How to analyze Haproxy port reuse
Author of this article: Spark (Ms08067 intranet security team member)
1. Overview
Haproxy is developed using c language High-performance load balancing proxy software, providing TCP and HTTP application proxy, free, fast and reliable.
Similar to frp, it can be run using one configuration file and one server.
Advantages:
Widely used in large business areas
Supports four-layer proxy (transport layer) and seven-layer proxy (application layer)
Supports acl ( Access Control List), routing can be configured flexibly
Windows can be run after compiling with cygwin (can be cross-platform)
Access Control Lists (ACL) are applied in routers A list of commands for an interface. These command lists are used to tell the router which data packets can be accepted and which data packets need to be rejected.
2. Configuration
Official configuration manual: https://cbonte.github.io/haproxy-dconv/2.2/configuration.html
The configuration file consists of global configuration and proxy configuration:
Global configuration (global): Defines parameters related to haproxy process management security and performance
Proxy settings (proxies) :
defaults: Provide default parameters for other configuration sections. The default configuration parameters can be reset by the next "defaults"
frontend: Define a series of listening sockets, these The socket can accept client requests and establish connections with it
backend: Define "backend" servers, and the front-end proxy server will dispatch short-term requests to these servers
listen: Defining the listening socket and backend server is similar to putting the frontend and backend segments together
Example:
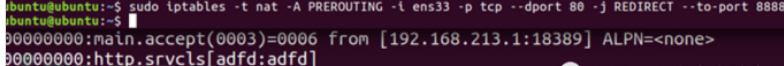
global defaults log global mode tcp option dontlognull timeout connect 5000 timeout client 50000 timeout server 50000 frontend main mode tcp bind *:8888 option forwardfor except 127.0.0.1 option forwardfor header X‐Real‐IP # 配置acl规则 acl is‐proxy‐now urlp_reg(proxy) ^(http|https|socks5)$ # 分发到对应的backend use_backend socks5 if is‐proxy‐now use_backend http backend socks5 mode tcp timeout server 1h server ss 127.0.0.1:50000 backend http mode tcp server http 127.0.0.1:80
Focus on frontend and backend.
You need to write acl rules and configure forwarding in Frontend. For example, when HTTP traffic comes, it is forwarded to the web service; when RDP traffic comes, it is forwarded to the RDP service.
Specific operations need to be written in Backend, which is to transfer to which port of which target.
3. Ideas
(1) Idea 1 (general)
Write acl rules at layer four (transmission layer) to carry out load and distribute it according to the protocol type. For example, when http traffic is encountered, it is sent to the http service, when rdp is encountered, it is sent to the rdp service, etc.
(2) Idea 2
Write acl rules, load them on the seventh layer (application layer), determine the application type for distribution, for example, when encountering http distribution to http service, otherwise sent to xxx service.
4. Steps
Take idea 1 as an example:
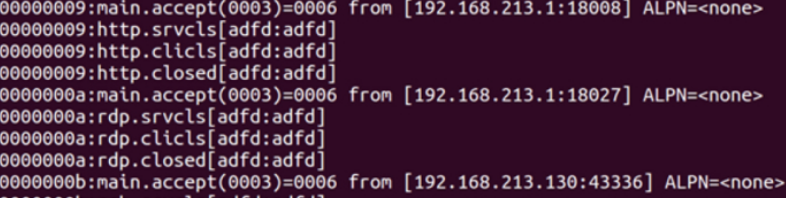
Capture tpkt (Application Layer Data Transfer Protocol) information through wireshark
Write acl rule routing for traffic distribution
Add backend server
Original interface takeover
Complete
##4.1 Capture tpkt
About tpkt, please refer to Baidu or view the reference linkAfter the three-way handshake, the application layer data transmission begins.
