What is the method of reverse engineering in Android?
1. Weapon get
Xiaobai, if you want to use this weapon, you must first open the meridians.
1.1 Meridians (Environment)
1.Root, mobile phone root, there is no Android without root. Only by opening up the root meridian can we proceed with subsequent operations.
2. Xposed framework installation. If you want to use Xposed as a weapon, you must first be able to pick it up before you can use it.
1.2 Weapons
xposedBridgeApi-82.jar.jar.
This is our weapon, Xiaobai, come on, I will show you the basic use of this weapon.
2. Weapon Demonstration
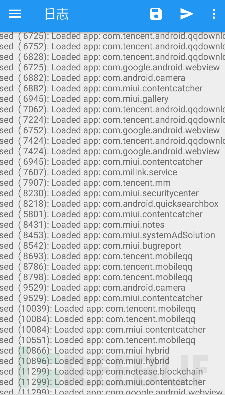
We use Xposed weapons to intercept packageName and then output it.
In fact, this weapon can only display its maximum capability when paired with internal strength.
Matching internal strength, master, how to do this.
Don’t be anxious, let’s take it step by step.
0x02 Practice using Hook’s first level of internal strength (Android Studio 3.0 Xposed)
Xiaobai, let me first teach you the operating acupoints of the first level of internal strength. Listen well.
Android Studio 3.0 Basic Configuration
Let’s first provide an environment for content running.
(1) First build a project that does not require Activity
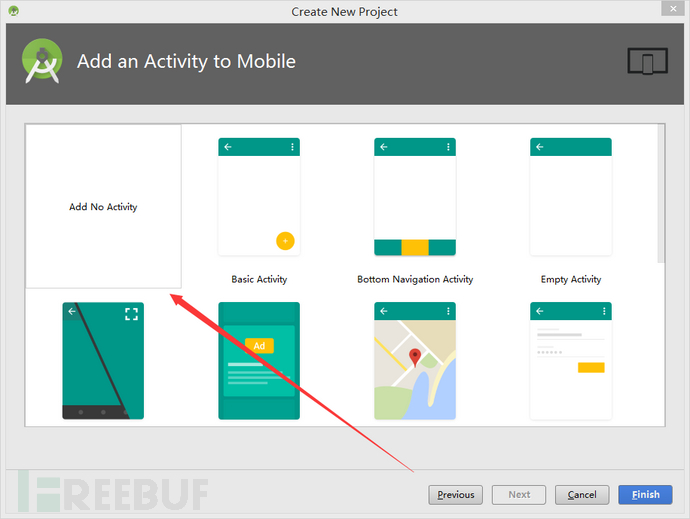
(2) Then import the jar package. And right click add as Library.
(3) Fill in the Androidmanifest.xml file.
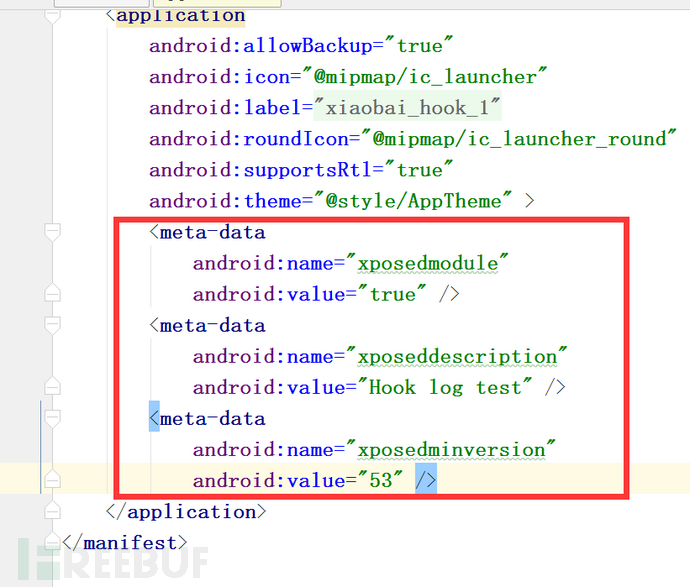
<meta-data></meta-data> <meta-data></meta-data> <meta-data></meta-data>
(4) Modify the dependency method
The jar package content already exists in Xposed, and it will conflict if it is packaged again.
