 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 What is the principle of fragmentation and assembly of IP datagrams?
What is the principle of fragmentation and assembly of IP datagrams?
What is the principle of fragmentation and assembly of IP datagrams?
When one host sends data to another host, the data needs to be forwarded through multiple routing layers. The forwarding process of IP at the routing layer is relatively complicated. How to process the datagram sent by the destination host?
First we need to understand the format of the datagram:
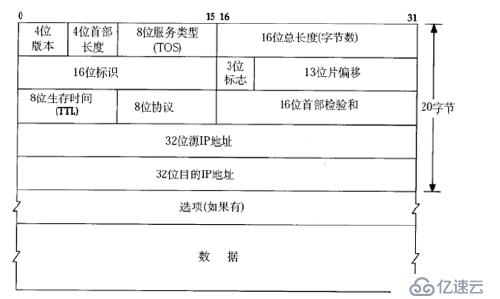
IP forwarding and control are determined by the header of the IP datagram
The value of the 4-digit header length is based on 4 bytes. The minimum value is 5. means that the minimum header length is 4x5=20 bytes.
means without For the IP header of any option, the maximum value represented by the 4-bit table is 15, which means that the maximum header length is 60 bytes.
The 8-bit TOS field has 3 bits to specify the priority of the IP datagram (Currently obsolete), there are 4 bits indicating the optional
including the minimum delay, maximum throughput, maximum reliability and minimum cost of the service type, and the total bit is always 0.
The total length of 16 bits is the number of bytes of the entire datagram (including IP header and IP layer payload).
Every time an IP datagram is transmitted, the 16-bit identifier is increased by 1. can be used to fragment and reassemble the datagram.
3-bit flag and 13-bit slice offset are used for slicing.
TTL (Time to live) is used like this :The source host sets a survival time for the data packet, such as 64, and sends the packet every time it passes through a router
The value is reduced by 1. If it is reduced to 0, it means that the route has been too long and the destination host's network cannot be found, so the packet will be discarded. Therefore, the unit of
this survival time is not seconds, but hops. .
The protocol field indicates whether the upper layer protocol is TCP, UDP, ICMP or IGMP.
Then there is the checksum, which only verifies the IP header, and the higher-layer protocol is responsible for data verification.
The IP address length of IPv4 is 32 bits.
In the IP datagram, the total length of the field is 16 bits, and the maximum length of a datagram is 2^16-1. Although the longest possible datagram can improve transmission efficiency, it rarely exceeds 1500 Bytes; so as long as it exceeds 1500 bytes, the datagram is considered to be fragmented. After the IP datagram is fragmented, each fragment forms a packet with an IP header and is routed independently. After arriving at the destination host, the IP layer of the destination host will process all received fragments before transmitting them to the transport layer. The fragments are reassembled into a datagram.
1.IP fragmentation
1.IP fragmentation principle:
The process of fragmentation and reassembly is transparent to the transport layer because the IP datagram After fragmentation, it can only be reassembled when it reaches the next station, and it is completed by the IP layer of the destination. The fragmented datagram can be fragmented again as needed;
IP fragmentation Fragments and complete packets have almost the same IP header, and the ID field is consistent for American and British fragments, so that the same IP data packet fragment can be identified during assembly. In the IP header, the 16-bit identification number uniquely records the ID of an IP packet, and IP fragments with the same ID will be reassembled; while the 13-bit fragment offset records the position of an IP fragment relative to the entire packet. ; The 3-bit flag in the middle of these two tables marks whether there are new fragments behind this fragment. The receiver can reassemble the IP data using the information provided in these three fields, which are all the information that makes up the IP fragmentation.
(1) The role of the flag field
0 DF MF
The flag field has three digits in total, the highest bit is 0, this value must be copied to all groups
Do not Fragment (DF) values must be copied. DF=1 means that the receiving host cannot fragment the packet. If the packet cannot be fragmented but its length exceeds the MTU, the packet can only be discarded and an ICMP error message needs to be used to notify the source host. DF=0, indicating that fragmentation is possible
Fragmentation (MF) indicates whether the fragmentation is the last fragmentation, MF=1 indicates that the accepted fragmentation is not the last fragmentation, MF=0 indicates when the fragmentation is accepted It is the last fragment
Intentional sending of some IP fragments instead of all will cause the target host to always wait for fragment consumption and occupy system resources.
2. MTU (Maximum Transmission Unit) Principle
When two remote CPs are interconnected, their data must pass through many routers and various network media to reach the other party. End
, the MTU of different media in the network are different, just like a long section of water pipes, consisting of water pipes of different thicknesses (different MTU). The maximum amount of water passing through this section of water pipe will be determined by the thinnest water pipe in the middle. Decide.
