How idaPro analyzes app decryption lua script
Taking the previous IDAPRO or HOOK, we can get XXTEA decrypting key. For SIGN, we can directly open the original file:
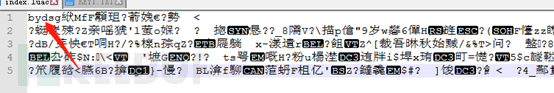
This can see the SIGN value: byds. Therefore, we can try to use the xxtea decryption tool (by getting the source code on GitHub and compiling it) to decrypt
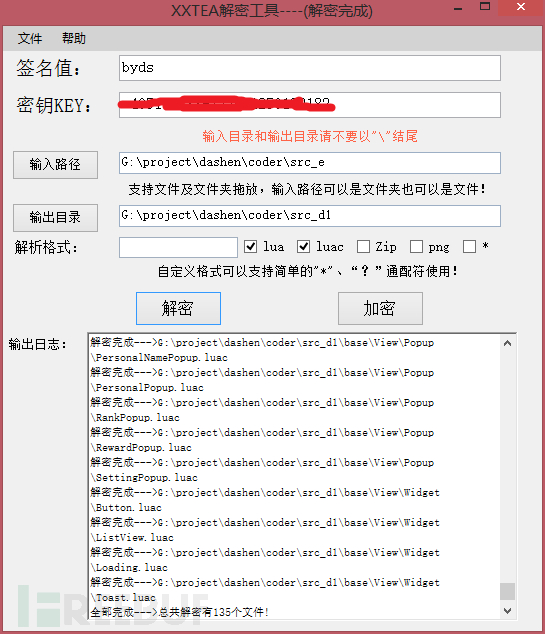
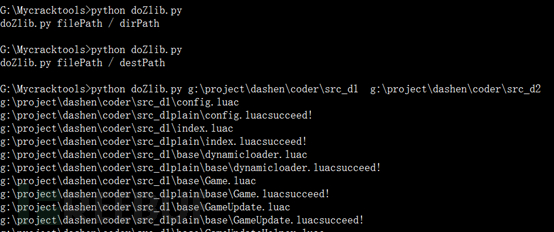
Take index.luac as an example, let’s look at index.luac decryption Changes before and after:
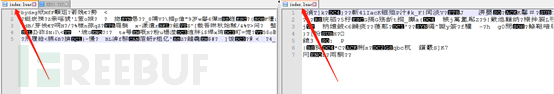
We see that the lua script decrypted by xxtea is still not clear text! We previously determined that the xxtea encryption was used based on the cocos2d framework source code and the master apk decoding result, and the app's Lua script also has a signature value, which also confirms that it is the xxtea encryption method, but the result we decrypted is still not plain text, which shows that we The decryption may not be complete. You have to go back to idapro to find out.
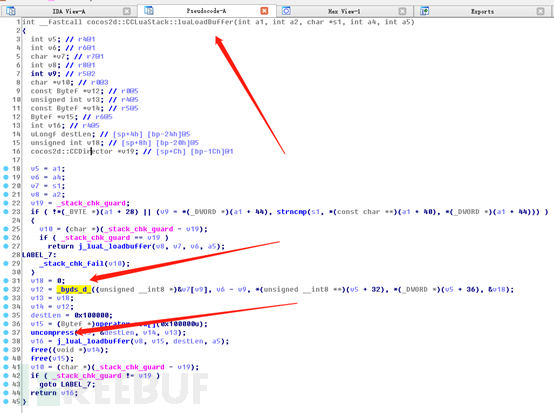
Open libgame.so with IDAPRO, search for Byds in the Export window, find the byds_d function, double -click in:
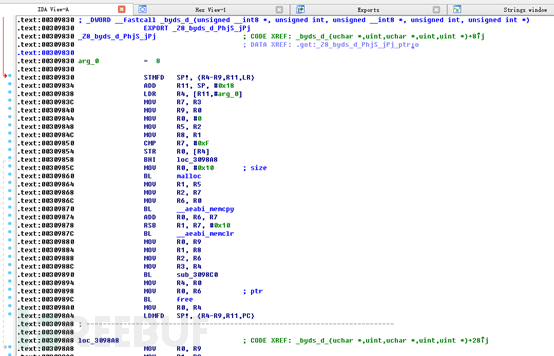
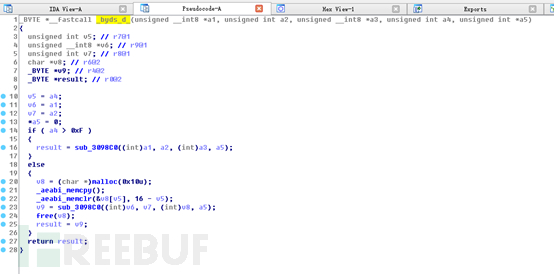
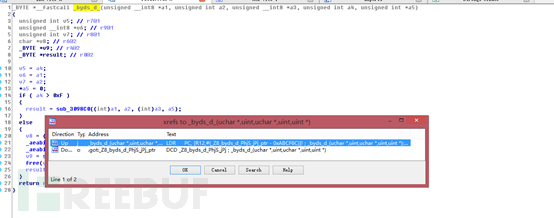
 Double-click to enter:
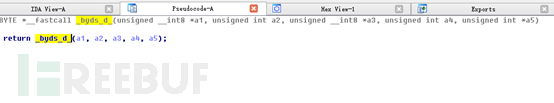
Double-click to enter:
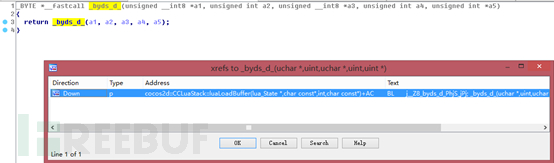 We see that the name of this function is the same as the call to xxtea_decrypt in the source code. We also included this function in the breach at the beginning. Now you can clearly see that after the script has been decrypted by byds_d, it has been decompressed again. It should be basically clear now. The lua script should be compressed and encrypted, so if you want to restore it, you should first decrypt it with xxtea and then decrypt it. compression. You can find a script to decompress zlib on GitHub, which can be used to decompress the decrypted text
We see that the name of this function is the same as the call to xxtea_decrypt in the source code. We also included this function in the breach at the beginning. Now you can clearly see that after the script has been decrypted by byds_d, it has been decompressed again. It should be basically clear now. The lua script should be compressed and encrypted, so if you want to restore it, you should first decrypt it with xxtea and then decrypt it. compression. You can find a script to decompress zlib on GitHub, which can be used to decompress the decrypted text
 Then look at index.lua:
Then look at index.lua:
 You can see that it has become clear text now.
You can see that it has become clear text now.
The above is the detailed content of How idaPro analyzes app decryption lua script. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to perform real-name authentication on Jingdong Mall APP
Mar 19, 2024 pm 02:31 PM
How to perform real-name authentication on Jingdong Mall APP
Mar 19, 2024 pm 02:31 PM
