Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 How to understand Wireshark filtering rules and filtering options
How to understand Wireshark filtering rules and filtering options
How to understand Wireshark filtering rules and filtering options
ip.addr == 192.168.6.1
Filter out the packets containing 192.168.6.1
ip.src == 192.168.43.137
Filter out the source IP address Packets with the target IP address of 192.168.43.137
ip.dst == 192.168.43.137
Filter out the packets with the destination IP address of 192.168.43.137
tcp.port == 80
Filter out the 80 port number containing tcp
tcp.src == 80
Filter out the 80 port number of the source tcp
tcp .dstport == 80
Filter out the 80 port number of the target tcp
eth.addr == 68:17:29:2f:c4:2f
Filter out the included mac Address
eth.src == 68:17:29:2f:c4:2f
Filter out the source mac address
eth.dst == 68:17 :29:2f:c4:2f
Filter out the target mac address
arp
Filter out the arp protocol
and and
or or
not non
( ) brackets
tcp or http and (not http)
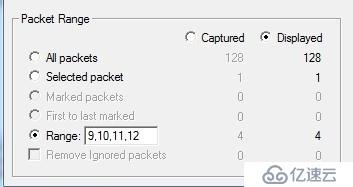
Save only the specified message
Save only Four messages 9, 10, 11, 12
The above is the detailed content of How to understand Wireshark filtering rules and filtering options. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1385
1385
 52
52