
In March 2017, ShadowBrokers released a confidential document that shocked the world, including two frameworks: DanderSpritz and FuzzBunch.
DanderSpritz is a pure plug-in designed to gather intelligence, exploit vulnerabilities, and control the taken over device. It is written in Java and provides a graphical interface similar to the botnet management panel and a control panel similar to the Metasploit tool. It also incorporates backdoors and plugins for non-FuzzBunch controlled devices.
DanderSprit Interface
Fuzzbunch provides a framework for different utilities to interact and work together, including various A type of plug-in whose purpose is to analyze objects, exploit vulnerabilities, implant tasks, etc. The files in the FuzzBunch framework plug-in package are divided into three types:
%pluginName%-version.fb
This is the utility file of the framework. It copies the header from the XML and contains the plugin's ID.
%pluginName%-version.exe
Run this executable file when FuZZbuNch receives the execution command.
%pluginName%-version.xml
This configuration file describes the name, type, and description of the plugin's input and output parameters. This information can be displayed through the FuzzBunch interface. This file type classification standard specifies the setting of default parameters, thereby enhancing the operability of the framework.
ImplantConfig is a Fuzzbunch callable toolkit, including a management module named DarkPulsar, which is used to manage plug-ins for controlled devices and is used to control the plugin named "sipauth42.tsp" remote control backdoor.
It supports the following commands:
BurnRawShellcodeEDFStagedUploadDisableSecurityEnableSecurityUpgradeImplantPingPong
Burn, RawShellcode, UpgradeImplant and PingPong support removing/upgrading implanted software, running arbitrary code and checking whether a backdoor has been installed on the remote machine, among other commands The purpose is not yet clear.
Kaspersky Lab’s analysis of DarkPulsar discovered several constants used to encrypt traffic between the C&C and the implant:
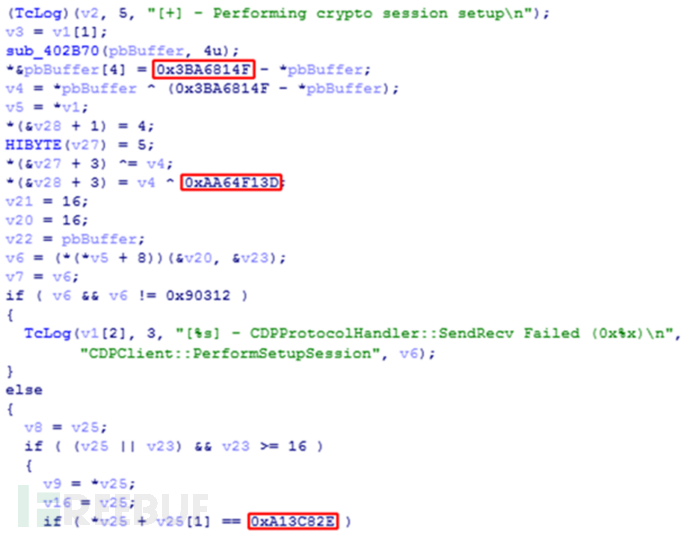
Kaspersky Lab Key thought these constants could serve as a starting point for further investigation, so he built a detector. A few months later, the mysterious DarkPulsar backdoor surfaced, containing both 32-bit and 64-bit versions. Researchers found about 50 cases, located in Russia, Iran and Egypt, commonly infected Windows 2003/2008 servers, involving nuclear energy, telecommunications, IT,Aerospace and R&D and other fields.
DarkPulsar is implanted with a dynamic library file. Judging from the functions exported by its workload, it can achieve the following functions:
Two anonymous functions are used to install backdoors in the system.
Function whose name is related to TSPI (Telephone Service Provider Interface) operation, used to ensure that the backdoor is present in the autorun list and starts automatically.
Functions whose names are related to SSPI (Security Support Provider Interface) operations are mainly used to run malicious code.
The implementation of SSPI and TSPI interfaces is very simple, so that the function exported by DarkPulsar has the same name as the interface function, but the correct phone service is replaced by malicious code.
This dynamic library is installed in the system through an anonymous function, calling Secur32.AddSecurityPackage with administrator privileges and the path to its own library in the parameters to start the backdoor, making lsass. exeLoads DarkPulsar as SSP/AP and calls its exported functionSpLsaModeInitialize to initialize the backdoor by DarkPulsar. Among them, AddSecurityPackage is used to inject code into lsass.exe. It also adds its library filename in HKLM\Software\Microsoft\Windows\CurrentVersion\Telephony\Providers.
As a result, the Telephony API (TapiSrv) starts to load and the Remote Access Connection Manager (RasMan) service starts to load. Set the startup type to "Automatic". When loading the telephony provider's library, TapiSrv calls TSPI_lineNegotiateTSPIVersion, which contains an AddSecurityPackage call to inject malicious code into lsass.exe.