How to get real-name authentication on Jingdong Mall APP? Jingdong Mall is an online shopping platform that many friends often use. Before shopping, it is best for everyone to conduct real-name authentication so that they can enjoy complete services and get a better shopping experience. The following is the real-name authentication method for JD.com, I hope it will be helpful to netizens. 1. Install and open JD.com, and then log in to your personal account; 2. Then click [My] at the bottom of the page to enter the personal center page; 3. Then click the small [Settings] icon in the upper right corner to go to the setting function interface; 4. Select [Account and Security] to go to the account settings page; 5. Finally, click the [Real-name Authentication] option to fill in the real-name information; 6. The installation system requires you to fill in your real personal information and complete the real-name authentication
 How to install and configure Lua support for Nginx
Jun 02, 2023 pm 10:01 PM
How to install and configure Lua support for Nginx
Jun 02, 2023 pm 10:01 PM
Nginx installation and configuration Lua support By default, Nginx does not support Lua modules. You need to install the LuaJIT interpreter and recompile Nginx, or you can use the modules required by openrestry developed by Chinese people: LuaJIT, Ngx_devel and lua-nginx-module1. Environment preparation [root @nginx_lua~]#yuminstall-ygccgcc-c++makepcre-develzlib-developenssl-devel2. Download the latest luajit and ngx_devel_kit and lua-nginx-module decompression [r
 Steps and precautions for registering a Hong Kong Apple ID (enjoy the unique advantages of the Hong Kong Apple Store)
Sep 02, 2024 pm 03:47 PM
Steps and precautions for registering a Hong Kong Apple ID (enjoy the unique advantages of the Hong Kong Apple Store)
Sep 02, 2024 pm 03:47 PM
Apple's products and services have always been loved by users around the world. Registering a Hong Kong Apple ID will bring more convenience and privileges to users. Let’s take a look at the steps to register a Hong Kong Apple ID and what you need to pay attention to. How to register a Hong Kong Apple ID When using Apple devices, many applications and functions require using Apple ID to log in. If you want to download applications from Hong Kong or enjoy the preferential content of the Hong Kong AppStore, it is very necessary to register a Hong Kong Apple ID. This article will detail the steps on how to register a Hong Kong Apple ID and what you need to pay attention to. Steps: Select language and region: Find the "Settings" option on your Apple device and enter
 How to cancel the data package on China Unicom app How to cancel the data package on China Unicom
Mar 18, 2024 pm 10:10 PM
How to cancel the data package on China Unicom app How to cancel the data package on China Unicom
Mar 18, 2024 pm 10:10 PM
The China Unicom app can easily meet everyone's needs. It has various functions to solve your needs. If you want to handle various services, you can easily do it here. If you don't need it, you can unsubscribe in time here. It is effective. To avoid subsequent losses, many people sometimes feel that the data is not enough when using mobile phones, so they buy additional data packages. However, they don’t want it next month and want to unsubscribe immediately. Here, the editor explains We provide a method to unsubscribe, so that friends who need it can come and use it! In the China Unicom app, find the "My" option in the lower right corner and click on it. In the My interface, slide the My Services column and click the "I have ordered" option
 Integration of Vue.js and Lua language to write lightweight embedded applications
Jul 31, 2023 pm 02:23 PM
Integration of Vue.js and Lua language to write lightweight embedded applications
Jul 31, 2023 pm 02:23 PM
