 Operation and Maintenance
Operation and Maintenance
 Nginx
Nginx
 How to prevent Nginx from being maliciously parsed by domain names
How to prevent Nginx from being maliciously parsed by domain names
How to prevent Nginx from being maliciously parsed by domain names
Mainly due to the lack of the following configuration code: nginx version 1.8.0
server {
listen 80 default_server;
server_name _;
return 403;
}Let all unconfigured server_name return 403 error
I have never added this configuration to nginx before , but I have never encountered such a problem before, and I tested it on another server. Even without this code, it is impossible to parse and request successfully. I am very speechless.
Supplement:
After searching around, I found that nginx should use its own unique 444 status code for this kind of problem. It is best
server {
listen 80 default_server;
server_name _;
access_log off;
return 444;
}This way on the browser side When accessing, the browser will automatically prompt the user that the user cannot access
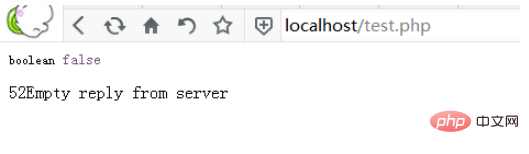
The results captured through curl (the output is http error message)
The above is the detailed content of How to prevent Nginx from being maliciously parsed by domain names. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to allow external network access to tomcat server
Apr 21, 2024 am 07:22 AM
How to allow external network access to tomcat server
Apr 21, 2024 am 07:22 AM
To allow the Tomcat server to access the external network, you need to: modify the Tomcat configuration file to allow external connections. Add a firewall rule to allow access to the Tomcat server port. Create a DNS record pointing the domain name to the Tomcat server public IP. Optional: Use a reverse proxy to improve security and performance. Optional: Set up HTTPS for increased security.
 How to run thinkphp
Apr 09, 2024 pm 05:39 PM
How to run thinkphp
Apr 09, 2024 pm 05:39 PM
Steps to run ThinkPHP Framework locally: Download and unzip ThinkPHP Framework to a local directory. Create a virtual host (optional) pointing to the ThinkPHP root directory. Configure database connection parameters. Start the web server. Initialize the ThinkPHP application. Access the ThinkPHP application URL and run it.
 What are the nginx start and stop commands?
Apr 02, 2024 pm 08:45 PM
What are the nginx start and stop commands?
Apr 02, 2024 pm 08:45 PM
The start and stop commands of Nginx are nginx and nginx -s quit respectively. The start command starts the server directly, while the stop command gracefully shuts down the server, allowing all current requests to be processed. Other available stop signals include stop and reload.
 Welcome to nginx!How to solve it?
Apr 17, 2024 am 05:12 AM
Welcome to nginx!How to solve it?
Apr 17, 2024 am 05:12 AM
To solve the "Welcome to nginx!" error, you need to check the virtual host configuration, enable the virtual host, reload Nginx, if the virtual host configuration file cannot be found, create a default page and reload Nginx, then the error message will disappear and the website will be normal show.
 How to register phpmyadmin
Apr 07, 2024 pm 02:45 PM
How to register phpmyadmin
Apr 07, 2024 pm 02:45 PM
To register for phpMyAdmin, you need to first create a MySQL user and grant permissions to it, then download, install and configure phpMyAdmin, and finally log in to phpMyAdmin to manage the database.
 How to deploy nodejs project to server
Apr 21, 2024 am 04:40 AM
How to deploy nodejs project to server
Apr 21, 2024 am 04:40 AM
Server deployment steps for a Node.js project: Prepare the deployment environment: obtain server access, install Node.js, set up a Git repository. Build the application: Use npm run build to generate deployable code and dependencies. Upload code to the server: via Git or File Transfer Protocol. Install dependencies: SSH into the server and use npm install to install application dependencies. Start the application: Use a command such as node index.js to start the application, or use a process manager such as pm2. Configure a reverse proxy (optional): Use a reverse proxy such as Nginx or Apache to route traffic to your application
 How to solve the problem of nginx when accessing the website
Apr 02, 2024 pm 08:39 PM
How to solve the problem of nginx when accessing the website
Apr 02, 2024 pm 08:39 PM
nginx appears when accessing a website. The reasons may be: server maintenance, busy server, browser cache, DNS issues, firewall blocking, website misconfiguration, network connection issues, or the website is down. Try the following solutions: wait for maintenance to end, visit during off-peak hours, clear your browser cache, flush your DNS cache, disable firewall or antivirus software, contact the site administrator, check your network connection, or use a search engine or web archive to find another copy of the site. If the problem persists, please contact the site administrator.
 How to communicate between docker containers
Apr 07, 2024 pm 06:24 PM
How to communicate between docker containers
Apr 07, 2024 pm 06:24 PM
There are five methods for container communication in the Docker environment: shared network, Docker Compose, network proxy, shared volume, and message queue. Depending on your isolation and security needs, choose the most appropriate communication method, such as leveraging Docker Compose to simplify connections or using a network proxy to increase isolation.