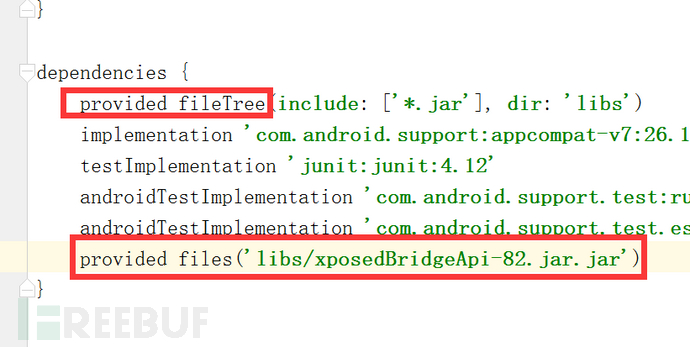
(5) Basic Xposed model creation
Use alt enter to implement a method.
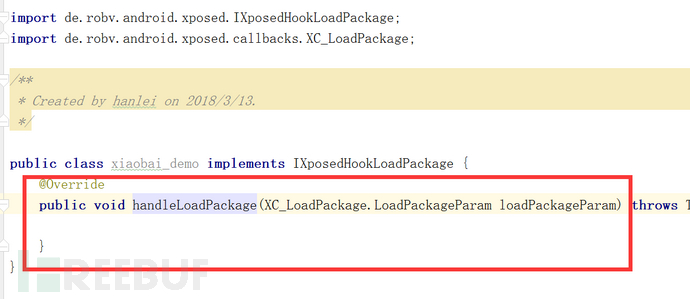
#Xiaobai, listen to my verbose words.
handleLoadPackage, this method is used to perform user operations when loading the application package.
LoadPackageParam loadPackageParam:, this parameter contains some basic information about the loaded application.
Internal strength realization
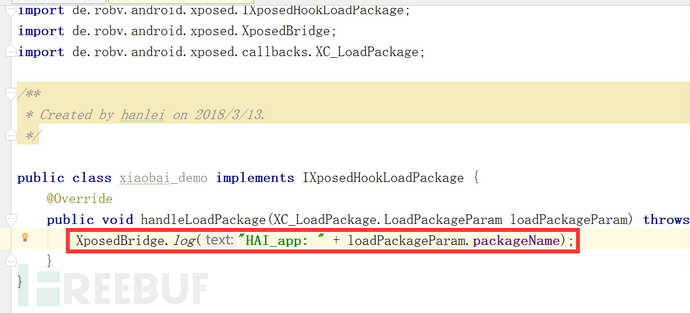
It can be achieved in one sentence.
XposedBridge.log("HAI_app: " loadPackageParam.packageName);
Here we have to think about what XposedBridge.log is.
The print of posedBridge.log will be output to the logging feature of the xposed framework's startup program.. This will also make it easier for us to view.
Let’s do the last step of configuration. Set the starting place.
Create a new file in the new assets directory. The file name is xposed_init.
Write the package name class.
Test results
Build APK
Install for testing.
Just install it on your phone and then restart it.
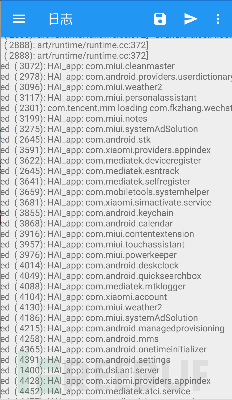
Thinking
The so-called master leads you in, and practice depends on the individual. so.
I understand, Master, can we filter through this simple method? For example, write a simple analysis system. Or something else, we can also filter this. I'll try it myself first.
Xiaobai’s self-cultivation
Through this running path, registrations are analyzed and filtered.
Give it a simple try.
Use the substring of the java string learned yesterday to filter the string.
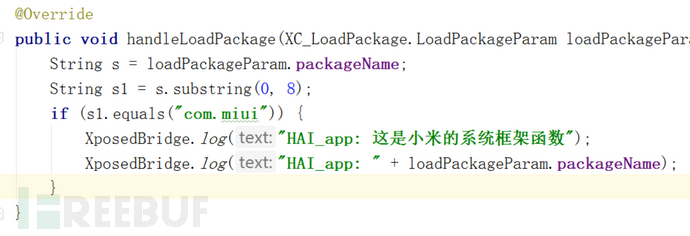
Then test.
Of course, this can also be explained in more detail.
0x03 Wooden pile actual combat practice
Xiaobai, come on, the master has found a wooden pile for you, I will punch it for you. How does this hook work and how to fight it. Learn well.
