How to understand LDAP injection
1. LDAP injection
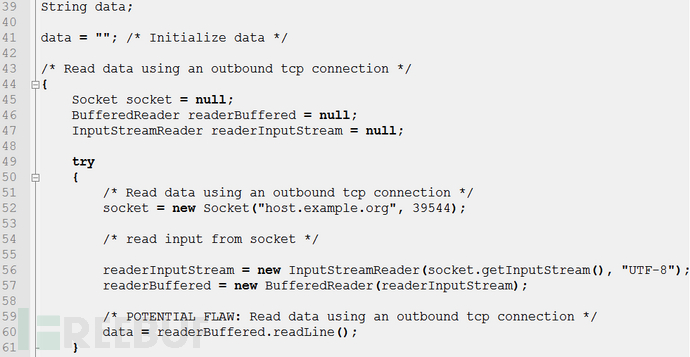
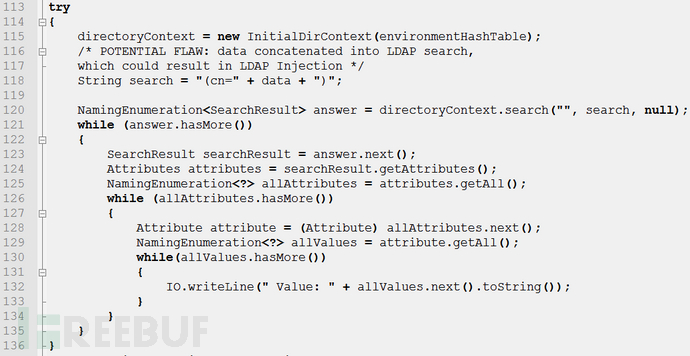
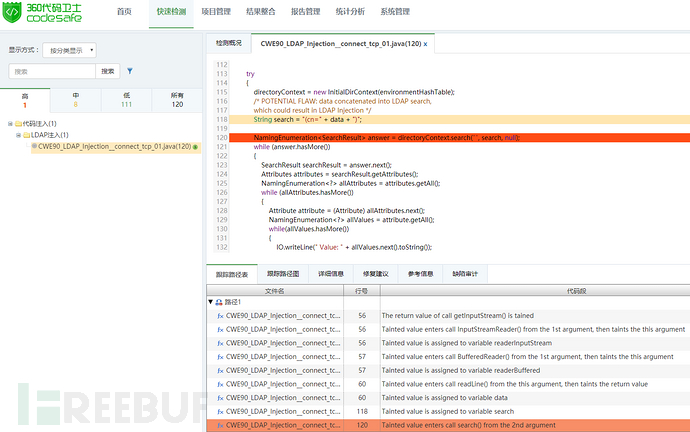
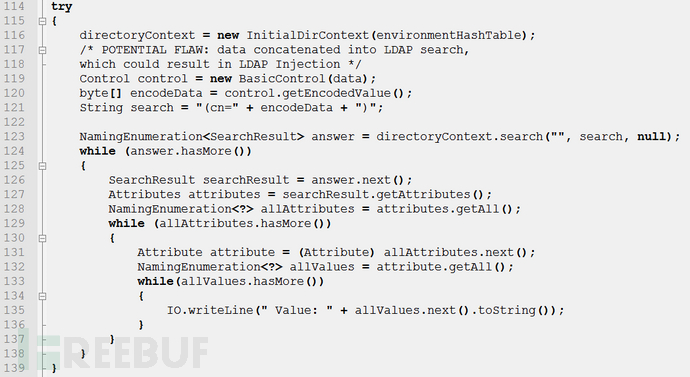
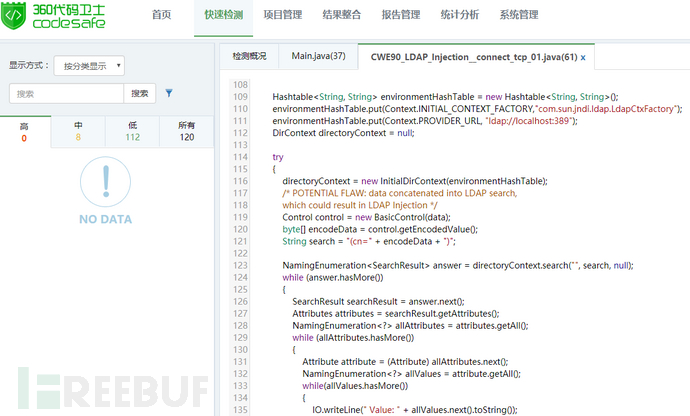
LDAP (Light Directory Access Portocol) is a lightweight directory access protocol based on the X.500 standard, providing services and protocols for accessing directory database methods. Commonly used to form directory services with directory databases. The directory is a professional distributed database optimized for query, browsing and search. It organizes data in a tree structure, similar to the file directory in Linux/Unix systems. It is suitable for storing data that does not change frequently, such as public certificates, security keys, and company physical device information, in the directory. Similar to SQL, LDAP is a search protocol with query syntax and the risk of potential injection attacks. LDAP injection refers to an attack method in which the input string when the client sends a query request contains some special characters, causing the original query structure of LDAP to be modified, thereby allowing access to more unauthorized data.
