
The Writeup I share with you today is a static analysis of Android APP. Due to the problems of insecure storage and hard-coded password leakage in the APP, it is possible to log in to its SMS management system and hijack its SMS interface configuration. The following is relevant analysis and research.
Since the scope of the public testing project involves a certain Android APP from a relevant manufacturer, I downloaded this APP on my Android phone and put it The APK file is taken out for static analysis. Here are two native and fast APK download URLs recommended:
https://apk.support/apk-downloader
https://apkpure.com/
After obtaining the APK file, we need to decompile it and find the Java class files in it for analysis. You can install the following two tools here:
https://github. com/pxb1988/dex2jar
https://mac.filehorse.com/download-jd-gui-java-decompiler/
After installing the above tools, we put the target APP Put the APK file into another separate folder, change its suffix from .apk to .zip, and then unzip the zip file. After that, we can see some xml documents, path files, template resource files, etc., in these files Our target is the classes.dex file. After decompression, you will usually find one or more classes.dex files. Next, we can convert the dex file into a java file by using the dex2jar tool. The specific command is as follows:
dex2jar classes.dex
If this command does not work, Then you can use another version of dex2jar command:
d2j-dex2jar classes.dex
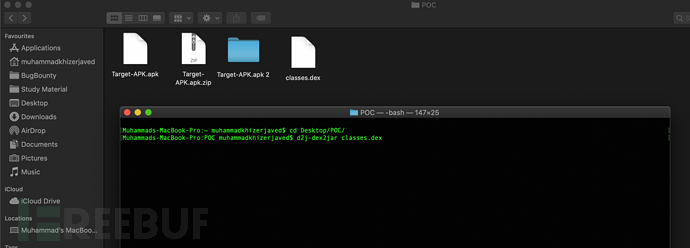 After running the above command, classes_dex2jar will be generated in the folder. jar's java file. Once we have this file, we have to use another useful tool to decompile it. I personally like to use JD-GUI here, https://github.com/java-decompiler /jd-gui, after using it to open the generated jar file, we can see many java resource files, and we can also save and read these different resource files.
After running the above command, classes_dex2jar will be generated in the folder. jar's java file. Once we have this file, we have to use another useful tool to decompile it. I personally like to use JD-GUI here, https://github.com/java-decompiler /jd-gui, after using it to open the generated jar file, we can see many java resource files, and we can also save and read these different resource files.
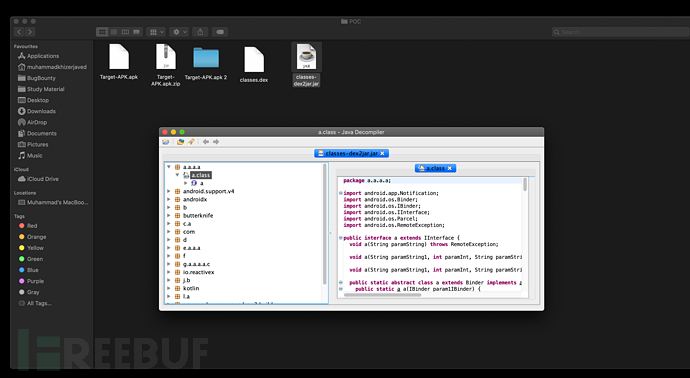
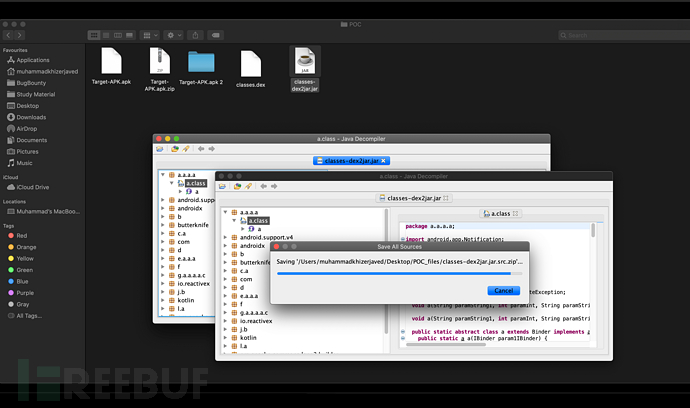 With the saved resource file code, we must try to find some problems from it. Here I recommend a tool - the automated mobile security penetration testing framework: Mobile Security Framework (MobSF) , it is an intelligent, integrated open source mobile application (Android/iOS) automatic penetration testing framework that supports binary files (APK & IPA) and source code compression packages. It can be used for static and dynamic analysis.
With the saved resource file code, we must try to find some problems from it. Here I recommend a tool - the automated mobile security penetration testing framework: Mobile Security Framework (MobSF) , it is an intelligent, integrated open source mobile application (Android/iOS) automatic penetration testing framework that supports binary files (APK & IPA) and source code compression packages. It can be used for static and dynamic analysis.