I know the master.
Collecting stake information
1. Basic information
Xiaobai, let’s use a weapon we used before to collect this basic information.
Master, what kind of information do we usually collect?
Well, we generally need to collect
1. The package name of the wooden pile
2. The simple logic of the wooden pile
....
小Bai, just collect this yourself.
Xiaobai’s operation
The first is the package name. Use weapons, apkhelper.
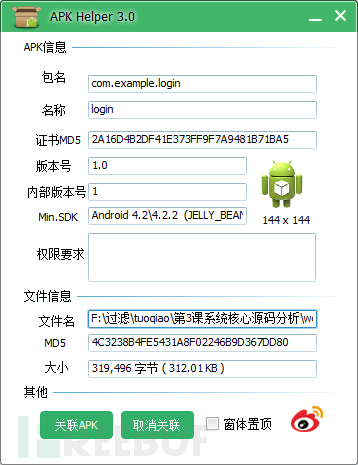
Get the package name information. com.example.login
Then simple logic phone.
2.反编译信息收集
小白啊,收集玩了吗?
收集完了师傅。
好,我们接下来收集反编译信息。知己知彼,方能百战不殆。
师傅的操作
首先我们来看看我们要收集的东西。
1.关键的类名。
2.关键的函数位置。
来用Android Killer武器反编译木桩。
定位。
查看类名,进行记录。
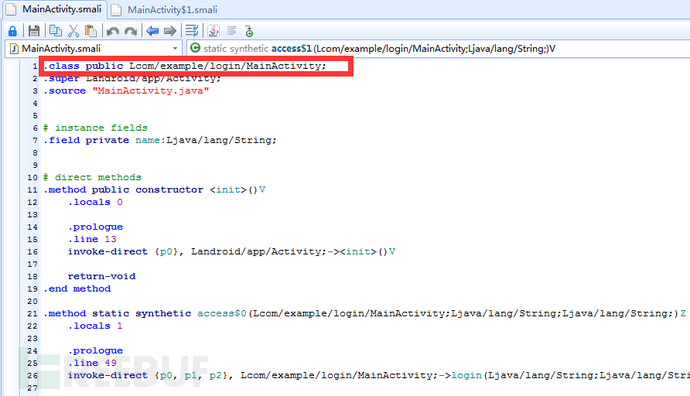
小白,看清楚,是这个样子进行记录。
原来是这样。com/example/login/MainActivity;
但是我们要改成这样的。com.example.login.MainActivity
现在就需要定位到关键函数了。
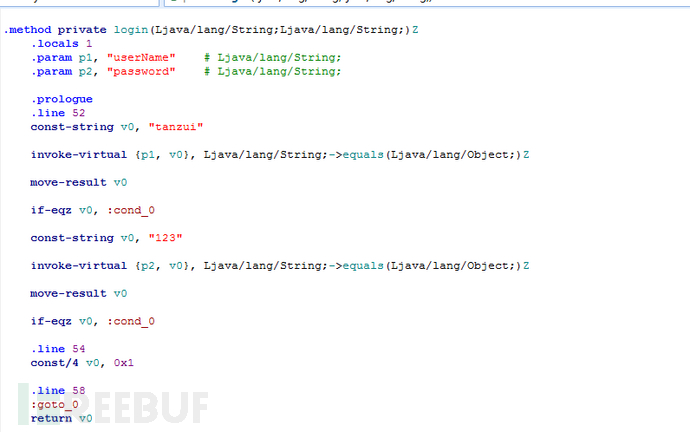
这个login就是我们要Hook住的函数啦。
Ljava/lang/String;Ljava/lang/String;从这里我们可以看到是两个输入内容。并且类型是String。我们现在要做的就是要hook住这个输出,然后对其进行输出。
木桩实战练习
环境搭建
好了,小白,前期资料收集的差不多了。我现在要发功了,要看清楚我的使用哦。
先把环境调整好。
然后先做一个简单的过滤。
这个时候,收集的包名就排上用场了。
因为是hook的是方法,所以我们这里使用一个方法。
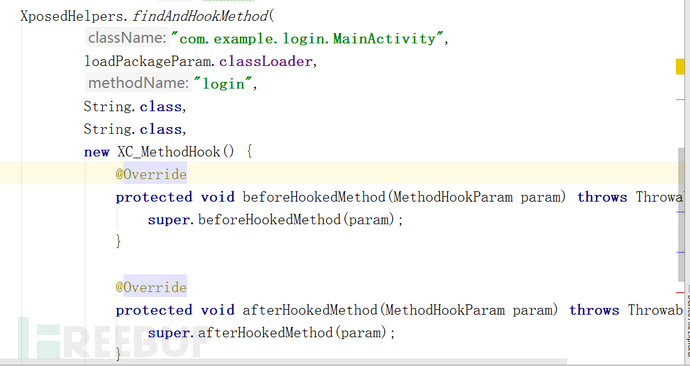
第一个参数,要hook的包名+方法名,这个也是我们收集好的。
第二个参数不动
第三个参数方法名
第四个参数 输入的参数
我们有两个String类型的参数,所以才这样写
最后一个参数,就是做一个监听。可以监听这个方法的使用前和使用后。
f for木桩
小白,一切准备你就须,看为师给你f这个木桩。
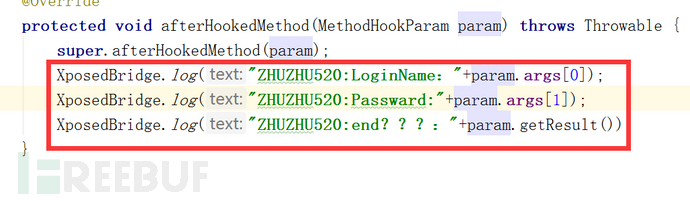
小白,你看这第一招
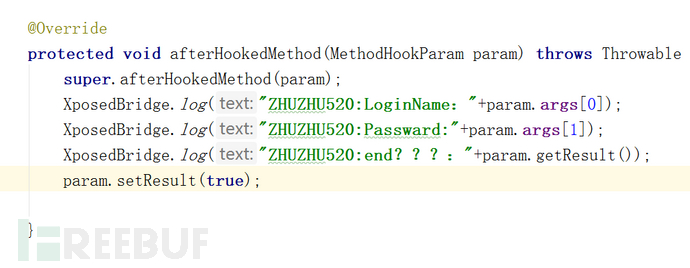
XposedBridge.log("ZHUZHU520:LoginName:"+param.args[0]);这一招搞它的第一个输入。
然后再来看这一招
XposedBridge.log("ZHUZHU520:Passward:"+param.args[1]);这一招搞它的第二个输入。
然后最后一招。
XposedBridge.log("ZHUZHU520:end???:"+param.getResult());这一招就是拦截返回值。
小白啊,这里有一个需要思考的内容。
这样hook的意义或者作用是什么?
小白的思考
师傅,我觉得首先,这样可以拦截下输入的参数,还有返回的值。如果在hook里做一个转发信息的技能。那不就可以成功的对登录账户的人进行账号和密码的获取。
这不就是和钓鱼一样了嘛。
我觉得这是一个很大的漏洞,如果登录厂商没有做相应的处理,那这里我可以拿这个搞死他。
好了,小白,你说的很对,我们现在来对这个进行下测试吧。
f 木桩测试
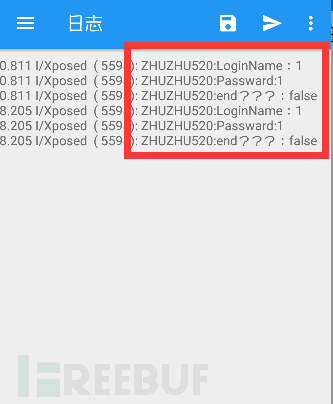
小白啊,你看这里我们就成功的拦截内容了。小白分配给你一个任务,使用hook f来拦截木桩,并确保不管我是否输入正确,木桩能够成功登录。
0x04 木桩f进阶(小白的自我进步)
XposedBridge.log("ZHUZHU520:end???:"+param.getResult());思考一
师傅之前使用了一个param.getResult()获取了返回值,那我是不是可以使用相同的set方法,重新对这个进行赋值啊。
根据各种方式,我们知道了这里的返回值就是Z,也就是布尔型。