This article takes the JAVA language source code as an example to analyze the causes and repair methods of the LDAP injection vulnerability in the CWE ID 90: Improper Neutralization of Special Elementsused in an LDAP Query ('LDAP Injection') sample. For details, please see:
CWE ID 90: Improper Neutralization of Special Elements used in an LDAP Query ('LDAP Injection')
http://cwe .mitre.org/data/definitions/90.html
CWE ID 639: Authorization Bypass ThroughUser-Controlled Key
http://cwe.mitre.org/ data/definitions/639.html
2. Dangers of LDAP injection
LDAP injection is introduced by using users Parameters generate malicious LDAP queries to bypass access control and user privilege escalation by constructing LDAP filters. Through the construction of normal filters, AND and OR operation injection is implemented to obtain sensitive information.
From January 2018 to January 2019, there were a total of 4 vulnerability information related to it in CVE. Some of the vulnerabilities are as follows:
| Overview | |
|---|---|
| phpLDAPadmin 1.2.2 allowed via cmd.php? LDAP injection with a crafted serverid parameter in the cmd=loginform request or a crafted username and password in the login panel. | |
| MIT krb5 1.6 or later allows authenticated kadmin to add principals to the LDAP Kerberos database by providing "linkdn" and "containerdn" database parameters to bypass the DN container check, or by providing the DN string as an extension to the DN container check. | |
| Apache Karaf before 4.0.8 uses the LDAPLoginModule to authenticate users through LDAP. However, the username is not encoded correctly and is therefore vulnerable to an LDAP injection attack, resulting in a denial of service. | |
| PacketFence html/admin/login.php before 3.0.2 allows remote attackers to conduct an LDAP injection attack via a crafted Username bypasses authentication. |
The above is the detailed content of How to understand LDAP injection. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to understand LDAP injection
May 22, 2023 pm 09:47 PM
How to understand LDAP injection
May 22, 2023 pm 09:47 PM
1. LDAP injection LDAP (Light Directory Access Portocol) is a lightweight directory access protocol based on the X.500 standard. It provides services and protocols for accessing directory databases. It is often used to form directory services with directory databases. The directory is a professional distributed database optimized for query, browsing and search. It organizes data in a tree structure, similar to the file directory in Linux/Unix systems. Data that is not modified frequently, such as public certificates, security keys, and company physical device information, is suitable for storage in the directory. LDAP can be understood as a search protocol, which is similar to SQL and has query syntax, but also has the risk of injection attacks. LDAP injection refers to the client
 How to conduct range practice with bee-box LDAP injection
May 13, 2023 am 09:49 AM
How to conduct range practice with bee-box LDAP injection
May 13, 2023 am 09:49 AM
If the essence of sql injection is to splice strings, then the essence of everything that can be injected is to splice strings. LDAP injection is no exception as a kind of injection. What is more interesting is that it is splicing parentheses (sql injection is also concatenates parentheses, but it is more conventional to say that it concatenates strings). In the environment configuration chapter, the configuration of the ldap environment in bee-box has been discussed in great detail. The shooting range practice chapter is more about the connection process between php and ldap, the introduction of the special functions used in the middle, and some techniques for splicing parentheses. Let’s first talk about the login process of the ldap shooting range in bwapp: First, this is an LDAP login interface, the URL is http://192.168.3.184/bW
 How to configure the environment for bee-box LDAP injection
May 12, 2023 pm 08:37 PM
How to configure the environment for bee-box LDAP injection
May 12, 2023 pm 08:37 PM