Use wireshark to capture packets:
ssh protocol: 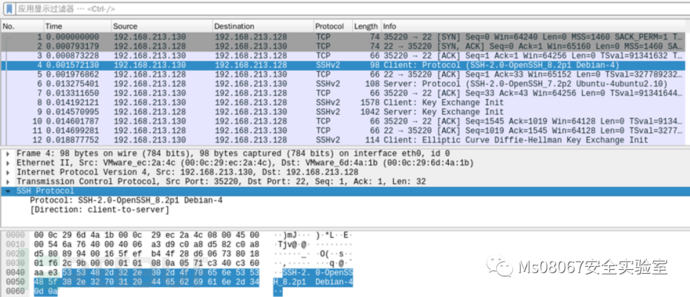
rdp protocol: 030000
Quick check: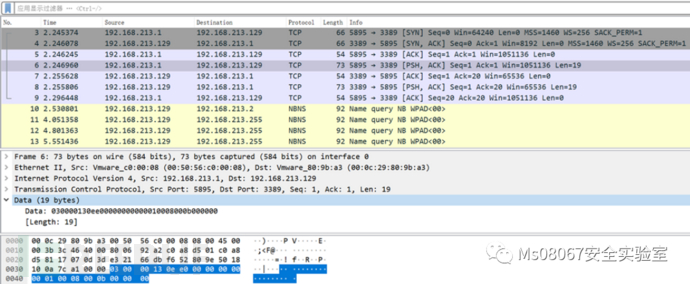
| TPKT | |
|---|---|
| 535348 | |
| 030000 | |
| 474554 | |
| 504f53 | |
| 505554 | |
| 44454c | |
| 4f5054 | |
| 484541 | |
| 434f4e | |
| 545241 | |
| 160301 |
The above is the detailed content of How to analyze Haproxy port reuse. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52



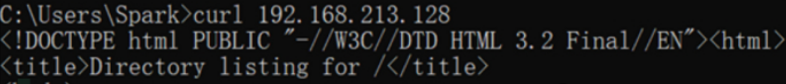
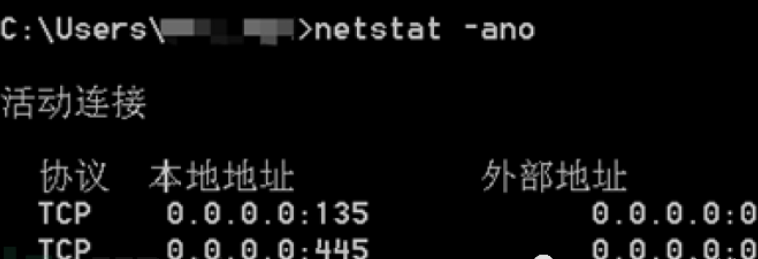
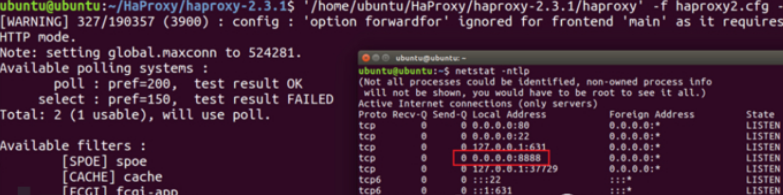
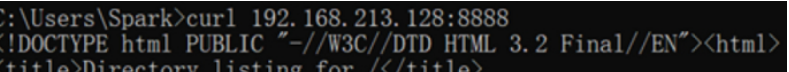
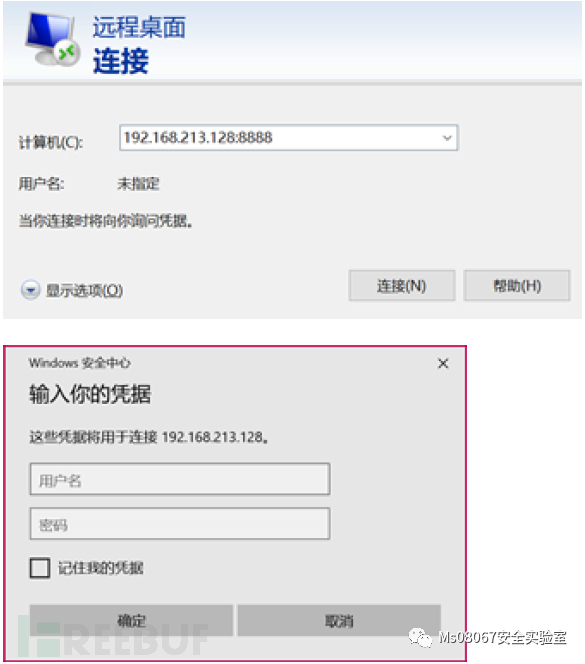 SSH协议:访问靶机的8888端口,流量被haproxy分发至本机的22。
SSH协议:访问靶机的8888端口,流量被haproxy分发至本机的22。