说干就干,争取f掉木桩。
The above is the detailed content of What is the method of reverse engineering in Android?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 New report delivers damning assessment of rumoured Samsung Galaxy S25, Galaxy S25 Plus and Galaxy S25 Ultra camera upgrades
Sep 12, 2024 pm 12:23 PM
New report delivers damning assessment of rumoured Samsung Galaxy S25, Galaxy S25 Plus and Galaxy S25 Ultra camera upgrades
Sep 12, 2024 pm 12:23 PM
In recent days, Ice Universe has been steadily revealing details about the Galaxy S25 Ultra, which is widely believed to be Samsung's next flagship smartphone. Among other things, the leaker claimed that Samsung only plans to bring one camera upgrade
 Samsung Galaxy S25 Ultra leaks in first render images with rumoured design changes revealed
Sep 11, 2024 am 06:37 AM
Samsung Galaxy S25 Ultra leaks in first render images with rumoured design changes revealed
Sep 11, 2024 am 06:37 AM
OnLeaks has now partnered with Android Headlines to provide a first look at the Galaxy S25 Ultra, a few days after a failed attempt to generate upwards of $4,000 from his X (formerly Twitter) followers. For context, the render images embedded below h
 IFA 2024 | TCL\'s NXTPAPER 14 won\'t match the Galaxy Tab S10 Ultra in performance, but it nearly matches it in size
Sep 07, 2024 am 06:35 AM
IFA 2024 | TCL\'s NXTPAPER 14 won\'t match the Galaxy Tab S10 Ultra in performance, but it nearly matches it in size
Sep 07, 2024 am 06:35 AM
Alongside announcing two new smartphones, TCL has also announced a new Android tablet called the NXTPAPER 14, and its massive screen size is one of its selling points. The NXTPAPER 14 features version 3.0 of TCL's signature brand of matte LCD panels
 Samsung Galaxy S24 FE billed to launch for less than expected in four colours and two memory options
Sep 12, 2024 pm 09:21 PM
Samsung Galaxy S24 FE billed to launch for less than expected in four colours and two memory options
Sep 12, 2024 pm 09:21 PM
Samsung has not offered any hints yet about when it will update its Fan Edition (FE) smartphone series. As it stands, the Galaxy S23 FE remains the company's most recent edition, having been presented at the start of October 2023. However, plenty of