1. Overview According to my learning process, I must know what the model and vulnerability of my web attack are. Now I have encountered an unexpected situation. The first time I saw LDAP was during a penetration test in a state-owned enterprise. I found an unpopular one (authorized) and piqued my interest in it. The concept of LDAP: Full name: Lightweight Directory Access Protocol (Lightweight Directory Access Protocol), features: I won’t talk about the protocol, it’s too esoteric, it can be understood as a database for storing data, its special feature is that it is a tree A database in the form of a database. First, the name of the database is equivalent to the root of the tree (i.e. DB=dc), and then the process from the root to a leaf node is
 Solution to PHP Fatal error: Call to undefined function ldap_bind()
Jun 22, 2023 pm 11:37 PM
Solution to PHP Fatal error: Call to undefined function ldap_bind()
Jun 22, 2023 pm 11:37 PM
When developing web applications using PHP, we often need to use LDAP authentication to protect application access. However, in some cases, when we try to use PHP's LDAP functionality to implement authentication, we may encounter the following error message: "PHPFatalerror:Calltoundefinedfunctionldap_bind()". This error message usually occurs when an application calls the ldap_bind() function
 Using LDAP for user authentication in PHP
Jun 20, 2023 pm 10:25 PM
Using LDAP for user authentication in PHP
Jun 20, 2023 pm 10:25 PM
LDAP (LightweightDirectoryAccessProtocol) is a protocol for accessing distributed directory services. It can be used for tasks such as user authentication, authorization, account maintenance, and data storage. In PHP applications, LDAP can be used as a powerful authentication mechanism to provide powerful authentication and authorization functions for applications. This article will introduce how to use LDAP for user authentication in PHP. The specific content includes: Installation and configuration L
 How to use Nginx to protect against LDAP injection attacks
Jun 10, 2023 pm 08:19 PM
How to use Nginx to protect against LDAP injection attacks
Jun 10, 2023 pm 08:19 PM
With the increase in network security vulnerabilities, LDAP injection attacks have become a security risk faced by many websites. In order to protect website security and prevent LDAP injection attacks, some security measures need to be used. Among them, Nginx, as a high-performance web server and reverse proxy server, can provide us with a lot of convenience and protection. This article will introduce how to use Nginx to prevent LDAP injection attacks. LDAP injection attack LDAP injection attack is an attack method targeting the LDAP database. The attacker
 How to protect against LDAP injection vulnerabilities using PHP
Jun 24, 2023 am 10:40 AM
How to protect against LDAP injection vulnerabilities using PHP
Jun 24, 2023 am 10:40 AM
As network security issues receive more and more attention, more and more programmers are beginning to pay attention and learn how to prevent code from being attacked. Among them, common attack methods include SQL injection, XSS, CSRF, etc. However, there is another common attack method that is underestimated: LDAP injection vulnerabilities. This article will introduce the principle of this attack method and how to use PHP to prevent LDAP injection vulnerabilities. LDAP introduction LDAP (LightweightDirectoryAccessProtocol)
 How to use PHP and LDAP to implement user group management and authorization
Jun 25, 2023 am 08:22 AM
How to use PHP and LDAP to implement user group management and authorization
Jun 25, 2023 am 08:22 AM
As the scale of enterprises and business needs continue to expand, user group management and authorization have become an essential part. LDAP (Lightweight Directory Access Protocol), as a directory service protocol widely used in enterprise networks, provides an efficient way to achieve user group management and authorization. This article will introduce how to use PHP and LDAP to implement user group management and authorization. 1. What is LDAP LDAP is a lightweight directory access protocol that is widely used as a directory service protocol in enterprise networks. LDAP is client/server based