After completing the above work, we can deeply analyze the code of the target Android APP. When I sat down to analyze according to my checklist, I soon found one of the files called Constant.java. It was located in the SMS path of the APP and contained some scattered information, such as Username, Loacation, Password and other hard-coded services. Message and the URL path of the SMS API. The general situation is as follows:
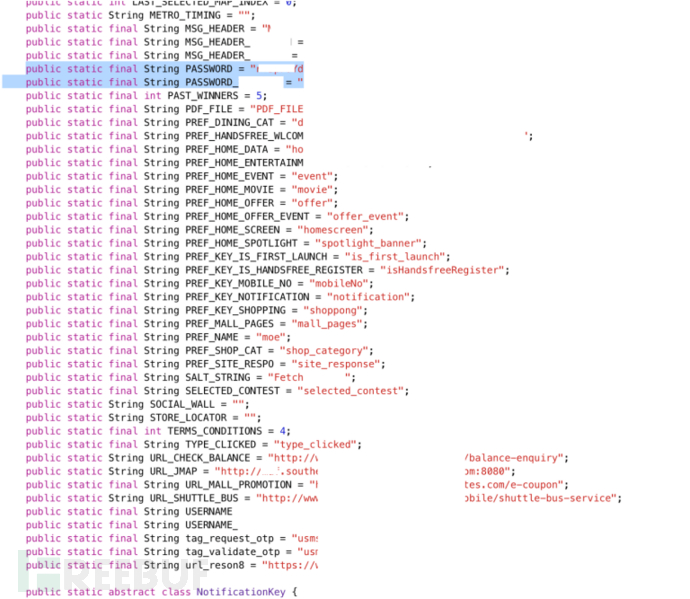 Further analysis found that the APP uses reson8 company’s instant messaging platform for commercial promotion, https://www.reson8.ae/, I browsed the reson8 company website , and found that it has a user login interface, so I thought of the Username and Password information leaked in the above static analysis, and brought it here to log in and use it. Sure enough, as soon as I entered and submitted, I entered the SMS sending management of the target APP company. System:
Further analysis found that the APP uses reson8 company’s instant messaging platform for commercial promotion, https://www.reson8.ae/, I browsed the reson8 company website , and found that it has a user login interface, so I thought of the Username and Password information leaked in the above static analysis, and brought it here to log in and use it. Sure enough, as soon as I entered and submitted, I entered the SMS sending management of the target APP company. System:
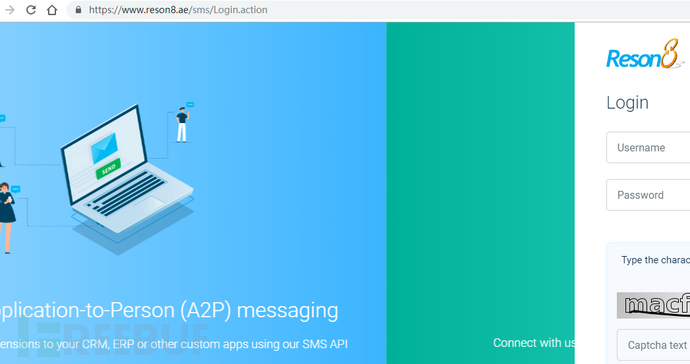
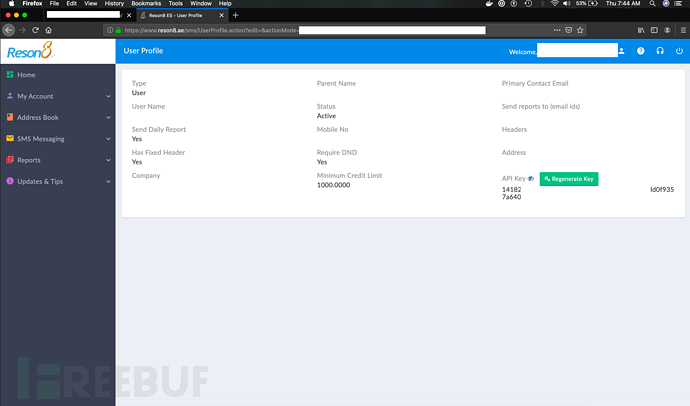
The management system is an SMS API gateway, through which management operations such as SMS directional sending settings, marketing upgrades and recharges can be implemented, and more importantly It is the mobile phone number of the user that can be downloaded.
Before doing dynamic and other analysis on the APP, it is recommended to do some static analysis on it. You can do it in sequence according to your own check list, and you may be able to get some unexpected bits and pieces from it. information. For APP application companies, they must avoid storing some password and credential-related information in the APP. Even if necessary, some appropriate encryption processing is required.
The above is the detailed content of Example analysis of static analysis of APK files to discover leakage of hard-coded passwords in APP applications. For more information, please follow other related articles on the PHP Chinese website!