DarkPulsar implements malicious functionality by installing a hook for SpAcceptLsaModeContext (the function responsible for authentication). Such injection behavior occurs within multiple system authentication packets in process lsass.exe and allows Darkpulsar to control the authentication process according to the following protocol:
1, Msv1_0 .dll - for NTLM protocol,
2, Kerberos.dll - for Kerberos protocol,
3, Schannel.dll - for TLS/SSL protocol,
4. Wdigest.dll - used for digest agreement,
5. Lsasrv.dll - used for negotiation agreement.
After completing this process, Darkpulsar is able to inject malware traffic into system protocols. Since this type of network activity is carried out according to system standards, it is only reflected in system processes, which means that it uses system ports reserved for the above protocols without hindering their normal operation.
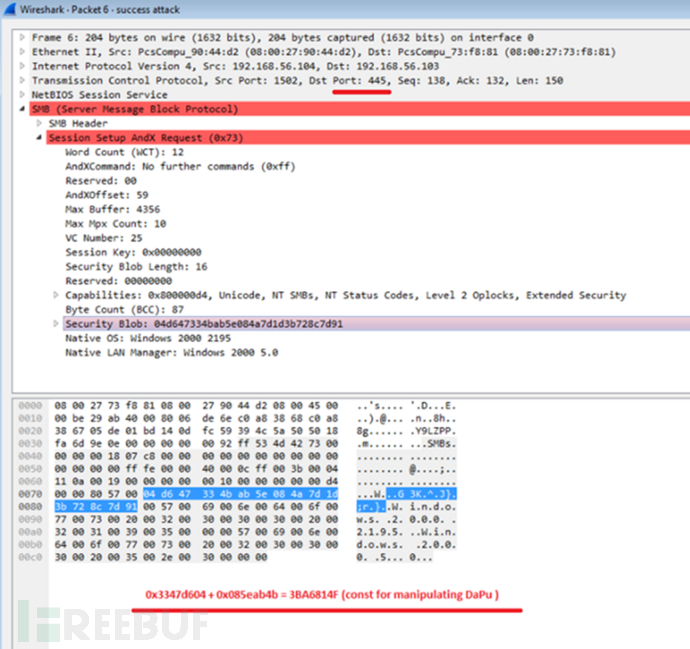
Network traffic successfully connected to the DarkPulsar implant
The second advantage of controlling the authentication process is that entering username and password protection can be bypassed to obtain access to Access to objects that require authentication, such as process lists, remote registries, SMB file systems. After sending Darkpulsar's DisableSecurity command, the controlled device's backdoor hook will call the SpAcceptLsaModeContext function, making the credentials passed in the function valid, and the system will then provide access to the client's protected objects.
The management interface of Darkpulsar-1.1.0.exe is built based on the "one command and one startup" principle. The command to be executed must be specified in the configuration file Darkpulsar-1.1.0.9.xml, or specified as a command line parameter, at least specify:
Whether the target machine uses a 32-bit or 64-bit system;
Protocol (supports SMB, NBT, SSL, RDP protocols) to provide command and port number;
used to decrypt the session AES key Private RSA key.
The Fuzzbunch framework’s plug-in Darkpulsar-1.1.0 can coordinate different components and manage parameters. Here is an example of the DisableSecurity command in action in Fuzzbunch:
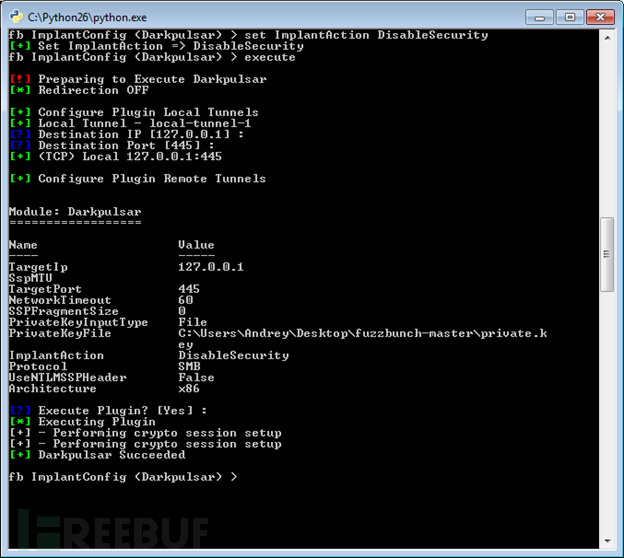
Here is an example of the process table after running DisableSecurity, allowing the execution of any plugin without valid credentials, and through the regular system Function (Remote Registry Service) to operate:
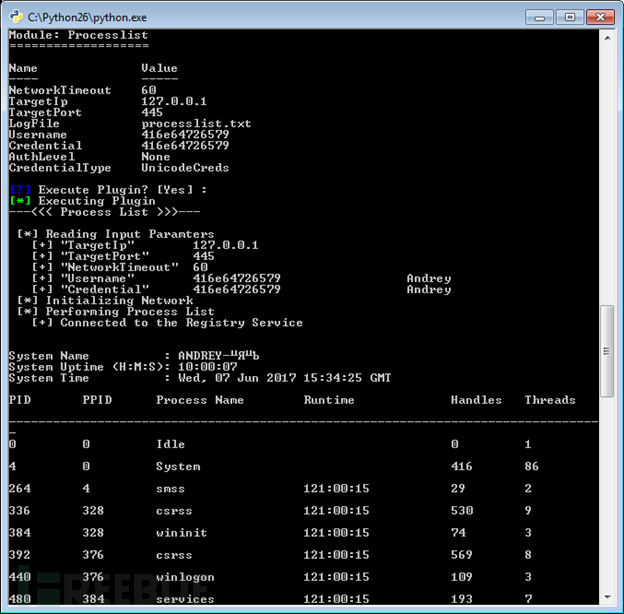
DanderSpritz is a framework for controlling infected machines, unlike FuZZbuNch, Because the latter provides part of the toolkit for later development stages with specific functionality, such as DisableSecurity and DarkSeuls’ EnableSecurity.
