Example analysis of MSSQL backdoor from Winnti hacker group
For some time, ESET researchers have been tracking the activities of Winnti, a group that has been active since 2012 and has targeted the video game and software industry supply chains. A previously unregistered backdoor was recently discovered that targets Microsoft SQL (MSSQL) systems. This backdoor bears many similarities to the PortReuse backdoor, another tool used by the Winnti Group and first documented in October 2019.
Members of the Winnti group released a new backdoor sample, named Skip-2.0, which was detected this year. This backdoor targets MSSQL servers 11 and 12 and allows an attacker to connect to any MSSQL account using a magic password while automatically hiding these connections in the logs. Attackers can use backdoors to enter the database, copy, modify or delete its contents, thereby manipulating the in-game currency for financial gain. According to our knowledge, Skip-2.0 is the first publicly documented MSSQL server backdoor.
This article will focus on the technical details and functions of the mssql server backdoor, as well as the technical similarities between skip.2-0 and winnti’s known arsenal (especially the portreuse backdoor and shadowpad).
vmprotected launcher
We found skip-2.0 when looking for vmprotected launcher, whose payload is usually portreuse or shadowpad.
Embedded Payload
Like the encrypted portreuse and shadowpad payloads, skip-2.0 is embedded into the vmprotected launcher, as shown in Figure 1:

Encryption
Like other launchers using VMProtect, the payload must also be encrypted. This encryption method uses the RC5 algorithm, and the key consists of volumeID and the string "f@ukd!RCTO R$".
Persistence
Like portreuse and shadowpad, the startup program may persist by exploiting a dll hijack by installing it in c:\windows\system32\tsvipsrv.dll. This causes the standard Windows SessionEnv service to load the DLL when the system starts.
Packager
The decrypted embedded payload is actually the winnti group’s custom packer. This packager is the same code we documented in the white paper. The tool was used to package the PortReuse backdoor and embed the payload into compromised video games.
Configuration
The program packaging configuration contains the key required to decrypt the binary file, as well as the name, size and execution type (exe or dll) of the original file. The payload configuration is shown in Table 1.
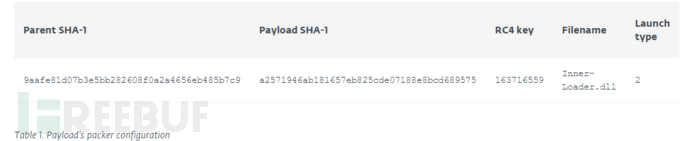
Packager configuration As you can see, the payload is called an internal loader. Internal loader is the name of an injector that is part of the winnti group's arsenal and is used to inject the portreuse backdoor into processes listening on specific ports.
Internal Loader
This is a variation of the internal loader that instead of looking for a process listening on a specific port like when injecting the portreuse backdoor, it looks for a process named sqlserv.exe , which is the conventional process name of mssql server. If found, the internal loader injects the payload into this process. This payload is packaged with a custom packer whose configuration is listed in Table 2.
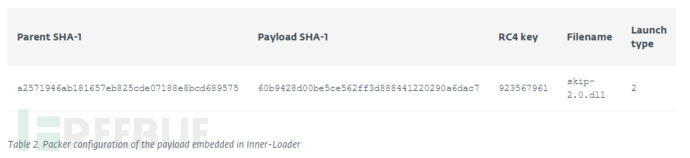
The original file name of this injected payload is skip-2.0.dll.
skip-2.0
After being injected and started by the internal loader, skip-2.0 first checks whether it is executing in the sqlserv.exe process, and if so, retrieves the handle to sqllang.dll , the handle is loaded by sqlserv.exe. Then continue to find and hook multiple functions from that dll. Figure 2 describes the running process of skip-2.0.
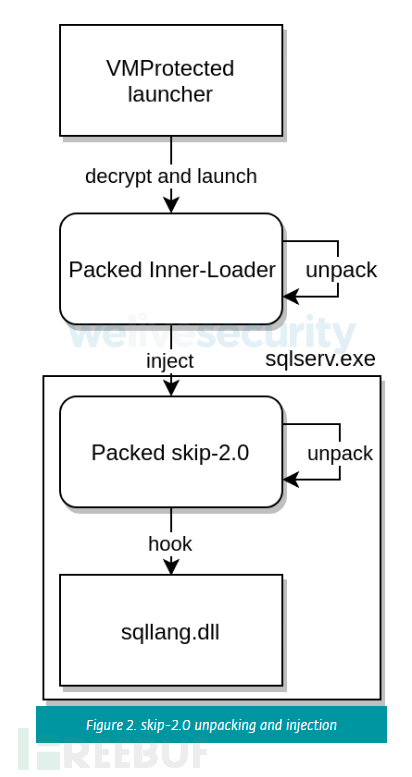
Hooking sqllang.dll
The hook process used by skip-2.0 is very similar to netagent, which is the portreuse module responsible for installing network hooks. This hook library is built on the open source distorm disassembler, which is also used by multiple open source hooking frameworks. A disassembly library is needed to correctly calculate the size of the instructions to be hooked. Almost the same hook process is used by NetAgent and Skip-2.0, as shown in the figure below.
