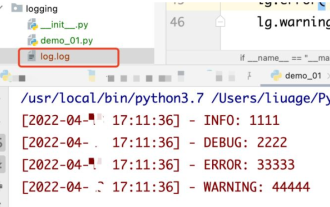 How to use python+Flask to realize real-time update and display of logs on web pages
May 17, 2023 am 11:07 AM
How to use python+Flask to realize real-time update and display of logs on web pages
May 17, 2023 am 11:07 AM
1. Log output to file using module: logging can generate a custom level log, and can output the log to a specified path. Log level: debug (debug log) = 5) {clearTimeout (time) // If all results obtained 10 consecutive times are empty Log clearing scheduled task}return}if(data.log_type==2){//If a new log is obtained for(i=0;i
 How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
Introduction to Caddy Caddy is a powerful and highly scalable web server that currently has 38K+ stars on Github. Caddy is written in Go language and can be used for static resource hosting and reverse proxy. Caddy has the following main features: Compared with the complex configuration of Nginx, its original Caddyfile configuration is very simple; it can dynamically modify the configuration through the AdminAPI it provides; it supports automated HTTPS configuration by default, and can automatically apply for HTTPS certificates and configure it; it can be expanded to data Tens of thousands of sites; can be executed anywhere with no additional dependencies; written in Go language, memory safety is more guaranteed. First of all, we install it directly in CentO
 Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web Server Processing in JavaAPI Development With the development of the Internet, the Web server has become the core part of application development and is also the focus of many enterprises. In order to meet the growing business needs, many developers choose to use Jetty for web server development, and its flexibility and scalability are widely recognized. This article will introduce how to use Jetty7 in JavaAPI development for We
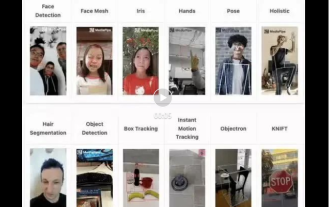 Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Face-blocking barrage means that a large number of barrages float by without blocking the person in the video, making it look like they are floating from behind the person. Machine learning has been popular for several years, but many people don’t know that these capabilities can also be run in browsers. This article introduces the practical optimization process in video barrages. At the end of the article, it lists some applicable scenarios for this solution, hoping to open it up. Some ideas. mediapipeDemo (https://google.github.io/mediapipe/) demonstrates the mainstream implementation principle of face-blocking barrage on-demand up upload. The server background calculation extracts the portrait area in the video screen, and converts it into svg storage while the client plays the video. Download svg from the server and combine it with barrage, portrait
 How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
Form validation is a very important link in web application development. It can check the validity of the data before submitting the form data to avoid security vulnerabilities and data errors in the application. Form validation for web applications can be easily implemented using Golang. This article will introduce how to use Golang to implement form validation for web applications. 1. Basic elements of form validation Before introducing how to implement form validation, we need to know what the basic elements of form validation are. Form elements: form elements are
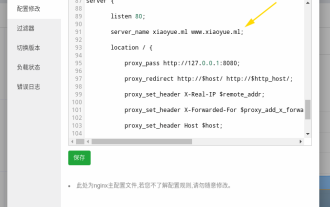 How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
First of all, you will have a doubt, what is frp? Simply put, frp is an intranet penetration tool. After configuring the client, you can access the intranet through the server. Now my server has used nginx as the website, and there is only one port 80. So what should I do if the FRP server also wants to use port 80? After querying, this can be achieved by using nginx's reverse proxy. To add: frps is the server, frpc is the client. Step 1: Modify the nginx.conf configuration file in the server and add the following parameters to http{} in nginx.conf, server{listen80
 How to enable administrative access from the cockpit web UI
Mar 20, 2024 pm 06:56 PM
How to enable administrative access from the cockpit web UI
Mar 20, 2024 pm 06:56 PM
Cockpit is a web-based graphical interface for Linux servers. It is mainly intended to make managing Linux servers easier for new/expert users. In this article, we will discuss Cockpit access modes and how to switch administrative access to Cockpit from CockpitWebUI. Content Topics: Cockpit Entry Modes Finding the Current Cockpit Access Mode Enable Administrative Access for Cockpit from CockpitWebUI Disabling Administrative Access for Cockpit from CockpitWebUI Conclusion Cockpit Entry Modes The cockpit has two access modes: Restricted Access: This is the default for the cockpit access mode. In this access mode you cannot access the web user from the cockpit
 What are web standards?
Oct 18, 2023 pm 05:24 PM
What are web standards?
Oct 18, 2023 pm 05:24 PM
Web standards are a set of specifications and guidelines developed by W3C and other related organizations. It includes standardization of HTML, CSS, JavaScript, DOM, Web accessibility and performance optimization. By following these standards, the compatibility of pages can be improved. , accessibility, maintainability and performance. The goal of web standards is to enable web content to be displayed and interacted consistently on different platforms, browsers and devices, providing better user experience and development efficiency.