 Vivo Y300 Pro packs 6,500 mAh battery in a slim 7.69 mm body
Sep 07, 2024 am 06:39 AM
Vivo Y300 Pro packs 6,500 mAh battery in a slim 7.69 mm body
Sep 07, 2024 am 06:39 AM
The Vivo Y300 Pro just got fully revealed, and it's one of the slimmest mid-range Android phones with a large battery. To be exact, the smartphone is only 7.69 mm thick but features a 6,500 mAh battery. This is the same capacity as the recently launc
 New report delivers damning assessment of rumoured Samsung Galaxy S25, Galaxy S25 Plus and Galaxy S25 Ultra camera upgrades
Sep 12, 2024 pm 12:22 PM
New report delivers damning assessment of rumoured Samsung Galaxy S25, Galaxy S25 Plus and Galaxy S25 Ultra camera upgrades
Sep 12, 2024 pm 12:22 PM
In recent days, Ice Universe has been steadily revealing details about the Galaxy S25 Ultra, which is widely believed to be Samsung's next flagship smartphone. Among other things, the leaker claimed that Samsung only plans to bring one camera upgrade
 Xiaomi Redmi Note 14 Pro Plus arrives as first Qualcomm Snapdragon 7s Gen 3 smartphone with Light Hunter 800 camera
Sep 27, 2024 am 06:23 AM
Xiaomi Redmi Note 14 Pro Plus arrives as first Qualcomm Snapdragon 7s Gen 3 smartphone with Light Hunter 800 camera
Sep 27, 2024 am 06:23 AM
The Redmi Note 14 Pro Plus is now official as a direct successor to last year'sRedmi Note 13 Pro Plus(curr. $375 on Amazon). As expected, the Redmi Note 14 Pro Plus heads up the Redmi Note 14 series alongside theRedmi Note 14and Redmi Note 14 Pro. Li
 iQOO Z9 Turbo Plus: Reservations begin for the potentially beefed-up series flagship
Sep 10, 2024 am 06:45 AM
iQOO Z9 Turbo Plus: Reservations begin for the potentially beefed-up series flagship
Sep 10, 2024 am 06:45 AM
OnePlus'sister brand iQOO has a 2023-4 product cycle that might be nearlyover; nevertheless, the brand has declared that it is not done with itsZ9series just yet. Its final, and possibly highest-end,Turbo+variant has just beenannouncedas predicted. T




