
When the Internet era came, people once lamented that everything was being digitized. Today, everything is mobile. In the streets and alleys, people were busy swiping their screens with their heads down. Data from foreign authoritative organizations show that Chinese smartphones have accounted for 96% of total mobile phone sales, and traditional feature phones have basically faded out of the stage of history. According to a recent report by eMarketer, an American market research company, data from Gartner, an authoritative market research organization, shows that in China, smartphones account for 96% of mobile phone sales, while the United States also accounts for 96%. In other words, at the hardware level of mobile Internet, China and the United States are already on the same level.
The popularity of smart phones has promoted the rapid development of mobile apps. Currently, mobile apps can range from communication and chatting, takeout booking, ticket booking, travel booking, shopping, news browsing, etc. to banking investment and financial management. , hospital registration, payment transactions, etc. A person's daily activities can basically be completed by relying on mobile phones. Because of the massive popularity of apps, many software developers have seen the benefits brought by this market. Driven by profits, various apps emerge one after another, and the app market is also a mixed bag. Since the security of instant apps cannot be fully guaranteed, personal information leakage incidents have occurred very frequently through apps in recent years.
Through big data analysis, a statistical table of the commonly used apps on mobile phones is as follows:
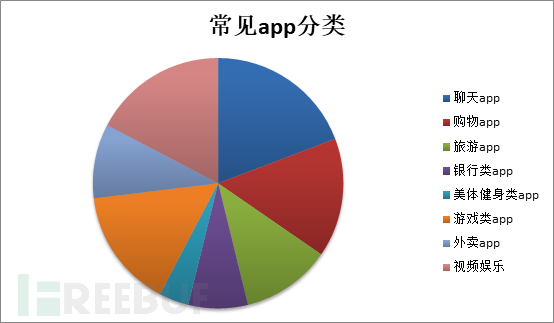
It is not difficult to see from the chart statistics that almost every Mobile phones are equipped with chat, video entertainment, shopping and other related apps. So how do these apps work on mobile phones? What information will be obtained from the mobile phone unknowingly?
With the development of technology, the functions of mobile phones are far more than these. The era of big data has arrived, and the era of smart home Internet of Things has also followed. , here we use Android app or apk for analysis. Download any apk and modify its suffix to tar to view some apk related files
Service service is a background service. When using service service, it needs to be declared in AndroidManifest.xml. The apk for this test is declared as follows in AndroidManifest.xml,
Service is independent of the activity component and performs some operations in the background. For example, when you need to obtain data from the server regularly, you need to use service at this time.
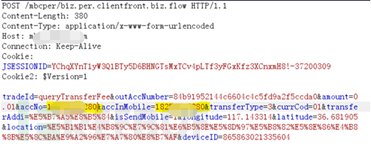
In addition to the security vulnerabilities in the four major components, various web vulnerabilities will also appear when calling the web interface, such as sql injection vulnerabilities, xss vulnerabilities, override, unauthorized and other related vulnerabilities. The screenshot is from an app http request data packet, and through testing it was found that the post data packet contains a vulnerability of unauthorized access. You can use a certain parameter to view other people's account information without authorization.
In short, there are many places where app vulnerabilities may appear, and there are many places worthy of our attention, such as whether the data is encrypted during transmission and whether the data is stored locally. Whether it is encrypted, whether it is safe to start the activity component by intent, etc.
With so many apps, as ordinary users, it is still impossible for users to perform security checks on the apps. So how should we prevent personal information from being leaked due to the apps?
l First of all, it is recommended to download the app through regular channels to prevent the downloaded app from being modified and compiled and not the original application;
l If there are no special requirements, it is not recommended to root the phone;
When installing an application, please pay attention to its required open permissions and turn off unnecessary permissions, such as location information, reading mobile phone contacts, etc.
l can be installed on your phone Appropriate anti-virus software, regularly scan and clean up useless software, program packages, etc.;
l Regularly upgrade relevant apps to fix bugs in old versions.
The above is the detailed content of How to briefly discuss the security issues of APP. For more information, please follow other related articles on the PHP Chinese website!