For the upper-layer protocols of the network layer (here, take the TCP/IP protocol cluster as an example), they do not care about the thickness of the water pipe because they think it is a matter of the network. At the network layer, the IP protocol detects the size of each data packet transmitted from the upper layer protocol, and determines whether it needs to be fragmented based on the MTU size of the machine. The biggest disadvantage of sharding is that it reduces transmission performance and requires that tasks that can be completed once are divided into multiple processes. Therefore, the higher layers of the network (implementation of the transport layer) often pay attention to this, because some higher layers may require that the packets cannot be fragmented for some reasons, and the index will add a label to the header of the IP datagram. :DF When an IP data packet is transmitted over a large network segment, if the MTU is smaller than the data packet, the forwarding device will drop the data packet according to the situation. Then an error message is returned to the sender, which often causes communication problems, but fortunately most network link MTU is 1500 or greater than 1500
For UDP, the protocol itself is useless The connection protocol does not care whether the arrival order of data packets is correct, so generally UDP does not have much requirements for fragmentation
It is different for TCP. This protocol is a connection-oriented protocol. For TCP It is very concerned about the arrival order of data packets
and whether errors occur during the transmission process, so some TCP applications have requirements for fragmentation---cannot be fragmented
3.MSS (maximum (Message segment length) Principle
MSS is the maximum data segment that can be transmitted by a TCP packet each time. In order to achieve the best transmission performance, the TCP protocol usually negotiates the MSS value of both parties when establishing a connection. This The value is replaced by MTU when the TCP protocol is implemented (minus the 20bites header size of the IP packet and the 20bites header size of the TCP data segment), so the MSS size is often 1460. Both parties will determine the MSS of this connection based on the minimum MSS value provided. Maximum value
2. IP fragmentation steps
The fragmentation information field of an unfragmented datagram is all 0, that is, multiple fragmentation flags are 0, and the offset is 0, fragmenting a datagram requires the following steps
(1) Check the DF flag bit to see if fragmentation is allowed. If this bit is set, the datagram will be discarded and an ICMP error will be returned. To the source
(2) Based on the MTU value, divide the data field into two or pairs of parts. Except for the last data part, the length of all newly created data options must be a multiple of 8 bytes
(3) Each data is put into an IP datagram, and the headers of these datagrams are slightly changed from the original headers
(4) Except for the last datagram fragment, all Each fragment has multiple fragmentation flags set
(5) The fragment offset field in each fragment is set to the position occupied by this data part in the original datagram. This position is relative to The beginning of the original unfragmented datagram.
(6) If options are included in the original datagram, the high-order byte of the option type byte determines whether this information is copied to all fragmented datagrams or only to the first datagram.
(7) Set the header field and total length field of the new datagram.
(8) Recalculate the checksum field of the message header.
At this time, these fragmented datagrams are forwarded like a complete IP datagram. IP processes each datagram fragment independently. Datagram fragments can reach their destination through different routes. If they After passing those routes that specify a smaller MTU, they can be further fragmented
On the destination host, the data is reassembled into the original datagram, and the identification field set by the sending host is the same as that in the datagram. The Yuan IP address is used together with the destination IP address. The fragmentation process does not change this field
3. Reassembly
In order to reconstruct the fragments of these datagrams, the receiving host will A storage buffer is allocated when the slice arrives. This host will also start a timer. When subsequent fragments of the datagram arrive, the data is copied into the buffer memory at the location specified by the fragment offset, and when all fragments have arrived, the complete, unfragmented original datagram is restored.
If the timer expires and the shard remains in an unapproved state, the data will not be retained. The initial value of this timer is the lifetime value of the IP datagram. It is implementation dependent and some implementations allow it to be configured.
Reassembly step
On the receiving side, an original data IP packet sent by the sender reassembles all the fragments before they can be submitted to the upper layer protocol. Each one will be The reassembled IP datagrams are represented by an ipq structure
In order to effectively improve the assembly of fragments, the structure used to save fragments must achieve the following points
(1) Quick positioning A group of packets of a certain datagram
(2) Quickly insert new fragments into a group of fragments belonging to a certain datagram
(3) Effectively judge a datagram Whether all fragments have been received
(4) It has a reassembly timeout mechanism. If the timeout overflows before the reassembly is completed, all contents of the datagram will be deleted
The above is the detailed content of What is the principle of fragmentation and assembly of IP datagrams?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How do websites set black/whitelist IP restrictions and country and city IP access restrictions through nginx?
Jun 01, 2023 pm 05:27 PM
How do websites set black/whitelist IP restrictions and country and city IP access restrictions through nginx?
