
R1(config)#int f0/0
R1(config-if)#ip add 12.1.1.1 255.255.255.0
R1( config-if)#no sh
R1(config-if)#exit
R1(config)#int f0/1
R1(config-if)#ip add 10.1.1.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#exit
R1(config)#ip route 0.0 .0.0 0.0.0.0 12.1.1.2
R3(config)#int f0/0
R3(config-if)#ip add 192.168.1.3 255.255.255.0
R3(config-if)#no sh
R3(config-if)#exit
R3(config)#int f0/1
R3(config-if) #ip address dhcp
R3(config-if)#no sh
R3(config-if)#exit
R3(config)#int loopback 0
R3(config-if)#ip add 3.3.3.3 255.255.255.255
R3(config-if)#exit
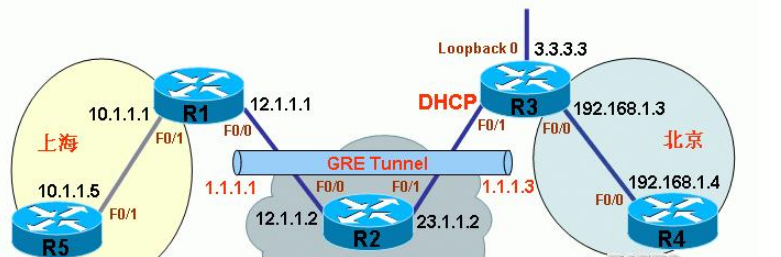
Description: On the interface F0/1 of R3 connected to the Internet Enable DHCP to obtain an address dynamically, so the IP address on F0/1 is not known in advance, and create a Loopback 0 (address 3.3.3.3/32) as the source address of the local p2p GRE tunnel.
(1) Configure a p2p GRE tunnel on R1 with the endpoint being R3:
R1(config)#interface tunnel 1
R1(config-if)#ip address 1.1.1.1 255.255.255.0
R1(config-if)#tunnel source 12.1.1.1
R1(config-if)#tunnel destination 3.3.3.3
R1( config-if)#exit
R1(config)#ip route 3.3.3.3 255.255.255.255 12.1.1.2
Description: The p2p GRE tunnel interface number from R1 to R3 is 1, and the tunnel address is 1.1.1.1, the source point of the tunnel is the external network interface address 12.1.1.1, and the end point of the tunnel is the Loopback 0 interface address of R3 3.3.3.3. Although the tunnel end address is not routable on the Internet, a static route must be written Point 3.3.3.3/32 to your own Internet exit as this is a configuration rule.
R3(config)#int tunnel 3
R3(config-if)#ip address 1.1.1.3 255.255.255.0
R3(config-if)#tunnel source loopback 0
R3(config-if)#tunnel destination 12.1.1.1
R3(config-if)#exit
Description: p2p GRE tunnel interface from R3 to R1 The number is 3, the tunnel address is 1.1.1.3, the source point of the tunnel is the Loopback 0 interface address 3.3.3.3, and the end point of the tunnel is the external network interface address of R1 12.1.1.1.
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#encryption 3des
R1(config-isakmp)#hash sha
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2
R1(config-isakmp)#exit
R1(config )#crypto isakmp key 0 cisco123 address 0.0.0.0 0.0.0.0
R1(config)#crypto ipsec transform-set ccie esp-3des esp-sha-hmac
R1(cfg-crypto -trans)#exit
R1(config)#crypto dynamic-map ddd 10
R1(config-crypto-map)#set transform-set ccie
R1( config-crypto-map)#exit
R1(config)#crypto map mymap 10 ipsec-isakmp dynamic ddd
R1(config)#crypto map mymap local-address fastEthernet 0/0
R1(config)
#R1(config)#int f0/0
R1(config-if)#crypto map mymap
R1(config -if)#exit
*Mar 1 00:32:44.307: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R1(config)
#Description: static The configuration of IP side R1 is slightly different from that of Dynamic LAN-to-LAN ××× in that there is an additional command "crypto map mymap local-address fastEthernet 0/0" because the IOS version used in this experimental environment is higher than 12.2 (13)T, so Crypto map can only be applied on the physical interface and does not need to be applied on the GRE tunnel interface.
R3(config)#crypto isakmp policy 1
R3(config-isakmp)#encryption 3des
R3(config-isakmp)#hash sha
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#group 2
R3(config-isakmp)#exit
R3 (config)#crypto isakmp key 0 cisco123 address 12.1.1.1
R3(config)#crypto ipsec transform-set ccie esp-3des esp-sha-hmac
R3(cfg-crypto- trans)#exit
R3(config)#access-list 100 permit gre host 3.3.3.3 host 12.1.1.1 R3(config)
#R3(config)#crypto map l2l 1 ipsec -isakmp
R3(config-crypto-map)#set peer 12.1.1.1
R3(config-crypto-map)#set transform-set ccie
R3( config-crypto-map)#match address 100
R3(config-crypto-map)#exit
R3(config)#crypto map l2l local-address f0/1
R3(config)#int f0/1
R3(config-if)#crypto map l2l
R3(config-if)
#*Mar 1 00 :32:58.907: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R3(config-if)
# Description: Dynamic IP side R3 and configuration are the same as ordinary LAN-to-LAN × The slight difference of ×× is that there is an additional command "crypto map l2l local-address f0/1". Because the IOS version used in this experimental environment is higher than 12.2(13)T, Crypto map is only under the physical interface. Just apply it and do not need to apply it under the GRE tunnel interface.
Note: No matter how traffic is sent, ISAKMP SA cannot be established because in a Dynamic p2p GRE over IPsec environment, data must be sent from the dynamic IP to the static IP side first, otherwise the GRE tunnel cannot be established, ××× can not complete.
Configuring dynamic routing protocol
The above is the detailed content of What is dynamic P2P-GRE based on IPsec?. For more information, please follow other related articles on the PHP Chinese website!
 How to use subplot in matlab
How to use subplot in matlab
 What should I do if the itinerary card cannot be opened?
What should I do if the itinerary card cannot be opened?
 SpringBoot project building steps
SpringBoot project building steps
 What are the video server configuration parameters?
What are the video server configuration parameters?
 Introduction to the usage of axis function in Matlab
Introduction to the usage of axis function in Matlab
 mobile phone screen tft
mobile phone screen tft
 How to import mdf files into database
How to import mdf files into database
 Delete redundant tables in the table
Delete redundant tables in the table
 Implementation method of vue online chat function
Implementation method of vue online chat function