DanderSpritz lends itself to a wider range of backdoors, using PeedleCheap in a controlled device to launch the attacker's malware. DanderSpritz's plug-in PeddleCheap can be used to configure embedded software and connect to infected computers. Once connected, all DanderSpritz post-development features are available.
This is the channel through which DarkPulsar in EDFStagedUpload mode infects devices by implanting malware: PCDllLauncher (a plug-in for Fuzzbunch) deploys PeddleCheap implant software on the side of the controlled device, and DanderSpritz provides a user-friendly development interface. Therefore, the full name of PCDllLauncher is 'PeddleCheap DLL Launcher'.
Integrating the DanderSpritz solution, PeddleCheap plug-in, DarkPulsar plug-in and PCDllLauncher to achieve malicious functions includes four steps:
Through FuZZbuNch, run the command EDFStagedUpload to start DarkPulsar.
In DanderSpritz, run the command pc_prep (PeedelCheap Preparation) to prepare the malicious code and library files to be launched.
In DanderSpritz, run the command pc_old (this is the default alias of the command pc_listen -reuse -nolisten -key), which will set it to wait for the socket from the Pcdlllauncher.
Launch Pcdlllauncher via FuZZbuNch and specify a valid path prepared using the command pc_prep in the ImplantFilename parameter.
DanderSpritz
lsass.exe:
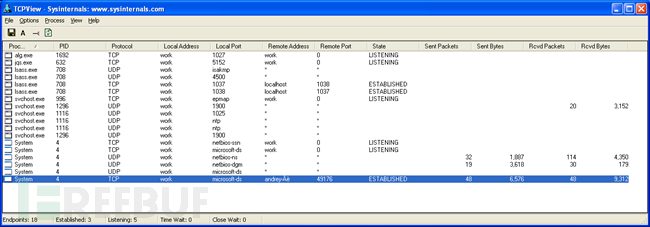
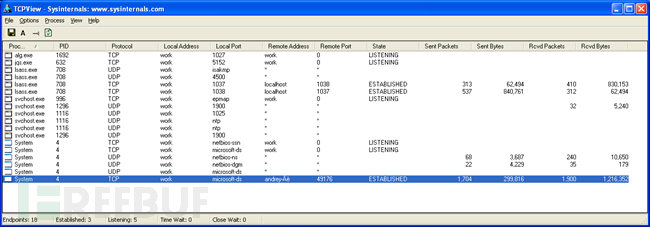
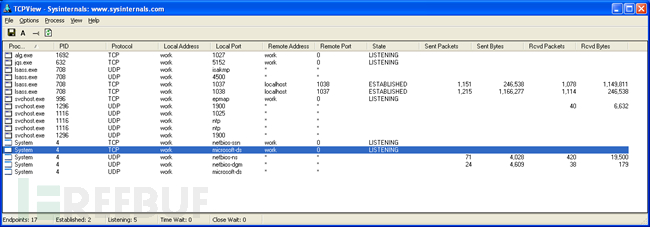
When the connection to the infected computer is terminated, network activity stops and only the two bound sockets in lsass.exe remain:
Implantation-96f10cfa6ba24c9ecd08aa6d37993fe4
File path-%SystemRoot%\System32\sipauth42.tsp
Registry-HKLM\Software\Microsoft\Windows\CurrentVersion\ Telephony\Providers
The above is the detailed content of How to use NSA's new APT framework DarkPulsar. For more information, please follow other related articles on the PHP Chinese website!
 Usage of UpdatePanel
Usage of UpdatePanel
 How do I set up WeChat to require my consent when people add me to a group?
How do I set up WeChat to require my consent when people add me to a group?
 How to use spyder
How to use spyder
 What is the difference between css framework and component library
What is the difference between css framework and component library
 Configure HOSTS file
Configure HOSTS file
 What are the methods of remote computer maintenance?
What are the methods of remote computer maintenance?
 What are the common testing techniques?
What are the common testing techniques?
 Usage of drawstring
Usage of drawstring
 How is the performance of thinkphp?
How is the performance of thinkphp?