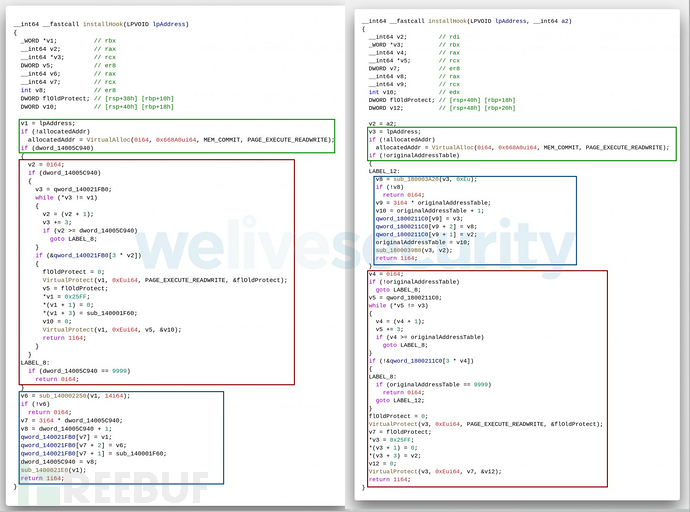
Figure 3 Hex-Rays output comparison between the NetAgent (left) and skip-2.0 (right) hooking procedures
One significant difference is skip- The hooking function in 2.0 takes the address of the hook to be installed as a parameter, but for netagent, the address of the hook to be installed is hard-coded. This is because skip-2.0 must hook multiple functions in qllang.dll to run properly, while netagent only targets one function.
To locate each sqllang.dll function of the hook, skip-2.0 first retrieves the size of the dll loaded into memory (i.e. its virtual size) by parsing the pe header. Next, the byte array that needs to be matched in sqllang.dll needs to be initialized, see Figure 4. Once the address of the first match to the byte array is found, the hook is installed using the process shown in Figure 3.
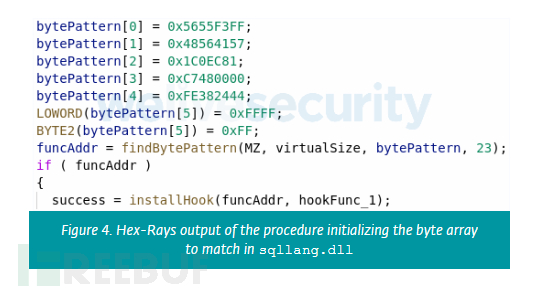
Then, after the hook is successfully installed, it will be recorded in cleartext. The file is located in the hard-coded path c:\windows\temp\ts\u 2ce1.tmp, as shown in the figure 5 shown.
If the target function is not found, the hook installer searches for a fallback function with a different set of byte patterns.
By matching the byte sequence to locate the address of the target function instead of using a static offset, coupled with the use of a fallback sequence of bytes, skip-2.0 can adapt to mssql updates more flexibly and can Updates for multiple sqllang.dll.
Password Control
The target functions of skip-2.0 are related to authentication and event logging. Target functions include:
CPwdPolicyManager::ValidatePwdForLogin CSECAuthenticate::AuthenticateLoginIdentity ReportLoginSuccess IssueLoginSuccessReport FExecuteLogonTriggers XeSqlPkg::sql_statement_completed::Publish XeSqlPkg::sql_batch_completed::Publish SecAuditPkg::audit_event::Publish XeSqlPkg::login::Publish XeSqlPkg::ual_instrument_called::Publish
The most interesting of these is the first function (cpwdpolicymanager::validatepwdforlogin), which is responsible for validating the password provided for a given user.
This function's hook checks whether the user-supplied password matches the magic password; if so, the original function will not be called and the hook will return 0, allowing the connection. Next, a global flag is set up to be checked by other hook functions responsible for event logging. The corresponding decompilation process is shown in Figure 6. With this global flag set, the hook's logging function will return silently without calling its corresponding original function, so the operation will not be logged.
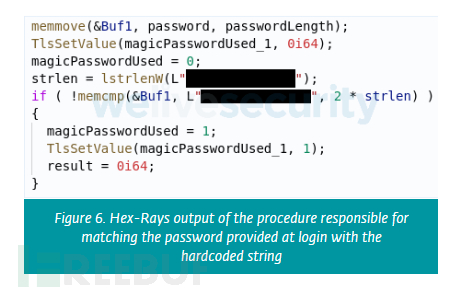
If you log in with a magic password, the reportloginsaccess and issueloginsuccessreport hooks will not call the original function. The same behavior applies to feexecutelogontriggers. Other logging features, such as xesqlpkg::sql_completed::publish or xesqlpkg::sql_batch_completed::publish, will also be disabled in cases where the user logs in with a magic password. Several audit events are also disabled, including secauditpkg::audit_event::publish, xesqlpkg::login::publish, and xesqlpkg::uau instrument_called::publish.
This series of hooks not only allows the attacker to gain persistent control in the victim's mssql server via a special password, but also disables multiple logs when using that password, making the attacker undetectable.
Researchers tested Skip-2.0 against multiple MSSQL Server versions and found that they could successfully log in using passwords for MSSQL Server 11 and 12. In order to check if skip-2.0 targets a specific sqllang.dll version, a yara rule was created which can be found in the github repository.
Connection with Winnti
skip-2.0 has many similarities with other tools from winnti. The vmprotected launcher, custom packager, internal loader and hook framework are part of the winnti toolset.
The above is the detailed content of Example analysis of MSSQL backdoor from Winnti hacker group. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)





