How to Conduct Authorized APK Penetration Testing
This article aims to provide some testing ideas for beginners who also lack penetration testing experience. The content involved may be relatively basic, cousins, please forgive me. After unpacking the APK and getting the apk, use 7-Zip to unzip it directly to get several folders, an AndroidManifest.xml file, and a dex file. Use dex2jar https://sourceforge.net/projects/dex2jar/ to decompress this dex file to generate a jar file, and then use jd-gui to view the java source code. While it is possible to look for code vulnerabilities by looking at the source code, obfuscation often occurs and will not be discussed in depth here. The xml file mentioned above must not be distributed before. It involves many important configuration items, such as: - android:debuggable is true in the AndroidManifest.xml file. The app can be debugged arbitrarily - android: allowBackup is true in the AndroidManifest.xml file. App data can be backed up and exported. - Wait... There is another point that may be used during the actual test: after decompressing the apk, you can try to search the db file in powershell. There may be sensitive information (why do you say this, because I encountered it once ...)
for /r F:\source-code %i in (*.db) do echo %i
apk security analysis and detection:
Experiment: apk security analysis and detection (Hetian Network Security Laboratory)
Conduct experiments to learn how to run apk security analysis Detection program, and use this to perform security analysis and detection on the apk, and the results reveal potential threats. )
The simplest case of enumerating user names is that when entering a user name and logging in, the system will respond that the user name does not exist. What I encountered this time was that logging in does not require a password, but you need to enter a registered username. Then a verification code will be sent to the corresponding mobile phone based on the username. At the same time, it is set that it cannot be resent within 120s, and the verification code is valid for 120s. At this time, it seems that we can't do anything through the verification code, but during the actual test process, we found that 1. When we enter the existing account, it prompts that the sending is successful; 2. If we send it repeatedly, we will respond that it cannot be sent again within 120s; 3. Enter If there is no user, it will prompt that the sending failed. Even if a time limit is set, username enumeration can still verify whether the username exists through blasting, just based on the information returned by the server.
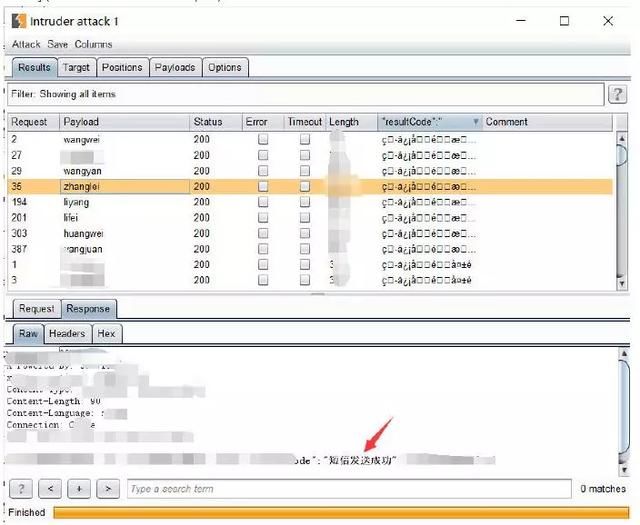
Wait, since we don’t know the mobile phone number and we are not allowed to enter the password to log in, even if we get the username to generate the social engineering dictionary, it will not be used. Then we get the user What's the use of a name? Of course it is useful, but it depends on the specific scenario. For example, in the following case, any verification code can be bypassed. When we log in, the server sends a SMS verification code to the mobile phone number bound to the account. We enter an account number obtained in the previous step and enter the verification code casually. Click to capture the packet after logging in. The login fails and there are two code fields in the response
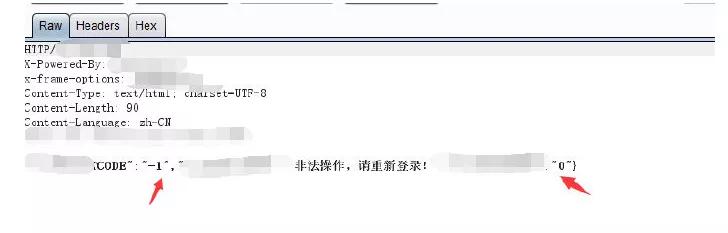
Try changing it:

It works!
Verification code bypass vulnerability:
Experiment: Verification code bypass vulnerability
(Master the common verification code bypass vulnerability principles, and bypass Method exploitation and vulnerability protection)
After successfully logging in to the function page, click on each function. On the personal information page, there is a function to query the number of people online in real time. That column only displays the number of people, and there is no arrow next to it
I once thought I couldn't click there (in fact, because the amount of data was too large, it took a long time to load, so I just clicked back, which gave me the feeling that there was nothing here) , after entering, you can see the information of all logged in people.

After I tried different users, I found that the user information here does not have permission restrictions, which means it is visible to everyone, and the permissions are obviously improperly configured. The application also has several query functions. The BURP tool shows that the format of the returned data packets is JSON
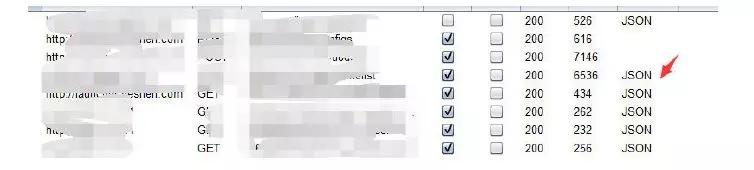
. Try injecting JSON and trying XXE. Trying everywhere does not help. Because I don't have much experience. There is another parameter in front, try it?

