How to parse Apache vulnerability recurrence
apacheParsing vulnerability
Vulnerability principle
Parse the file suffix name from right to left. If If you find an unrecognized file suffix, continue to the left. For example, test.php.owf.rar ".owf" and ".rar" are two suffixes that apache cannot recognize and parse, and apache will parse wooyun.php.owf.rar into php.
Vulnerability form
www.xxxx.xxx.com/test.php.xxx
Other configuration issues lead to the vulnerability
(1) If there is such a line in Apache's conf to configure AddHandler php5-script .php, then as long as the file name contains .php, even if the file name is test2.php.jpg, it will be executed as php.
(2) If there is such a line configuration in Apache's conf AddType application/x-httpd-php .jpg, even if the extension is jpg, it can still be executed in php mode.
Experimental environment: Windows Server 2008 R2
Phpstudy2018
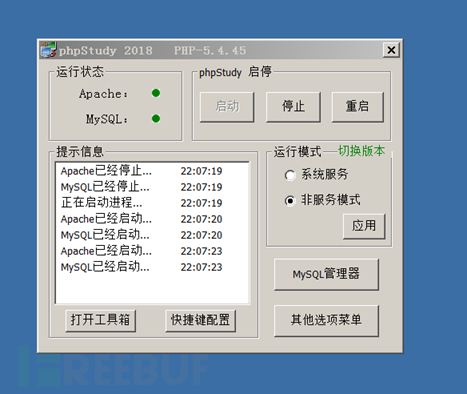
Add AddHandler php5-script .php in httpd.conf and restart after adding
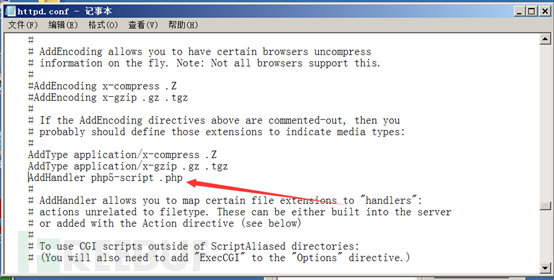
Create a php sentence in the root directory with the suffix .php.xxx
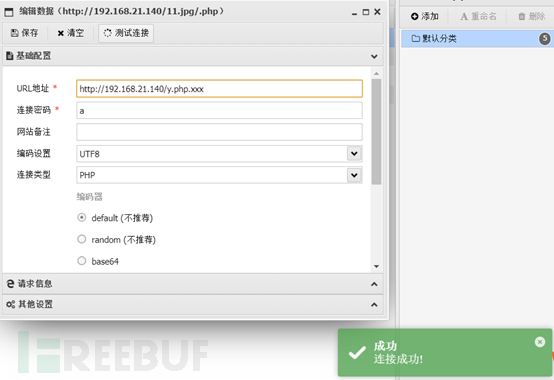
Access and see if it can be parsed
Parse successfully, Ant Sword connection
The above is the detailed content of How to parse Apache vulnerability recurrence. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 PHP Framework Performance Comparison: The Ultimate Showdown of Speed vs. Efficiency
Apr 30, 2024 pm 12:27 PM
PHP Framework Performance Comparison: The Ultimate Showdown of Speed vs. Efficiency
Apr 30, 2024 pm 12:27 PM
According to benchmarks, Laravel excels in page loading speed and database queries, while CodeIgniter excels in data processing. When choosing a PHP framework, you should consider application size, traffic patterns, and development team skills.
 Integration and expansion of golang function concurrency control and third-party libraries
Apr 25, 2024 am 09:27 AM
Integration and expansion of golang function concurrency control and third-party libraries
Apr 25, 2024 am 09:27 AM
Concurrent programming is implemented in Go through Goroutine and concurrency control tools (such as WaitGroup, Mutex), and third-party libraries (such as sync.Pool, sync.semaphore, queue) can be used to extend its functions. These libraries optimize concurrent operations such as task management, resource access restrictions, and code efficiency improvements. An example of using the queue library to process tasks shows the application of third-party libraries in actual concurrency scenarios.
 How to conduct concurrency testing and debugging in Java concurrent programming?
May 09, 2024 am 09:33 AM
How to conduct concurrency testing and debugging in Java concurrent programming?
May 09, 2024 am 09:33 AM
Concurrency testing and debugging Concurrency testing and debugging in Java concurrent programming are crucial and the following techniques are available: Concurrency testing: Unit testing: Isolate and test a single concurrent task. Integration testing: testing the interaction between multiple concurrent tasks. Load testing: Evaluate an application's performance and scalability under heavy load. Concurrency Debugging: Breakpoints: Pause thread execution and inspect variables or execute code. Logging: Record thread events and status. Stack trace: Identify the source of the exception. Visualization tools: Monitor thread activity and resource usage.
 The evasive module protects your website from application layer DOS attacks
Apr 30, 2024 pm 05:34 PM
The evasive module protects your website from application layer DOS attacks
Apr 30, 2024 pm 05:34 PM
There are a variety of attack methods that can take a website offline, and the more complex methods involve technical knowledge of databases and programming. A simpler method is called a "DenialOfService" (DOS) attack. The name of this attack method comes from its intention: to cause normal service requests from ordinary customers or website visitors to be denied. Generally speaking, there are two forms of DOS attacks: the third and fourth layers of the OSI model, that is, the network layer attack. The seventh layer of the OSI model, that is, the application layer attack. The first type of DOS attack - the network layer, occurs when a large number of of junk traffic flows to the web server. When spam traffic exceeds the network's ability to handle it, the website goes down. The second type of DOS attack is at the application layer and uses combined
 How to add a server in eclipse
May 05, 2024 pm 07:27 PM
How to add a server in eclipse
May 05, 2024 pm 07:27 PM
To add a server to Eclipse, follow these steps: Create a server runtime environment Configure the server Create a server instance Select the server runtime environment Configure the server instance Start the server deployment project
 Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
1. Background of the Construction of 58 Portraits Platform First of all, I would like to share with you the background of the construction of the 58 Portrait Platform. 1. The traditional thinking of the traditional profiling platform is no longer enough. Building a user profiling platform relies on data warehouse modeling capabilities to integrate data from multiple business lines to build accurate user portraits; it also requires data mining to understand user behavior, interests and needs, and provide algorithms. side capabilities; finally, it also needs to have data platform capabilities to efficiently store, query and share user profile data and provide profile services. The main difference between a self-built business profiling platform and a middle-office profiling platform is that the self-built profiling platform serves a single business line and can be customized on demand; the mid-office platform serves multiple business lines, has complex modeling, and provides more general capabilities. 2.58 User portraits of the background of Zhongtai portrait construction
 How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
To successfully deploy and maintain a PHP website, you need to perform the following steps: Select a web server (such as Apache or Nginx) Install PHP Create a database and connect PHP Upload code to the server Set up domain name and DNS Monitoring website maintenance steps include updating PHP and web servers, and backing up the website , monitor error logs and update content.
 Java package management and integration of dependencies and version control
Apr 24, 2024 pm 09:48 PM
Java package management and integration of dependencies and version control
Apr 24, 2024 pm 09:48 PM
In Java, package management and version control integration are crucial, using Maven to manage dependencies and Git for version control. The integration steps include initializing the Git repository, creating the Maven function package information file, and adding it to the Git repository. In a practical case, add the CommonsLang dependency, use Maven to download it and add it to the Git repository to ensure that the team uses the same dependency version.