Jun 01, 2023 pm 05:27 PM
1. Black/white list IP restricted access configuration nginx There are several ways to configure black and white lists. Here are only two commonly used methods. 1. The first method: allow, denydeny and allow instructions belong to ngx_http_access_module. nginx loads this module by default, so it can be used directly. This method is the simplest and most direct. The setting is similar to the firewall iptable. How to use: Add directly to the configuration file: #Whitelist settings, followed by allow is accessible IPlocation/{allow123.13.123.12;allow23.53.32.1/100;denyall;}#Blacklist settings,
 What does binding ip and mac mean?
Mar 09, 2023 pm 04:44 PM
What does binding ip and mac mean?
Mar 09, 2023 pm 04:44 PM
IP and mac binding refers to associating a specific IP address with a specific MAC address, so that only the device using the MAC address can use the IP address for network communication. Binding ip and mac can prevent the IP address of the bound host from being spoofed. Prerequisites: 1. The MAC address is unique and cannot be spoofed; it can only be bound to hosts on the network directly connected to the router (that is, The host's gateway is on the router).
 How to check IP address on WeChat
May 31, 2023 am 09:16 AM
How to check IP address on WeChat
May 31, 2023 am 09:16 AM
How to check the IP address on WeChat: 1. Log in to the computer version of WeChat, right-click the taskbar at the bottom of the screen, and click "Task Manager"; 2. When the task manager pops up, click "Details" in the lower left corner; 3. Task management Enter the "Performance" option of the browser and click "Open Resource Monitor"; 4. Select "Network" and check the WeChat process "Wechat.exe"; 5. Click "TCP Connection" below to monitor the WeChat network IP related situation. Sending a message and getting a reply will reveal the other person's IP address.
 How to set directory whitelist and ip whitelist in nginx
May 18, 2023 pm 03:52 PM
How to set directory whitelist and ip whitelist in nginx
May 18, 2023 pm 03:52 PM
1. Set the directory whitelist: There is no restriction on the specified request path. If there is no restriction on the request path to the api directory, it can be written as server{location/app{proxy_passhttp://192.168.1.111:8095/app ;limit_connconn20;limit_rate500k;limit_reqzone=fooburst=5nodelay;}location/app/api{proxy_passhttp://192.168.1.111:8095/app/api}}#Because nginx will give priority to accurate matching
 How to obtain the user's real IP address based on nginx reverse proxy
May 13, 2023 pm 05:07 PM
How to obtain the user's real IP address based on nginx reverse proxy
May 13, 2023 pm 05:07 PM
Introduction When nginx is used as a reverse proxy, the IP address obtained by the default configuration backend comes from nginx. Use request.getRemoteAddr(); to obtain the IP address of nginx, not the user's real IP. 1. Modify Nginx Configuration: server{listen80;server_namejenkins.local.com;location/{proxy_set_headerHost$host;proxy_set_headerX-Real-IP$remote_addr;proxy_passhttp://192.168.10.
 Local IP address query
Jan 05, 2024 pm 01:42 PM
Local IP address query
Jan 05, 2024 pm 01:42 PM
The methods for querying the IP address of this machine are: 1. Under Windows system, open the "Start Menu" and search for "cmd" to open the command prompt, enter "ipconfig", and then press the Enter key to find a line named "IPv4 Address" , the number next to it is the IP address of the machine; 2. Under macOS system, click the Apple icon in the upper left corner of the screen, select "System Preferences", find the currently connected network in the "Network" option, and click the "Advanced" button , find the IP of the machine in the "TCP/IP" tab, etc.
 What should I do if my wifi shows no IP allocation?
Aug 30, 2023 am 11:58 AM
What should I do if my wifi shows no IP allocation?
Aug 30, 2023 am 11:58 AM
Solution to wifi showing no IP allocation: 1. Restart the device and router, turn off the Wi-Fi connection on the device, turn off the device, turn off the router, wait a few minutes, then reopen the router to connect to wifi; 2. Check the router settings and restart DHCP, make sure the DHCP function is enabled; 3. Reset network settings, which will delete all saved WiFi networks and passwords. Please make sure they are backed up before performing this operation; 4. Update the router firmware, log in to the router management interface, and find the firmware Update options and follow the prompts.
 How does NGINX count the PV, UV, and independent IP of the website?
May 19, 2023 am 09:13 AM
How does NGINX count the PV, UV, and independent IP of the website?
May 19, 2023 am 09:13 AM
Concept: uv (uniquevisitor): unique visitor, each independent Internet computer (based on cookies) is regarded as a visitor, and the number of visitors who visit your website within a day (00:00-24:00). Visits to the same cookie within a day are only counted once PV (pageview): visits, that is, page views or clicks, each visit to the website by the user is recorded once. When a user visits the same page multiple times, the total number of visits is counted. Independent IP: The same IP address is only counted once within 00:00-24:00. Friends who do website optimization are most concerned about this. Let me first state the environment. This run nginx version 1.7, the backend tomcat runs dynamic