The integration of Vue.js and Lua language to write lightweight embedded applications. In modern development, the front-end framework Vue.js and the scripting language Lua each have a wide range of applications. Vue.js is a progressive framework for building user interfaces, while Lua is a lightweight scripting language often used for embedded application and game development. This article will introduce how to integrate Vue.js with Lua language to write lightweight embedded applications, and provide code examples. First, we need to install Vue.j
 How to issue invoices with multipoint app
Mar 14, 2024 am 10:00 AM
How to issue invoices with multipoint app
Mar 14, 2024 am 10:00 AM
As a shopping voucher, invoices are crucial to our daily lives and work. So when we usually use Duodian app for shopping, how can we easily issue invoices in Duodian app? Below, the editor of this website will bring you a detailed step-by-step guide for opening invoices on multi-point apps. Users who want to know more must not miss it. Come and follow the text to learn more! In the [Invoice Center], click [Multi-Point Supermarket/Free Shopping], select the order that needs to be invoiced on the completed order page, click Next to fill in the [Invoice Information], [Recipient Information], and click Submit after confirming that they are correct. After a few minutes, enter the receiving mailbox, open the email, click on the electronic invoice download address, and finally download and print the electronic invoice.
 How to use Redis+Lua script to implement the anti-swipe function of the counter interface
May 28, 2023 pm 11:32 PM
How to use Redis+Lua script to implement the anti-swipe function of the counter interface
May 28, 2023 pm 11:32 PM
[Implementation process] 1. Problem analysis If the set command is set, but when setting the expiration time, the setting is not successful due to network jitter and other reasons, then a dead counter (similar to a deadlock) will appear; 2. Solution Redis+Lua It is a good solution. Use a script to make the set command and the expire command work together so that Redis is executed without being interfered with. This guarantees atomic operations to a large extent. Why is it said that it guarantees atomic operations to a large extent rather than completely? ensure? Because problems may occur when Redis is executed internally, but the probability is very small; even for small-probability events, there are corresponding solutions, such as solving deadlocks. An idea worth referring to: To prevent deadlocks, the value of the lock will be stored in
 Integration of Vue.js and Lua language, best practices and experience sharing in building front-end engines for game development
Aug 01, 2023 pm 08:14 PM
Integration of Vue.js and Lua language, best practices and experience sharing in building front-end engines for game development
Aug 01, 2023 pm 08:14 PM
The integration of Vue.js and Lua language, best practices and experience sharing for building a front-end engine for game development Introduction: With the continuous development of game development, the choice of game front-end engine has become an important decision. Among these choices, the Vue.js framework and Lua language have become the focus of many developers. As a popular front-end framework, Vue.js has a rich ecosystem and convenient development methods, while the Lua language is widely used in game development because of its lightweight and efficient performance. This article will explore how to