There is drama!
Try xss
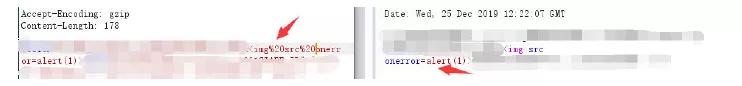
Put it in the browser and the pop-up window will be successful!
The above is the detailed content of How to Conduct Authorized APK Penetration Testing. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to Conduct Authorized APK Penetration Testing
May 20, 2023 pm 12:29 PM
How to Conduct Authorized APK Penetration Testing
May 20, 2023 pm 12:29 PM
As a penetration testing novice, the purpose of this article is to provide some testing ideas for those novices like me. The content involved may be relatively basic, cousins, please forgive me. After unpacking the APK and getting the apk, use 7-Zip to unzip it directly to get several folders, an AndroidManifest.xml file, and a dex file. Use dex2jar https://sourceforge.net/projects/dex2jar/ to decompress this dex file to generate a jar file, and then use jd-gui to view the java source code. Of course, you can find loopholes in the code from the source code, but there is usually confusion, so we won’t discuss it in depth here.
 Google app beta APK teardown reveals new extensions coming to Gemini AI assistant
Jul 30, 2024 pm 01:06 PM
Google app beta APK teardown reveals new extensions coming to Gemini AI assistant
Jul 30, 2024 pm 01:06 PM
Google's AI assistant, Gemini, is set to become even more capable, if the APK teardown of the latest update (v15.29.34.29 beta) is to be considered. The tech behemoth's new AI assistant could reportedly get several new extensions. These extensions wi
 How to open APK files on Windows 11
Apr 14, 2023 am 11:19 AM
How to open APK files on Windows 11
Apr 14, 2023 am 11:19 AM
Have you ever downloaded a file ending with the letters APK? This usually happens with apps that work on your phone and are loaded onto your computer. Most of these files end with the letters APK. You may have been trying to open these files but can't figure out where they are stored or how to open them due to their unusual extensions. If you're looking for a way to open such files on Windows 11 and have Googled your hair out, don't worry! It's actually much easier than that. In fact, it's free to do so and you don't even need to install anything. Well, you'll have to download an APK file opener for your operating system - but only if you haven't already
 How to rename apk software
Dec 08, 2023 am 10:23 AM
How to rename apk software
Dec 08, 2023 am 10:23 AM
Change steps: 1. Make sure that the APK file whose name you want to change has been saved to your computer; 2. Right-click the APK file and select the "Rename" option; 3. Replace the original file name with the new name you want. Make sure to only change the file name part and not the file extension ".apk"; 4. Press the Enter key or click the "Rename" button in the window to save the changes.
 How to grab apk network package in frida
May 16, 2023 pm 07:16 PM
How to grab apk network package in frida
May 16, 2023 pm 07:16 PM
1. Analyze the pitfalls and find hook points from a system perspective instead of capturing packets just for the sake of capturing them. 1.okhttp calling process publicstaticfinalMediaTypeJSON=MediaType.get("application/json;charset=utf-8");OkHttpClientclient=newOkHttpClient();Stringpost(Stringurl,Stringjson)throwsIOException{RequestBodybody=RequestBody
 How to encrypt Android apk released by unity
May 13, 2023 am 11:10 AM
How to encrypt Android apk released by unity
May 13, 2023 am 11:10 AM
Security Issues of the Unity3D Program Code Security Issues The core assembly file Assembly-CSharp.dll of the Unity3D program is a standard .NET file format and comes with rich metadata information such as method names, class names, type definitions, etc. You can use tools such as DnSpy to It can be easily decompiled and tampered with, and the code logic, class names, method names, etc. can be seen at a glance. Once the code logic is decompiled, it is easy to breed various types of plug-ins and destroy the balance of the game. If there are loopholes in the code logic, it is easy to be discovered and exploited, which may cause unpredictable losses to developers. Resource security issues: During the compilation and packaging phase, the Unity3D program will package resources into AssetBun through the Unity editor.
 Win11 apk installation guide
Jan 03, 2024 pm 10:24 PM
Win11 apk installation guide
Jan 03, 2024 pm 10:24 PM
As we all know, Microsoft announced that win11 will be able to run Android applications and install local apk. However, after updating win11, users found that they did not know how to install the local apk. In fact, this is because Microsoft has not yet implemented this feature for win11. It is necessary Wait for the function to be installed before you can use it. How to install local apk in win11: 1. According to Microsoft, after win11 has installed this function, you can directly double-click the downloaded apk file to install it directly. 2. After the installation is completed, users can also run it directly in the system. 3. Although it is now the official version of win11, Microsoft has not yet implemented this feature for win11. 4. So if the user wants to use win11
 How to perform APK simple code injection
May 14, 2023 am 11:43 AM
How to perform APK simple code injection
May 14, 2023 am 11:43 AM
1. Foreword When the apk is not encrypted, the smail file is obtained by decompiling it. Just inject the code that needs to be injected. Then seal and sign it! 2. Make apk Use androidstudio to generate a simple apk. Just use the default code. packagecom.example.myapplication1;importandroidx.appcompat.app.AppCompatActivity;importandroid.os.Bundle;publicclassMainActivityextendsAppCompatActivity{






